Installing Mend for GitLab
Overview
Before beginning the installation process, ensure that the guidelines described in Installation Prerequisites have been fulfilled.
Note: Follow all procedures in order as they are presented here.
Installing the GitLab Integration
Note: When setting up repository integrations, you can only connect one source code management (SCM) system to a single Mend organization. For example, if you integrate a GitHub organization, you cannot link additional SCM systems like GitLab groups or Bitbucket teams to the same Mend organization.
Note: This article is relevant for all self-managed GitLab instances, however, there are a few key steps that differ for self-managed GitLab instances on GitLab.com. The instructions for those will be highlighted in each step where differences exist.
Configure a System Hook
Notes:
This step is different for self-managed GitLab.com instances. If applicable, follow the collapsed “Add Group Hooks (GitLab.com)” steps at the end of this section.
The Mend webhook handler URL can only be checked after running the wss-gls-app container.
Go to your GitLab instance and click Admin Area > System Hooks.
Fill in the fields according to these guidelines:
URL: The Mend webhook handler URL. The URL should end with '/payload'. Enter the webhook URL in the following format: http://<docker-wss-gls-app-destinationURL>:5678/payload.
Secret Token: Secret token for payload validation
Trigger: All checkboxes except Tag push events must be marked
Enable SSL Verification: Yes
Click Add system hook. Your system hook will appear in the System Hooks section at the bottom of the screen.
Creating a New GitLab User and a Personal Access Token
Create a new and regular GitLab user and name it @mend. This user does not need to be an admin. Note:
This user does not require a real email address. The Personal Access Token for the next step can be created by an admin impersonating the @mend user.
The username is not required to be exactly “mend”, any other username is valid. In the documentation, we are still referring to the @mend user as a technical username for the integration.
Create a Personal Access Token for your new @mend user. Go to the @mend Settings > Access Tokens, and fill in the fields according to these guidelines:
Name: The name of your token, e.g. "mendToken"
Expires at (optional): The expiration date for your token
Scopes: All checkboxes should be marked.
Click Create personal access token. Copy the generated Personal Access Token to the clipboard, to be used in the next section.
Creating an Activation Key
Note: This step slightly differs between the Mend AppSec Platform and the Legacy SCA application. Instructions for the Legacy application are listed at the bottom of this section.
Open a separate browser tab or window and log in to the Mend Application.
Navigate to the Integrations page of the Mend application.
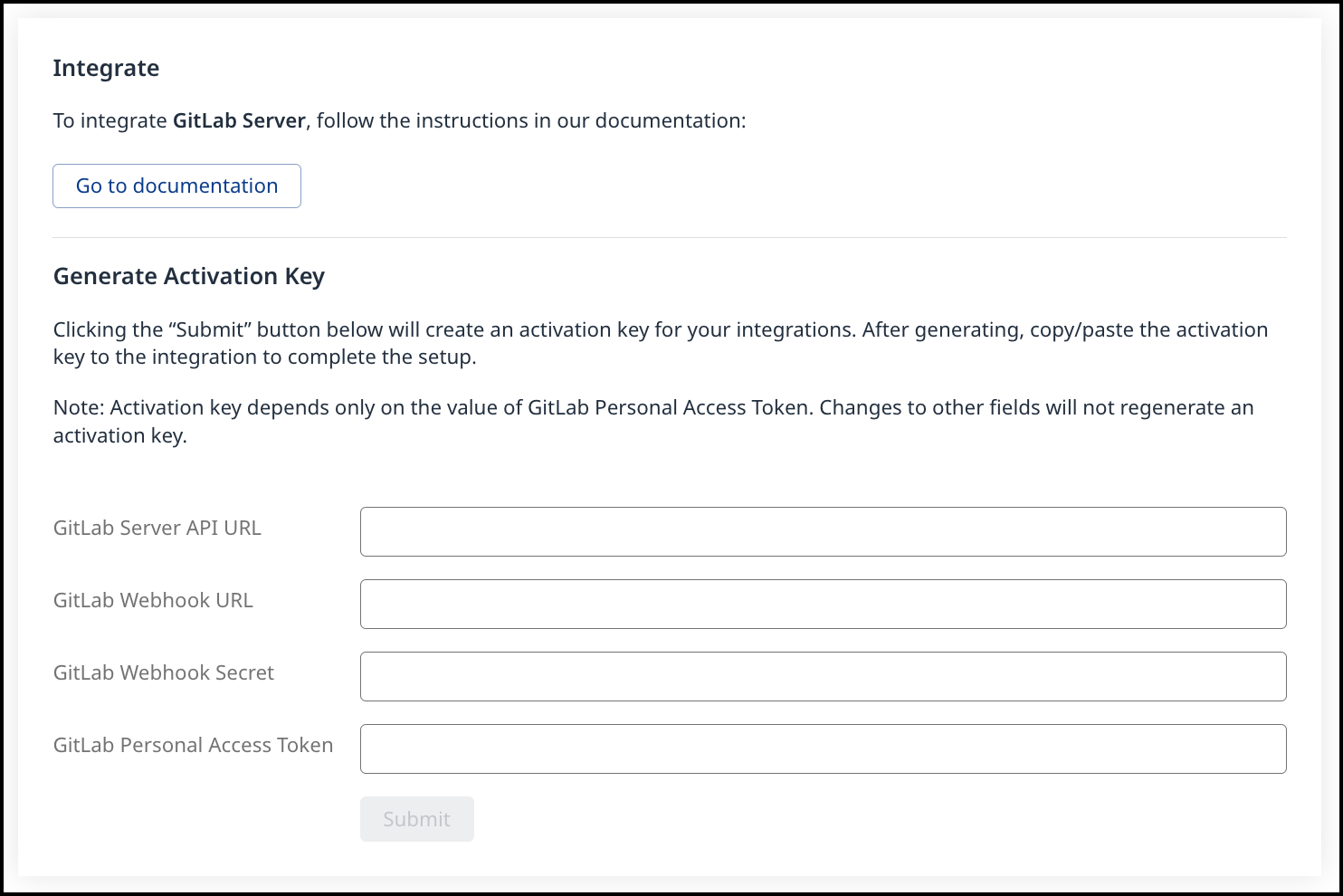
Expand the Mend for GitLab bar to view the following fields:
GitLab Server API URL: Your GitLab Server instance's API URL. For example: https://GitLabDevServer.com/api/v4
GitLab.com API URL: https://gitlab.com/api/v4GitLab Webhook URL: The URL of the Mend webhook handler (the same URL as the system hook from Configure a System Hook).
The webhook URL is used to create webhooks from GitLab projects the integration is installed, to allow Mend Remediate to receive issue-related events.
NOTE: If this webhook URL is on a local server, make sure your GitLab server is configured to allow outbound requests to local servers in Admin Area > Settings > Network > Outbound Requests. Here you can allow outbound requests to your entire local network or simply whitelist the Mend webhook URL.GitLab Webhook Secret: The webhook secret you entered when creating the system hook in Configure a System Hook.
GitLab Personal Access Token: The @mend user's personal access token was created in the previous step.
Click Get Activation Key to generate your activation key. A new Service user is created for this integration inside the Mend Application with a WS prefix. NOTE: Do not remove this Service user and ensure this user remains part of the Admin group.
Copy the newly generated Activation Key (You will need it in the next procedure).
Running the UI Configuration Tool
The UI Configuration tool enables you to configure the deployment file according to your specific configuration requirements.
Open index.html located inside the wss-configuration directory via a Chrome or Firefox Web browser. The Mend Configuration Editor page is displayed.
Load the template JSON configuration file by clicking Choose File and selecting the file located at wss-configuration/config/prop.json. The General tab appears in the Editor.
Click the General tab and enter the Activation Key which you copied in the previous section.
To manage the creation of GitLab Issues or Commit Statuses globally across all of your organization's repositories, click the Issues tab. (The parameters in this tab are displayed in the table below.)
To display the Proxy tab, click the Advanced Properties checkbox on the Home tab. Proxy fields that are not mandatory (e.g., user name and password) must be left blank. (The parameters in this tab are displayed in the table below.)
Click Export, and save the JSON file with the name prop.json. This file will be used in the next sections.
You can export the JSON file at any time, even if you did not finish editing it in order to save your configurations and to enable assigning the configuration of a specific section to the appropriate professional in your organization (e.g., data source section may be assigned to the DBA of your organization).
When exporting the configuration file, it is important to give it the filename “prop.json”
In case of replacing the prop.json file with a new one, it is not enough to restart the controller and scanner pods. It is required to delete the old pods and run new ones.
Details on Attributes of the Configuration File
Section | Label | Name | Type | Mandatory | Description | Sample Value |
|---|---|---|---|---|---|---|
General | Activation Key | bolt.op.activation.key | String | yes | Your generated activation key in the Mend application | |
Proxy | HTTP Proxy Host | proxy.host | Host Address | no | HTTP proxy host. Leave blank to disable. Default value: Empty | |
Proxy | HTTP Proxy Port | proxy.port | Integer | no | HTTP proxy port. Leave blank to disable. Default value: Empty | |
Proxy | Proxy User | proxy.user | String | no | Proxy UserName (if applicable) | user |
Proxy | Proxy Password | proxy.password | String | no | Proxy Password (if applicable) | abc123 |
Proxy | Enable Proxy For All Traffic | proxy.for.all | Boolean | no | If set to NOTES:
| |
Advanced | Controller URL | controller.url | String | no | The ability to modify the App container URL in case its default name (wss-ghe-app) was modified. Default value: http://wss-ghe-app:5678 | |
Issues | Should Create Issues | bolt4scm.create.issues | Boolean | no | The ability to globally enable/disable Issues creation across all of your organization's repositories. Default value: true (NOTE: Supported from version 20.5.1.3 only) | |
Issues | Should Update Commit Status | bolt4scm.create.check.runs | Boolean | no | The ability to globally enable/disable commit statuses across all of your organization's repositories. Default value: true (NOTE: Supported from version 20.5.1.3 only) |
Uploading Mend Scan Results to the GitLab Security Dashboard (For GitLab Ultimate Users Only)
To upload the Mend scan results to the GitLab security dashboard, add the following YAML to your .gitlab-ci.yml file:
- CODE
whitesource-security-publisher: image: openjdk:8-jdk when: manual script: - curl "{{WEBHOOK_URL}}/securityReport?repoId=$CI_PROJECT_ID&repoName=$CI_PROJECT_NAME&ownerName=$CI_PROJECT_NAMESPACE&branchName=$CI_COMMIT_REF_NAME&defaultBranchName=$CI_DEFAULT_BRANCH&commitId=$CI_COMMIT_SHA" -o gl-dependency-scanning-report-ws.json artifacts: paths: - gl-dependency-scanning-report-ws.json reports: dependency_scanning: - gl-dependency-scanning-report-ws.json expire_in: 30 days Replace
{{WEBHOOK_URL}}with the GitLab Webhook URL from Creating an Activation Key (remove the “payload” part from the URL).
NOTE: The CI job’s name must be whitesource-security-publisher for Mend to recognize and trigger it.
Supported Dependency Files
The following dependency files are supported for Mend for GitLab SCA scans:
bower.json
build.gradle
build.gradle.kts
build.sbt
conanfile.py
conanfile.txt
cargo.toml
composer.json
dependencies.scala
environment.yml
Gemfile.lock
glide.lock
go.mod
Godeps.lock
gogradle.lock
Gopkg.lock
gradle.lockfile
gradle.properties
libs.gradle
libs.versions.toml
package-lock.json
package.json
paket.dependencies
packages.config
packages.lock.json
packrat.lock
Pipfile
pipfile.lock
pnpm-lock.yaml
Podfile
poetry.lock
pom.xml
pubspec.yaml
pyproject.toml
requirements.txt
settings.gradle
setup.cfg
setup.py
vendor.conf
versions.kt
yarn.lock
Any metafile with one of the following extensions:
asp
aspx
config
csproj
do
gitmodules
htm
html
jsp
shtml
tf
xhtml
Cargo.lock
Running the Containers
Deploying Using Docker
Note: For self-managed GitLab.com instances, it is mandatory to specify the WS_CONFIG_ACCOUNT_NAME env var in the controller, with a value that is not the default “whitesource-config”. This value would be your GitLab.com group that contains the global config repo (still named “whitesource-config”), which all other groups and repos will inherit from.
Create a network bridge (this will create a private network between the different containers since all containers need to run within the same network):
docker network create -d bridge my_bridgeRun the wss-gls-app app container:
docker run --name wss-gls-app --network my_bridge -p 9494:9494 -p 5678:5678 -v <path/to/config/directory>:/etc/usr/local/whitesource/conf wss-gls-app:<version>
# For example:
docker run --name wss-gls-app --network my_bridge -p 9494:9494 -p 5678:5678 -v c:/tmp/gls/:/etc/usr/local/whitesource/conf/ wss-gls-app:19.9.1.1Run the wss-scanner scanner container:
docker run --name wss-scanner-gls --restart=always --network my_bridge -p 9393:9393 -v <path/to/config/directory>:/etc/usr/local/whitesource/conf/ wss-scanner:<version>
# For example:
docker run --name wss-scanner-gls --restart=always --network my_bridge -p 9393:9393 -v c:/tmp/gls/:/etc/usr/local/whitesource/conf/ wss-scanner:19.9.1.1Run the wss-remediate server container:
docker run --name remediate-server --restart=always --network my_bridge -e LOG_LEVEL=debug -p 8080:8080 -v <path/to/config/directory>/prop.json:/etc/usr/local/whitesource/conf/prop.json -v /tmp:/tmp wss-remediate:<version>
# For example:
docker run --name remediate-server --restart=always --network my_bridge -e LOG_LEVEL=debug -p 8080:8080 -v c:/tmp/gls/prop.json:/etc/usr/local/whitesource/conf/prop.json -v /tmp:/tmp wss-remediate:19.8.1
# NOTE: If port 8080 isn't available, you can use a different port by modifying the first port entry in the 'docker run' command. For example:
# docker run --name remediate-server --network my_bridge -e LOG_LEVEL=debug -p 8082:8080 -v c:/tmp/gls/prop.json:/etc/usr/local/whitesource/conf/prop.json -v /tmp:/tmp wss-remediate:19.8.1Deploying Using Helm Charts
The wss-deployment folder consists of the following structure:
helm
configs
templates
config.yaml
wssScmIntegration.yaml
Chart.yaml
values.yaml
Chart.yaml
This file contains information about the chart.
Values.yaml
This file represents the Mend integration image names and versions.
wsscanner:
image: {image}
version: {version}
wsscontroller:
image: {image}
version: {version}
wssremediate:
image: {image}
version: {version}For each image declaration (wssscanner, wsscontroller, wssremediate), replace {image} and {version} with the actual built image name and version. NOTE: For wsscontroller, use the name and version of the wss-gls-app image.
An optional parameter, imagePullSecrets, can be added to this file in case Docker repository authentication is required.
configs/prop.json
Copy the helm folder from wss-deployment to your target environment. Inside the helm/configs folder, add the configuration properties JSON file (prop.json) that you previously edited and exported using the Configuration Editor.
templates/config.yaml
This is a configuration file pointing to the configs/prop.json file.
NOTE: Do not edit this file.
templates/wssScmIntegration.yaml
This is a configuration file containing all the parameters for deploying the integration.
NOTE: In this file, there are 3 dashes ("- - - ") that separate the services Do not remove them.
For the webhook URL to be accessible publicly by the integration, a load balancer service must be added to the file. An example of such a service is provided below:
apiVersion: v1
kind: Service
metadata:
name: lb1
namespace: acme
annotations:
external-dns.alpha.kubernetes.io/hostname: helm.acme.io
service.beta.kubernetes.io/aws-load-balancer-backend-protocol: http
service.beta.kubernetes.io/aws-load-balancer-ssl-ports: "443"
service.beta.kubernetes.io/aws-load-balancer-ssl-negotiation-policy: "ELBSecurityPolicy-TLS-1-2-2017-01"
service.beta.kubernetes.io/aws-load-balancer-ssl-cert: arn:aws:acm:us-east-7:834027593108:certificate/4720e07a-a231-4fd5-9c4a-12ab1450567d
spec:
type: LoadBalancer
ports:
- port: 443
name: https
targetPort: 5678
selector:
app: wss-controllerSelecting Repositories to Scan
If you are integrating multiple repositories and want to apply global configurations, refer here before continuing in this procedure.
Add the @Mend user (the user you created during Creating a New GitLab User and a Personal Access Token) as a member with Maintainer permissions to the repositories you want Mend to scan. This is how Mend will determine which repositories will be scanned.
If you would like Mend for GitLab to scan an entire GitLab group, add the @mend user to the group to enable Mend for GitLab for all of the projects within that group.
Note: Adding the @mend user to a repository with any permissions less than Maintainer may create side effects in the integration's functionality.Unless specified otherwise via the global configuration, an onboarding merge request is created for each repository to which the @mend user was added. This request contains a mend configuration file (.whitesource) that can be customized before merging the request. The initial PR must be merged with the base branch first. This will then initiate the installation and start the first scan. You can then define further settings (like selected branches) in the .whitesource file.
To disable scanning for a repository, remove the @mend user from the repository members.
Accessing Scan Statistics via API
See here for more information.
Health Check APIs
See here for more information.
The .whitesource File
A Mend configuration file (.whitesource) is a JSON file added to each repository enabled for scanning. It provides configurable parameters for the Mend scan. The .whitesource file is only added in the default branch of the repository (unless modified, it is the master branch).
Note: For self-managed GitLab.com instances with a global configuration, it is mandatory to set the includedOwners property in the global-config.json, with a list of the GitLab.com groups you wish to include in the integration.
This step can only be skipped if there is no global configuration (i.e., you only have a .whitesource config file per repo, with no global-config.json overlooking it).
CODE
|
Python Support
If you want to specify the Python version for your repository, you can choose one of the following versions included in your scanner Dockerfile: 2.7.18, 3.6.15, 3.7.12, 3.8.12, 3.9.9, or 3.11. For this, you will need to perform the following procedure:
Ensure the relevant Python version is uncommented in your scanner container’s Dockerfile.
Add or edit the .whitesource configuration file in your repository.
Use the
configModeparameter and set it to eitherLOCALorEXTERNAL.Create a whitesource.config file and add the following:
CODEpython.invokePipAsModule=true python.path=python3.9 python.installVirtualenv=true
Note:
For
python.path, use one of the following values:2.7,3.6,3.7,3.8,3.9,or3.11.Alternatively, you can apply this globally across your repositories by using the Global Repo Configuration repo-config.json file.
Parameters
Global Settings
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
settingsInheritedFrom | String | When the global configuration is enabled, this parameter will specify the location of the whitesource-config repository from which it will inherit its configuration. It must contain the GitLab user name, repository name, and branch (optional) of the repo-config.json file location. The default branch is 'master', but can be modified according to the location of the repo-config.json file in the whitesource-config repo. Note: You can override specific parameters that are relevant only in the specific repository by adding these after this parameter. Parameters with the type of array do not override the value from the global configuration but only add new values. Examples: Using only values defined in the global configuration:
CODE
Using values defined in the global configuration and overriding the scan settings parameters:
CODE
| No | N/A |
overrideConfigAllowList | Array | When the global configuration is enabled, this parameter will regulate the ability of repositories that inherit their configuration from the whitesource-config repository to override the parameters locally. There are three options:
Note: This parameter must be used in the repo-config.json file of the whitesource-config repository. | No | null |
Scan Settings (scanSettings)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
configMode | String | The configuration mode is to be used for each scan. There are three options:
Note: whitesource.config can be provided both in the global config and in the repo itself. If it is provided in both places and some parameters are set on both levels - the repo level will take precedence. | No | Auto |
configExternalURL | String | The URL of the external configuration file (you can choose any filename). The configuration file content should be in the same format as the Unified Agent configuration file. The following protocols are supported: 'ftp://', 'http://', 'https://'. For example: 'https://<mydomain.com>/whitesource-settings/wss-unified-agent.config' Notes:
| No | Empty |
projectToken | String | Adds the ability to map a GitLab repository to a Mend project. The parameter used needs to be the Mend project token. Note: Not supported in the Global Configuration. | No | Empty |
baseBranches | Array | Adds the ability to specify one or more base branches for which scanning results will be sent to a new Mend project. Example usage: ["master", “integration"] This will set both master and integration branches as base branches. Note the following:
Note: This parameter is available only from version 20.7.1. | No | Empty In this case, the base branch only consists of the default branch. |
enableLicenseViolations | Boolean | When enabled, a new Mend License Check will be generated for each valid push. Notes:
| No | false |
enableIaC | Boolean | When enabled, a new Mend IaC Check will be generated for each valid push. This will scan cloud infrastructure configurations to find misconfigurations before they are deployed, and alert on these via the creation of a Work item. Notes:
| No | false |
javaVersion | String | Defines the version of Java in the Scanner. Available values are listed in the support matrix under “Java”. Note: For any projects that are using Gradle versions before v7.3, we recommend setting your Java version used by the integration to one of the lower supported versions, 8 or 11, via the | No |
|
cloneSubmodules | Boolean | If set to Notes:
| No | false |
repoNameSync | Boolean | When set to | No | false |
skipScanningStage | Object | Controls what stages of the scanning process will be skipped for specific package managers. The available parameters are:
All package managers for which a pre-step is available can be specified, e.g., Usage example:
CODE
| No | none |
exploitability | Boolean | When set to Additional information about exploitability is available in the designated Public Exploits page. | No | false |
uaConfigMergeSetting | String | Possible values: Note: All other UA settings are always overridden on a local level. | No | OVERRIDE |
Commit Status Settings (commitStatusSettings)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
displayMode | String | How to display Mend security information for a scan performed on a non-base branch:
| No | diff |
enableNeutralCommitStatus | Boolean | Controls the behavior for neutral checks, The available values are:
| No | true |
enableNeutralCommitComment | Boolean | Controls, whether commit comments for neutral commits, are going to be enabled or disabled. If set to | No | true |
vulnerableCommitStatus | String | Customizable commit status settings.
| No | FAILED |
licenseCommitStatus | String | Customizable commit status settings. Note: The license check is dependent on the vulnerabilities check and will not be triggered if vulnerableCommitStatus is set to none.
| No | FAILED |
iacCommitStatus | String | Customizable commit status settings.
Note: When an IaC issue is closed it will not be detected in future scans. | No | FAILED |
showWsInfo | Boolean | Whether to show additional Mend information such as the project token inside the Mend Commit Status (after the scan token). Mend information is only displayed if the commit originated from a base branch. The following hidden JSON object will also be added inside the Commit Status when this parameter is enabled:
CODE
Note: Additional Mend data may be added inside the JSON object in the future. | No | false |
useMendStatusNames | Boolean | If set to Note: When .whitesource is created the value of useMendCheckNames is | No | false |
strictMode | String | Controls the messaging and status of security and license checks in the case of partial scan results (i.e. Mend Scanner experienced issues pulling some of the project’s dependencies during the scan). The available parameter values are:
Note: For strictMode to work, the vulnerableCheckRunConclusionLevel and licenseCheckRunConclusionLevel parameters must be set to | No |
|
strictModeInfo | Boolean | Controls the inclusion of INFO logs in the Scan Details report.
| No |
|
Issue Settings (issueSettings)
NOTE: Starting with the release of version 22.12.1 (January 2nd, 2022), to take advantage of the Critical label for vulnerabilities for existing Issues created by our repo integration, a new scan must be triggered on the repository. If a scan has not been triggered after upgrading to this version, the repo will continue to only show the previous three labels (High, Medium, Low) for existing Issues. For more information on the Critical setting, please visit our documentation here.
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
minSeverityLevel | String | Enables users to decide whether to open a new Issue only if a certain severity level is available on a detected vulnerability. Available values for minSeverityLevel:
Notes:
| No | LOW |
minVulnerabilityScore | String | Enables users to define issue creation based on a specified minimum vulnerability CVSS score. Allowed values - floats with one decimal from 0 to 10. For more information on CVSS 3 Scores, click here. Notes:
| No | 0 |
maxVulnerabilityScore | String | Enables users to define issue creation based on a specified maximum vulnerability CVSS score. Allowed values - floats with one decimal from 0 to 10. For more information on CVSS 3 Scores, click here. Notes:
| No | 10 |
openConfidentialIssues | Boolean | Whether the GitLab issues opened by Mend will be confidential. | No | true |
displayLicenseViolations | Boolean | Whether to generate an Issue for every detected license policy violation. Note: This parameter is relevant only if enableLicenseViolations (scanSettings) is set to true. | No | true (only if enableLicenseViolations (scanSettings) is set to true) |
iacIssues | Boolean | Whether to generate issues for IaC findings. The available values are:
Note: This parameter is relevant only if the IaC scan is enabled by setting scanSettings.enableIaC to | No |
|
issueType | String | Defines the type of issue that will be created in the repository: VULNERABILITY (one for each vulnerability) or DEPENDENCY (one for each direct dependency). | No | DEPENDENCY |
customLabels | Array | Setting that will define labels that will be added to the issues created after the scan. Usage example:
CODE
The following labels are not available for use:
| No | Empty |
Remediate Settings (remediateSettings)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
enableRenovate | Boolean | When enabled, Remediate will raise automated Merge Requests for outdated dependencies in addition to Merge Requests remediating vulnerable dependencies. Remediate will then perform all the functionality and support all the configuration options available in Mend Renovate. See Renovate configuration options for all configuration options. Refer here for parameter usage. | No | false |
workflowRules | Object | This parameter is used to specify the rules that regulate when to open remediation pull requests. Usage examples:
CODE
| Yes |
CODE
|
workflowRules.enabled | Boolean | Enables Workflow Rules to be set from a .whitesource file. Note: workflow rules can also be set in the Mend application in the Admin → Integration Workflow Rules. But if this parameter is set to | Yes | true |
workflowRules.minVulnerabilitySeverity | String | The minimal vulnerability severity level to automatically create remediation pull requests for. Allowed values - E.g. if set to Note: if this parameter is used together with minVulnerabilityScore and maxVulnerabilityScore then only minVulnerabilitySeverity will have effect. | No | LOW |
workflowRules.minVulnerabilityScore | Float | The minimal vulnerability CVSS 3 score to automatically create remediation pull requests for. Allowed values - floats with one decimal from 0 to 10. For more information on CVSS 3 Scores, click here. Note: if this parameter is used together with minVulnerabilitySeverity it will not have any effect. | No | 0 |
workflowRules.maxVulnerabilityScore | Float | The maximal vulnerability CVSS 3 score to automatically create remediation pull requests for. Allowed values - floats with one decimal from 0 to 10. For more information on CVSS 3 Scores, click here. Note: if this parameter is used together with minVulnerabilitySeverity it will not have any effect. | No | 10 |
Private Registry Settings (hostRules)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
matchHost | String | Defines where the credentials will be applied during the scan. More details.
| No | Empty |
hostType | String | Type of private registry. Supported values: Required if Note: When using Renovate with a Ruby private registry, add a | No | Empty |
userName | String | Used when credentials require a username. | No | Empty |
encrypted.password | String | Used when credentials require a password. For more information on setting up hostRules encryption, please visit the Handling Private Registries and Authenticated Repositories section. An encrypted secret that will be applied as a credential to the host set in the
JSON
| No | Empty |
encrypted.token | String | Used when credentials require a token. For more information on setting up hostRules encryption, please visit the Handling Private Registries and Authenticated Repositories section. An encrypted secret that will be applied as a credential to the host set in the
JSON
| No | Empty |
envVariablesMapping | Object | Use this parameter if you used environmental variables in the settings of your package manager to include username and password/token (e.g. for a specified package index).
CODE
or
CODE
Then, set
CODE
| No | Empty |
sourceName | String | This parameter is relevant only for Pipenv private registries. Use this parameter if you don’t have a specified package index, in this case, Mend will create one for you based on other parameters of hostRules. The value of sourceName should be an index name used for your private packages. For example, if you have packages with such index
CODE
Then set sourceName to
CODE
| No | Empty |
Providing a Global Configuration File
NOTE: Supported from version 20.5.1.3 only.
You can provide a custom .whitesource configuration file as part of the wss-gls-app container, to apply it globally to all of your organization's repositories. Doing so will apply the file to all onboarding pull requests for newly selected repos. Repos that were already selected and activated before this change will not be affected by this global configuration. Only newly onboarded repos will be affected.
To apply this global change, do as follows:
Stop the wss-gls-app container.
In the "wss-gls-app/conf" folder, add your custom “.whitesource” file (where the prop.json file is located).
Start the wss-gls-app container.
Configuration Error Issues
Will alert the user on configuration errors that affects their scan by creating a configuration error issue and commit status. In case of such an error the following will occur:
Stop the workflow. Do not create a scan or the Mend Security commit status.
Create a “Configuration Failed” commit status.
For each config file that failed parsing - create a new type of issue, titled Action Required: Fix Mend Configuration File - {fileName}. If the error originated from the repo-config.json or global-config.json files, then the issue will be created in the whitesource-config repo.
Handled errors:
Error parsing the configuration files (.whitesource/repo-config.json/global-config.json json)
Missing repository and/or branch in the inheritance configuration
Handling Private Registries and Authenticated Repositories
Private registries hosted on any platform that can be accessed with credentials are supported (Nexus, GitHub, Artifactory, Azure Artifacts, GitLab, NPM)
Supported languages and package managers:
NPM
Yarn
Maven
Gradle
Pip
Pipenv
Go
Nuget
Ruby
SBT
To scan dependencies from private registries and authenticated repositories, Mend must be provided with credentials, such as an NPM token. These credentials must be added as encrypted secrets to the .whitesource file, either per-repository or in the shared global config if the secret scope is org-wide.
Сreate the encrypted secrets. Each secret you encrypt must be scoped to a GitLab group or repository and use of it will be restricted to those within the app.
Note: Decryption is only available for 2048-bit gpg keys. Any other key size will result in an error.
Use GPG to generate a PGP Key. Use the command
gpg --full-generate-keyand follow the prompts to generate a key. Please note that at this time we do not support using a passphrase for decryption, so it is best to generate the keys without a passphrase. Name and email are not important.Copy the key ID from the output or run
gpg --list-secret-keysif you forgot to take a copy. This is your public key.Run
gpg --armor --export-secret-keys YOUR_NEW_KEY_ID > ws-private-key.ascto generate an armored (text-based) private key fileRun
gpg --armor --export YOUR_NEW_KEY_ID > ws-public-key.ascto generate an armored (text-based) public key file
Provide the private key to the Controller, Remediate, and Scanner with environmental variables (learn more about environmental variables in the Advanced Technical Information documentation). There are two options for how to do it, but only one option should be used.
WS_HOST_RULES_PRIVATE_KEY- the value of the private key itself.Please note, that the private key should be formatted to work properly:
Remove the beginning and end comments (as well as any extra lines).
At the end of the key, remove the buffer text. It is usually 5 characters long and looks like the example below:
Remove all of the new lines in the key so it is all in one line (i.e. delete all
\ncharacters).
WS_HOST_RULES_PRIVATE_KEY_FILE_PATH- path to the file containing the private key. This file should be mapped to the running containers.
Open wss-encryption/secret-encryption.html in your favorite editor.
Find and replace the text "COPY_YOUR_PUBLIC_PGP_KEY_HERE" with your newly generated public key and save the file.
const publicKeyString = `COPY_YOUR_PUBLIC_PGP_KEY_HERE`;Generate a secret. There are the following fields on the encryption page:
Organization\Group - required, your Gitlab group to which tokens secret be scoped.
Repository - optional, your Gitlab repository to which the secret should be scoped.
Raw value - required, confidential values/secrets such as tokens or passwords.
Encrypted value - the result of the encryption to be used in the integration.
After the secret is created, please add it to the hostRules parameter of the .whitesource file.
Example of hostRules:
{
"hostRules": [
{
"matchHost": "registry.npmjs.org",
"hostType": "npm",
"userName": "bot1",
"encrypted": {
"token": "3f832f2983yf89hsd98ahadsjfasdfjaslf............"
}
},
{
"matchHost": "https://custom.registry.company.com/maven/",
"hostType": "maven",
"userName": "bot1",
"encrypted": {
"password": "p278djfdsi9832jnfdshufwji2r389fdskj........."
}
}
]
}Additional notes
Copy the entire output of the key generator including comments to paste into the string.
i.e., include "-----BEGIN PGP PUBLIC KEY BLOCK-----..."
The string uses JavaScript backticks and not quotes. This is to allow a multi-line string so that you do not have to replace any line breaks with new-line characters. Be aware of any auto indenting by your editor that may introduce spaces to the public key and cause encryption to fail.
We use asymmetric public-key cryptography of the PGP methodology. Organization/Group, Repository, Raw Value - all information you provide on the encryption page is secured with this approach.
Notes for NPM private registries:
To connect to private registries the .npmrc file of the scanned project is used. It is either edited (
hostRulesfrom the config are applied) or created for scanning purposes.If .npmrc is missing and only one host is used in the project it should be connected to the official http://npmjs.com . Otherwise, only private dependencies will be scanned and all public dependencies of this registry will be omitted.
If several hosts are used in the project it is required that .npmrc file exists in the project and contains information about these hosts.
Notes for Yarn private registries:
For Yarn 1 projects, to connect to private registries the .npmrc file of the scanned project is used. For Yarn 2/3 .yarnrc is used. It is either edited (
hostRulesfrom the config are applied) or created for scanning purposes.If .yarnrc is missing (or
npmRegistryServerin it is not set) and only one host is used in the project - it will be set to thehostRules.matchHostfrom the config. In the same case, if several hosts are used,npmRegistryServerwill be set to https://registry.yarnpkg.com.
Notes for Maven private registries:
To connect to private registries the settings.xml file of the scanned project is used. It is either edited (
hostRulesfrom the config are applied) or created for scanning purposes.
Notes for Gradle private registries:
To connect to private registries the build.gradle or settings.gradle file of the scanned project is used. For both of these files, we also support the kotlin (.kts) format.
The buildscript or pluginManagement blocks need to be at the beginning of the
build.gradleorsettings.gradlerespectively.matchHostshould contain the full path to the private registries, not just the domain.
Notes for Nuget private registries:
To connect to private registries the NuGet.Config file of the scanned project is used. It is either edited (
hostRulesfrom the config are applied) or created for scanning purposes.
Notes for Pip private registries:
Certain special characters are not valid in the credential part of a URL. If the user or password part of the login credentials contains any of these special characters then they must be percent-encoded.
Notes for Pipenv private registries:
Use either envVariablesMapping or sourceName when setting host rules.
Notes for Go private registries:
To connect to private registries the .netrc file of the scanned project is used. It is either edited (
hostRulesfrom the config are applied) or created for scanning purposes.Only HTTPS is available for
matchHost, HTTP is not supported.If the private registry is hosted on GitHub, only
tokencan be used in theencrypted(i.e.,passwordis not supported).
Automate Secret Encryption for Private Registries
You can encrypt secrets from the CLI, using the curl, echo, jq, gpg, grep and tr CLI programs.
Here is an example:
curl https://app.renovatebot.com/renovate.pgp --output renovate.pgp
echo -n '{"o":"your-organization", "r":"your-repository (optional)", "v":"your-secret-value"}' | jq . -c | gpg --encrypt -a --recipient-file renovate.pgp | grep -v '^----' | tr -d '\n'
The above script uses:
curlto download the Mend Renovate hosted app's public keyechoto echo a JSON object intojqjqto validate the JSON and then compact itgpgto encrypt the contentsgrepandtrto extract the encrypted payload which we will use
The jq step is optional, you can leave it out if you wish. Its primary value is validating that the string you echo to gpg is valid JSON and compact.
Note: Encrypted secrets must have at least an org/group scope, and optionally a repository scope. This means that Renovate will check if a secret's scope matches the current repository before applying it, and warn/discard if there is a mismatch.
Encrypted secrets usually have a single organization. But you may encrypt a secret with more than one organization, for example, org1,org2. This way the secret can be used in both the org1 and org2 organizations.
For more information on how to use secrets for private packages, refer to the Private package support documentation.
