Public Exploits in Mend SCA
Overview
This feature enhances the security of your software, exposing known public exploits in detected open-source vulnerabilities within the Mend Legacy SCA application. By proactively identifying and highlighting vulnerabilities that have public exploits, we empower users to take immediate action and prioritize the necessary remediation efforts.
Further reading that will help you get acquainted with public exploits.
Getting it done
Prerequisites before getting started with Public Exploits
UI - Access to the Mend Legacy SCA application is required
API 2.0 - Permissions to execute the following API calls: Get Product Security Alerts / Get Project Security Alerts / Get Product Library Vulnerabilities / Get Project Library Vulnerabilities
API 1.3/1.4 - Permissions to execute the following API calls: getProjectAlertsByType / getProductAlertsByType / getOrganizationAlertsByType
Viewing Public Exploits in the Legacy SCA UI
A known exploit will be displayed only when the Exploit Code Maturity is "Proof of Concept" or higher ("Proof of concept” / "Functional" / "High").
The exploitability information will be presented in the following screens in the Legacy SCA UI:
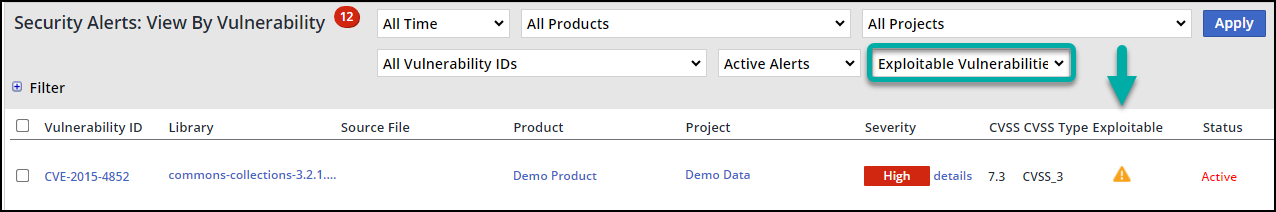
Alerts View by Vulnerability:
You should be able to see a new column named "Exploitable”. If there is a related exploit, the exploitability icon will be displayed.
There’s also a new filter under "Security Alerts: View by Vulnerability" called "Exploitable Vulnerabilities". This option will display alerts with known exploits.
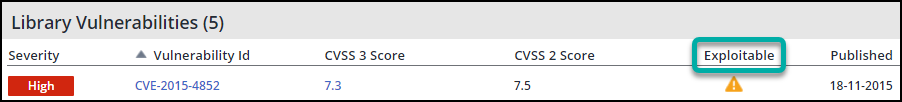
Library Page:
On the library page, under the “Library Vulnerabilities” section, you should see a new column named “Exploitable”.
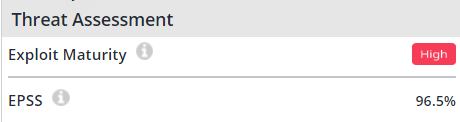
Vulnerability Page:
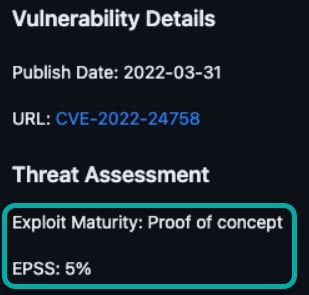
On the vulnerability page, the exploit maturity and EPSS scores are visible under the “Threat Assessment” section.
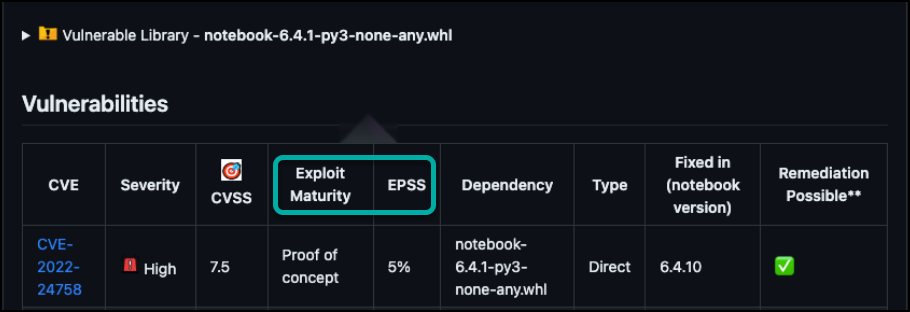
When a related exploit exists, there will be an exploitability icon next to the vulnerability ID to indicate its presence.
We introduced a new section titled "Threat Assessment" on the Vulnerability page. This section will display the following parameters:
Exploit Code Maturity: Options include "Not defined," "Unproven," "Proof of concept," "Functional," and "High."-
Proof-of-concept- exploit code is accessible, or a practical attack demonstration is challenging for many systems. The code or technique may not be functional in all scenarios and could demand significant alteration by a skilled attacker.
Functional- The code works in most situations where the vulnerability exists.
High- Functional autonomous code exists, or no manual exploit is needed (automatic activation), and information is widely accessible. Code functions universally, or it's being spread by self-operating agents like worms or viruses. Network-linked systems will probably face scanning or attacks. Exploit creation is advanced with dependable, widely available, user-friendly automation tools.
EPSS (%)
Public Exploits in the Mend API
API 2.0
2 parameters, exploitCodeMaturity and epssPercentage, have been added to the 4 API calls listed below:
API Call | Added Parameter 1 | Added Parameter 2 |
|---|---|---|
Get Product Security Alerts |
|
|
Get Project Security Alerts |
|
|
Get Product Library Vulnerabilities |
|
|
Get Project Library Vulnerabilities |
|
|
More information about these API calls is available in the Mend API 2.0 documentation.
API 1.3/1.4
2 parameters, exploitCodeMaturity and epssPercentage, have been added to the 3 API calls listed below:
API Call | Added Parameter 1 | Added Parameter 2 |
|---|---|---|
|
|
|
|
|
|
|
|
|
The 2 parameters will only be returned when the specified alert is of type SECURITY_VULNERABILITY.
They will show up in the response under the CVE’s “threatAssessment” section.
Example:
{
"requestType": "getProjectAlertsByType",
"userKey": "xxx",
"alertType": "SECURITY_VULNERABILITY",
"projectToken": "xxx",
"fromDate": "2023-09-01",
"toDate": "2023-12-31"
} Response:
"vulnerability": {
"name": "CVE-2015-4852",
"type": "CVE",
"severity": "high",
...
"threatAssessment": {
"exploitCodeMaturity": "HIGH",
"epssPercentage": 96.5More information about these API calls is available in the Mend API 1.3/1.4 documentation, here.
Public Exploits in the Mend Repo Integrations
The Public Exploits data can also be toggled in the repo integration, by adding "exploitability": true to the scanSettings section of the .whitesource config file
If
scanSettings.exploitabilityis set totrueand the vulnerability has exploitability data → this will be reflected in the issues and security checkIf
scanSettings.exploitabilityis set totrueand the vulnerability has no exploitability data → no threat assessment information will be displayed for the vulnerability in the table and the “Threat Assessment” section shouldn’t be in the details
Example:
{
"scanSettings": {
"configMode": "AUTO",
"enableLicenseViolations": true,
"baseBranches": [],
"exploitability": true
},More information about the repo integrations is available here.
Reference
More information about exploitability is available here.
