Global Repo Configuration
Note: This feature is only available from version 20.7.1.
Overview
This topic provides instructions on how to enable a global repo configuration which will affect all new repositories to be integrated using either Mend for GitHub.com, Mend for GitHub Enterprise, Mend for Bitbucket Server/Data Center, Mend for Bitbucket Cloud, Mend for GitLab Server, or Mend for Azure Repos. For information on how to migrate existing repositories to the global configuration, see here. Using this global configuration, you will be able to define a configuration template file (repo-config.json), which can be inherited by all future integrated repositories. You will also be able to define a global configuration (not specific to a repository) file (global-config.json) for your integration. The currently supported global configuration enables you to define how the user onboarding flow will occur for your integrated repositories.
Prerequisites
Ensure that you have already integrated the relevant repository platform with Mend.io. If needed, refer to the installation sections of the relevant repo integration.
Enabling the Global Configuration
(Only for Self-Hosted integrations) Create a new organization (GitHub Enterprise), Group (Gitlab Server), and Project (Bitbucket Server/Data Center) named whitesource-config (the name must be exactly as specified here) in your integrated repository platform.
(Only for AzureRepos) This integration is using Global Configuration by default so just follow the installation steps of the Mend for Azure Repos documentation.
Create a new repository named whitesource-config (the name must be exactly as specified here). In Self-Hosted integrations, this repository needs to be inside the whitesource-config entity you created in the previous step.
Add the new whitesource-config repository to your integration. Based on your relevant platform, refer to the correct section:
The whitesource-config repository will now contain a README file and two new configuration files (automatically created by the integration), repo-config.json and global-config.json. Configure these files by referring to the following sections and then continue in this procedure.
Add repositories you want Mend to scan, to your integration.
NOTE: whitesource-config repository does not support changes to the configuration files done via pull requests, any edits must be committed directly to the default branch of the repository. Because of this branch protection rules should not be applied to the whitesource-config repository.
repo-config.json
This configuration template file is a JSON formatted file that will be applied globally to each newly selected integrated repository. It provides configurable parameters for a Mend scan. All new integrated repositories will inherit the configuration set in this file unless explicitly overridden by a local .whitesource file in the relevant repository. Refer to the following sections for information on which parameters can be added to the repo-config.json file:
Parameters that can be used only in repo-config.json
Note: The parameters below are exclusive to the repo-config.json file. The configuration parameters of the .whitesource file can be applied in the repo-config.json as well, but to be used globally.
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
overrideConfigAllowList | Array | If global configuration is enabled, this parameter will regulate the ability of repositories that inherit their configuration from the whitesource-config repository to override the parameters locally. There are three options:
| No | overrideConfigAllowList |
global-config.json
This global configuration file is a JSON-formatted file where you can define global configurations for the integration. The following parameters can be provided:
global-config.json - General Parameters
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
repoConfigMode | String | The configuration mode to be used on all integrated repositories. There are three options:
Note: If the pushwhitesourceFile parameter is set, please ensure there are no policies set on the default branch. For example, a default branch that only accepts changes to be made via a pull request. As this is a push update, such a policy will block onboarding.
Note: If the nowhitesourceFile parameter is set, the existing repositories that Mend has access to require a valid commit before scanning will continue. Newly created repositories that Mend has access to will automatically start the initial scan (versus waiting for the onboarding PR to be merged when createOnboardingPR is set). | Yes | createOnboardingPR |
repoConfigFileName | String | It is possible to rename the .whitesource configuration file added to an integrated repository. Notes:
| No | .whitesource |
branchProtectionRule | Automatically create a “Mend Security Check” branch protection rule for all branches configured by the “baseBranches” property. This will only occur for newly onboarded repositories. Notes:
CODE
| No | “none” | |
settingsInheritedFrom | Add an option for a regular account repo-config.json or global-config.json file to inherit settings from the whitesource-config account’s global-config.json file. For example, a global-config.json file in {someOrg}/whitesource-config could inherit settings from the whitesource-config/whitesource-config file. If this parameter is enabled, after creating a whitesource-config file inside the repos of the given organization, it will be automatically populated with the settings from the whitesource-config/whitesource-config file. Note: Examples: Using only values defined in the global configuration:
CODE
Using values defined in the global configuration and overriding the scan settings parameters:
CODE
| No | “none” | |
enableCustomProductMapping | Boolean | If set to Notes:
| No | False |
ignoreSpecificVulnerabilities | Boolean | When set to Format of ignored-vulnerabilities.txt: list CVE, WS or MSC IDs separated by a new line. Example:
CODE
Notes:
| No | False |
overrideConfigAllowList | Array | Regulate the ability of repositories that inherit their configuration from the whitesource-config repository to override the parameters locally. There are three options:
Notes:
| No |
|
global-config.json - Ignored Repos (ignoredRepos)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
exactNames | Array | Provide a list of specific repositories to ignore from the integration. For example: GitHub.com:
CODE
Azure Repos:
CODE
| No | Empty |
global-config.json - Included Repos (includedRepos)
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
exactNames | Array | Provide a list of specific repositories that will be onboarded. For example:
CODE
NOTES:
| No | Empty |
global-config.json - Account Management
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
includedOwners->exactNames | Array | Define a whitelist of GitHub Organizations and/or GitHub repository owners that can integrate with the Mend integration. For example:
CODE
NOTES:
| No | Empty |
allowedUserAccounts->exactNames | Array | Provide a way to limit the integration to organization accounts and block all or specific user accounts. If the When a blocked account is trying to install the integration, it will be automatically uninstalled. NOTE: Only valid for the GitHub Enterprise integration.
CODE
| No | Null |
global-config.json - Azure Repos (azureReposSettings)
NOTE: When the configuration for the workitemType or customFields parameters is changed, all Mend-created work items will be updated after a valid push in the repository.
Parameter | Type | Description | Required | Default |
|---|---|---|---|---|
workItemType | String | This parameter specifies the type of work item to be created for all Mend work items. Set this parameter to a string equal to the name of a work item type in your project. NOTES:
| No | Depends on the process type:
|
customFields | Object | This parameter specifies custom fields to be added to all Mend work items. If a field with a matching name exists in the work item template and the value is a compatible data type, it will be added to the work item. Example of use:
CODE
NOTES:
| No | None |
Manually Triggering Repository Scans
This feature enables users to manually trigger SCA or SAST scans for specific repositories.
To trigger the manual scans, a file called scan.json needs to be pushed to the whitesource-config repo. The scan.json file contains a list of repositories to scan.
NOTES:
Manually triggering SAST scans is currently supported by Mend for GitHub.com only.
The repository list is limited to 10. If there are more than 10, no repositories will be scanned, and a check run will be created.
The default value can be changed for Self-Hosted integrations. See Advanced Technical Information environment variables for more information.
If a branch name is not specified, the default branch will be scanned.
For each repository in the list, a scan will be triggered (in the latest commit of the specified branch), including the creation of the security check run.
Manually trigger SCA repository scans
To trigger a manual SCA scan for a defined repository, push a scan.json file to the whitesource-config global configuration repo with the following settings:
{
"repositories": [
{
"fullName": "orgName1/repoName1",
"branchName": "main",
"scanType": "sca"
}
]
}Manually trigger SAST repository scans
NOTE: Manually triggering SAST scans is currently supported by Mend for GitHub.com only.
To trigger a manual SAST scan for a defined repository, push a scan.json file to the whitesource-config global configuration repo with the settings provided in the example below. Please note that the scanType parameter must be included and set to sast to trigger the SAST repository scan:
{
"repositories": [
{
"fullName": "org-name/repo-name",
"branchName": "main",
"scanType": "sast"
}
]
}Manual scan logs
When triggering a manual scan, it is possible to save the scan logs as a single zip file to a dedicated repository. To review the logs, perform the following steps:
Create a dedicated repository for the logs:
Mend for GitHub Enterprise - Create a
ws-logsrepository under your whitesource-config organizationMend for GitHub.com - Create a
ws-logsrepository in your organization
Add the
ws-logsrepository you created to the Mend integration. Based on your relevant platform, please refer to the correct section:Add the following parameter to the scan.json file;
uploadScannerLogs, and set it to true.
Example:
{
"repositories": [
{
"fullName": "orgName1/repoName1",
"branchName": "main",
"uploadScannerLogs": true
}
]
}NOTES:
Name of the zip file: scanner_logs_{SCAN_TOKEN}.zip
(only for self-hosted) The name of the
ws-logsrepo is configurable using the environment variable:WS_LOG_REPO_NAMEIf the
ws-logsrepository does not exist, the manual scan will not run and a check run will explain why: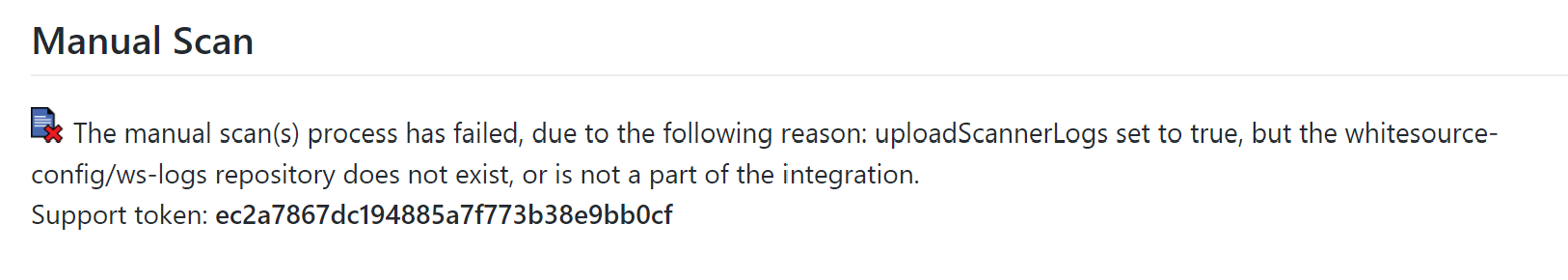
Migrating Existing Repositories to the Global Configuration
NOTE: Performing a migration may slow down the overall responsiveness of the integration. Migration may take a few hours to complete.
For GitHub integrations, when performing a migration on more than 500 repositories, the migration Check Run indicating the status of the migration may not be created due to a GitHub content size limitation.
If you have existing repositories that you want to inherit from the global configuration, do as follows:
Ensure you performed the steps described in Enabling the Global Configuration.
Go to the whitesource-config repository.
Add a new file named migration.json in the default branch.
Inside the file, add the following content (to change parameters and values, refer to the table below):
CODE{ "migrationMode": { "changeType": "inheritance", "openPR": true } }To run the migration, commit and push the file.
A Mend Security Check (as part of a Check Run for GitHub.com/GitHub Enterprise, Commit Status for GitLab, and Build Status for Bitbucket Server) will be generated and display a summary of the migrated repositories. In addition, the migration.json file will be deleted after the migration is completed.
NOTE: In Mend for Bitbucket Server, the migration.json file needs to be manually removed.
NOTE: For self-hosted organizations, if the migration.json file is pushed from the global configuration repository of a global organization (whitesource-config/whitesource-config), the migration will affect all the integrated organizations. If the migration.json file is pushed from the global configuration repository of a regular organization (regular-org/whitesource-config), the migration will affect only the repositories from this organization.
migration.json File Parameters
Parameter | Type | Description | Required? | Default |
|---|---|---|---|---|
migrationMode.changeType | String | Type of change to perform as part of the migration. There are three possible values:
| No | inheritance |
migrationMode.openPR migrationMode.openMR | Boolean | Whether an onboarding PR/MR should be created for the migrating repositories. NOTE: When set to false, every migrating repository that currently contains a .whitesource file will trigger an automatic scan after these are migrated. This may affect overall performance of the integration depending on how many migrating repositories you have. | No | true |
migrationMode.triggerScan | Boolean | Control whether the migration should trigger a scan after completion. NOTE: This parameter is relevant only when using migrationMode.changeType=inheritance. | No | true |
includeRepos | Array | Provide a list of specific full repository names (organization/repo_name) on which the migration should run. Organization is a GitHub term and each source control manager has an equivalent term that should be used in place of organization. Azure DevOps(project), Bitbucket(workspace), GitLab(group), GitHub(organization) Example:
CODE
NOTES:
| No | Empty |
excludeRepos | Array | Provide a list of specific full repository names (owner/repo_name) on which the migration should not run. Example:
CODE
NOTES:
| No | Empty |
Examples of the migration.json
Below are a few examples of what a migration.json would be like in an environment. Some items to keep in mind:
The includeRepos and excludeRepos settings cannot be used together in the same migration / migration.json
GitHub and Bitbucket use the openPR setting, while GitLab uses the openMR setting
Example One: The complete migration.json file will look something like this for GitHub and Bitbucket using the includeRepos setting:
{
"migrationMode": {
"changeType": "inheritance",
"openPR": true
},
"includeRepos": ["organization/repo1","organization/repo2"]
}Example Two: The complete migration.json file will look something like this for GitHub and BitBucket using the excludeRepos setting:
{
"migrationMode": {
"changeType": "inheritance",
"openPR": true
},
"excludeRepos": ["organization/repo3","organization/repo4"]
}Example Three: The complete migration.json file will look something like this for GitLab using the includeRepos setting:
{
"migrationMode": {
"changeType": "inheritance",
"openMR": true
},
"includeRepos": ["group/repo1","group/repo2"]
}