Repository Integrations - Scan Flow
This article describes the steps completed in our Repository Integrations when a scan is completed on a repository.
Introduction
Mend’s Developer Integrations include products called Repository Integrations, that integrate directly into your source control management system. Our current integrations include:
When comparing scans with your Repository Integrations to a Unified Agent scan, you may notice that the Repository Integrations scans have additional steps beyond a Unified Agent scan. These integrations include the creation of issues within your source control management system, as well as the creation of fix pull requests or merge requests to resolve found vulnerabilities, which are not included in a Unified Agent scan.
Initiating a Scan
Repository Integration scans are initiated by a valid push on an onboarded repository. A valid push must meet one of the following requirements:
One of the commits in the push command added/removed a source file(s) that has an extension supported by Mend.
Refer to the Mend Languages page in order to find out whether or not a specific language and its extensions are supported.One of the commits in the push command includes an addition/modification of the package manager dependency file(s).
Refer to the list of supported dependency files to find out whether your dependency files are supported.
The webhook generated by a valid push is then sent to the Mend Controller container where it is intercepted and inserted into the persistence queue. Once the webhook is extracted from the queue, a check run is created within your repository, a Mend project is created if one does not already exist, and the scan process begins.
Unified Agent Scan is Completed on the Scanner Container
After the scan has been initiated, the Scanner container completes the Unified Agent scan using the following steps:
The Scanner clones the repository and the Mend configuration file if you are using a non-default configuration
The Scanner runs the Unified Agent scan on your cloned repository. See the article “Unified Agent - Scan Flow” for more details on this step
The update request generated by the Unified Agent scan is sent to the Mend server
The Mend Server Processes the Update Request
Once the update request is sent to the Mend server, it matches the scanned components to the relevant open-source libraries and determines whether your repository is affected by vulnerabilities.
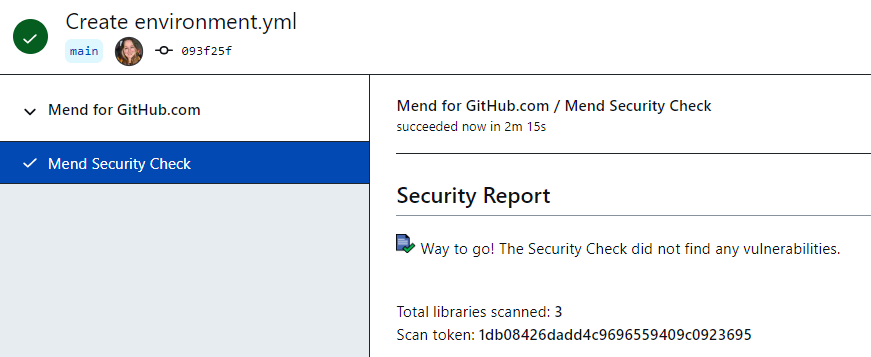
If the Mend server has finished processing the update request and no vulnerabilities were found, the check run status is set to “success”. Below is an example of a “successful” Mend Security Check on GitHub.com:
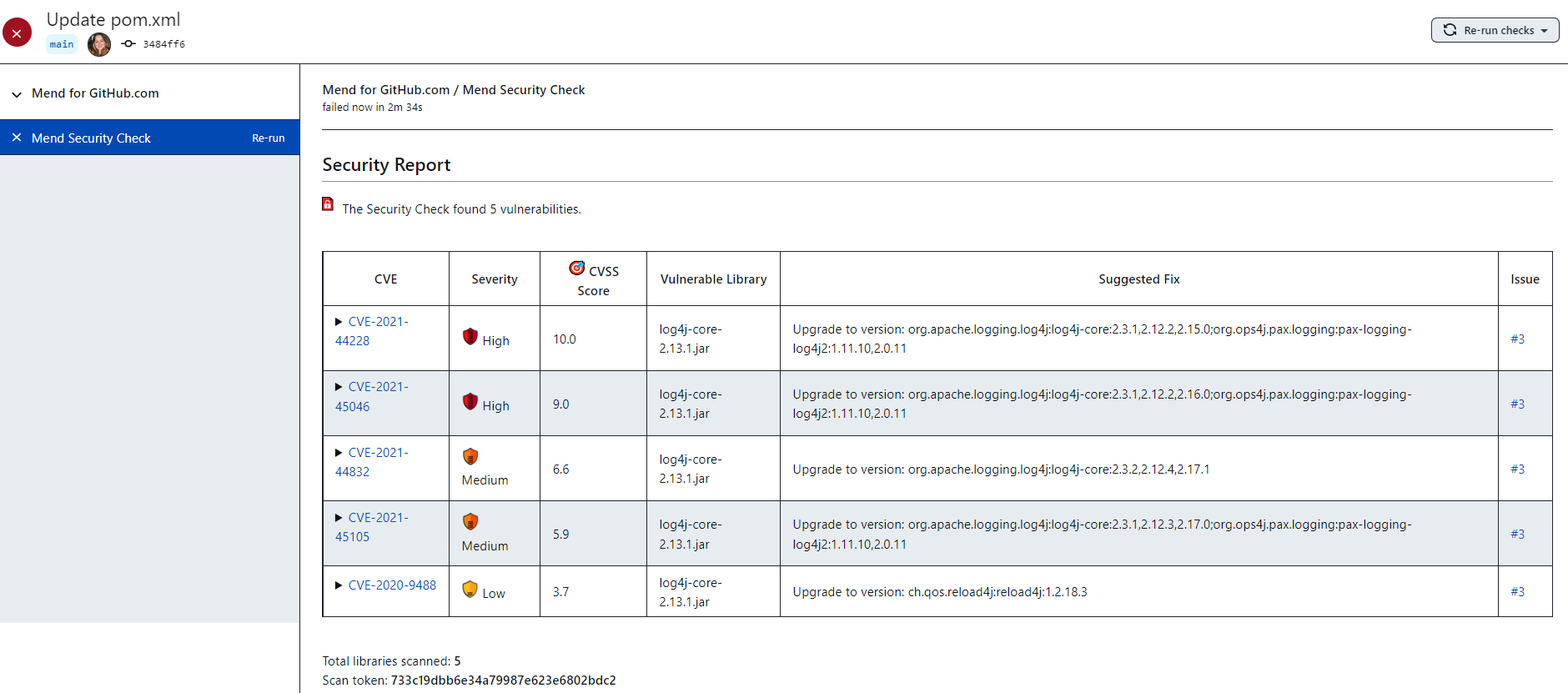
If the Mend server has finished processing the update request and vulnerabilities were found, the check run status is set to “failure” unless you have set the parameter ‘vulnerableCheckRunConclusionLevel’ to ‘success’ in your .whitesource configuration file. When ‘vulnerableCheckRunConclusionLevel’ is set to ‘success’ the check run will always finish with a status of ‘success’ regardless of whether your repository contains vulnerabilities. Below is an example of a “failed” Mend Security Check on GitHub.com:
Controller Container Opens Issues in Repository
Once the update request has been processed, for each vulnerability found in your repository, the Controller container generates an issue in your repository if one does not already exist.
Remediate Container Generates Remediation Pull Requests/Merge Requests
Once an issue is open, if the vulnerability can be remediated and a workflow rule can be matched in the Mend organization, the Remediate container generates a pull request or merge request in your repository.
Remediate will generate pull requests following the scan, as fixes are released.
