Prioritizing Findings
Overview
Scanning with Mend will provide a lot of insight into the security posture of your applications, however, processing all of the information can be overwhelming. Knowing which vulnerabilities to focus on is important for reducing your application risk. This document will provide some common guidelines for prioritizing vulnerabilities and the variety of tools Mend has to help you prioritize your findings within the Mend UI.
Addressing Critical and High Vulnerabilities
The most common place to start for new application security programs to address Critical and High vulnerabilities. These vulnerabilities are often easy for hackers to exploit and can provide an attacker with elevated privileges to the system. When addressing your critical and high vulnerabilities, you will often take out Medium and Low severities vulnerabilities with them greatly reducing the risk within your application.
Once you have addressed all/most of the Critical and High Vulnerabilities within your application, you can create an automation workflow to be alerted whenever a Critical or High vulnerability is found by a Mend scan.
To learn how to leverage the Mend UI to find your Critical and High Vulnerabilities see the documents below:
Review the top high-severity Dependency Findings within your organization
Review the top high-severity Custom-Code Security Findings within your organization
Review the Container Image Scan Findings within your Organization
While this is a good starting place for reviewing your vulnerabilities, It can still be an overwhelming task when starting out. Mend has several powerful tool that can be leveraged to further quantify the risk a vulnerability presents your organization and should be used to help prioritize your vulnerabilities.
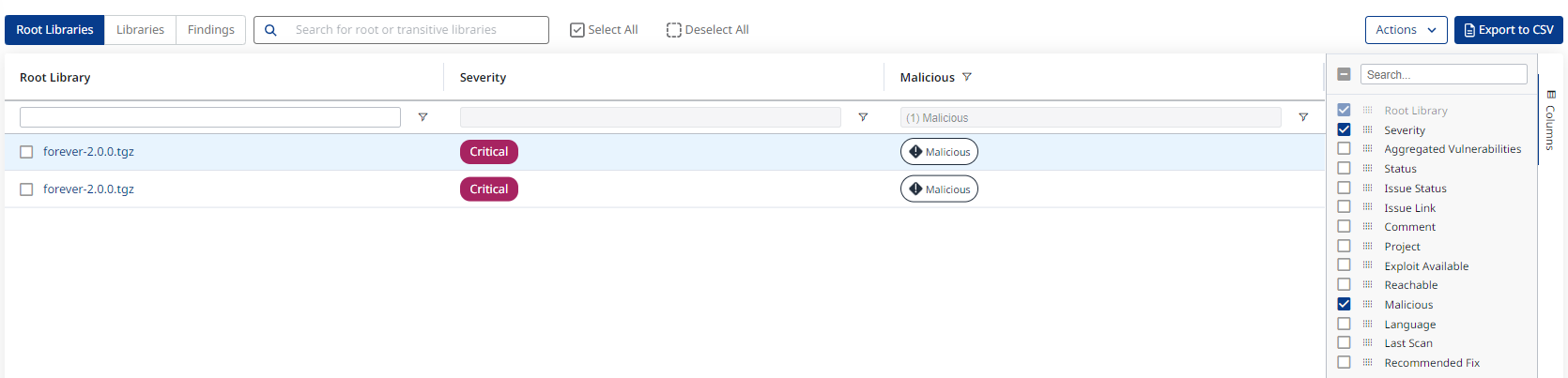
Malicious Packages
Malicious packages are a fast growing threat to software security. Created for a variety reasons, these packages introduce malicious code into your system that can range from protesting a specific political event to providing unauthorized access over your system. While vulnerabilities represent a potential risk to your environment from an outside actor, malicious packages must be treated as an active cyber attack by an outside actor.
Mend will automatically detect malicious packages within your system and report the findings as an MSC for NPM and RubyGem Packages. To learn more about our malicious package detection see Detecting Malicious Packages.
To view your Malicious Packages on the Mend Platform, simply filter your findings to those with “Malicious” tag in your findings view of an application.
Findings with Public Exploits
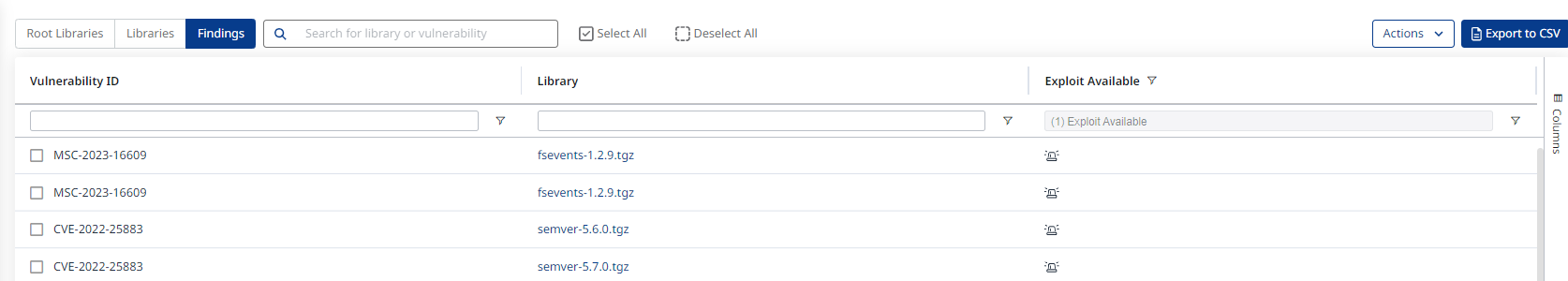
Vulnerabilities that have publicly known exploits present a huge risk to your application security. Mend pulls information from a variety of sources for exploitability and displays the level of exploit maturity for a vulnerability with a known exploits. We will only display an alert on the Mend UI when an Exploit Maturity is at the level of “Proof of concept” or higher. These vulnerabilities present a huge risk for your applications and should be prioritized.
To lean more about see Public Exploits in Mend SCA.
To view your findings with a Public Exploit on the Mend Platform, simply filter your findings to those with “Exploit Available” in your findings view of an application.
Reachable Findings
Mend Reachability currently only supports Java, JavaScript, C#, and Mend Container. Reachability is only available for Mend for http://Github.com , Mend Developer Platform, Mend for Github Enterprise and the Mend CLI.
Mend Reachability can help further prioritize your findings by showing whether the class the given vulnerability is associated is called by your applications source code. This will allow you to focus on addressing vulnerabilities that pose a potential risk of being exploited within your code.
To learn more about reachability, it’s limitations, how to configure reachability, and view the results see:
SCA Reachability
Reachability Results in Mend Container
