Review the top high-severity Dependency Findings within your Organization
Overview
As Security Champion or AppSec manager, you will be reviewing the top Applications and Projects with high-severity Dependency security findings. You will want to drill down into them to review their summaries and findings, including their information and suggested remediations.
Getting it done
Review the top Application with highest severity Dependency Security Findings
Beginning on the Mend Application Security Dashboard, ensure only the Dependency Scan engine is enabled.
Click the Code Scan engine to disable it if it isn’t already.
By default, the Applications widget showing the Top 10 high-risk Applications by Total Findings is ranked by the total number of findings.
Click the “C” in the red box on the Applications widget to rank by highest severity findings.
Note: If multiple applications are tied for the selected ranking order, they are listed alphabetically.
Click the Application that has been sorted to the top with the most high-risk findings. You will be redirected to that application's summary page.
Click Projects in the left pane or click the Projects widget in the Overview section to view the Projects associated with the Application.
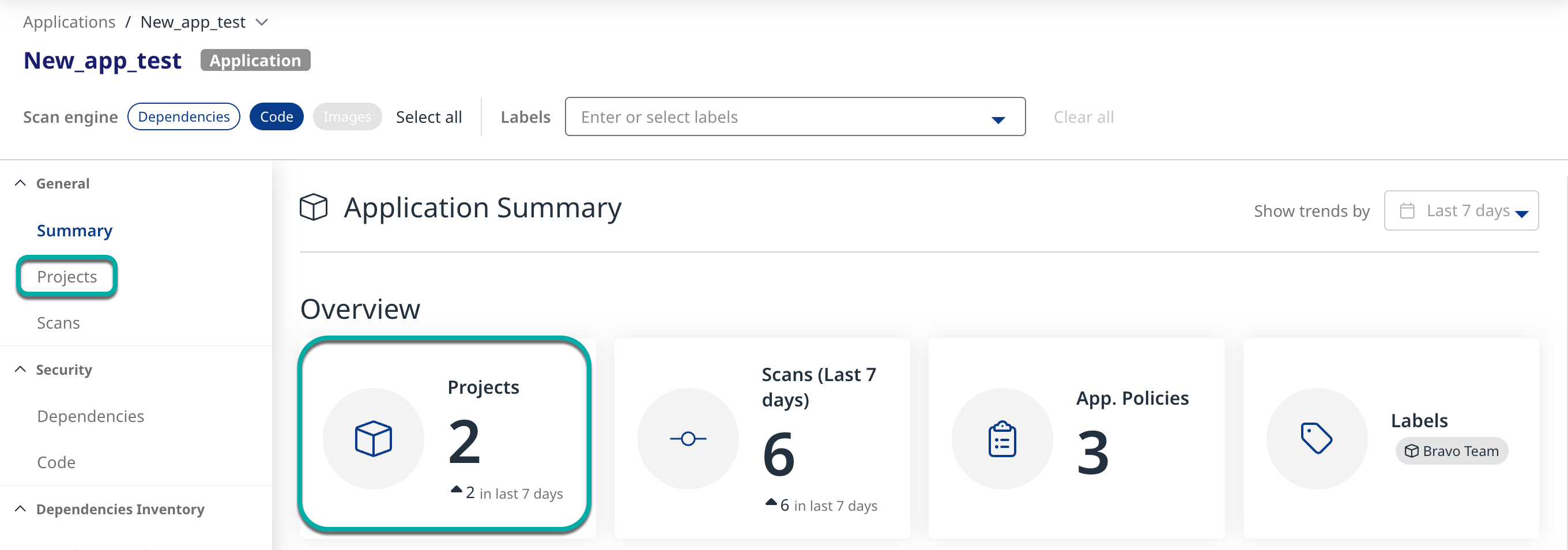
Review the top Project within the Application with the highest severity Dependency Security Findings
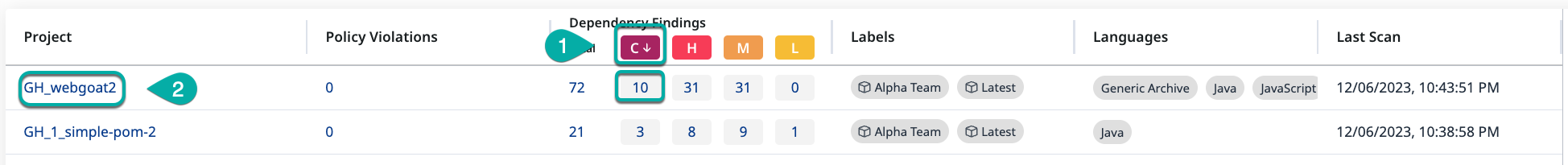
Click the “C” in the red box on the Projects table to rank by most high-severity findings.
Click the Project that has been sorted to the top with the most high-risk findings. You will be redirected to that project's summary page.
Click Dependencies in the left pane or the Total Findings by Scan Engine widget in the findings section to view the latest code findings associated with the Project.
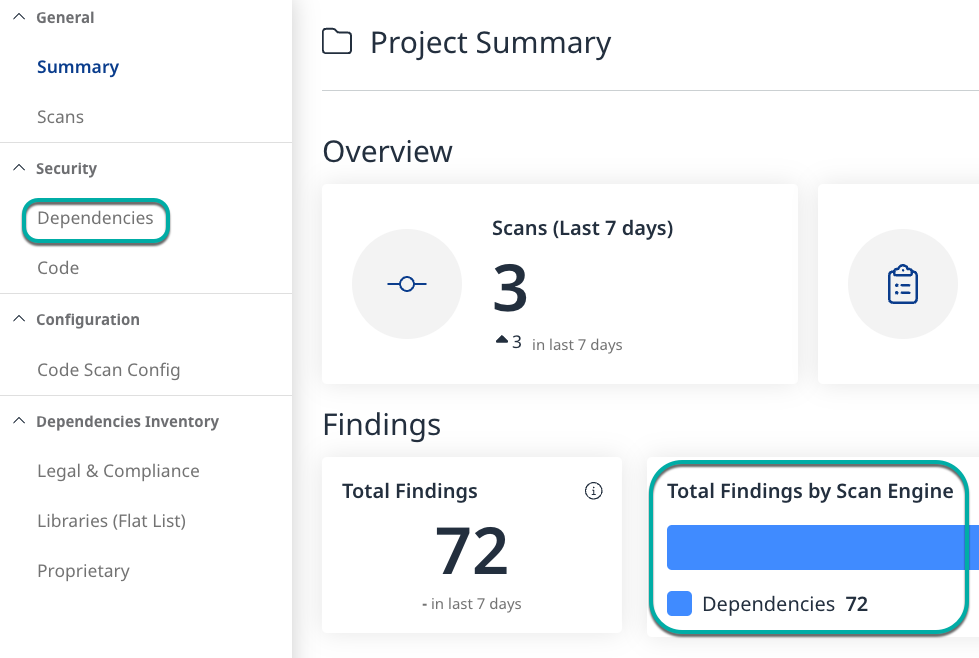
By default, the dependency page displays the findings by Root Libraries.
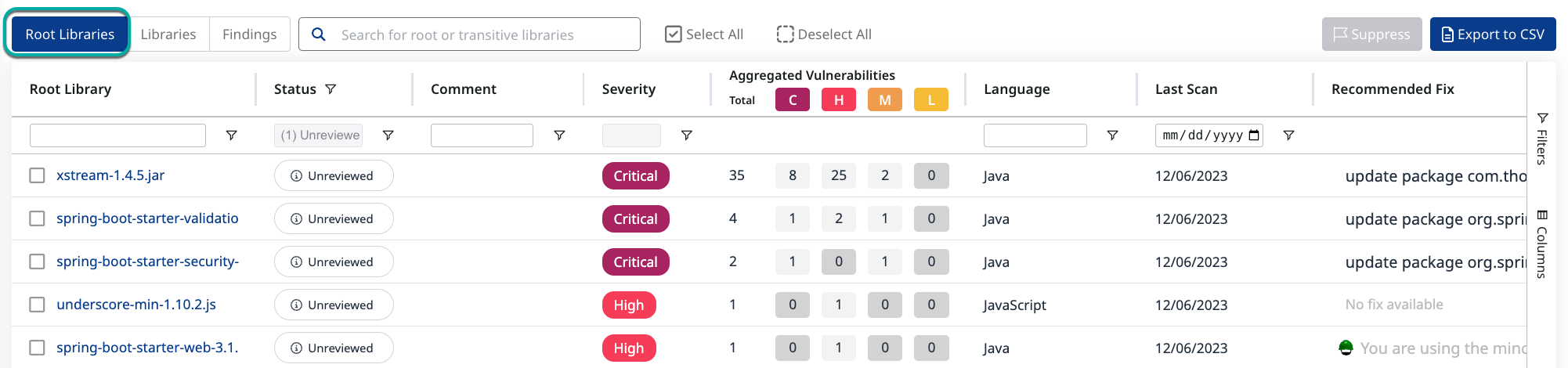
Click the Findings tab.
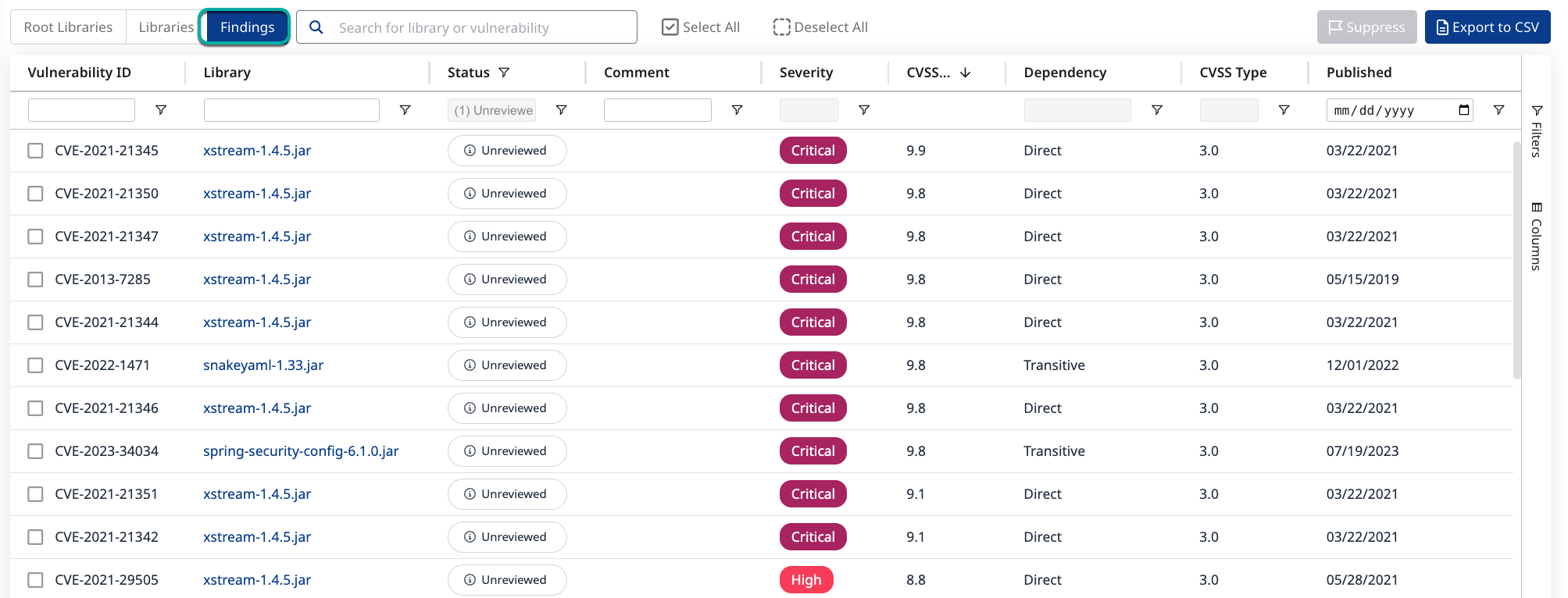
Click the Severity column's filter icon.
Select High to restrict the findings table to only show the highest-risk findings.
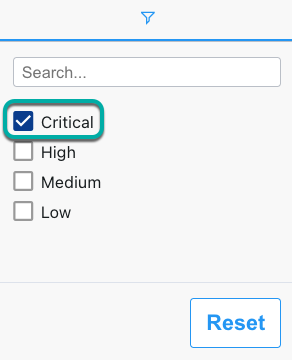
Reviewing the high-risk findings
Click a high-risk finding to show the details of that finding on the right side of the screen.
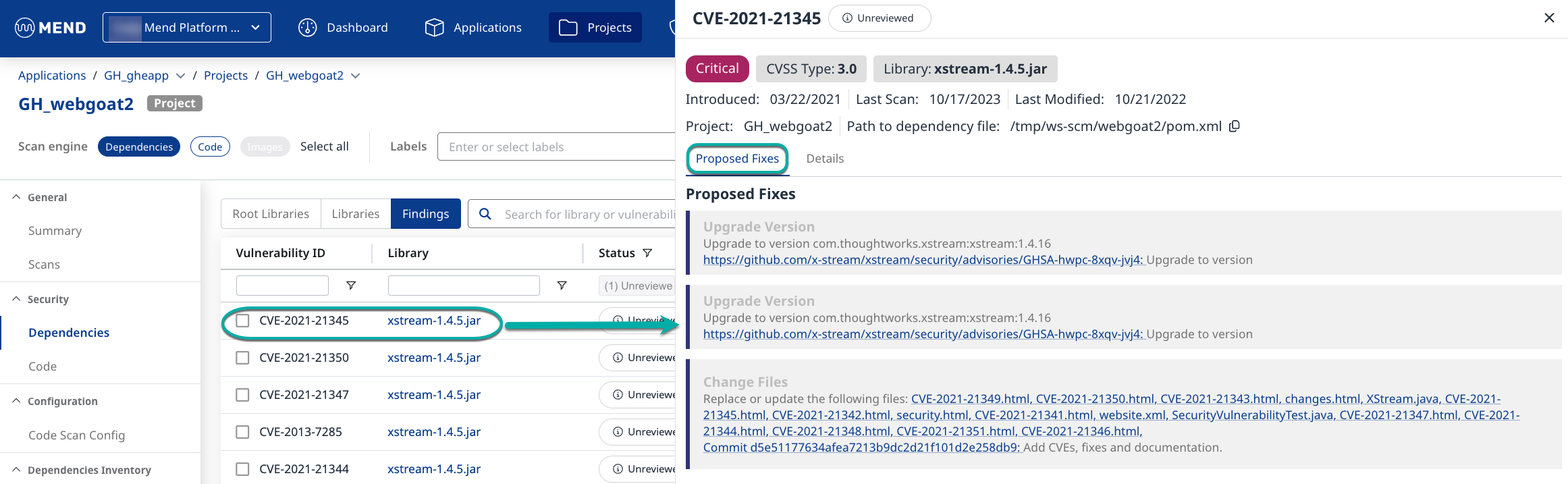
The finding details window defaults to the Proposed Fixes tab.
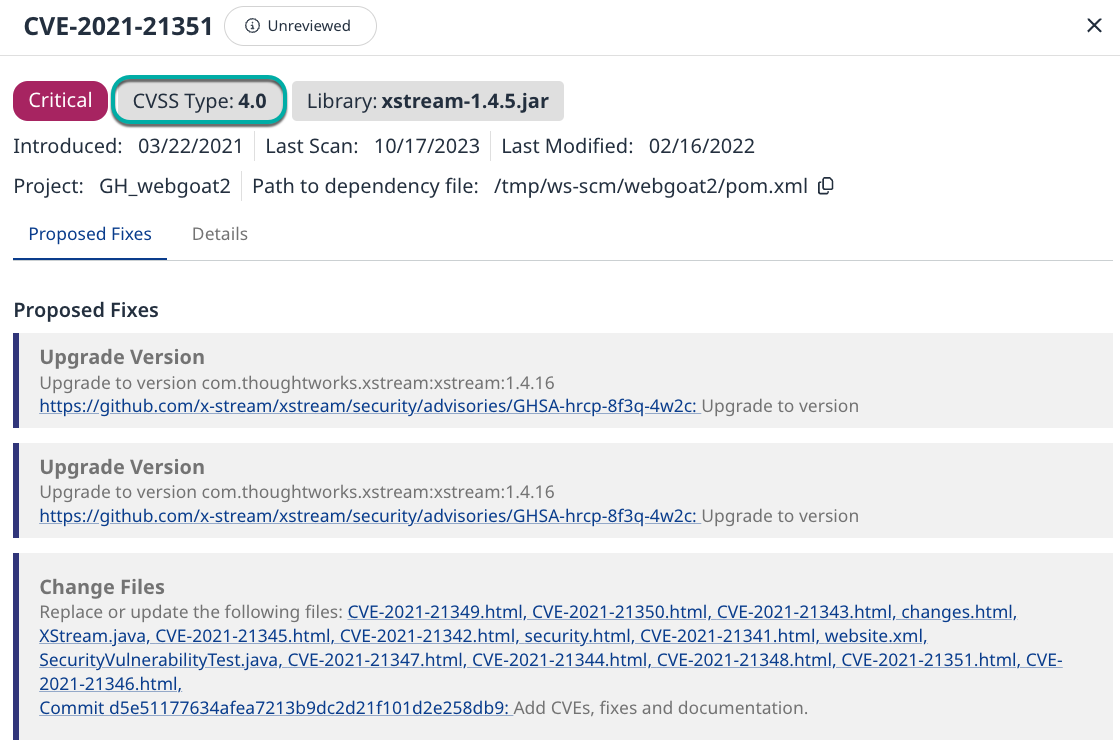
The top section of the finding details shows:
Severity: The severity assigned to the CVE based on the CVSS score.
CVSS Type: The version of CVSS scoring used
Library: The name of the library the CVE was found in
Introduced: The date the finding was introduced into the Project
Last Scan: The date the Project was last scanned
Last Modified: The date the Project was last modified
Project: The Project name
Path to the dependency file: The full path to the dependency file
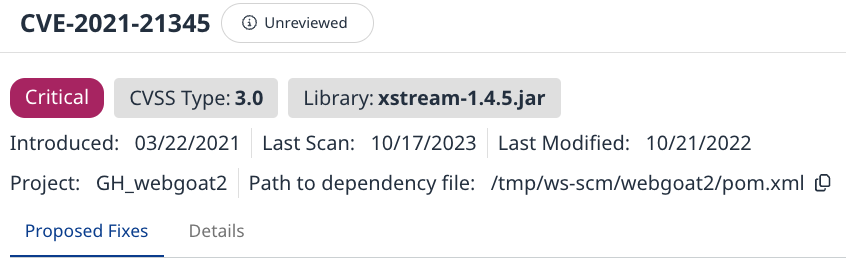
The bottom section shows the Proposed Fixes to resolve the finding
Click the Details tab
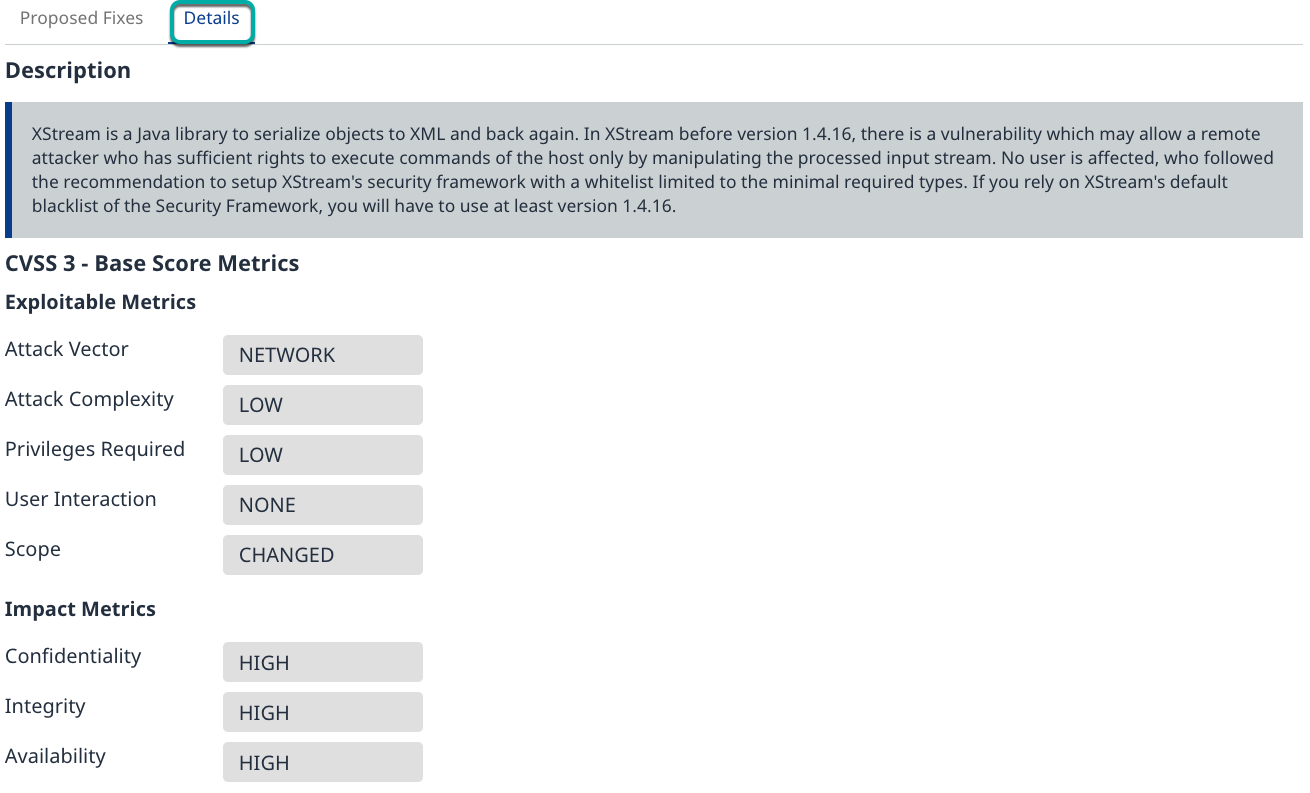
To close the finding details window, click the “X“ in the top right corner.

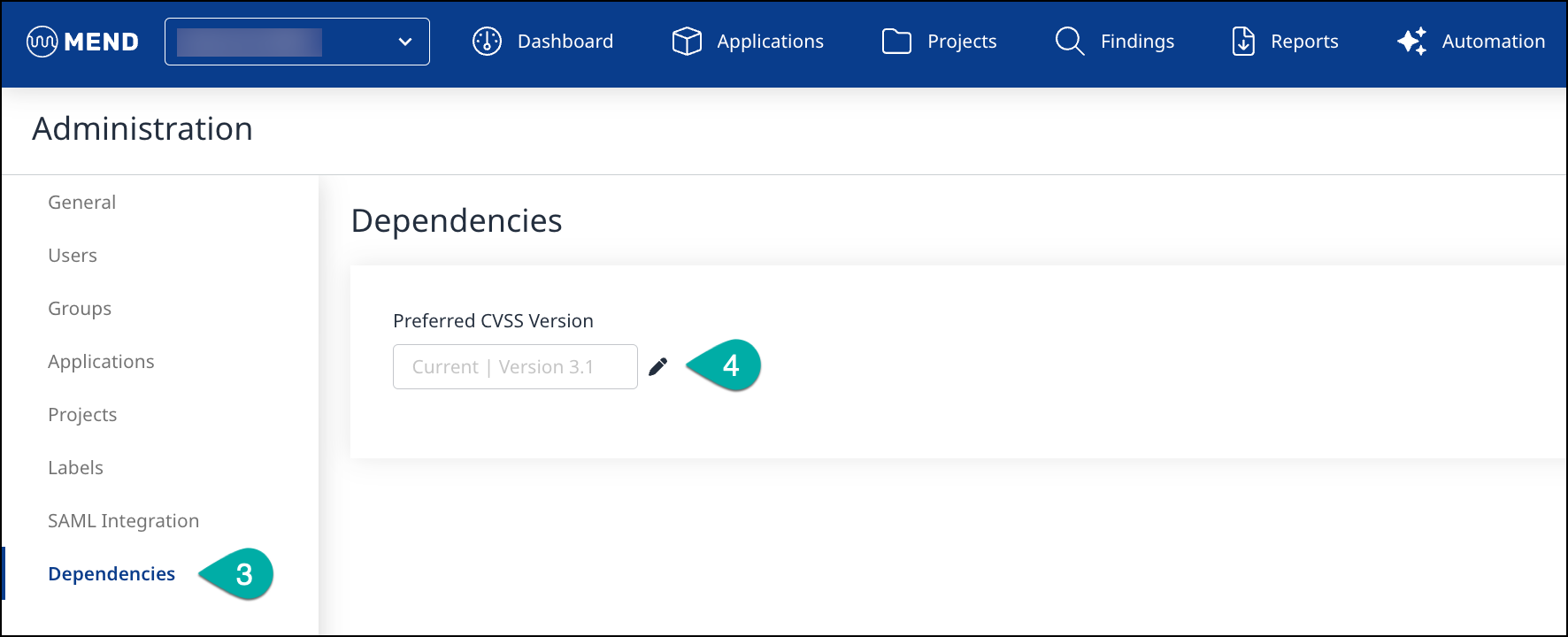
Enable CVSS 4.0 using the User Interface
By default, The latest CVSS Type the Mend Application will show is CVSS 3.1. CVSS 4.0 can be enabled in the Mend Application's Administration list.
This setting controls the CVSS Type across all our products, the Mend Application, the Mend Repo Integrations, and the Mend CLI.
Click the settings gear in the top right corner of the page.
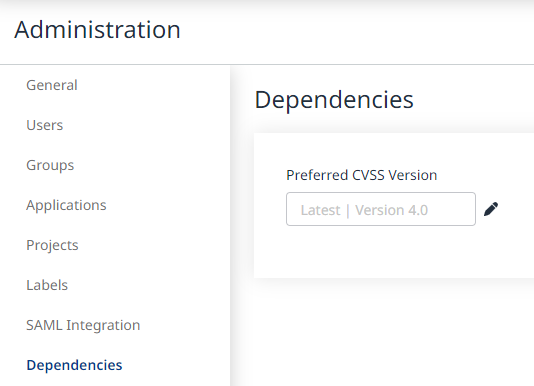
Click Administration to navigate to the Administration page.
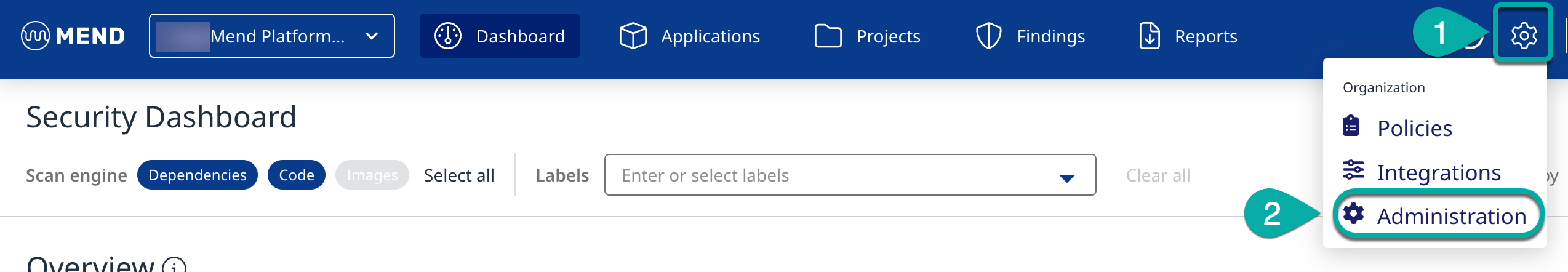
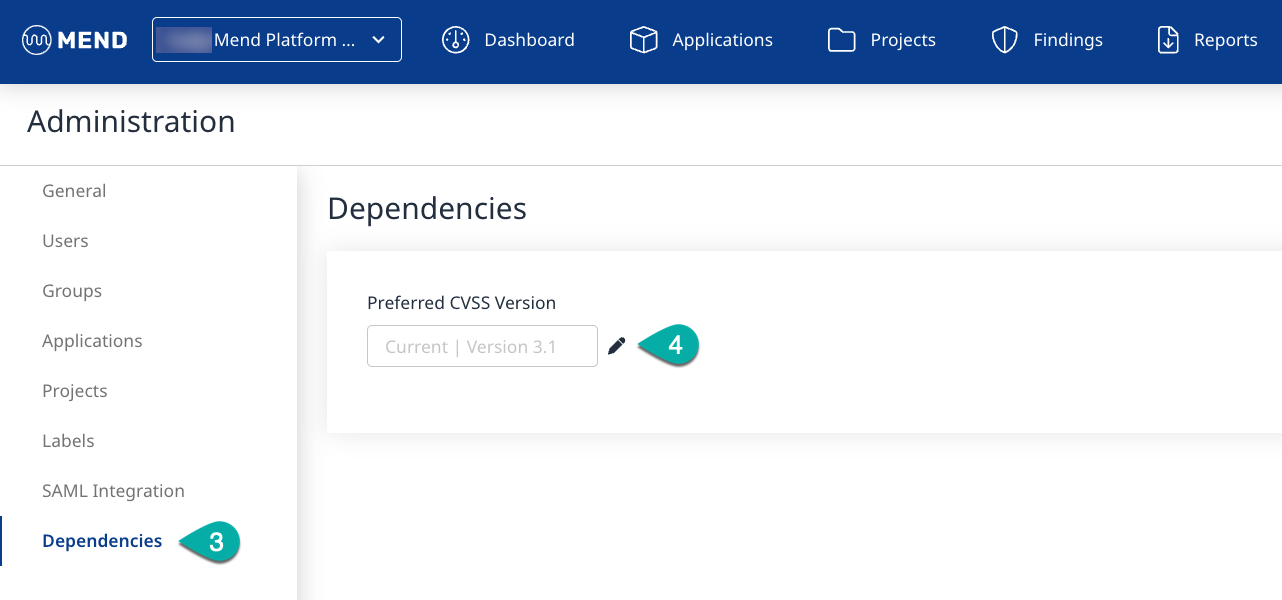
Click Dependencies in the left Administration list to navigate to the Dependencies management page.
Click the Edit icon next to the Preferred CVSS Version field to edit the Preferred CVSS Version.
Select Latest | Version 4.0 in the Edit Preferred CVSS Version pop-up window.
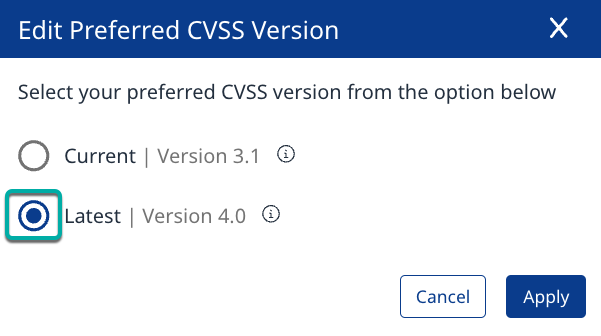
Click Apply.
The CVSS Type will be updated for CVEs in existing Projects and all future Dependency findings.
Enable CVSS 4.0 using API v2.0
Administrators can enable CVSS 4.0 at the organization level using the following API:
POST https://{baseUrl}/api/v2.0/orgs/{orgToken}/settings/cvss/rule
{
"settingValue":"CVSS_4"
} A successful response will look like the following:
{
"additionalData": {},
"supportToken": "XXX",
"retVal": {
"message": "CVSS settings rule changed successfully"
}
}After changing the value, the proper indication will also be visible in the UI:
For more information about CVSS Types, review our Vulnerabilities – Risk Scoring documentation.
