Integrate third-party Code Scan Results into Mend SAST
Overview
Some programming languages that are not covered by Mend.io may have dedicated open source scanners (e.g., Kani). Mend SAST allows you to import the scans/findings from such scanners into the Mend AppSec Platform using a Mend CLI command, so they can all be consumed by security managers alongside the Mend SAST results via the Mend AppSec Platform UI, maintaining a uniform user experience and retaining the Mend Platform as a single hub for all AppSec findings.
Use Cases
Security managers should be able to run any tool of preference and import the results from that tool into the Mend AppSec Platform to have them displayed alongside regular Code scans/findings. Imported results behave similarly to regular scan results and can be used in Automation Workflows to create violations, Jira tickets, etc.
Getting it done
Importing Results using the Mend CLI
To import scans/findings from a 3rd-party tool into the Mend AppSec Platform, run the following Mend CLI command:
mend code import --dir <projectDir> --scope <scope> --import-file <pathToFile>
The command will import the results from the specified file, process them (signatures, suppressions etc.) and try to extract snippets from the specified project directory.
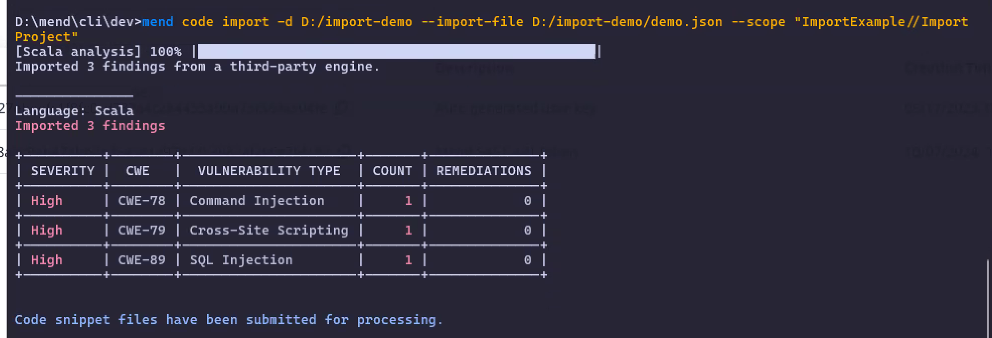
A Successful Import in the Mend CLI
Viewing Results in the Mend AppSec Platform
Once imported, imported results will be visible in the application or project’s Code findings just like any other application or project.
The Driver column in the Code Findings table distinguishes between Mend findings and third-party imports.
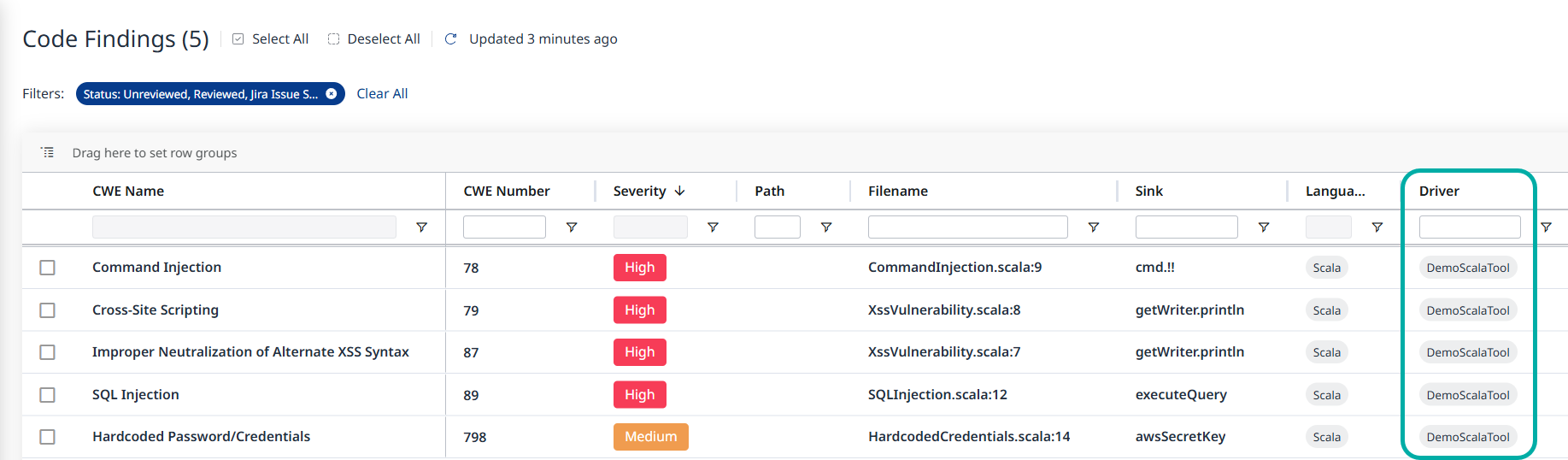
The Driver column showcasing imported Scala results
Setting up Automation Workflows
Imported results behave similarly to regular Code scan results and can be used in Automation Workflows to create violations, Jira tickets, etc.
For more information on setting up automation workflows, visit Automate your Workflows in the Mend AI Native AppSec Platform.
Import Format
This section is designed to help you map the output of the 3rd-party tool to Mend.io’s SARIF-like JSON format.
JSON Schema
{
"$schema": "http://json-schema.org/draft-07/schema#",
"title": "Scan Results Schema",
"type": "object",
"description": "Root object for the scan results",
"properties": {
"tool": {
"type": "object",
"description": "Information about the tool used",
"properties": {
"name": {
"type": "string",
"minLength": 1,
"description": "Tool name must not be empty"
},
"version": {
"type": "string",
"description": "Tool version can be empty or non-empty, no specific restriction"
}
},
"required": [
"name",
"version"
]
},
"run": {
"type": "object",
"description": "Run object",
"properties": {
"language": {
"type": "string",
"minLength": 1,
"description": "Language must not be empty"
},
"findings": {
"type": "array",
"description": "List of findings for this run",
"items": {
"type": "object",
"properties": {
"type": {
"type": "object",
"description": "Type details of the finding",
"properties": {
"name": {
"type": "string",
"minLength": 1,
"description": "Finding type name must not be empty"
},
"severity": {
"type": "string",
"enum": [
"critical",
"high",
"medium",
"low",
"unknown"
],
"description": "Possible severities for the finding"
},
"description": {
"type": "string",
"description": "Optional description"
},
"cwe": {
"type": "integer",
"minimum": 1,
"description": "If provided, cwe must be >= 1 (i.e., can't be 0)"
}
},
"required": [
"name",
"severity"
]
},
"description": {
"type": "string",
"description": "Optional top-level description for the finding"
},
"sink": {
"type": "object",
"description": "Sink location details for the finding",
"properties": {
"name": {
"type": "string",
"minLength": 1,
"description": "Sink name must not be empty"
},
"file": {
"type": "string",
"minLength": 1,
"description": "Sink file must not be empty"
},
"line": {
"type": "integer",
"minimum": 1,
"description": "Sink line must not be 0"
}
},
"required": [
"name",
"file",
"line"
]
},
"flows": {
"type": "array",
"description": "Optional flow trace for the finding",
"items": {
"type": "object",
"properties": {
"name": {
"type": "string",
"minLength": 1,
"description": "Flow name must not be empty if present"
},
"file": {
"type": "string",
"minLength": 1,
"description": "Flow file must not be empty if present"
},
"line": {
"type": "integer",
"minimum": 1,
"description": "Flow line must not be 0 if present"
}
},
"required": [
"name",
"file",
"line"
]
}
}
},
"required": [
"type",
"sink"
]
}
}
},
"required": [
"language",
"findings"
]
}
},
"required": [
"tool",
"run"
]
}JSON file example with schema import
{
"$schema": "./import-schema.json",
"tool": {
"name": "SomeTool",
"version": ""
},
"run": {
"language": "Scala",
"metrics": {
"files": 100,
"lines": 10000
},
"findings": [
{
"type": {
"name": "SQL Injection",
"severity": "high",
"description": "",
"cwe": 89
},
"description": "",
"sink": {
"name": "executeQuery",
"file": "/some/path/somefile.scala",
"line": 34
},
"flows": [
{
"name": "something",
"file": "/some/path/somefile.scala",
"line": 56
}
]
}
]
}
}Limitations
Configuration of the 3rd party tool (e.g., for which CWEs to scan, directories to exclude, etc.) is required for the import and is done within that tool; it cannot be achieved using the Mend scan configuration.
Consequently, you might get findings for CWEs that are disabled in the Mend AppSec Platform’s Code scan configuration.
If an imported finding has a CWE not natively supported by Mend.io, it will not be mapped to a compliance standard.
