View the results of your Mend for GitHub Enterprise SAST scan
Overview
Once your Mend for GitHub Enterprise SAST scan has been completed, there are multiple resources provided to help you review, analyze, and triage your results.
Mend Code Security Check
Once the Mend for GitHub Enterprise SAST scan is completed, the Mend Code Security Check is updated:
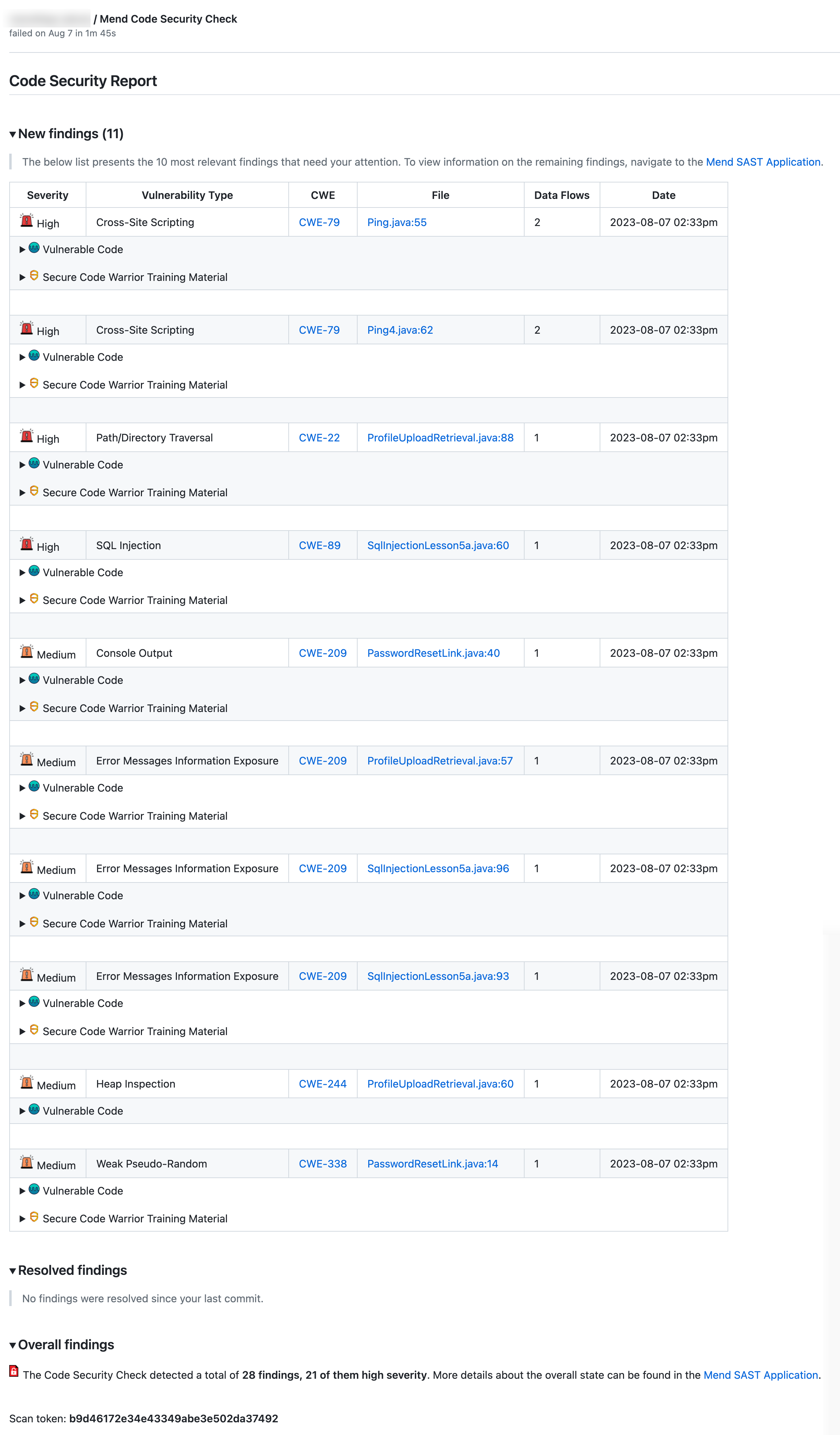
Within the Mend Code Security Check, there are three main sections:
New findings
Resolved findings
Overall findings
Depending on the type of scan that was done:
For base branch scans, New and Resolved findings are based on the comparison with the previous commit on the same branch.
For feature branch scans, New and Resolved findings are based on the comparison done against the base branch. This is to ensure that merging the feature branch does not introduce any new findings to the base branch.
The Mend Code Security Check also includes a Scan token, which you can provide to Mend Support for troubleshooting.
New findings
The New findings section provides details on the findings that were introduced in the commit:
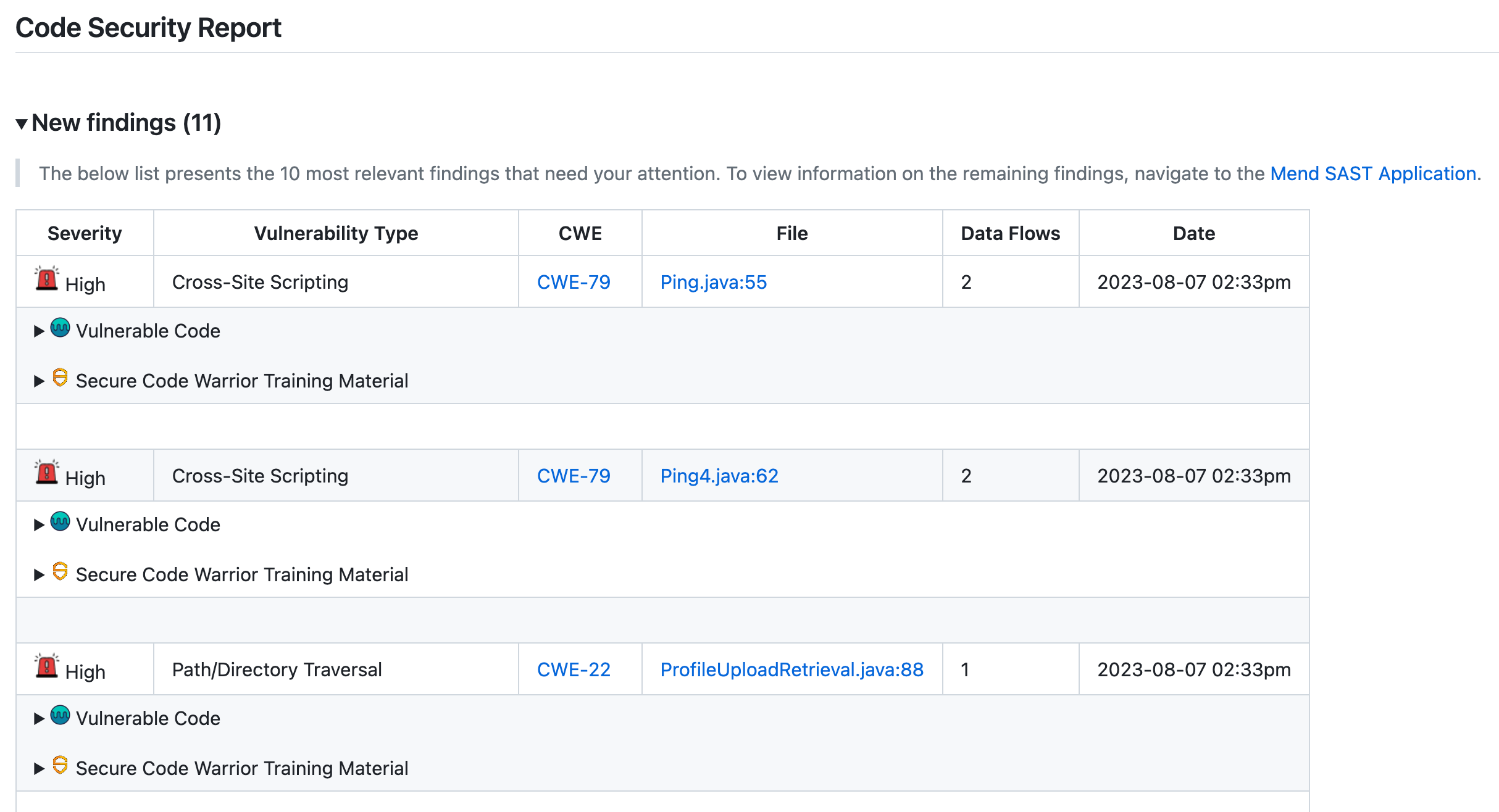
Severity: Level of severity (
High, Medium, Low) of the finding introduced.Vulnerability Type: Type of finding that was introduced.
CWE: CWE ID that was introduced. This links to the CWE’s page on the official MITRE site.
File: File and code line(s) that are impacted by the finding
Data Flows: Number of data flows that lead to the finding.
Date: Date and time the vulnerability was originally introduced (
YYYY-MM-DD 00:00).Vulnerable Code: Expand to show details of the Vulnerable Code of each finding.
Secure Code Warrior Training Material: Expand to see context-based links to Secure Code Warrior training material.
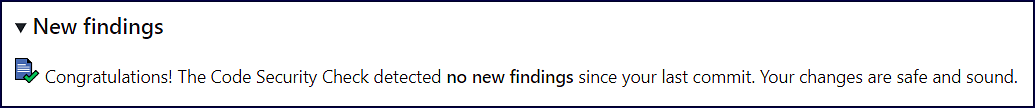
If no new findings are introduced, the New findings section will provide the following confirmation message:
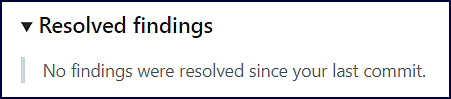
Resolved findings
The Resolved findings section provides details on the findings that were resolved in the commit:
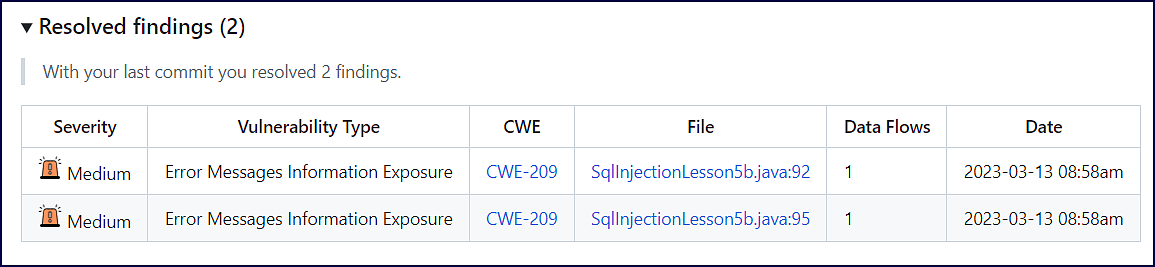
Severity: Level of severity (
High, Medium, Low) of the resolved finding.Vulnerability Type: Type of finding that was resolved.
CWE: CWE ID that was resolved. This links to the CWE’s page on the official MITRE site.
File: File and code line(s) impacted by the finding.
Data Flows: Number of addressed data flows that led to the finding.
Date: Date and time the finding was originally introduced (
YYYY-MM-DD 00:00).
If no findings were resolved, the Resolved findings section will not contain any data:
Overall findings
The Overall findings section provides the total count of findings as well as the direct link to the scan’s Details page within the Mend SAST application:

Mend Platform UI
Within the Mend Platform user interface, you can review each Mend for GitHub Enterprise SAST scan’s summary, details, and more. For more information on how to navigate your results in the Mend Platform, visit our Analyze your results in the Mend Application documentation.
GitHub Issue: Code Security Report
Note: The SAST GitHub Issue “Code Security Report” is only created and updated on base branch scans. By default, this GitHub Issue is created with the “Mend : code security findings” Issue label.
Once the Mend for GitHub Enterprise SAST scan on the base branch is completed, the Mend Code Security Check creates a GitHub Issue titled “Code Security Report”. The Code Security Report shows the most relevant findings, regardless of when they are introduced:
Within the Code Security Report, there are three main sections:
Scan Metadata
Most Relevant Findings
Findings Overview
Scan Metadata
The Scan Metadata provides the scan’s vitals and a high-level few of the findings:
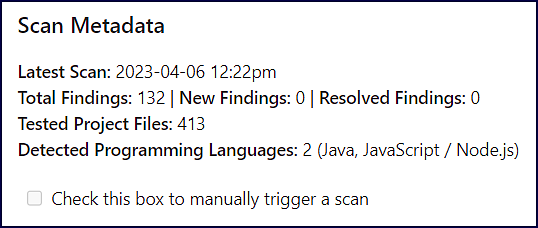
Latest Scan: Date and time of the last scan (
YYYY-MM-DD 00:00)Total Findings: Number of overall findings
New Findings: Number of new findings based on the comparison with the previous commit on the same branch
Resolved Findings: Number of resolved findings based on the comparison with the previous commit on the same branch
Tested Project Files: Number of files scanned with Mend SAST
Detected Programming Languages: Number and type(s) of programming language(s) discovered
“Check this box to manually trigger a scan”: Checking this box initiates a SAST scan on the same branch the Code Security Report was created from.
Most Relevant Findings
The Most Relevant Findings section provides details on 10 High Severity vulnerabilities that need your attention:
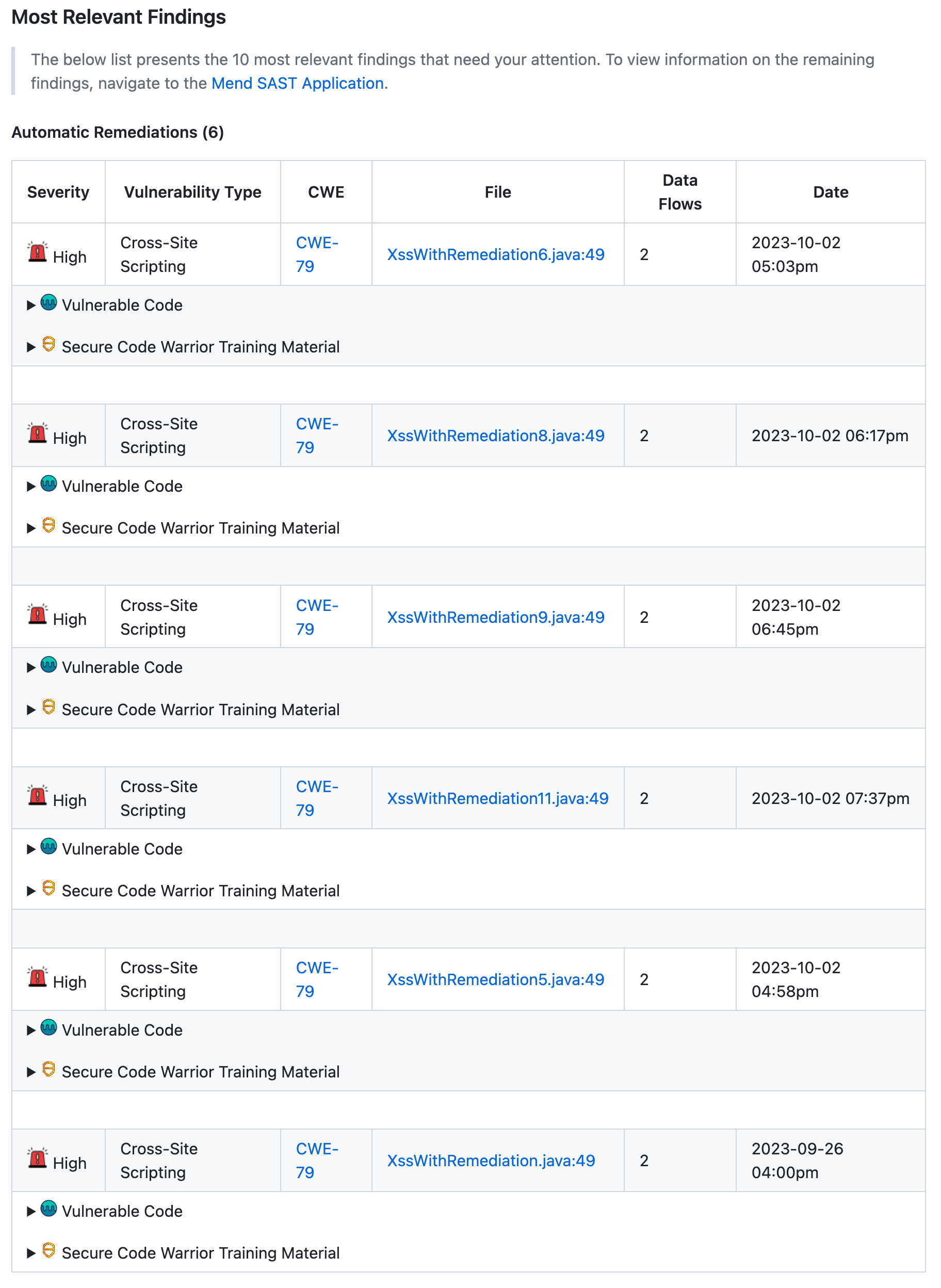
Severity: Level of severity (
High, Medium, Low) of the finding introduced.Vulnerability Type: Type of finding that was introduced.
CWE: CWE ID that was introduced. This links to the CWE’s page on the official MITRE site.
File: File and code line(s) that are impacted by the finding
Data Flows: Number of data flows that lead to the finding.
Date: Date and time the finding was originally introduced (
YYYY-MM-DD 00:00).
Vulnerable Code: Expand to show details of the Vulnerable Code of each CWE.
Secure Code Warrior Training Material: Expand to see context-based links to Secure Code Warrior training material.
Findings Overview
The Findings Overview section provides a summary of vulnerability types found from the SAST scan:
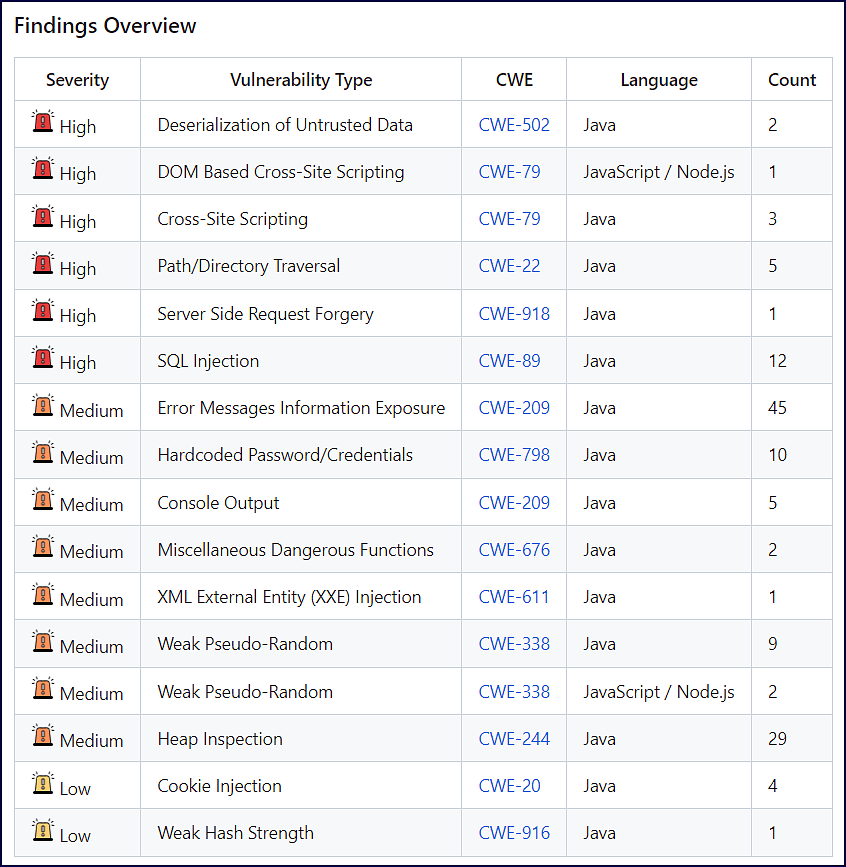
Severity: Level of severity (
High, Medium, Low) of the finding type.Vulnerability Type: Name of the finding type.
CWE: CWE ID associated with the vulnerability type. This links to the CWE’s page on the official MITRE site.
Language: Language associated with the finding type.
Count: Number of occurrences of the finding type.
