Legacy Mend UI - Determining Vulnerable Source Files
This article will walk you through how to identify which Source File is vulnerable in a Source File Library in your projects within the Mend UI.
Good to know
During the file system scan step of the Unified Agent, the files scanned may be source files or binary files, and each are treated differently.
Binary files contain source files (compiled or non-compiled, sometimes both), and represent libraries, components, or packages. Note that, source files are not libraries.
Source files are files containing "human readable" code written by programmers, and again, are not libraries themselves. Mend maps source files to “source libraries”, which are collections of source files, while binaries are libraries themselves.
A source library represents a specific tag (version) of a code repository and a collection of source files mapped to it. A single source file might belong to thousands of source libraries across different repositories and tags (versions).
Unlike a binary library, a source library isn't identified individually via SHA-1 or coordinates, but rather using the source files mapped to it.
Vulnerabilities are associated with source files, not source libraries. Therefore, even if you manually change the origin source library of a source file, your reported vulnerabilities will remain associated to the same source file.
Instructions
Follow the instructions below to view your reported source files in the Mend UI:
Sign into your Mend Organization
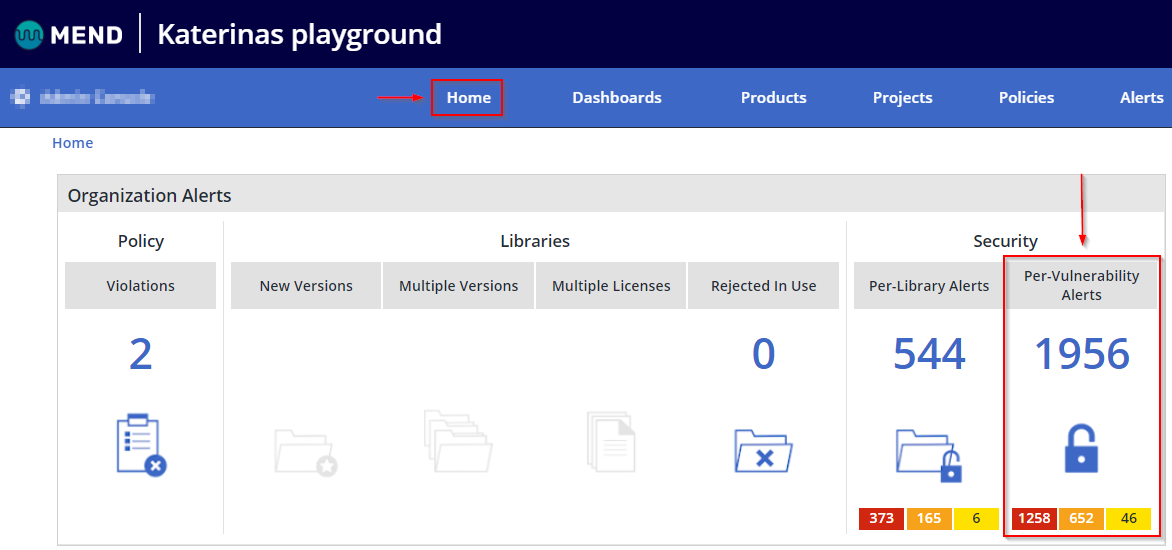
Via your Home page, click on the Per-Vulnerability Alerts section to access the Security Alerts: View By Vulnerability report:
An alternative way to get to this report is to click on Alerts > View by Vulnerability: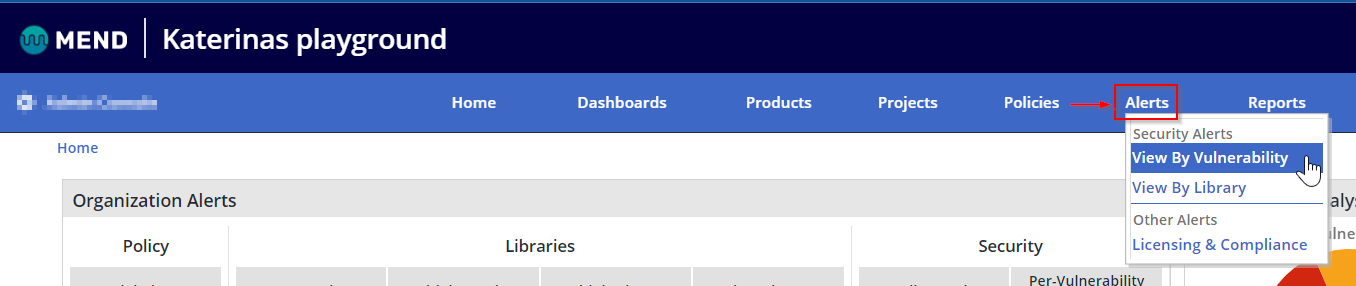
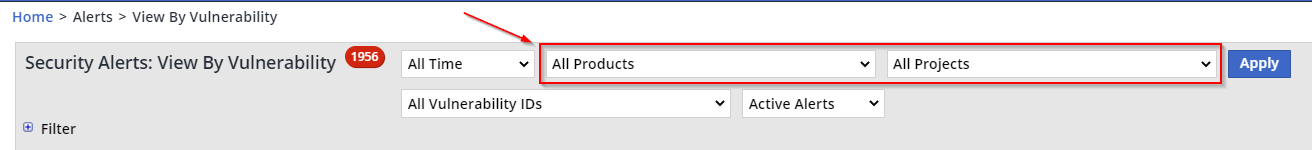
In the Security Alerts: View By Vulnerability report, you can narrow down the results to Product or Project level:
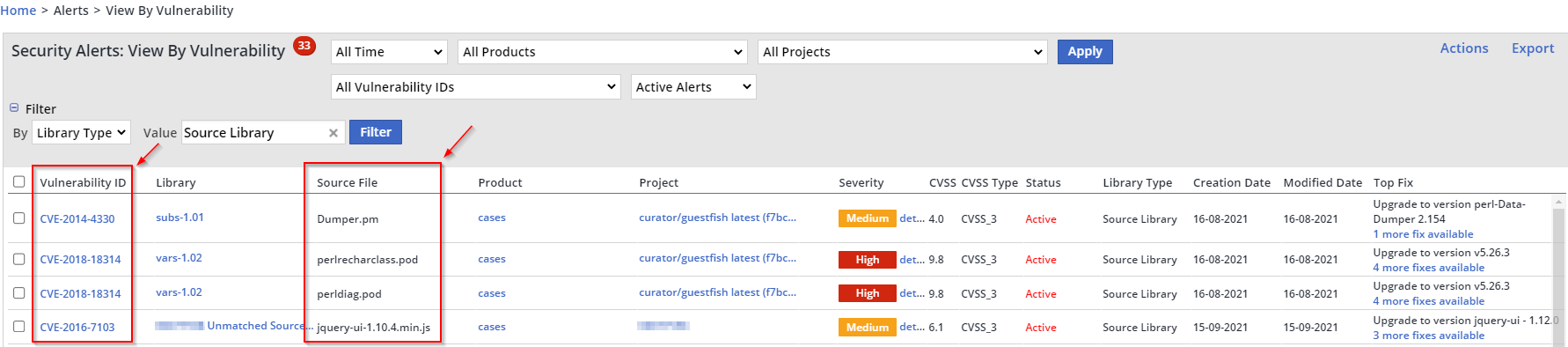
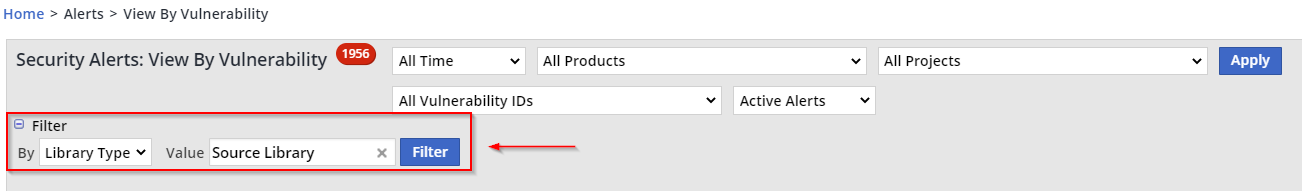
Filter the report by Library Type > “Source Library” and click on Filter:
The results will now show the source libraries with vulnerable source files in your Inventory:
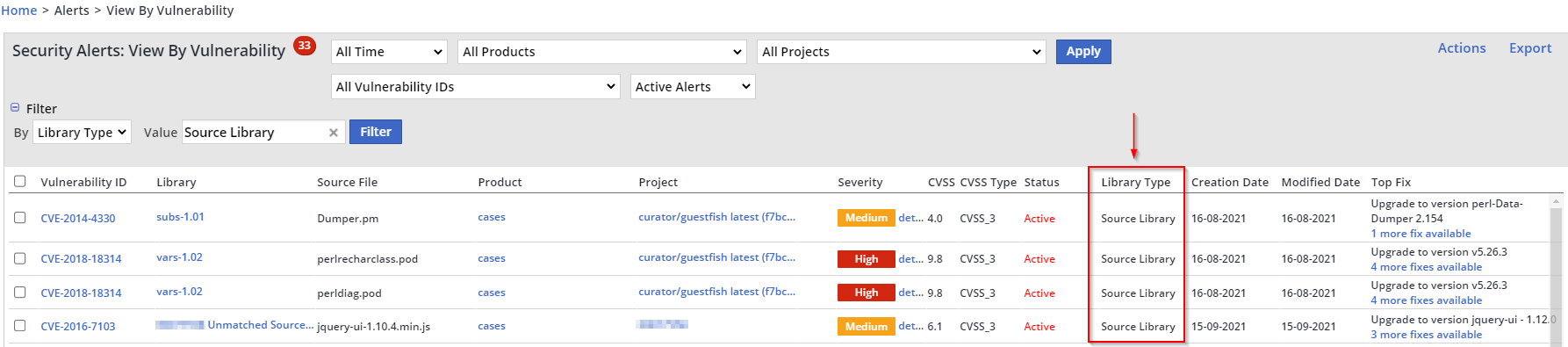
You will now see the CVE vulnerability that is associated with a specific source file: