Security Alerts: View by Vulnerability
Overview
The Security Alerts: View By Vulnerability screen enables you to manage the alerts per vulnerability according to the selected products/projects. For example, use this screen to ignore alerts of a specific vulnerability across all libraries in the selected scope.
In addition, this provides the ability to triage such vulnerability alerts with better granularity - per vulnerability instead of per library.
Accessing the Security Alerts: View By Vulnerability Screen
To access the Security Alerts: View By Vulnerability screen, do as follows:
From the menu bar, select Alerts > Security Alerts - View By Vulnerability. The Security Alerts - View By Vulnerability screen is displayed.
Selecting and Generating the Report Data
Filter the alert by the following parameters:
Time - Filters for the time scope
Products - Filters for the relevant product
Projects - Filters for the relevant project
Vulnerability ID - Filters for the relevant ID
Status - Filters for active, ignored, or resolved (resolved alerts are those that include statuses Ignored, Library Removed, and Library In-House) alerts
When hovering over the status column, in case the alert's status has been manually changed by a user, the user's email and the comment that was provided will appear as a tooltip.Scope - Filters for all security alerts, security vulnerabilities only, malicious packages only, or exploitable vulnerabilities only.
For additional (hidden) filters, expand Filter. Options are as follows:
By Library - Filters according to library, library type, severity, or source file
Value - Filters according to an entered value related to the selection in the By Library filter
Click Apply to set the filters. The list is generated.
Refer to the informative table below.
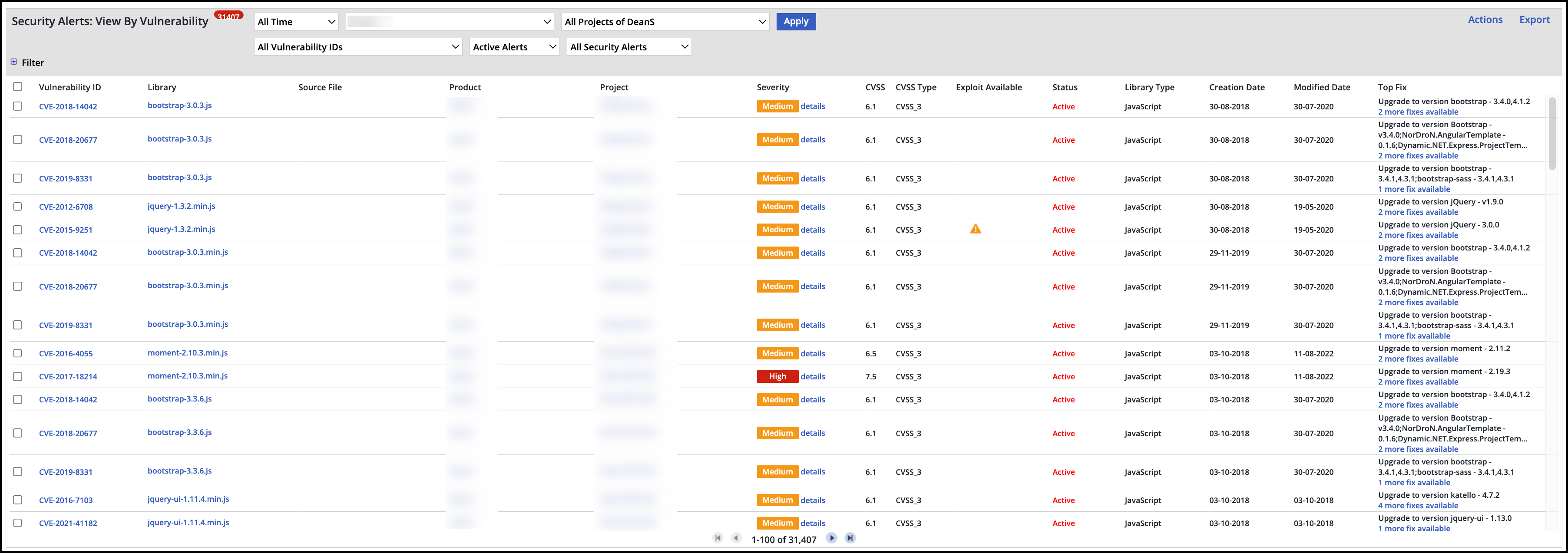
Table Components
Column | Description |
|---|---|
Vulnerability ID | The vulnerability and its individual ID |
Library | Library name where the vulnerability was found |
Source File | File where the vulnerability was found |
Product | The product where the vulnerability was found |
Project | The project where the vulnerability was found |
Severity | Critical, high, medium, low |
Details | The library’s vulnerabilities list. For customers using Prioritize, this screen displays the traces for the effective vulnerabilities. |
CVSS | The vulnerability's Common Vulnerability Scoring System (CVSS) score |
CVSS Type | CVSS 1, CVSS 2, CVSS 3. For more information, see here. |
Exploitable |
|
Status | Alerting status of the vulnerability:
All data can be filtered and sorted. |
Library Type | Java, source library, etc. |
Creation Date | The date when the alert was created |
Modified Date | The date when the alert was last modified |
Top Fix | The best fix that matches the vulnerability |
Actions | Change alert status (for example, change the status from ignored to active by selecting the “activate” action) |
Export | Export the table data to MS Excel, XML, or JSON |
Additional Actions
To ignore an alert, check the alert's row (checkbox on the left) and select Action > Ignore.
To activate an ignored alert, filter the table for ignored alerts, then check the alert's row (checkbox on the left) and select Action > Activate. The alert will no longer appear in the ignored alerts list and will appear instead in the list of active alerts.
Note: The actions of ignoring and activating alerts are saved to the Change Log History Report. This report can be used to filter and monitor these actions, and to view who performed them and when, and to view any informative comments that those users might have added.
To export an alert to a selected format (Excel, XML, or JSON), check the alert's row (checkbox on the left), select Action > Export, and select your desired format.
Viewing Vulnerabilities' Details
To view information for a specific vulnerability, in Vulnerability ID, select the vulnerability. The Security Vulnerability page displays relevant information regarding the vulnerability such as ID, description, and score, CVSS3 base score metrics, libraries that are vulnerable due to this specific vulnerability, and suggested fixes.
To view information for a specific vulnerability's library, in the Library column, click the library. The Library Details page displays Impact Analysis (in which projects those libraries are used and whether they are direct or transitive dependencies), general library details, license and copyright information, information on additional known versions of the library, a list of all of the libraries' vulnerabilities, library trends, etc.
To view information for a specific vulnerability's related product or project, in the Product or Project columns, click the product or project. The relevant Home screen for that product or project is displayed with a variety of dashboard options, including security alerts, license analysis, and vulnerability analysis.
