Integrate your Container Image Registries into Mend Container
Overview
The Mend container image registry scanning solution offers a seamless integration to Container Image registries on demand. It’s designed to scan container images at scale, directly from image registries, and identify security vulnerabilities in them.
Through our container image registry scanning, we empower you and your organization to proactively identify threats and ensure that you have a comprehensive view of your security posture to carry out the necessary remediations to protect your applications.
Use cases for integrating your private container image registries with Mend
The registry integrations can be utilized in the following ways:
You, a DevOps Engineer, are responsible for implementing tools that scan container images stored in your organization's registry for known vulnerabilities. You are looking for a tool that automates the scan process to reduce the workload of manual reviews.
You, an AppSec Manager, are tasked with ensuring that no container images with known vulnerabilities are deployed in the organization's production environment from your development team. You want a visual representation of the overall state of your registries.
You, a Security Champion, are in charge of analyzing image registry scan findings. You want a tool that will help you in providing feedback to your development teams on what risks need to be addressed first.
Mend’s Answer: By integrating Mend with your organization's private image registry, you provide security to your organization by automatically bulk-scanning images in your registries. This enables your organization to maintain an up-to-date view of the security posture of your container images, ensuring that potential vulnerabilities are detected, triaged, and addressed promptly.
Getting it done
Configure the private registry integration in the Mend Platform
Note: Pay special attention to the prerequisites section of each integration.
While logged into the Mend Platform, click the cogwheel icon at the top right corner of the screen and select ‘Integrations’:
Scroll down to the ‘Registries’ section and click the desired integration:
Fill in the relevant information. The steps are explained more explicitly in the designated article for each integration:
Types of registry integrations in the Mend application
We detect and save private and public registry occurrences.
Public registries will be tagged as
Public/Manualin the Registry Access column to indicate that we detected a public registry.Private registries will be tagged as
Private, these are registries created from the integration page.System-managed registries will be tagged as such,
System-managed, and indicate registries found automatically as part of a K8s scan.
Trigger a private registry scan
Note: Registry scans are set by default to scan the 10 most recent tags of each detected repository, to avoid storing unnecessary and outdated data in your Mend organization.
The latest tag will be scanned last to reflect the up-to-date version of each repository.
Once a tag has been scanned, it won’t be scanned again unless its push date to the registry was changed (not likely, not recommended).
Pull settings will be added soon to control which repositories and tags will be scanned.
The registry integration scan can be started by one of the following:
A scan will start automatically when the private registry is initially added via the Integrations dashboard.
Still in the Integrations screen, under Settings → My Integrations (1) select the relevant private registry or registries (2) and click on the Scan Now button to initiate a scan.
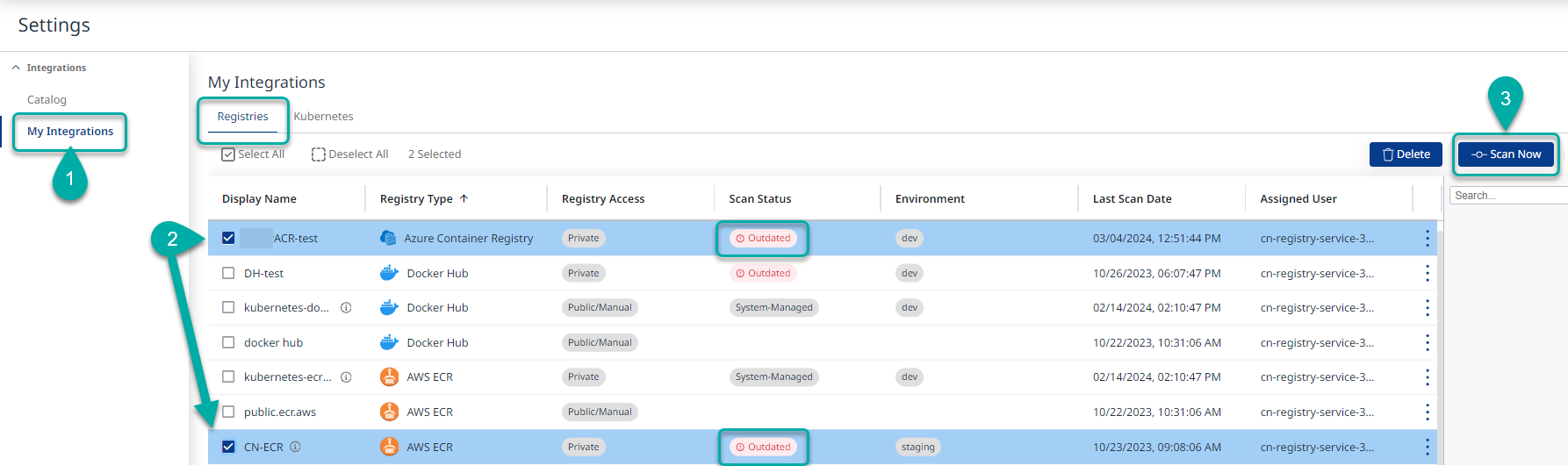
Alternatively, you can click the Scan Now button in the options menu at the far edge of the screen (applicable to a single registry at a time)
Scan Scheduling
The Scan Interval column provides scheduling details for your scans. Hovering over the Scan Interval value will spawn a tooltip that displays the Scan Schedule and the time of the next scan.
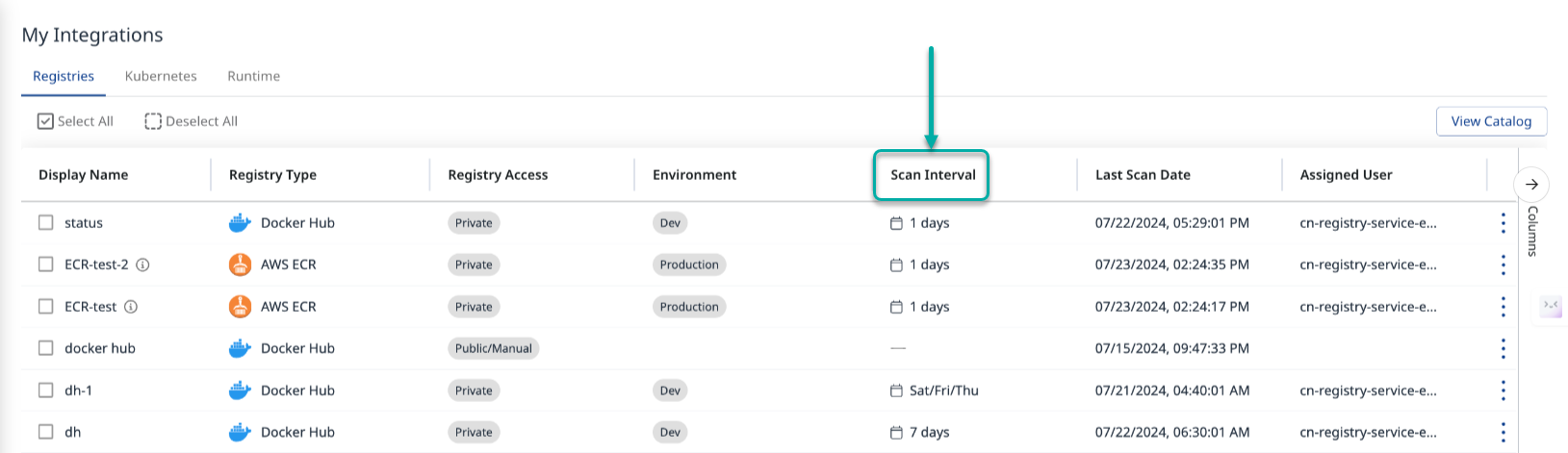
The Scan Interval Column
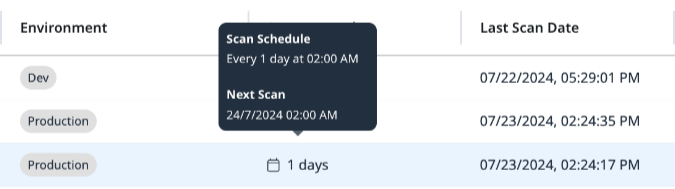
Scan Schedule & Next Scan Tooltip
You can change the schedule at any time by going to the “My Integrations” page, clicking the vertical menu button (![]() ) and choosing ‘Edit’:
) and choosing ‘Edit’:
This action will take you to the ‘Configuration’ step of the integration, where you can change the scheduling configuration:
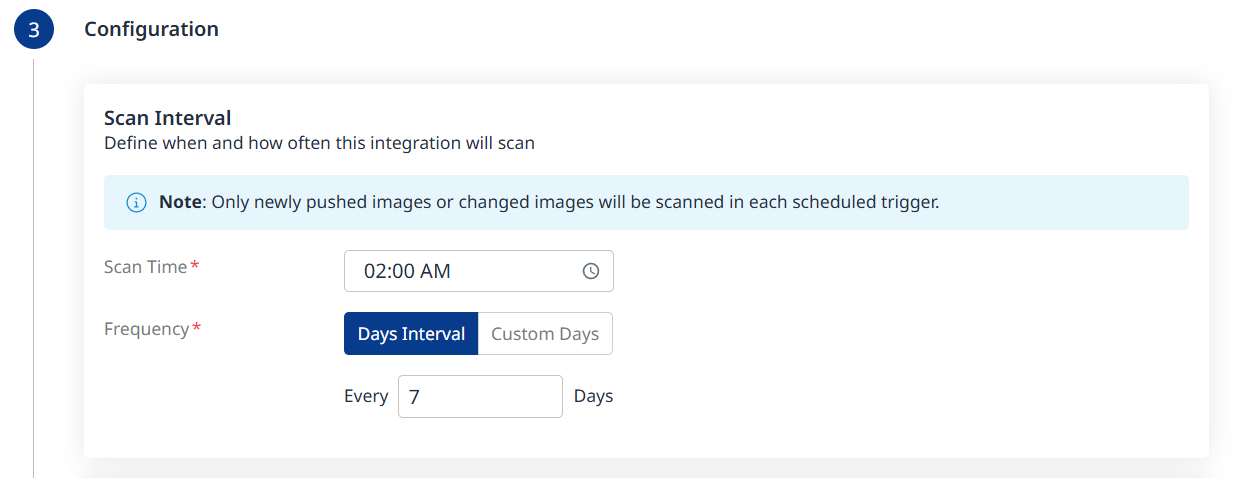
Note: After the first scan (in which the latest 10 tags are scanned), in every scheduled scan only newly pushed images from the registry or changed images will be scanned. This is because vulnerability and package updates occur automatically in an asynchronous manner, keeping the security information up-to-date without requiring new scans.
Click ‘Update’ to save the changes:

Review your private registry integration results
Visit the Review the Container Image Scan Findings within your Organization page for the documentation on reviewing container image scan results in the Mend Platform.
Reference
Supported registries
We support the following platforms for the Mend private registry integration:
Note: Scanning public registries with the Mend registry integration is not supported. Instead, you can scan individual images from Docker API-supported public registries with the Mend CLI using the mend image command.
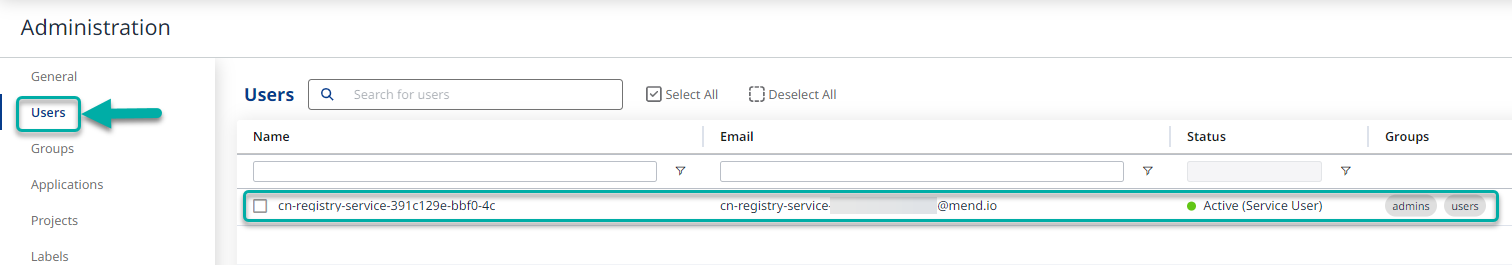
Mend private image registry integration service user
When you configure and activate any of our private registry integrations for the first time, a service user is automatically created within the integrated Mend organization.
The service user will have a name similar to “<cn-registry-service-unique_string>”. This service user is automatically added to the admins Group (with organization administrator permissions) and is required for the integration to function properly.
You can view this service user via the Administration --> Users page.