View the results of your Mend CLI SCA scan
Overview
Once your Mend CLI SCA scan is completed, there are multiple resources provided to help you review, analyze, and triage your results. The following Mend CLI SCA result sections are covered in this article:
Mend CLI SCA results - Console
The Mend CLI SCA scan outputs a summary of the detected malicious packages, security vulnerabilities, and the structure of the dependency tree for your application:
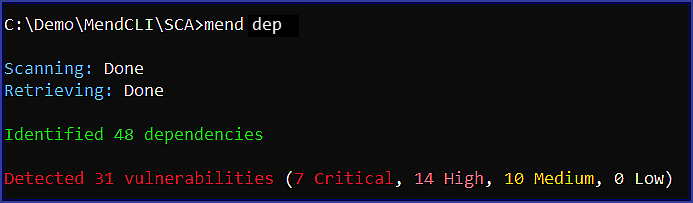
Malicious packages
Malicious packages and their data identified by the Mend CLI are displayed in an easy-to-read table:
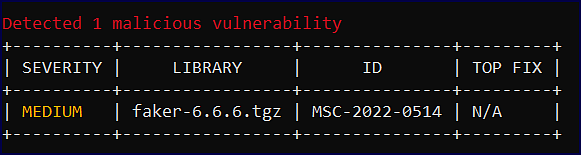
Field | Description |
|---|---|
| The severity of the malicious vulnerability. The available values are:
|
| The name of the library affected by the malicious vulnerability |
| The MSC ID associated with the identified malicious vulnerability. |
| Mend’s recommended fix to confront the malicious vulnerability. |
CVE vulnerabilities
The discovered CVE vulnerabilities are displayed in a visual table, providing the vitals you need to triage these findings:
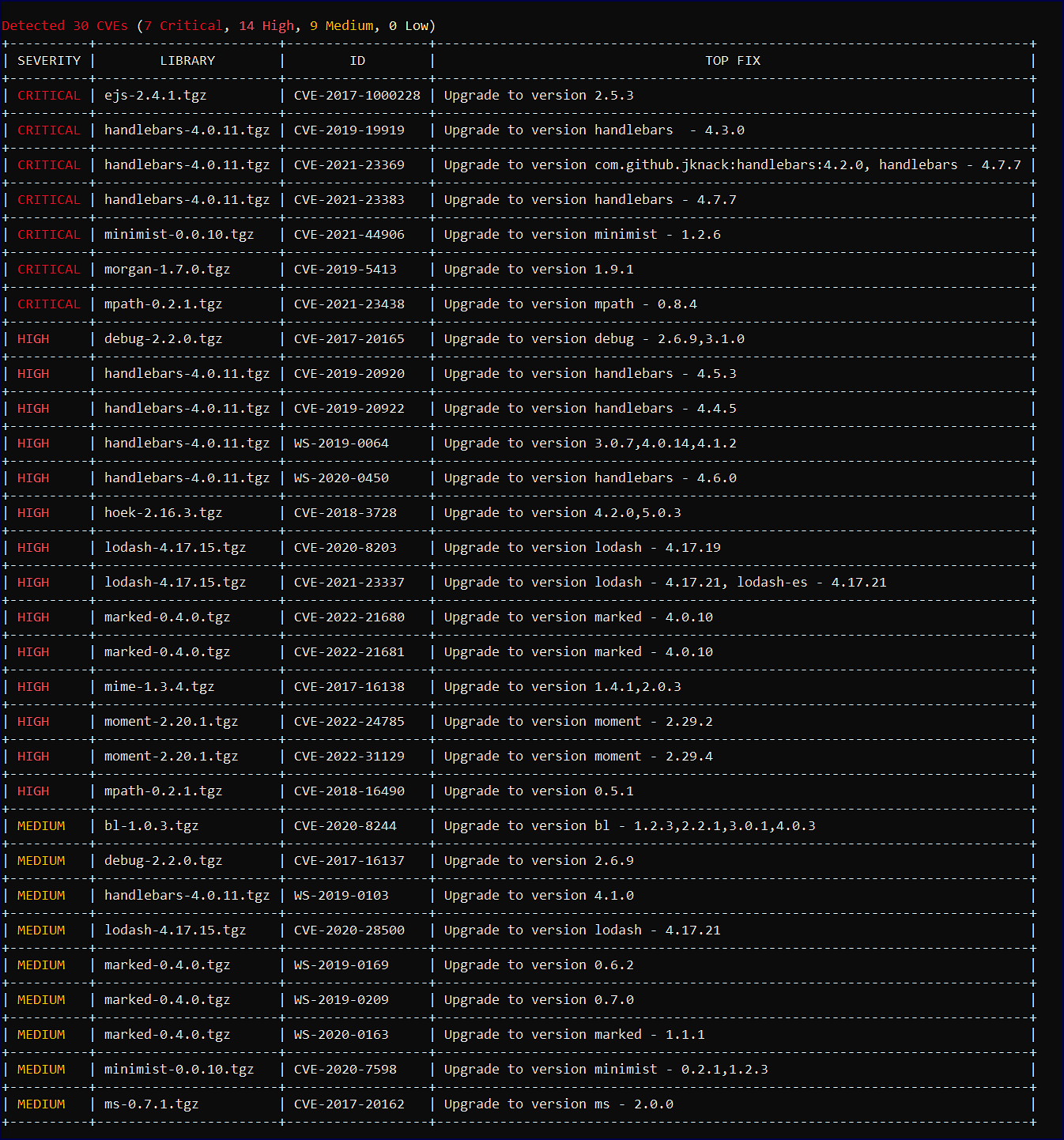
Field | Description |
|---|---|
| The severity of the vulnerability. The available values are:
|
| The name of the library. |
| The CVE ID associated with the identified vulnerability. |
| Mend’s recommended fix to remediate the CVE vulnerability. Tip: Visit our Vulnerability Database to research more info on a CVE. |
Policy Violations
If the Mend CLI scan scope falls under your policy created in the Mend Application, the Mend CLI will print out any violations found in the terminal:
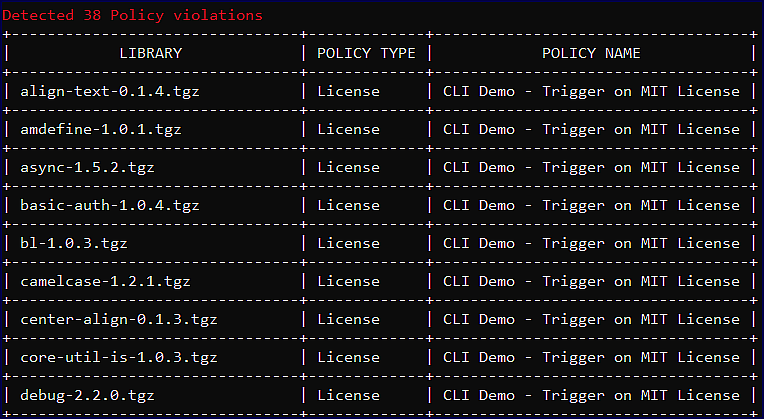
Field | Description |
|---|---|
| The name of the library that violated the policy. |
| The type of policy that was violated. The available values are:
Note: For more information on these policy types, check out our Matching a Policy to a Library documentation. |
| The name of the violated policy. |
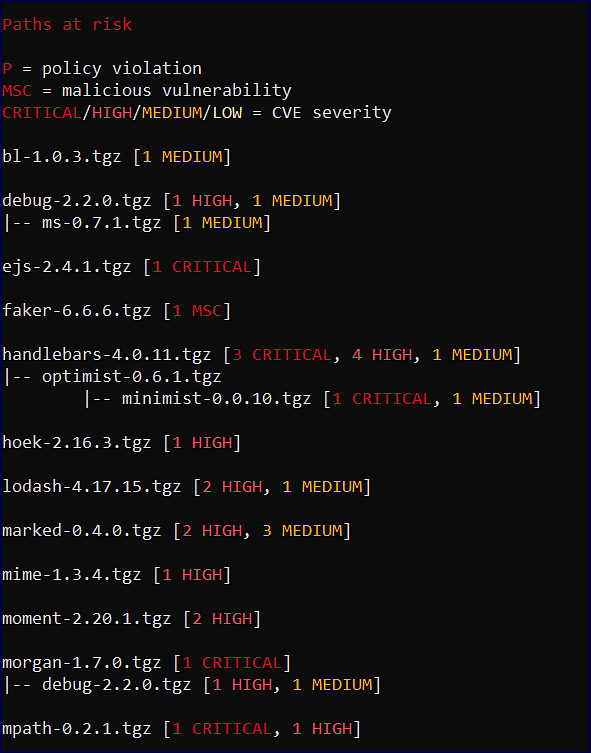
Paths at risk
The “Paths at risk” provides a visual hierarchy of the dependency paths within your project that are affected by a policy violation (P), malicious vulnerability (MSC), or a CVE vulnerability:
Mend CLI SCA results - Mend Application
Note: By default, the Mend CLI SCA results are not automatically uploaded to the Mend Application. To enable this functionality, use the -u (also --update) parameter.
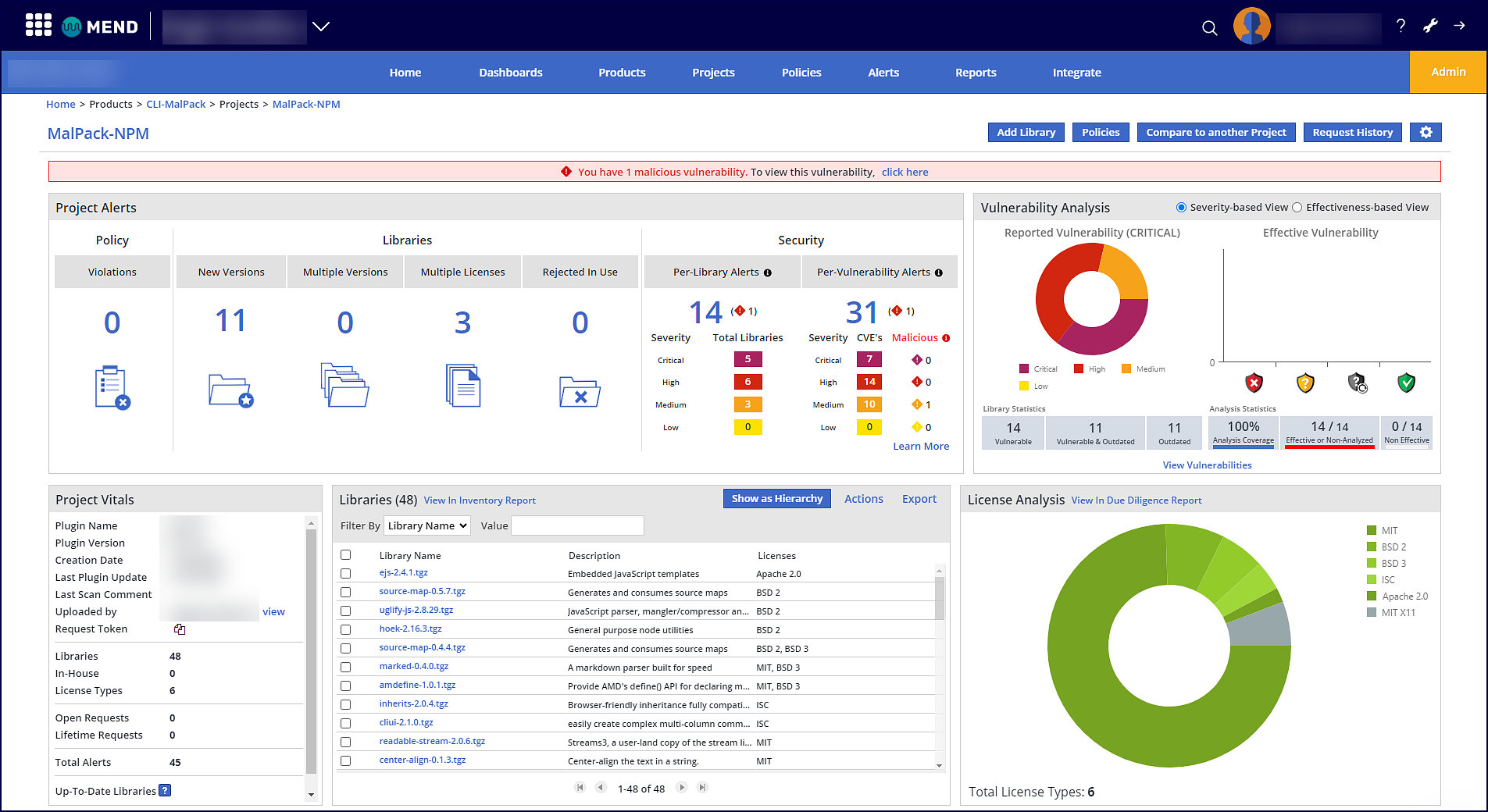
Within the Mend Application, you can review each Mend CLI scan’s summary, details, and more. For more information on how to navigate the Mend Cloud Native Application, visit our Mend Application documentation:
Mend CLI SCA Logs
At the end of the Mend CLI SCA scan, there is a Support token that can be provided to Mend Support and is extremely helpful for troubleshooting purposes.
The Mend CLI stores SCA scan logs in the .mend/logs/sca directory.
