Working With the Web-Based Application
Overview
The Mend Home page provides immediate visibility of your organization’s open source inventory (open source files), together with potential security vulnerabilities, license compliance, and easy-to-understand dashboards.
The following type of information is displayed on the Mend Home page:
A dedicated summary count of system category alerts reported for a given Organization, Product or Project, including the total count of policy violations, versions, licenses, quality, and security alerts.
An up-to-date overview of security risks and their severity for your components across all products (applications).
A list of the products and the number of projects and libraries per product. By default, the top 10 products with the most projects are displayed.
Detailed information about the product libraries (components).
License distribution data in which you can see the license resolution in your organization and check for licenses that might not comply with your company’s policy.
A list of unanswered update requests sent from the plugins regarding new libraries.
A list of update requests sent by the user from the plugins regarding new libraries.
NOTE: By default, all products are visible on the dashboard. If you want to prevent specific products from being seen by specific users or groups, you must update the product page.
Accessing the Home Page
The Mend Home page opens immediately after logging in to Mend. If required, you can change the default Home page that will be displayed when you log in.
For example, to change the Home Page to the All Products page, do the following:
From the menu bar, select Products > View All. The All Products page is displayed.
Select Set as Home Page. The All Products page will be your homepage beginning at your next login.
To reset the initial home page, clear the Set as Home Page checkbox at the top right of the page.
Organization Alerts
The Organization Alerts pane enables you to view a dedicated summary count of system category alerts reported for a given Organization, Product, or Project, including the total count of policy violations, versions, licenses, quality, and security alerts. Additionally, you can click each alert type to display an Alert View corresponding to its category, enabling you to perform selected actions on the listed alerts (e.g., ignore alerts).
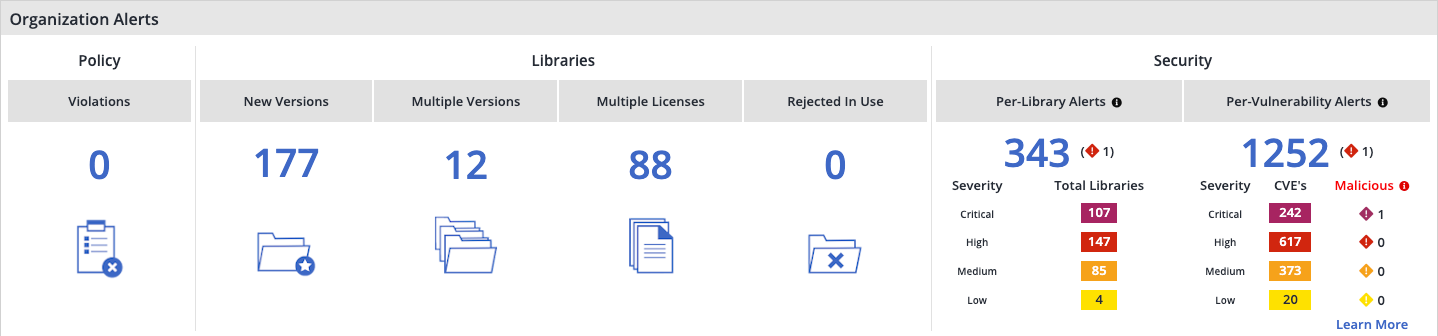
By clicking the icon or summary number in a category, an Alert View will be displayed listing alerts filtered to the relevant category:
For Policy and Libraries alert types, the Alert View will be displayed in the Licensing and Compliance Alertsscreen.
For Security alert types, the Alerts view will be displayed in the Security Alerts: View by Library or Security Alerts: View by Vulnerabilityscreen.
Note: In the Security Per-Library Alerts section, each severity level shows the number of libraries where that severity is the highest (Critical, High, Medium, or Low).
For example, clicking Multiple Versions will display the Licensing and Compliance Alerts screen listing only alerts of multiple library versions.
The following table describes the alert type categories:
Alert Type | Category | Description |
|---|---|---|
Policy | Violations | An alert is triggered upon meeting a condition inconsistent with defined policy. |
Libraries | New Versions | An alert is triggered for any scanned library found to be out-of-date (i.e., not having the latest version). |
Multiple Versions | An alert is triggered for any library that appears twice or more in different versions within a certain product. | |
Multiple Licenses | An alert is triggered for any library that has more than one license. | |
Rejected in Use | An alert is triggered for any library that created a request which was later rejected. | |
Security | Per-Library Alerts | The total number of libraries with alerts (regardless of project occurrences). For example, the alert count for a Product with two Projects where each features an alert for the same library will be "one" and will be displayed in one row noting two project occurrences. The color scheme is as follows:
|
Per-Vulnerability Alerts | The total number of vulnerability alerts (e.g., a CVE alert). For example, the alert count for the same CVE recorded in three separate occurrences will be "one", and will be displayed in one row noting three occurrences. The color scheme is as follows:
|
Vulnerability Analysis
The Vulnerability Analysis pane provides an analysis of your organization’s vulnerabilities.
The Vulnerability Analysis pane comprises the following sections:
Reported Vulnerability: Shows the library distribution based on the highest vulnerability severity – Critical, High, Medium, or Low.
Clicking on the pie chart launches the Security Alerts: View by Library screen, where you can review vulnerability statistics, such as the number of reported vulnerabilities and ignored alerts for a selected library, and ignore and activate (restore) a selection of vulnerability alerts associated with a library.Effective Vulnerability: Shows the vulnerability severity distribution based on an effectiveness indicator (i.e., shield).
You can select to view the effective vulnerability in two modes: Severity-based view (includes severity) or Effectiveness-based view
Clicking on the Effective Vulnerability graph launches the Security Alerts: View by Vulnerability screen, where you can manage the alerts per vulnerability according to specific products/projects. For example, use this screen to ignore alerts of a specific vulnerability across all libraries in the selected scope.
Library Statistics:
o Vulnerable: The total count of vulnerable libraries.
o Vulnerable & Outdated: The total count of outdated and vulnerable libraries (counts the libraries that have newer versions and include vulnerabilities).
o Outdated: The total count of outdated libraries (counts the libraries that have newer versions).
Analysis Statistics:
o Analysis Coverage: The percentage of analyzed libraries (excluding libraries marked with a gray shield) from the total count of libraries that can be analyzed.
o Effective or Non-Analyzed: Overall Effective Vulnerability Index which reflects the relative portion of security alerts that are not marked with a green shield.
o Non-Effective: Non-Effective Vulnerability Index which reflects the relative portion of security alerts that are marked with a green shield.
Product Summary (Top 10)
The Top 10 Products section lists the products and the number of projects, the number of libraries, the number and severity of vulnerable libraries, and the number of licenses per product. By default, the top 10 products with the most projects are displayed.
Clicking a product will display its product page. For details, see Understanding the Library Details Page.
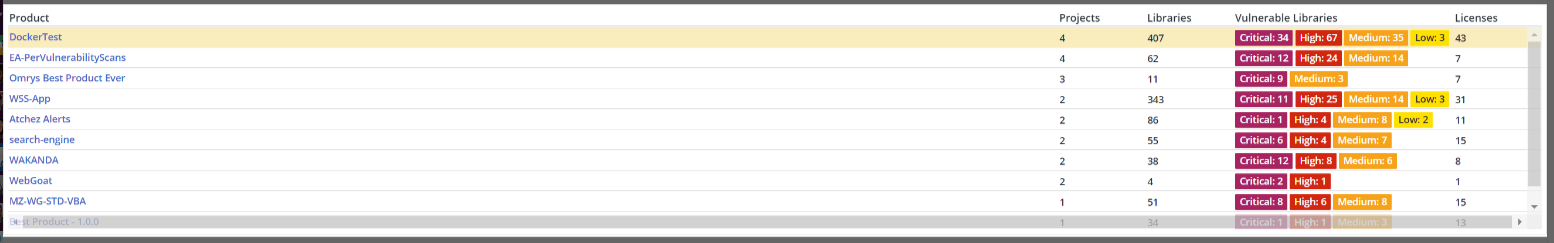
Clicking a library changes the License Distribution to reflect the selection, as displayed in the License Distribution pane (see directly below).
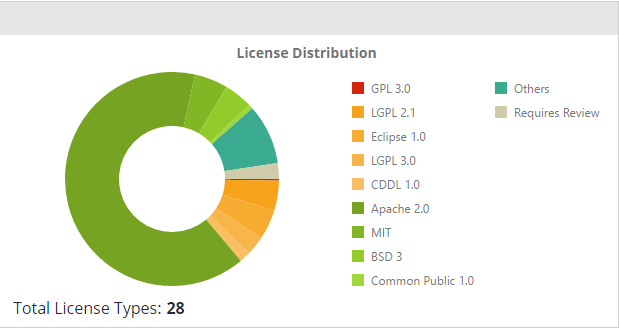
License Distribution
This pane provides license distribution data in which you can see the license resolution for products in your organization, and enable you to check for licenses that might not comply with your company’s policy.
For a selected product, the License Distribution chart displays:
Total number of license types for the product.
A pie chart showing the distribution of licenses. Hovering on a section in the chart shows the number of licenses of that type and its percentage out of all the licenses.
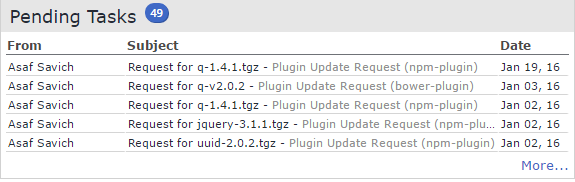
Pending Tasks
Pending Tasks display the unanswered update requests sent from the plugins for new libraries that are added to your inventory.
Clicking More.. directs you to the Organizational Pending Tasks page, where you can select one or multiple pending tasks, and then click More Information (relevant only in Vulnerability-based Alerts organizations). The Library Vulnerabilities and Licenses pop-up screen is displayed, enabling you to view the number of vulnerable libraries plus license information for the selected components.
User Requests (Requested by Me)
The Requested By Me table displays the update requests sent by the user from the plugins regarding new libraries.
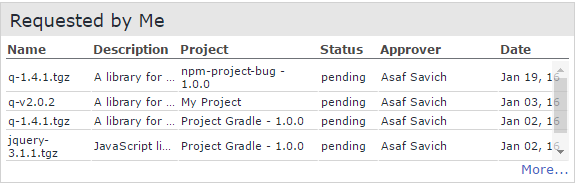
Clicking More… directs you to the Requests History Report which provides details about all requests in an organization for all statuses.
See Also:
