View the results of the Mend for Azure Repos SCA scan
Overview
Once your Mend for Azure Repos SCA scan is completed, multiple resources are provided to help you review, analyze, and triage your results.
Mend Check
Once the Mend for Azure Repos SCA scan is completed, the Mend checks are updated with the results. The Mend Security Check and the Mend License Check include a Scan token, which you can provide to Mend Support for troubleshooting.
Mend Security Check
The Security Report within the Mend Security Check populates within an overview of vulnerability findings within the commit:
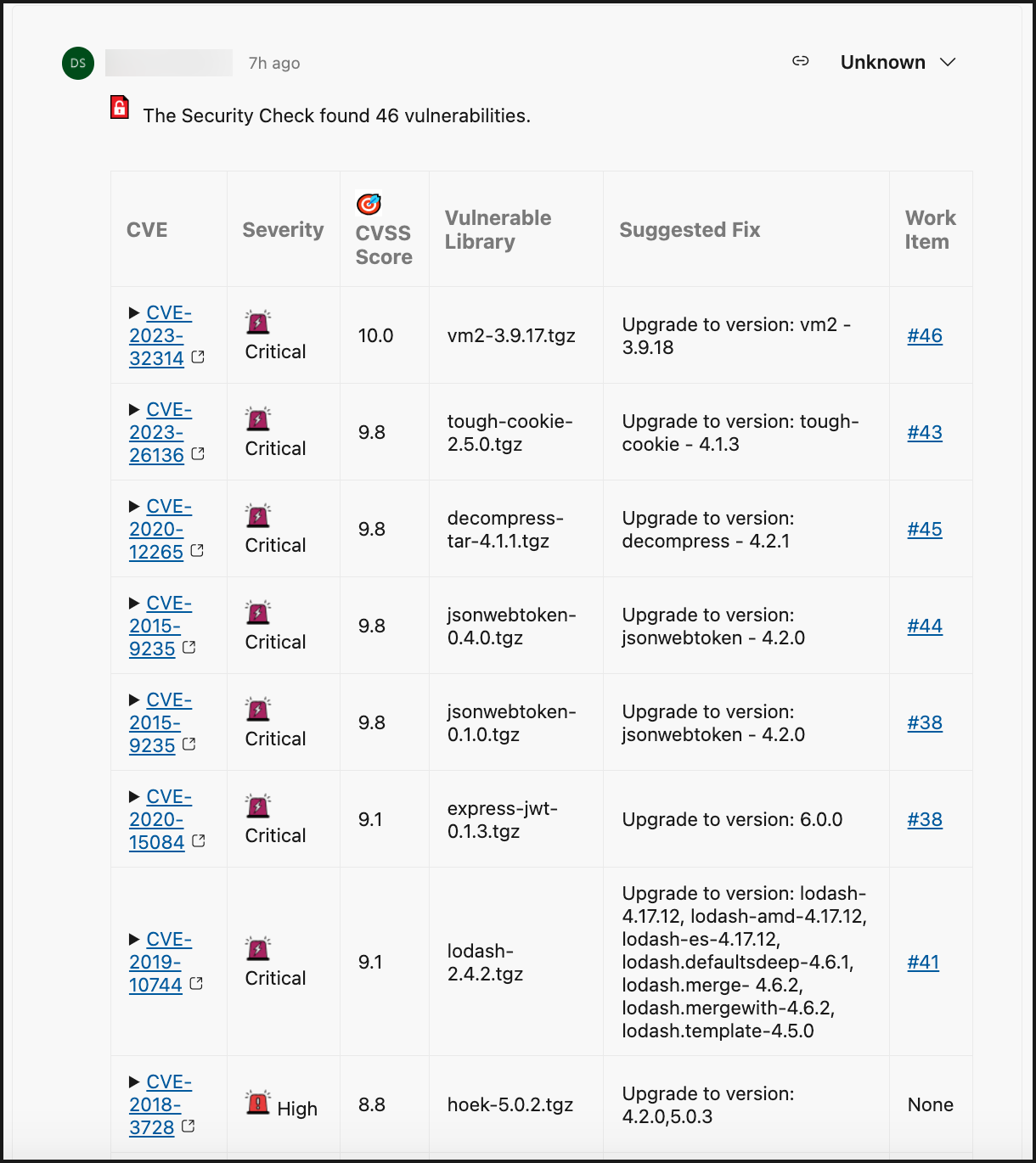
CVE: CVE ID of the vulnerability. This links to CVE’s page on Mend’s official database site.
Severity: Level of severity of the vulnerability (
Critical,High,Medium,Low)CVSS Score: CVSS Score (CVSS 3).
*Exploit Maturity: The Exploit Code Maturity (Proof of concept, Functional and High are reported by Mend as exploitable).
*EPSS: The EPSS percentage (probability of a vulnerability to be exploited)
Vulnerable Library: Name of the open-source component impacted by the vulnerability.
Suggested Fix: Fix suggestion to resolve the vulnerability.
Work Item: URL to the related Azure Repos Work Item that was created for the policy violation.
*Applicable when the exploitability flag is enabled, when a vulnerability contains exploitability data
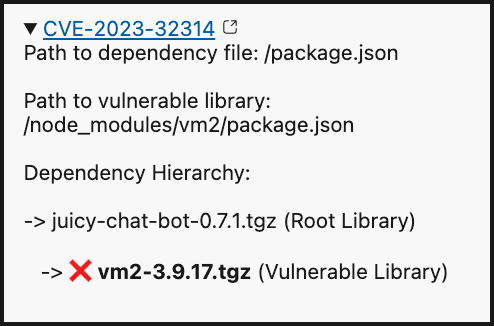
You can also click the dropdown arrow next to each CVE for more details:
Mend License Check
If you have the license violation analysis enabled as part of your SCA scan, the License Report within the Mend License Check will populate with any policy violation findings on the Commits page:
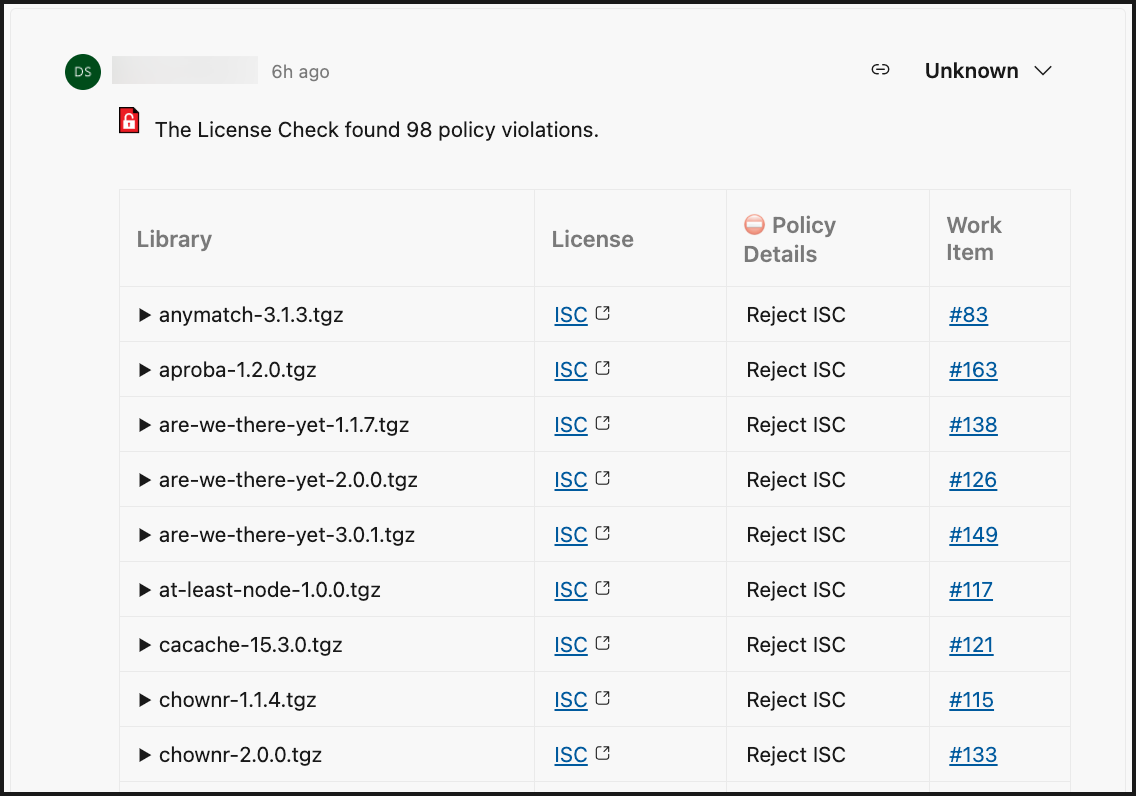
Library: Name of the open-source component impacted by the policy violation.
License: License type that was detected
Policy Details: Name of the license policy violation as defined in the Mend SCA UI, along with the policy level (Organization/Product/Project).
Work Item: URL to the related Azure Repos Work Item that was created for the policy violation.
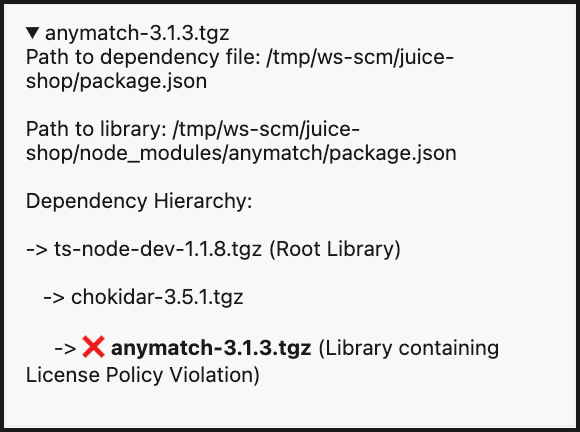
You can also click the dropdown arrow next to each library for more details:
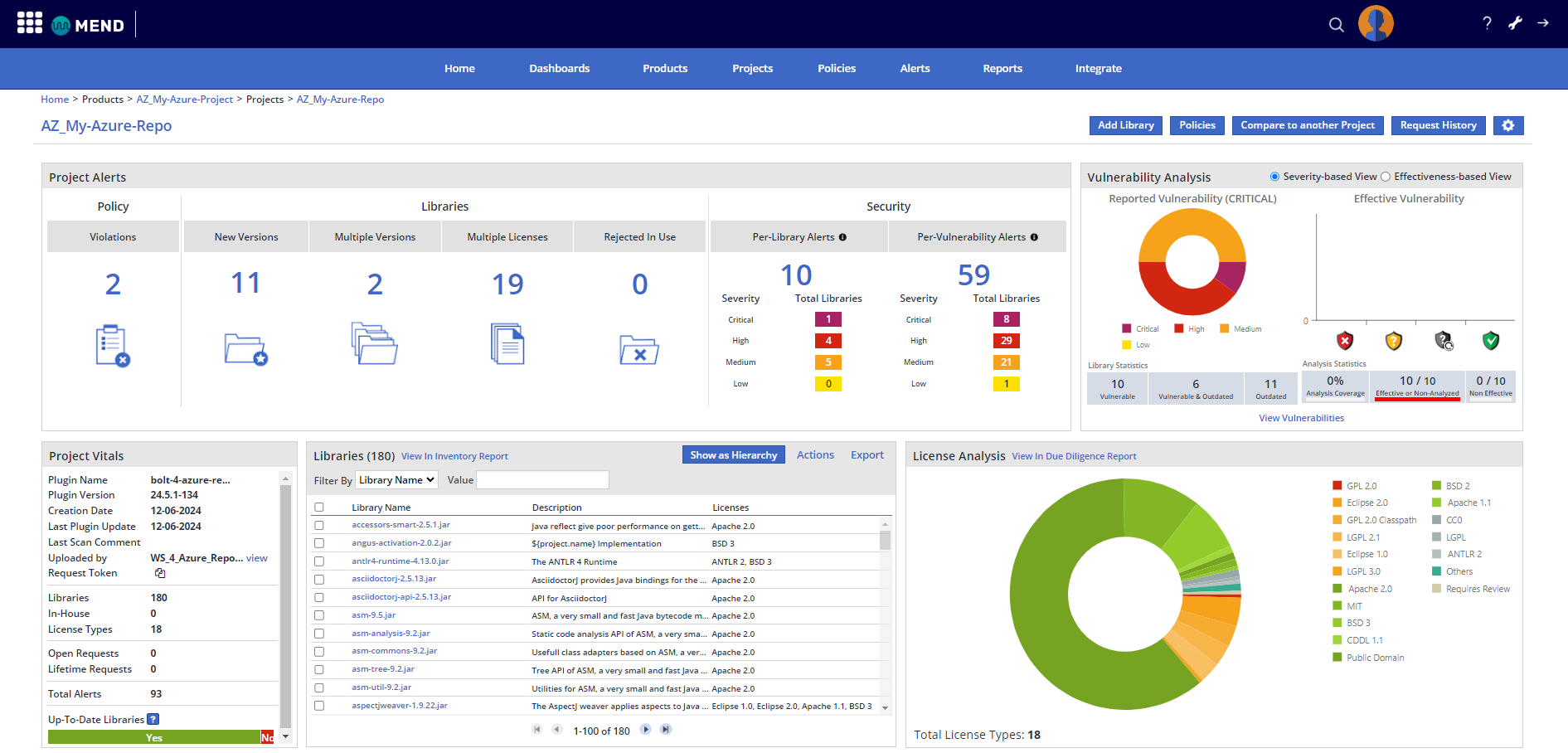
Mend SCA Application
This section differs between the Mend AppSec Platform and the Legacy SCA Application.
The Legacy application instructions are listed at the bottom of this section.
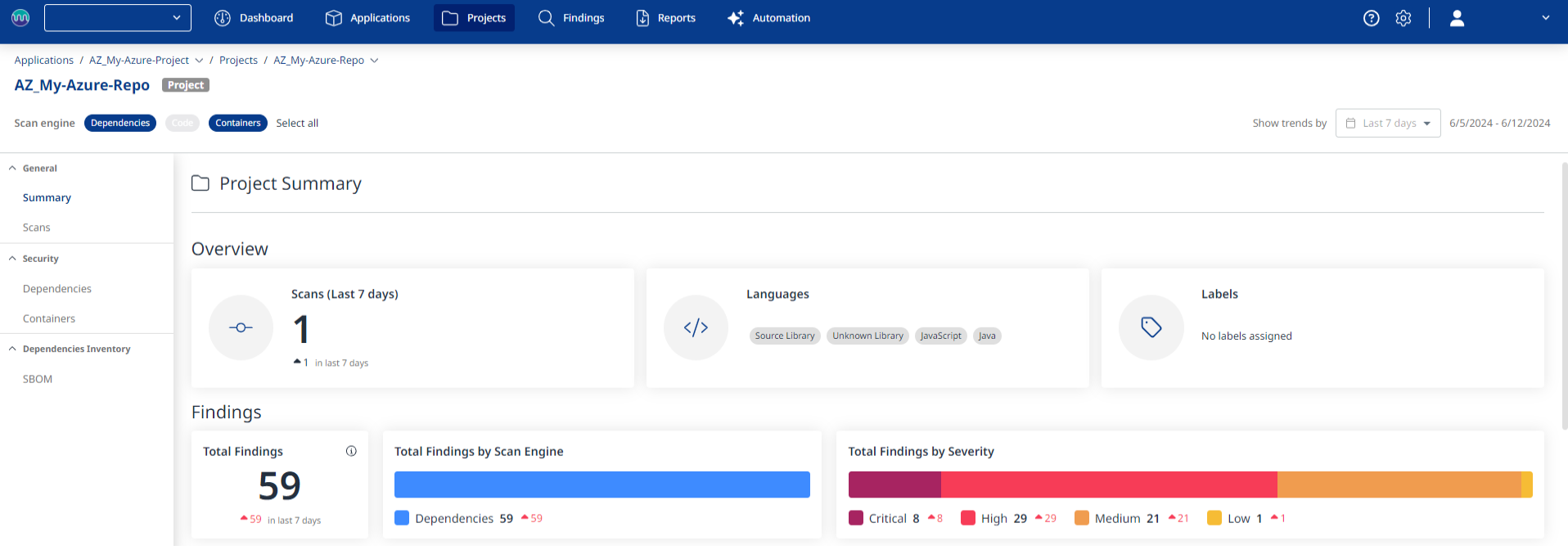
Within the Mend SCA application, when a scan is completed, a Mend application is created for each Azure DevOps project where the repo that was scanned resides. Similarly, for each branch defined in your baseBranches parameter, a Mend project is created for that branch. For both, Mend application and project, the name is prepended with an “AZ_" prefix. Let’s look at an example:
Azure DevOps hierarchy:
My-Azure-Project
My-SCA-Repo repository
mainbranch [default branch].whitesource file with
"baseBranches": ["main", "dev"]
devbranch
We run a scan on both the main and dev branches. The Mend hierarchy appears as follows:
Mend Platform Application hierarchy:
Application: AZ_My-Azure-Project
Project: AZ_My-SCA-Repo (the default branch does not get the “
_<branchname>" suffix)Project: AZ_My-SCA-Repo_dev
You can review each Mend for Azure Repos scan’s summary, details, and more. For more information on how to navigate the Mend application, visit our Analyze your results in the Mend Application documentation:
Azure Repos Work Item
If you are performing Pull Requests or push commands via the Web browser, refresh your Web browser to view the work items that were generated by Mend SCA Scan.
Note: It may take several minutes for the work items to be scanned and displayed after a valid push command is initiated.
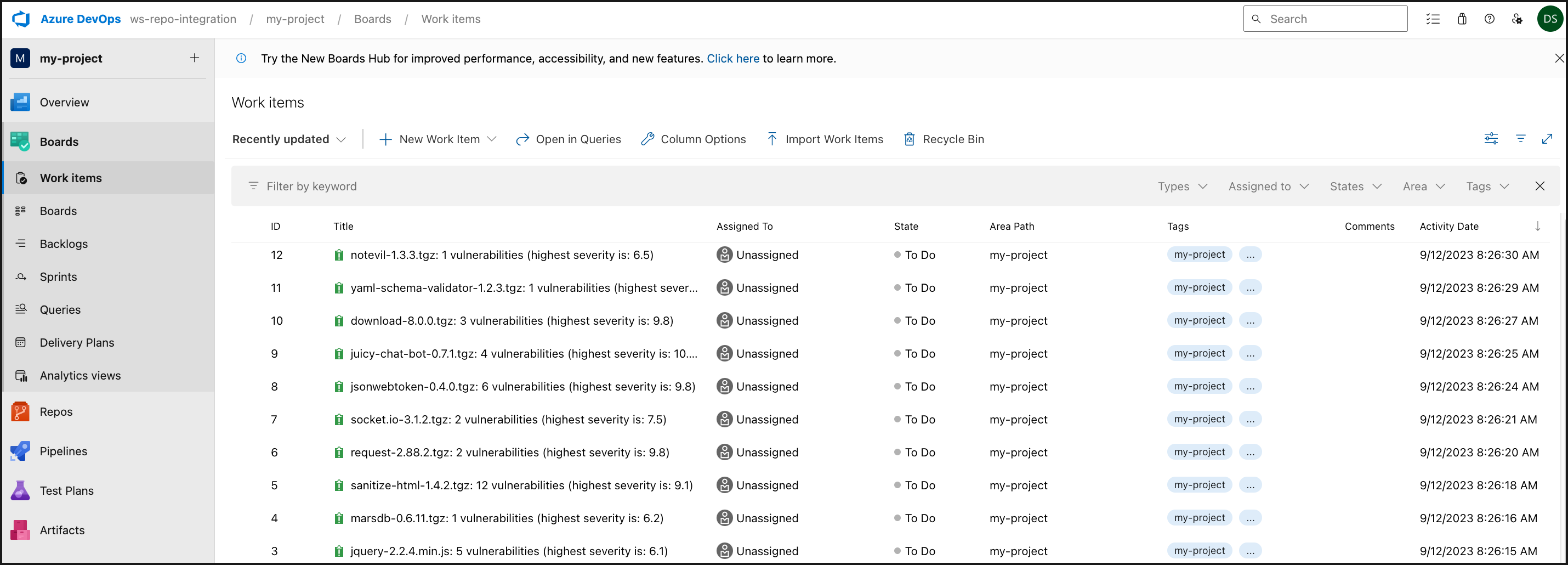
The Work Items section displays all the issues that Mend SCA Scan detected with the security vulnerability tag and a tag indicating a repository in which the issue was found. These proprietary labels indicate that a security vulnerability was detected by mend.
The created Work Item type depends on the Process that was used in the project, as follows:
Basic, Agile, and CMMI: Issue
Scrum: Impediment
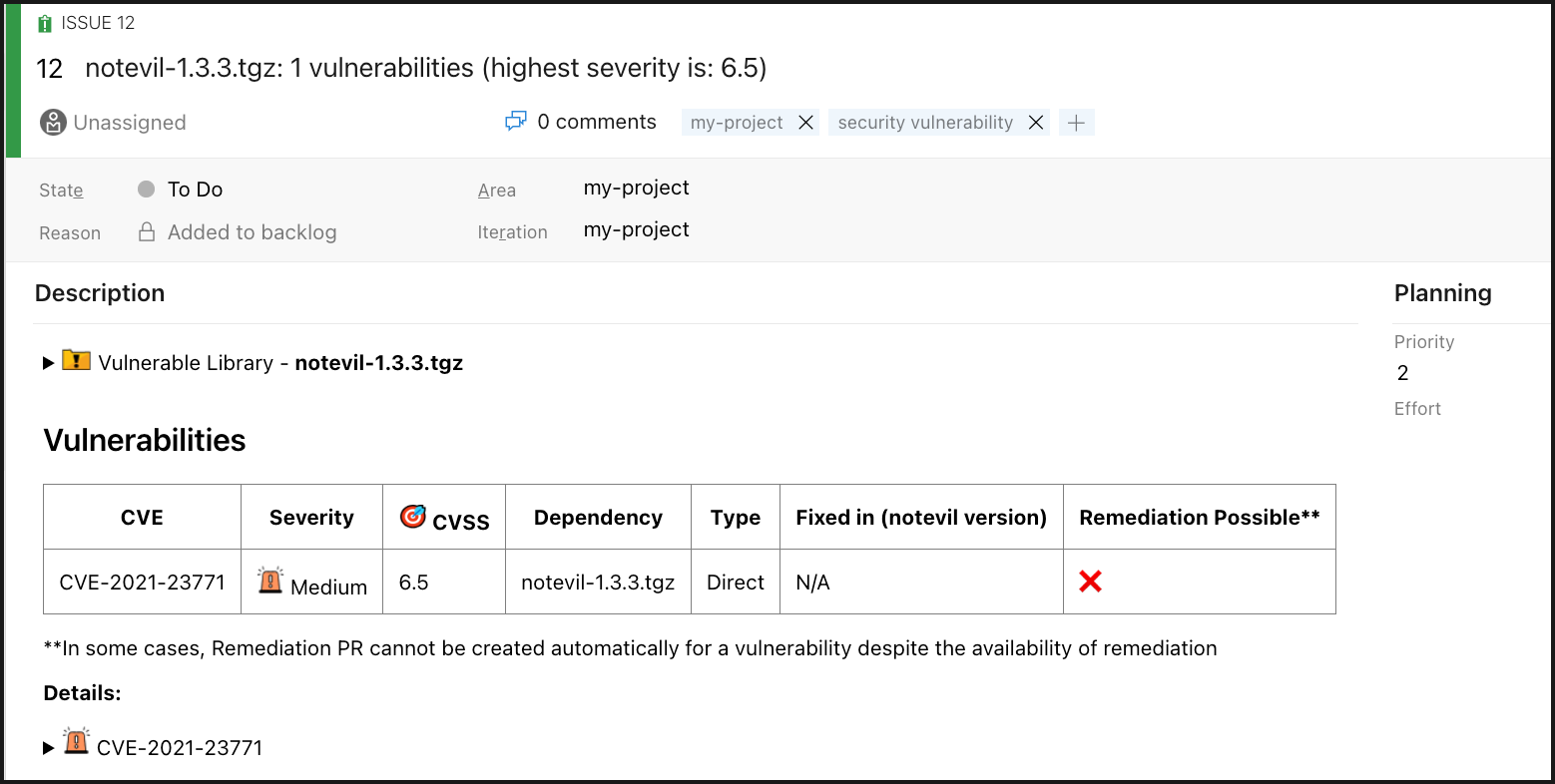
You can also create Area paths to group Work Items by team, product, or feature. This can be configured via the parameter customFields within the issueSettings configuration. Here’s an example of setting the area path:
"customFields": {
"Area Path": "test-2\\Area1\\SubArea1"
}
Notes:
Work items that were manually closed will not be re-opened during future Mend scans unless their tag and/or name have been changed.
As part of your workflow, you have the option to manually add a relevant tag(s) to specific work items, and close work items that were resolved.
Azure Repos Pull Request (PR)
Mend Remediate Pull Request
Note: By default, Remediate Pull Requests are created with the “security fix” tag.
If Remediate is enabled, and remediation is available for an identified open-source vulnerability, a remediate branch called whitesource-remediate/<nameofcomponent>will automatically create a Pull Request with actions included in the commits to resolve the vulnerability:
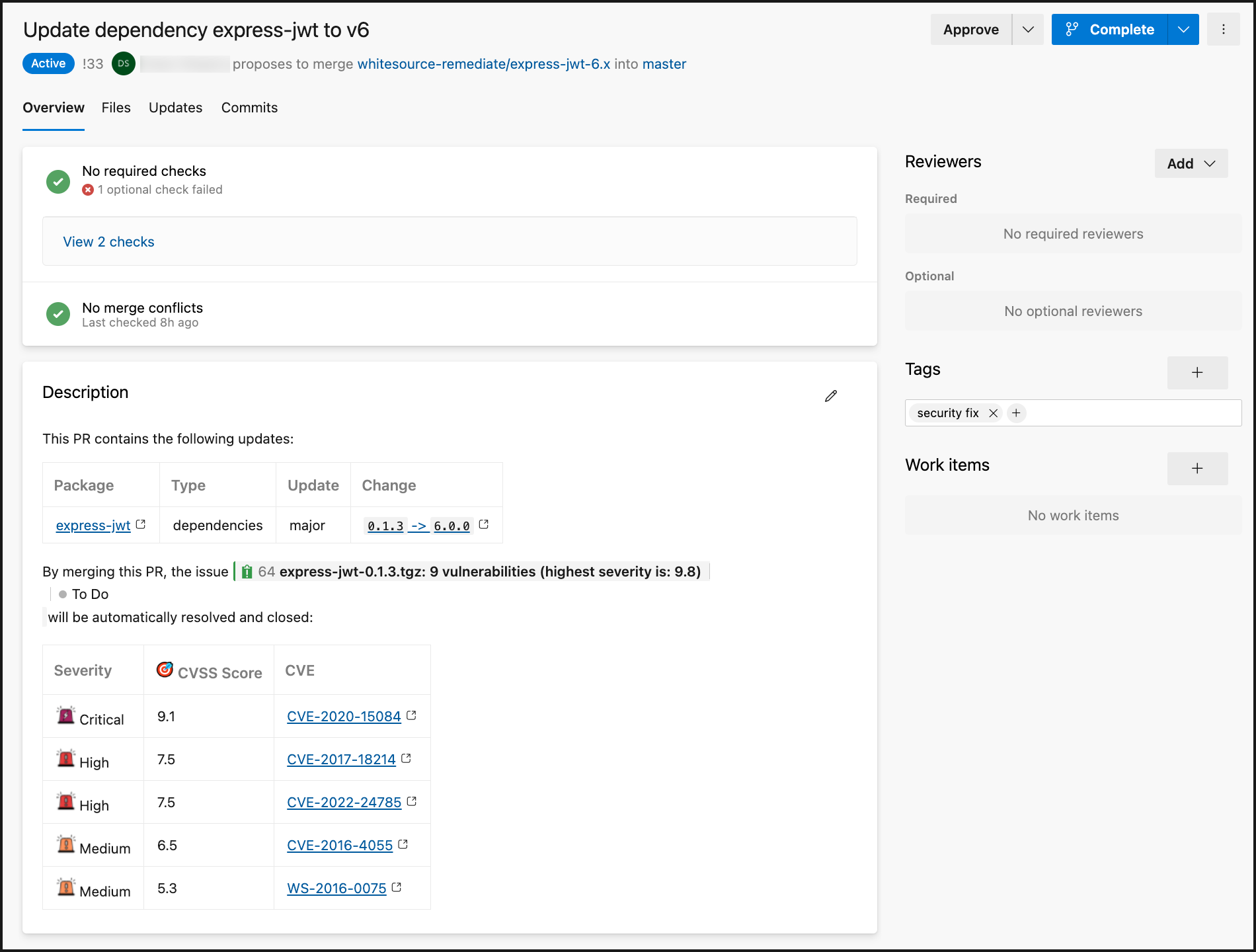
Summary:
Package: Name of the open-source component. Includes URL to the vendor and source pages.
Type: Type of Remediate update
Update: Update action
Change: Details on what is being changed
A note is included that links to the Azure DevOps Repos issue will be automatically closed when this Remediate PR is merged.
Vulnerabilities table: Lists the vulnerabilities that will be resolved with the merge of this Remediate PR.
Severity: Level of severity (Critical, High, Medium, Low)
CVSS Score: CVSS score of the vulnerability
CVE: CVE ID of the vulnerability. This links to CVE’s page on Mend’s official database site.
Release Notes: Includes URLs to compare the changes between the versions of the open-source component.
For rebasing/retrying the Remediate PR, select the “If you want to rebase/retry this PR, check this box” option: