View the results of your Mend Developer Platform SAST scan in Azure DevOps Repos
Overview
Once your Mend Developer Platform SAST engine scans are completed, there are multiple resources provided to help you review, analyze, and triage your results.
Viewing Details of the Scan
Results can be viewed in the following places:
The Work Items section in your Azure DevOps Repos project
Mend Developer Platform UI
The Mend Platform UI
Via email notifications
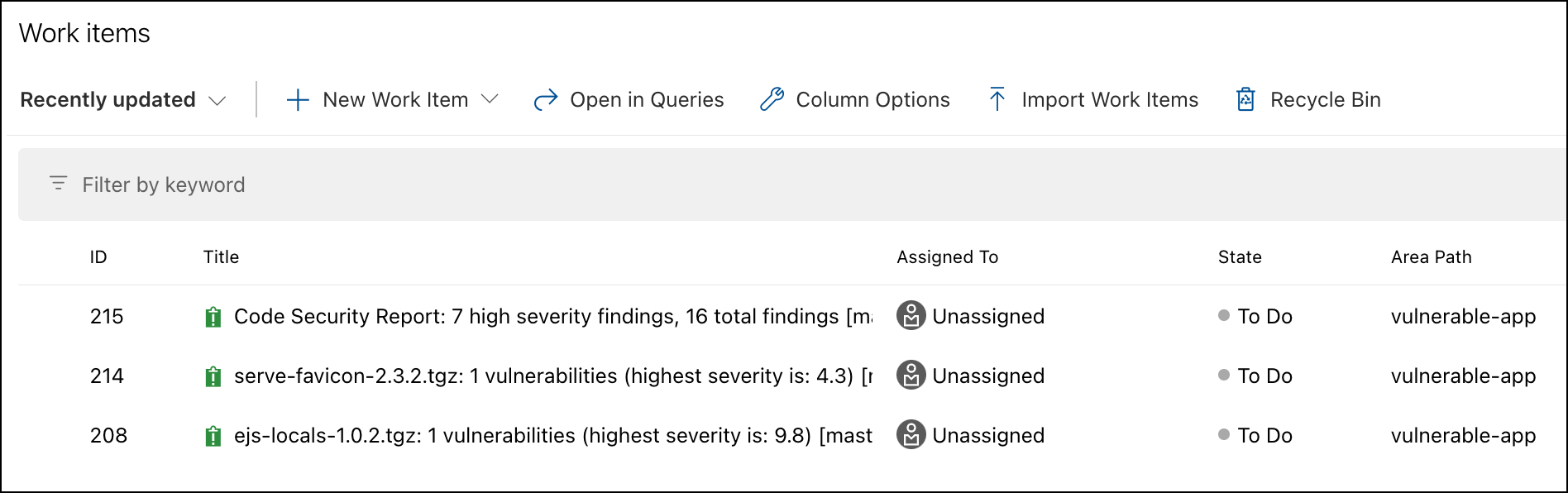
Viewing the Work Items section
Work Items are located under the Boards section in the left panel of Azure DevOps Repos. If you do not see the Boards section, please go to Project settings → Azure DevOps services and enable Boards for this project. Admin rights for this project are required.
If you are performing Pull Requests or push commands via the Web browser, refresh your browser in order to view the issues generated by Mend.
Note: After a valid push command is initiated, it may take a few minutes for the issues to be scanned and displayed.
The Work Items section displays all the issues that the Mend Integration detected. As part of your workflow, you have the option to close resolved items. Work Items manually closed will not be re-opened during future Mend scans unless their tag and/or name are changed.
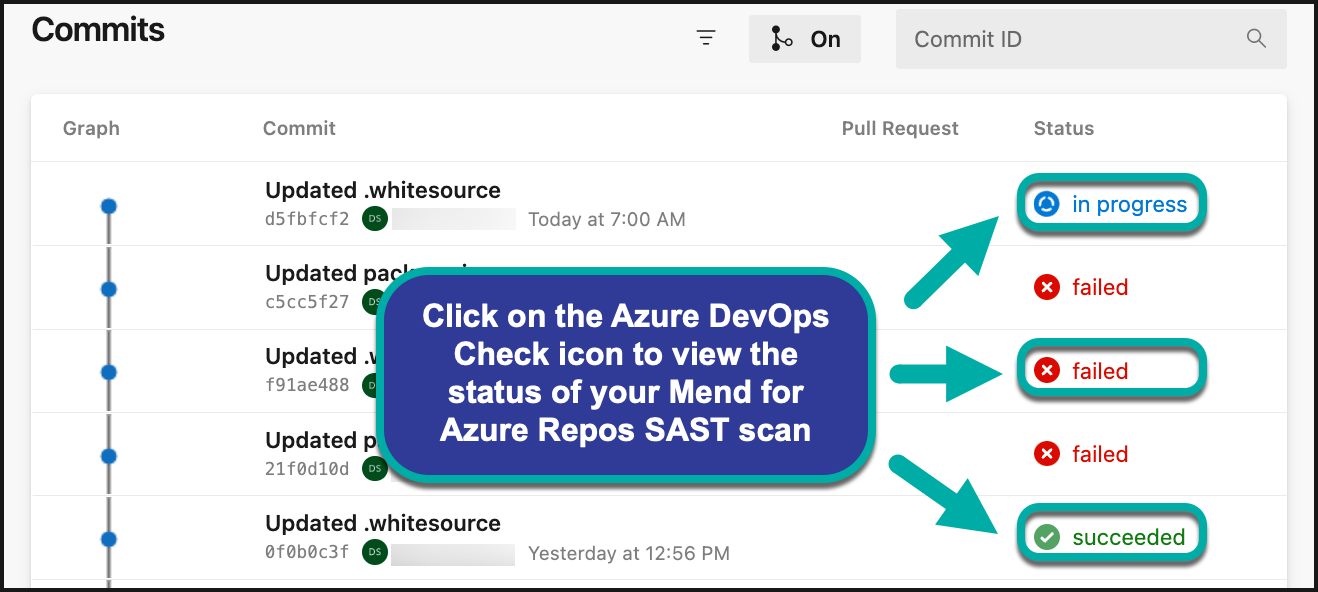
Viewing Mend Code Security Check
Once Code Security Check is running, Status Check messages are displayed for each commit. Clicking a specific security check message opens a related head commit with detailed information about detected findings:
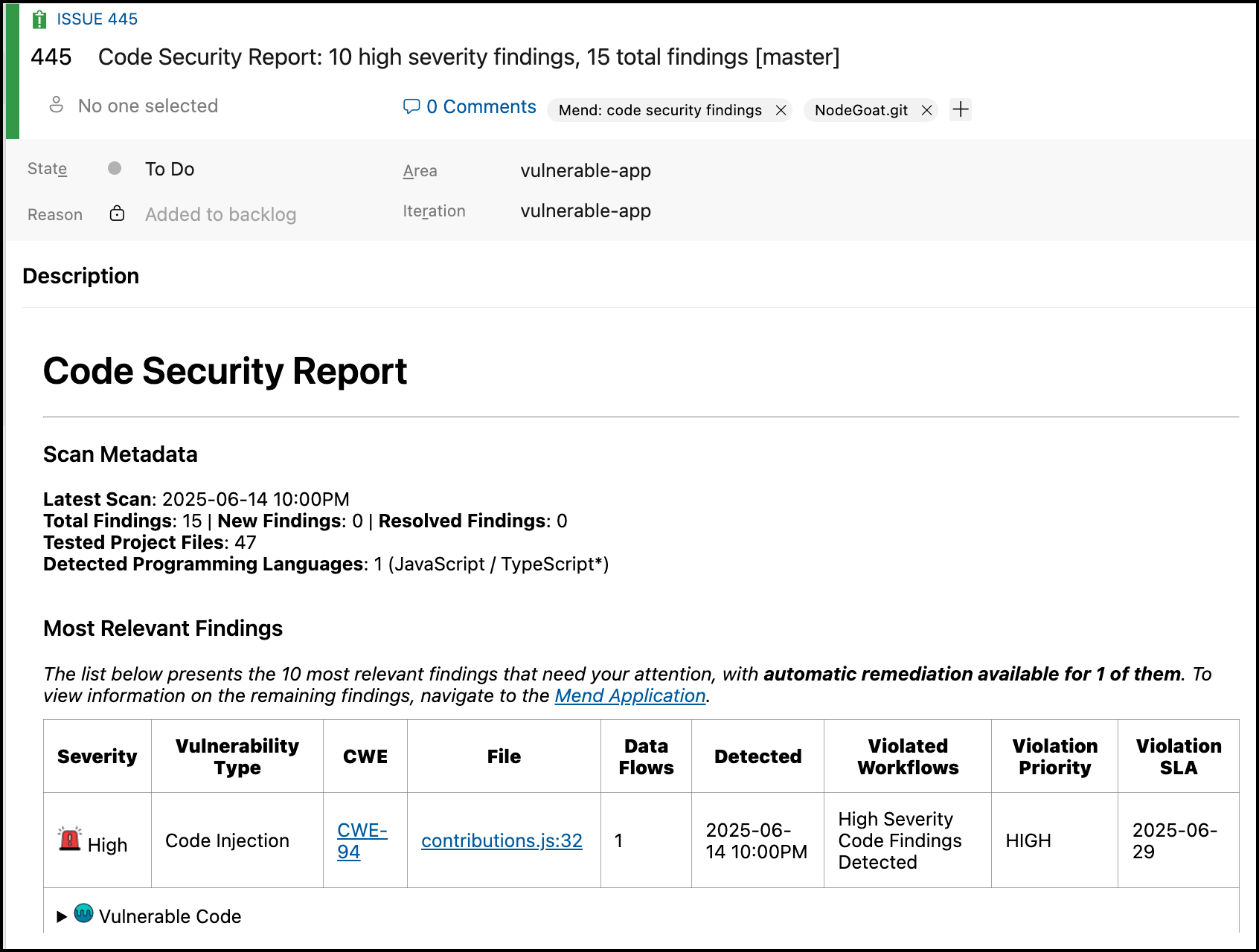
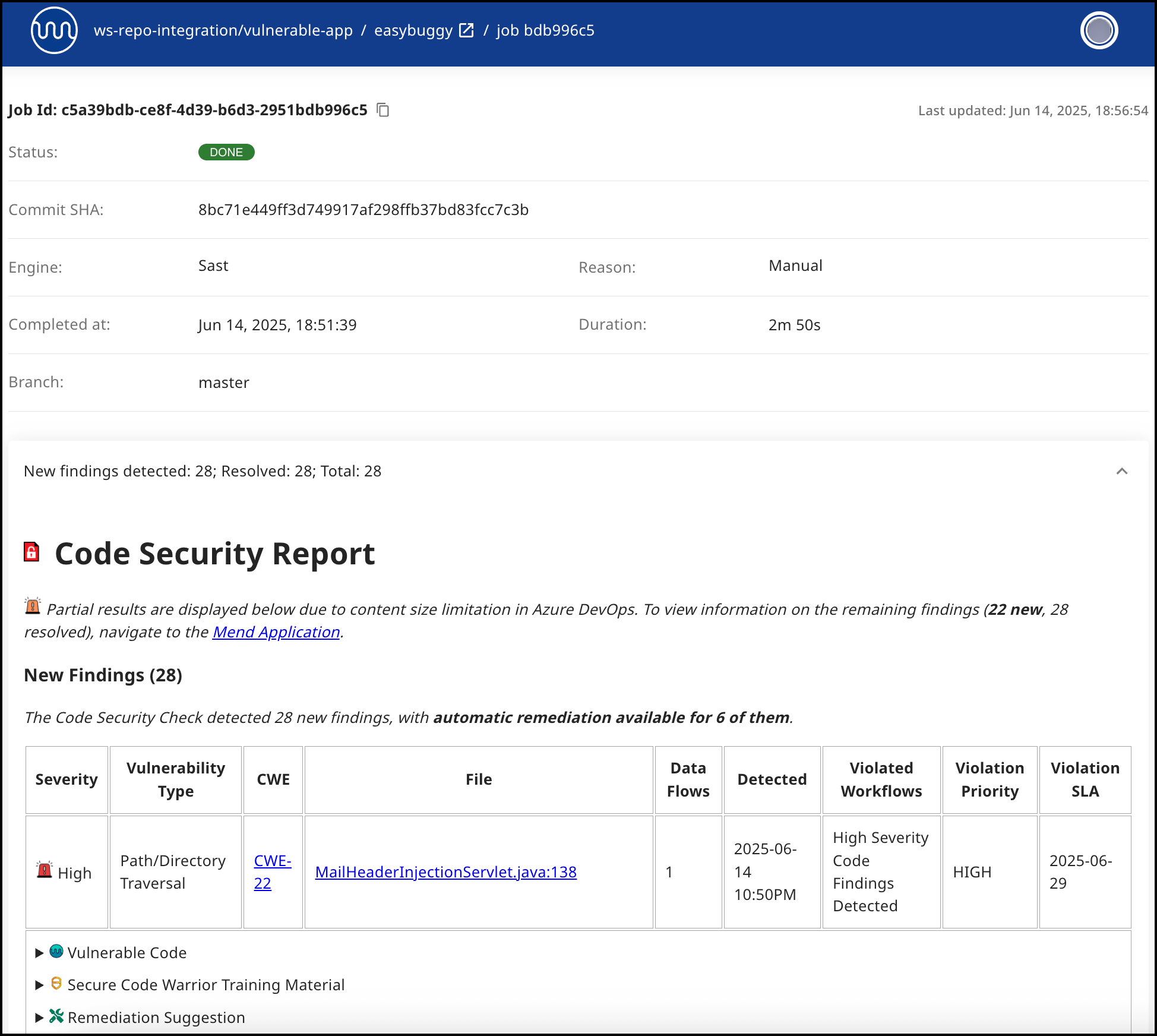
Code Security Report
The Code Security Report displays each CWE to see the code snippet in your project and the details of each vulnerability. The following information is displayed for each vulnerability:
Severity: Level of severity (
High, Medium, Low) of the introduced vulnerability.Vulnerability Type: The type of vulnerability that was introduced.
CWE: CWE ID that was introduced. This links to the CWE’s page on the official MITRE site.
File: File and code line(s) that are impacted by the vulnerability
Data Flows: Number of data flows detected that lead to the finding.
Detected: Date and time the vulnerability was originally introduced (
YYYY-MM-DD 00:00).Violated Workflows: The name of the Automation Workflows that triggered the violation.
Workflow Priority: The priority level defined for the triggered Workflow.
Workflow SLA: Defines the required resolution time that was set for the triggered automation workflow.
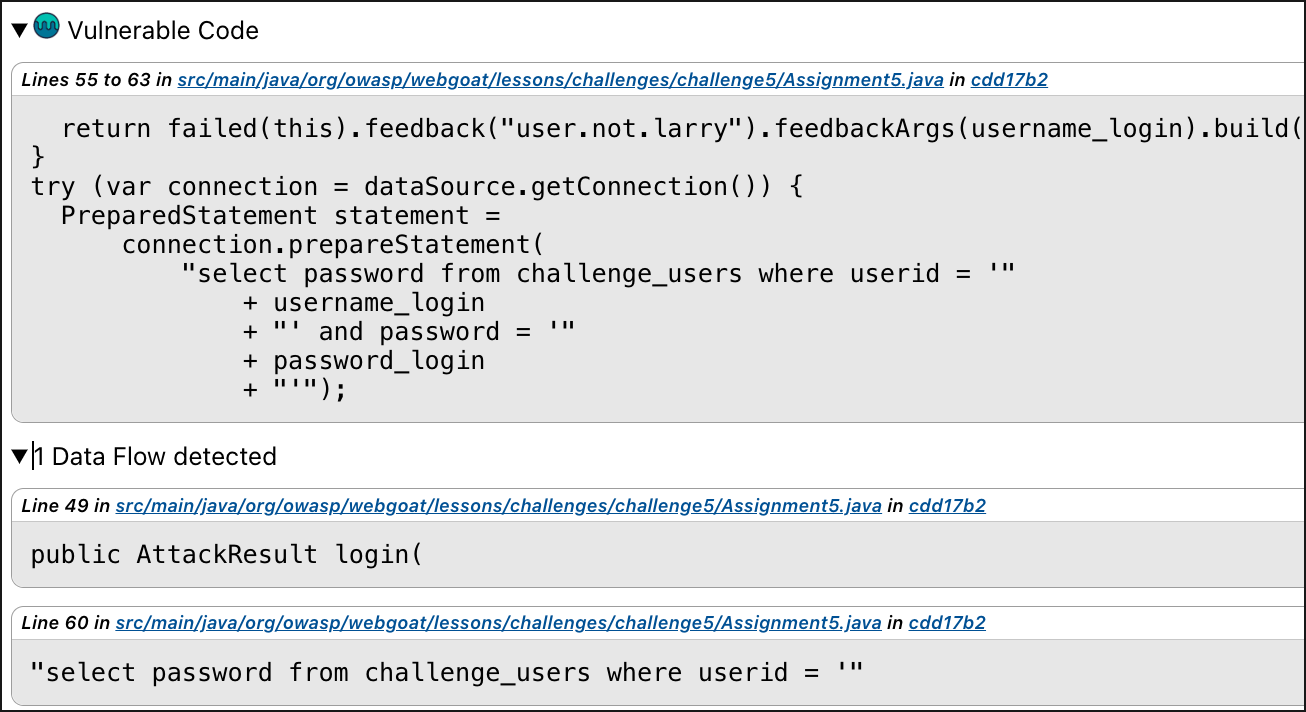
For each detected finding, the Code Security Check adds specific information about the vulnerable code, the data flow, and security training materials provided by Secure Code Warrior.
In the Mend Code Security Check, click Vulnerable Code to expand and see the Data Flow details:
When clicking on Secure Code Warrior Training Material, you will see the security training materials provided by Secure Code Warrior:

For more information about Secure Code Warrior training materials, please refer to our Get Training on Typical Vulnerabilities documentation.
When a repository is scanned using Monorepo Mapping (which can trigger multiple jobs), clicking the build status indicator ( ) will redirect you to the Scan Summary page in the Mend Developer Platform, where all projects defined in the Monorepo Mapping JSON file are displayed:
) will redirect you to the Scan Summary page in the Mend Developer Platform, where all projects defined in the Monorepo Mapping JSON file are displayed:
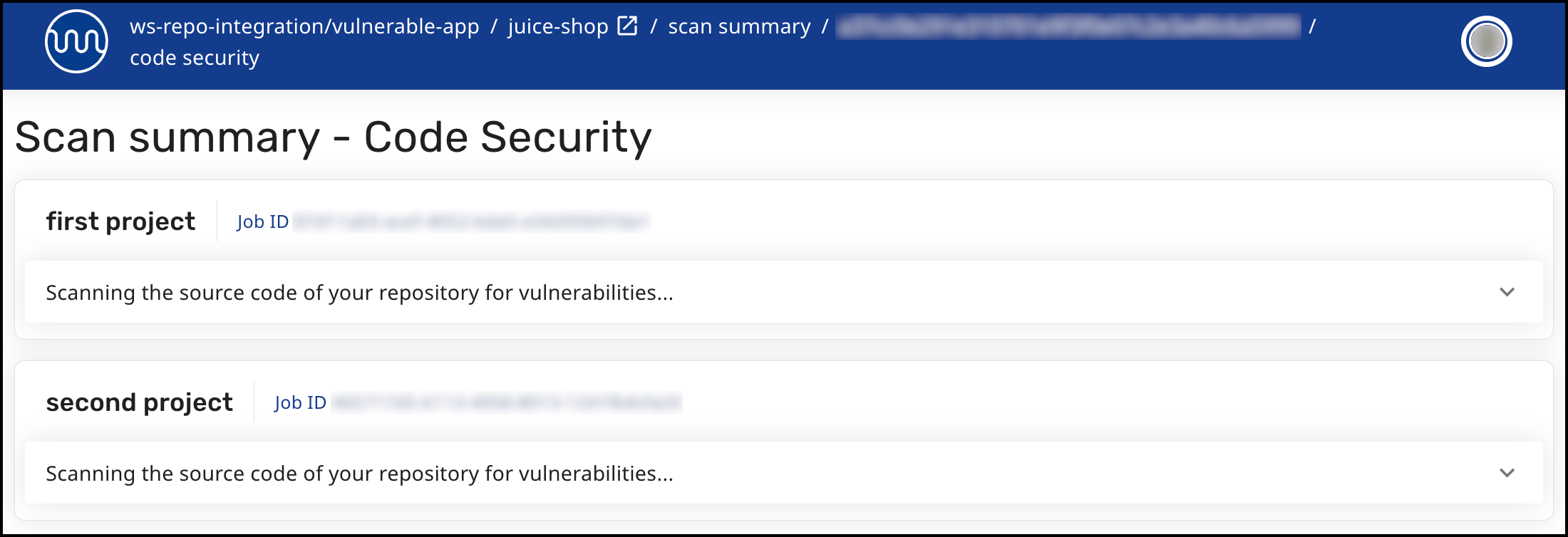
Types of Indicators
The following status indicators are available as feedback on a head commit:
Queued: Scan has not begun and is scheduled to begin.
In progress: Scan is in progress.
Completed: Scan completed with one of the following conclusions:
Success: When the parameter 'vulnerable.check.run.conclusion.level' is set to 'success', the status of the head commit is always success A 'Success' status is displayed for the commit even when it fails.
Failure: Default for all completed scans. When the parameter 'vulnerable.check.run.conclusion.level' is set to 'failure' (default), the status of a 'failed' head commit is 'failure', and a policy for approving merging pull requests that include failed head commits with another branch in the repository is enforced. Note that a 'failed' status can be caused due to security vulnerabilities or due to an error that occurred during the scan.
Neutral: Conclusion occurs when the push command was not valid.
Samples of Check Status Indicators
In Progress
The following is a sample of a 'Running' status, which indicates that the security check is currently scanning the head commit.

Completed with Success Conclusion
When no vulnerabilities are found and no errors occurred during the scan, Mend will display the following commit status, and a security report indicating that no vulnerabilities were detected.

Completed with Failure Conclusion
All head commits that fail the scan due to the security check detecting vulnerabilities or due to an error that occurred during the scan, will display a failed commit status.
The following screenshot displays a failure indicator for a head commit

Viewing Details in the Mend Developer Platform
Once an SAST scan job is complete, you can access the Mend Code Security Report and review the detected findings within the Mend Developer Platform, by clicking a specific scan in the Recent jobs view. The report content in shown in the Developer Platform UI due to technical limitations which prevent showing this information in the Azure Devops UI.
The following information is displayed for each finding:
Severity: Level of severity (
High, Medium, Low) of the introduced vulnerability.Vulnerability Type: The type of vulnerability that was introduced.
CWE: CWE ID that was introduced. This links to the CWE’s page on the official MITRE site.
File: File and code line(s) that are impacted by the vulnerability
Data Flows: Number of data flows detected that lead to the finding.
Remediation
Detected: Date and time the vulnerability was originally introduced (
YYYY-MM-DD 00:00).Violated Workflows: The name of the Automation Workflows that triggered the violation.
Workflow Priority: The priority level defined for the triggered Workflow.
Workflow SLA: Defines the required resolution time that was set for the triggered Automation Workflow.
Viewing Details in the Mend Platform
In the Mend Platform, Mend Projects will have the same name as the corresponding Azure DevOps repository, with a "AZ_" prefix. The name of the Mend Platform will be your Azure DevOps Project name preceded by "AZ_".
When a scan is completed for each branch defined in your baseBranches parameter, a Mend project is created for that branch with a “AZ_" prefix. Let’s look at an example:
Azure DevOps Repos hierarchy:
vulnerable-node repository
mainbranch [default branch]Mend Developer Platform settings for
"baseBranches": ["main", "dev"]
devbranch
We run a scan on both the main and dev branches. The Mend hierarchy appears as:
Mend Platform hierarchy:
Application: AZ_vulnerable-node
Project: AZ_vulnerable-node_main
Project: AZ_vulnerable-node_dev
Project Naming with Monorepo Mapping
When a monorepo mapping JSON file is configured, the Mend project name includes the project name defined in the mapping file.
Note: When scanning with Monorepo Mapping, newly created projects use an updated naming convention:
Previously, project names were in the format
AZ_repoName_branchName.Now, they include the project name from the mapping file, for example:
AZ_repoName_projectName(from the mapping file)_branchName
For example, if a mapping file defines a project first_mend_project, and a scan runs on the main branch, the project name will appear as: AZ_repoName_first_mend_project_main.
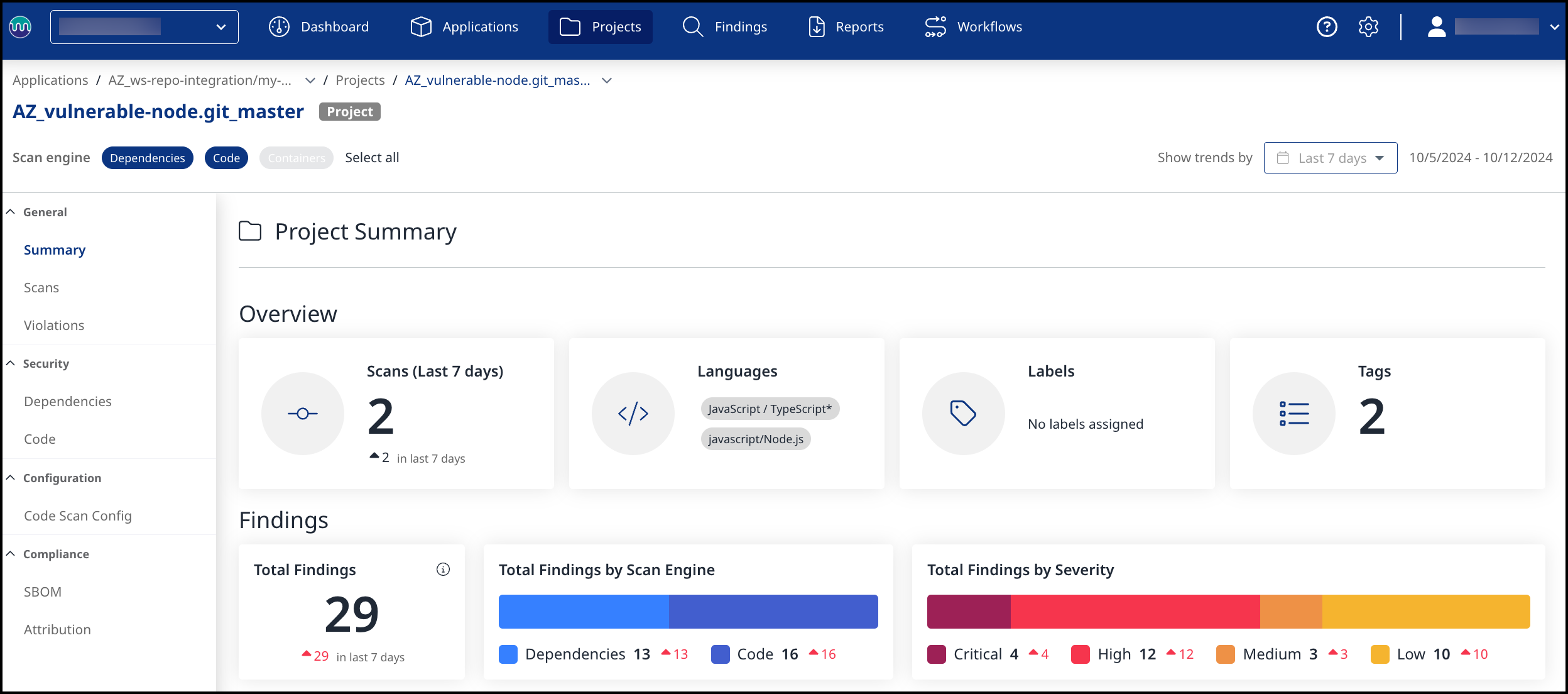
Within the Mend Application, You can filter the results by engine type:
(1) Dependencies -> Open-Source Security
(2) Code -> Code Security

