Get Training on Typical Vulnerabilities
Overview
When triaging your Code Security Findings, the Training section is available each finding to see context-based links to content for established training material provided by Secure Code Warrior. The links provide training resources directly for each finding within the Mend SAST scan. This will allow you to understand better and remediate vulnerabilities faster and increase awareness to prevent similar issues in the future.
Getting it Done
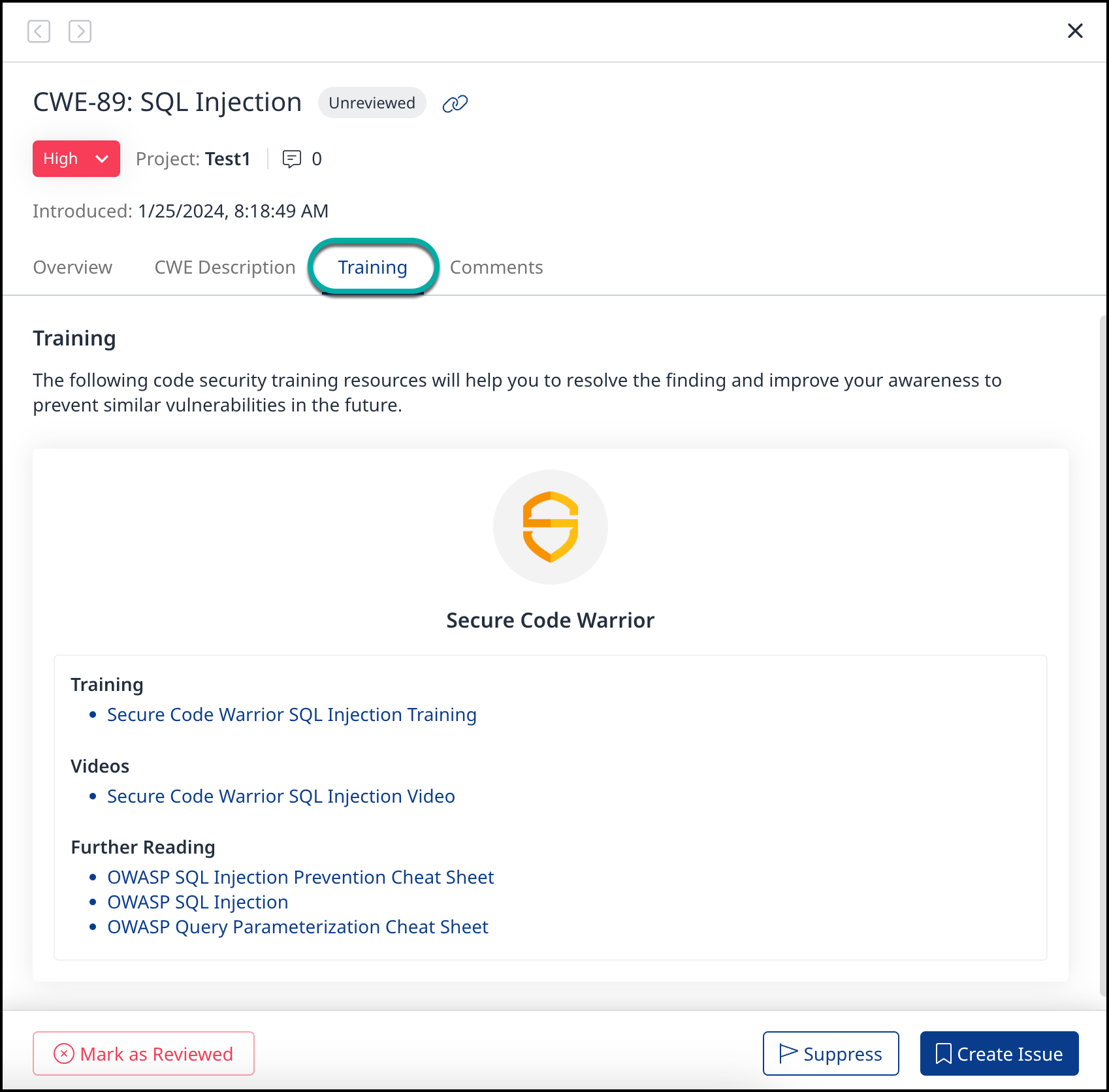
In your Code Findings within the Mend Application, click on the Training tab.
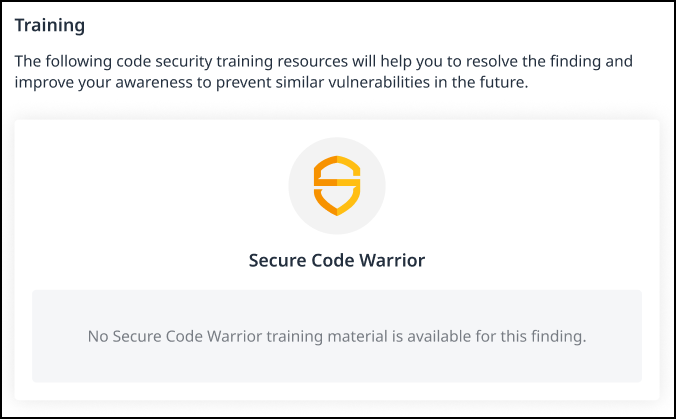
In case either a whole language or a certain finding is not supported, you’ll get a message saying that no training material is available.
If training material is available, click on Secure Code Warrior Training Material to see the training resources available for each finding.
Training: A Secure Code Warrior training session relevant to the reported finding.
Clicking on the training material links under the Training section will immediately take you to Secure Code Warrior’s login portal in your browser.
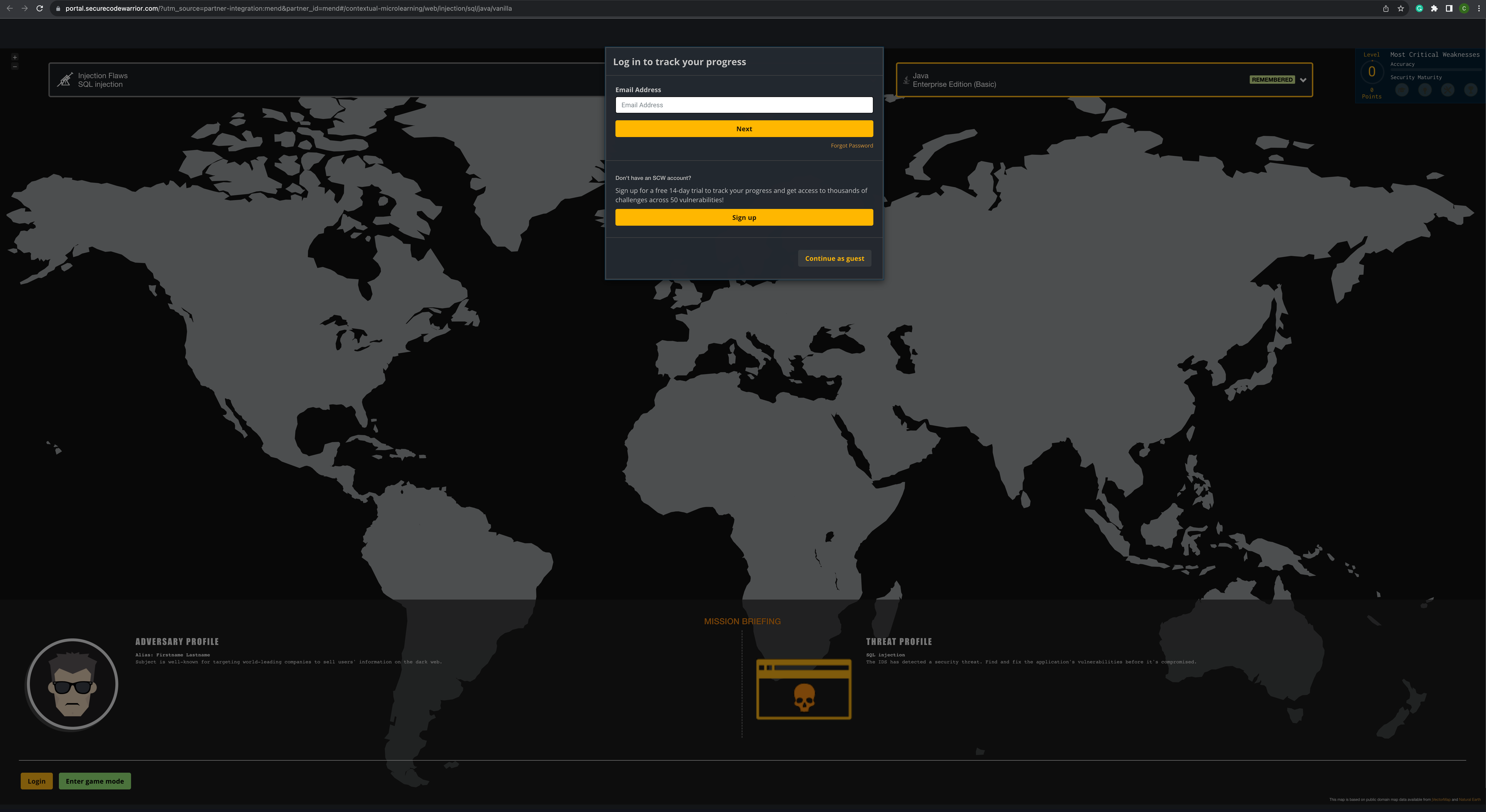
If you have a Secure Code Warrior account, log in so your progress through the learning challenges can be tracked.
You also have the ability to sign up for a 14-day free trial or continue as a guest.
After logging in or continuing as a guest, Secure Code Warrior will present you with a learning challenge catered to the detected finding by the Mend Code Scan. The Challenge will be pre-configured for the same vulnerability type and programming language.
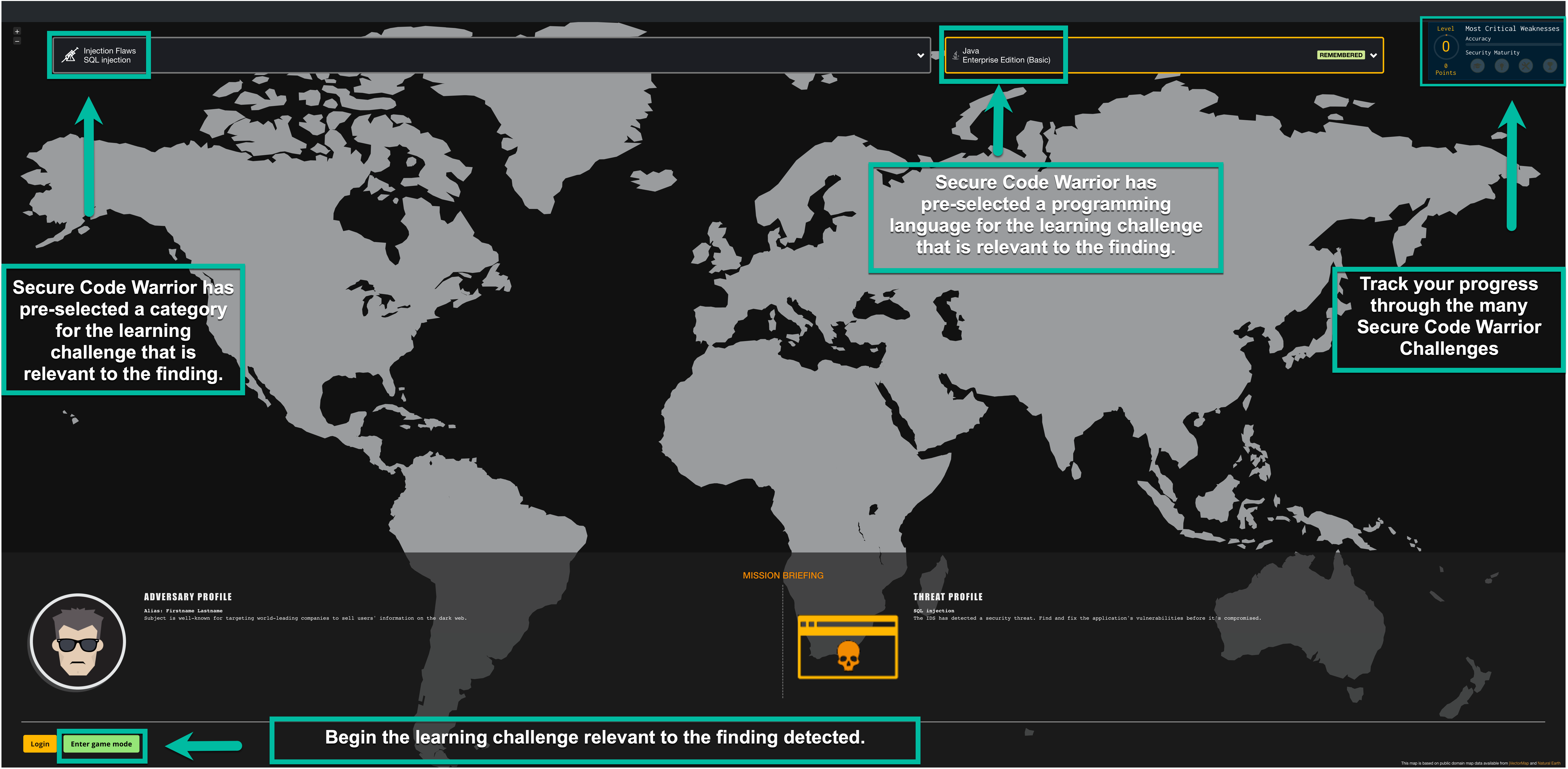
When you start the learning challenge, the challenge's goal and instructions will be located in the left pane, while the example file explorer and code for the challenge will be found in the right pane.
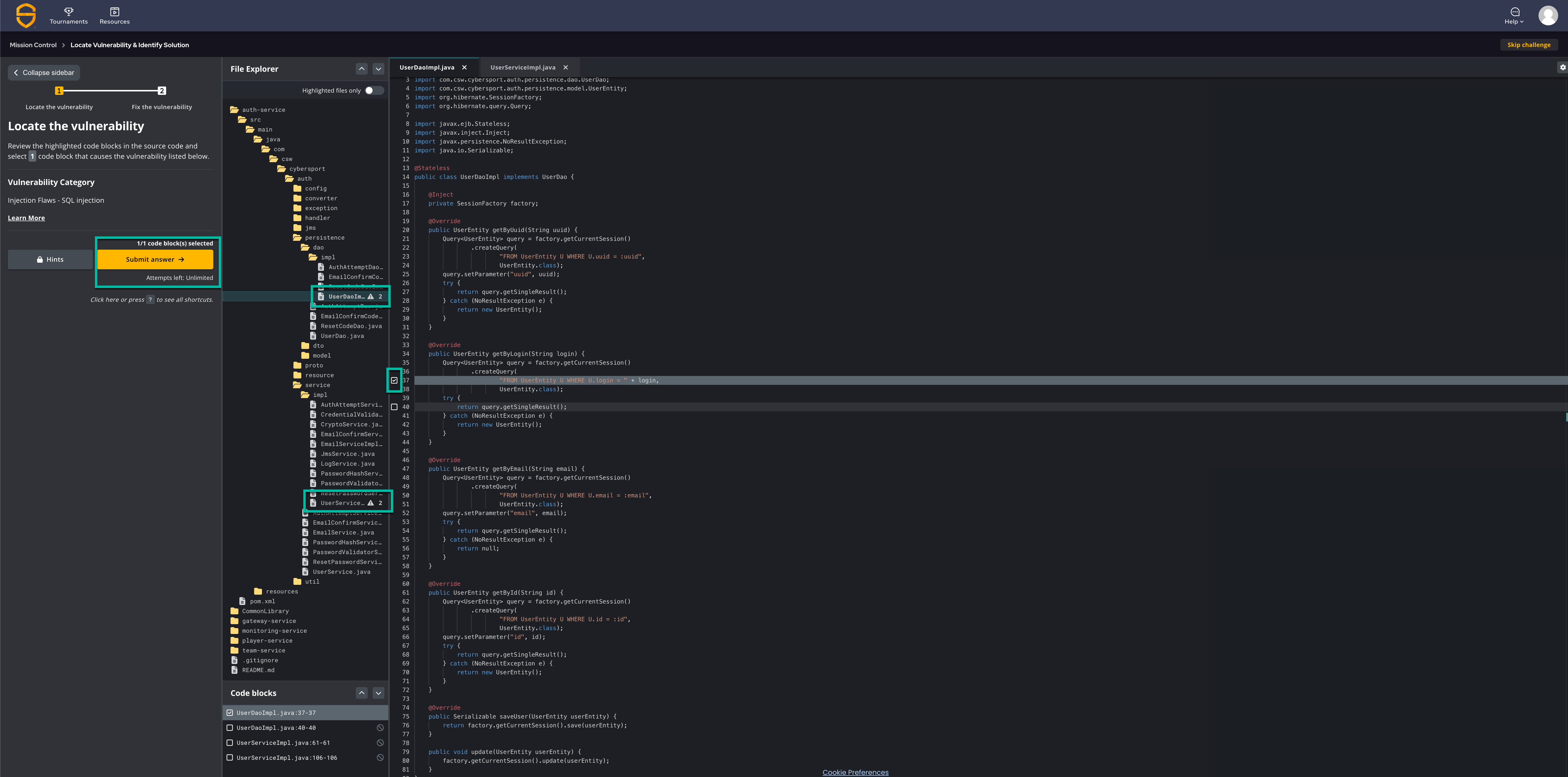
In the example challenge for SQL Injection, two files are marked with 2 highlighted lines of code in each file. The instructions are to find the one line of code that causes the vulnerability and then submit your answer.
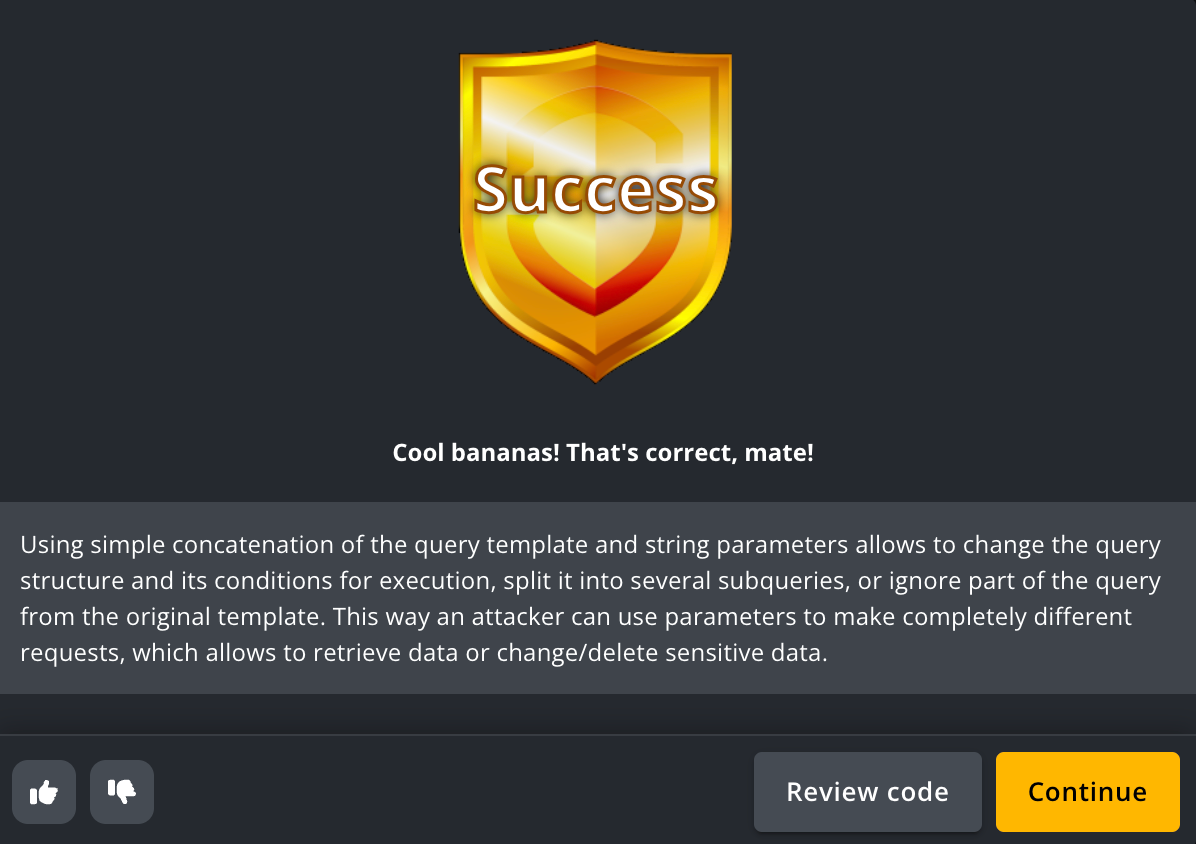
If you submit the correct line of code causing the vulnerability, you will be greeted with a golden Success shield with a brief explanation of why the correct line of code was selected and the ability to continue to another stage of the challenge.
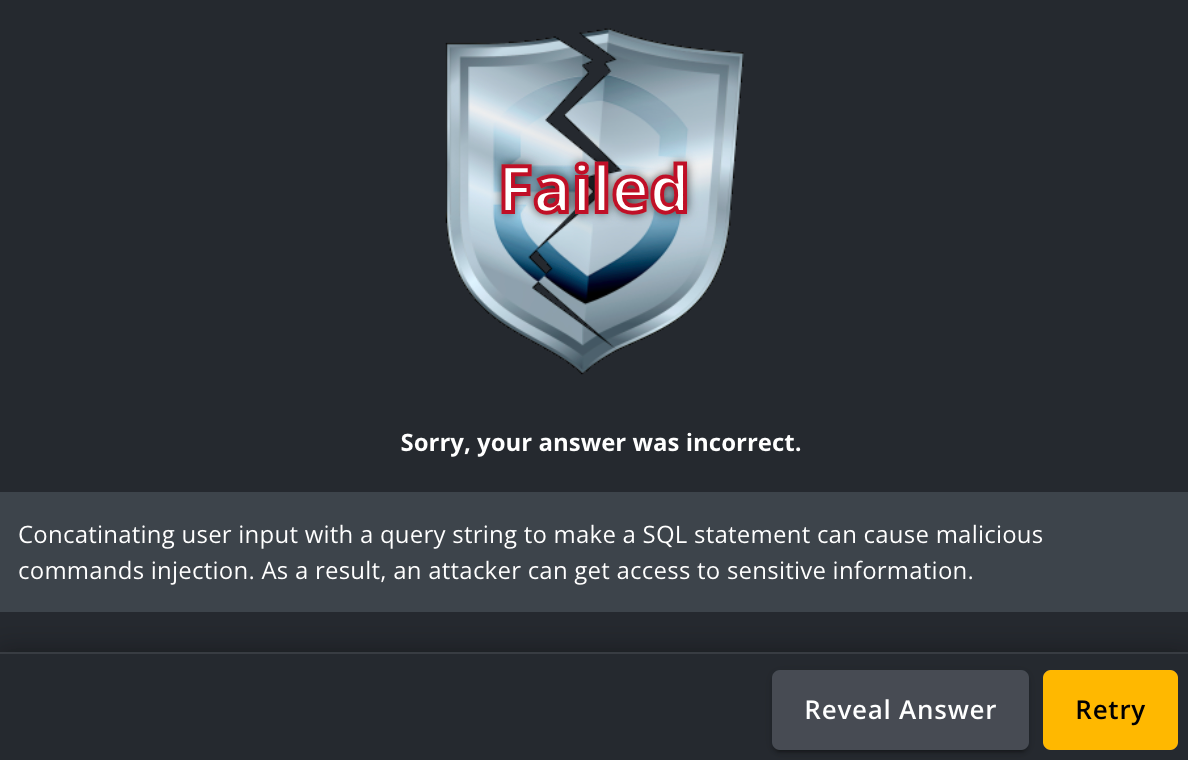
If you submit the incorrect line of code causing the vulnerability, you will be greeted with a broken Failed shield with a clue to help you select the correct line of code on your retries.
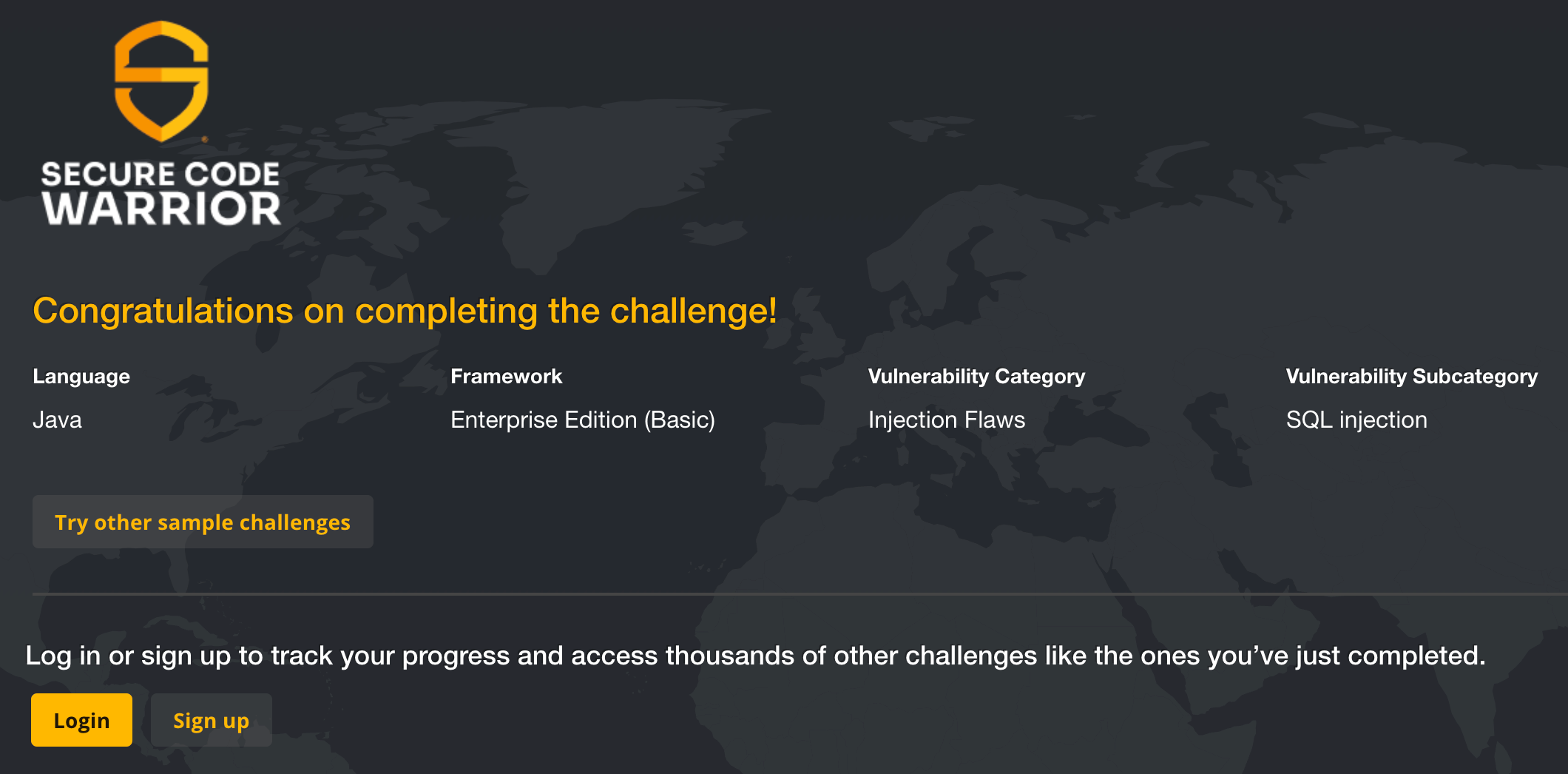
After completing the learning challenge, if you are logged in, the progress will be tracked on your account. If you complete the challenge as a guest, you will simply be congratulated for completing the challenge and given the opportunity to complete other challenges.
Each stage of the Secure Code Warrior challenges is formatted the same and gives similar feedback to help you learn secure coding best practices.
Videos: A Secure Code Warrior video relevant to the reported finding.
Clicking on the training material links under the Videos section will immediately open a video player in your browser and start playing a video related to the topic of the detected finding. The contents of the videos explain what the vulnerabilities are, how they are caused, and ways to prevent them.
Example video: Secure Code Warrior SQL Injection
Further Reading: Additional reading material relevant to the reported finding.
Clicking on the training material links under the Further Reading section will immediately open an article from http://owasp.org in your browser related to the topic of the finding. These articles can either explain the vulnerabilities and how they can be exploited or be cheat sheets containing examples of best practice code to resolve or avoid the vulnerabilities in the first place.
Example further reading: Secure Code Warrior SQL Injection
Learn more about SCW
Reference
Secure Code Warrior Language Coverage
Language | Coverage | Covered CWEs | Total CWEs |
|---|---|---|---|
ABAP | 100% | 6 | 6 |
ASP Classic/Visual Basic/VBScript | 0% | 0 | 18 |
Android Java | 64% | 9 | 14 |
Apex | 66% | 4 | 6 |
C/C++ (Beta) | 73% | 14 | 19 |
ColdFusion | 0% | 0 | 4 |
C# | 79% | 23 | 29 |
Cobol | 100% | 3 | 3 |
Go | 76% | 20 | 26 |
Groovy | 0% | 0 | 30 |
iOS Objective-C | 66% | 6 | 9 |
JavaScript / Node.js | 83% | 15 | 18 |
Java | 75% | 31 | 41 |
Kotlin | 76% | 23 | 30 |
Kotlin Mobile | 71% | 25 | 35 |
PHP | 77% | 21 | 27 |
PLSQL | 100% | 4 | 4 |
Python | 73% | 14 | 19 |
R | 0% | 0 | 8 |
Ruby | 83% | 15 | 18 |
Swift | 66% | 6 | 9 |
TypeScript | 80% | 12 | 15 |
VB.Net | 79% | 23 | 29 |
Xamarin (C#) | 0% | 0 | 27 |
