Configure SCA Reachability for GitHub Enterprise
Note:
- Reachability in the GitHub Enterprise integration can be enabled on demand.
- Reachability for Python is available starting from version 24.10.1.1 of the integration.
- Reachability for .NET is available starting from version 24.12.1 of the integration.
Overview
As part of our commitment to reducing developers' security burden, we are excited to introduce Mend's innovative differentiation - Reachability Analysis. With Mend Reachability, developers can easily identify and address reachable vulnerabilities in their GitHub repositories, streamlining the security remediation process.
Mend Reachability determines the level of security risk by examining and analyzing the paths and dependencies within the codebase to determine which vulnerabilities are actually reachable. By focusing on these vulnerabilities, developers can prioritize their efforts and efficiently address the most critical security issues.
Use case for Mend Reachability
One of the valuable use cases of reachability analysis is its integration into the repository scan process. By including a dedicated "reachability scan" step, Mend enhances the depth of the scan to provide vital insights into the actual exploitability of listed vulnerabilities.
While the scan may take slightly longer, the results become enriched with reachability information. This enrichment is showcased in the scan report through clear visual indications in the user interface that will help you identify whether each listed vulnerability is reachable or not and assess each vulnerability's effectiveness.
Getting it done
Prerequisites before getting started with Mend Reachability
Ensure you have performed the steps described in Mend for GitHub Enterprise installation procedures
Mend Reachability scans are currently supported for Java and JavaScript GitHub repositories
Configure Reachability
The .whitesource file configures Mend for GitHub Enterprise SCA scans. To set up your configuration file for SCA scans, see the Parameters section provided in this documentation. Below is an example of fine-tuning the Mend Reachability scan within a repository’s .whitesource file:
{
"scanSettings": {
"configMode": "AUTO",
"enableReachability": true
},
"checkRunSettings": {
"strictMode": "warning"
}To learn more about the SCA-supported languages, configuration, and parameters, visit our Mend for GitHub Enterprise documentation.
Run the Mend Reachability scan
After configuring the .whitesource file mentioned in the configuration section above, the reachability analysis feature will automatically be enabled for your GitHub repository once you merge the onboarding PR into your default branch.
With Mend SCA check runs, your code commits trigger analysis for the following scenarios:
Changes to packages manifest files
Addition or deletion of supported source files
When you enable reachability analysis, every Mend SCA check run will include this feature and be triggered based on the following scenarios:
Changes to packages manifest files (similar to regular SCA check runs)
Addition or deletion of supported source files (similar to regular SCA check runs)
Changes to existing supported source files will be analyzed after a specific elapsed time interval (a new feature introduced for reachability analysis)
For more details, please refer to how to initiate and run a scan using Mend for GitHub Enterprise.
Review the results of Mend Reachability scan
Once your Mend Reachability scan is completed, multiple resources are provided to help you review, analyze, and triage your results.
GitHub Check
Once the Mend for GitHub Enterprise SCA scan is completed, the Mend checks are updated with the results. The Mend Security Check includes a Scan token, which you can provide to Mend Support for troubleshooting.
Mend Security Check
The Security Report within Mend Security Check populates within an overview of vulnerability findings within the commit:
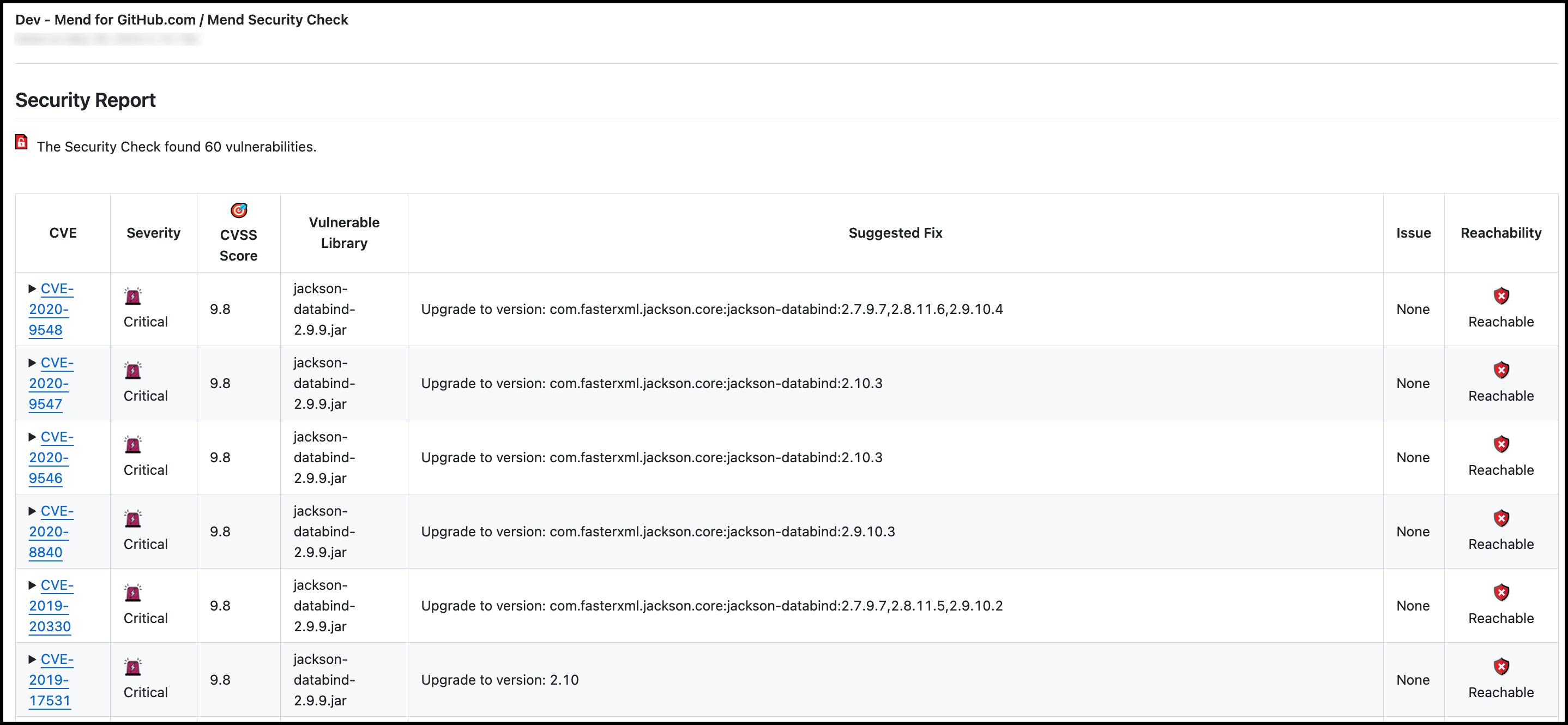
CVE: CVE ID of the vulnerability. This links to CVE’s page on Mend’s official database site.
Severity: Level of severity of the vulnerability (
Critical,High,Medium,Low)CVSS Score: CVSS Score (CVSS 3).
Vulnerable Library: Name of the open-source component impacted by the vulnerability.
Suggested Fix: Fix suggestion to resolve the vulnerability.
Issue: URL to the related GitHub Issue that was created for the policy violation.
Reachability: A Reachable / Unreachable indicator will be specified, depending on the reachability status of each vulnerability.
You can also click the dropdown arrow next to each CVE for more details:
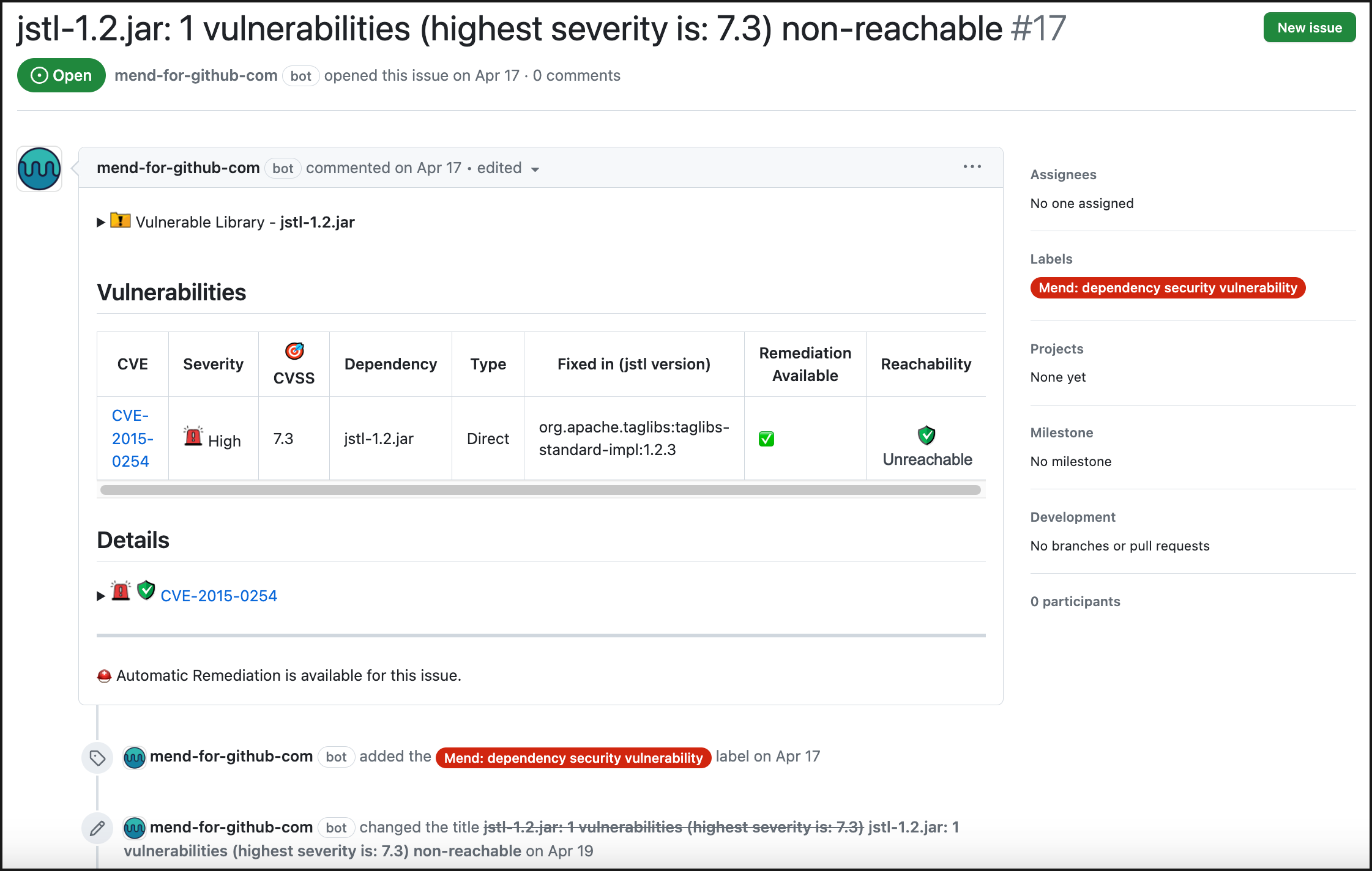
GitHub Issue
Once the Mend Reachability for GitHub Enterprise scan is completed, by default, the Mend SCA Check creates a GitHub issue for the findings of each SCA component, if any were discovered.
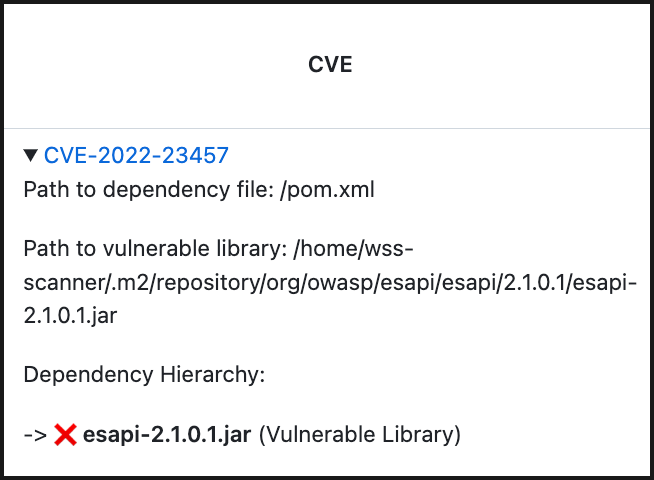
Vulnerable Library: Name of the vulnerable dependency file. Click on the dropdown arrow for more information. This information includes the path to the dependency file and the path of the library. If the path is of a transitive dependency, then only the path information of the root library is displayed. This section also contains a commit link, which includes the path to the commit link where the vulnerability was found.

Vulnerabilities table:
CVE: CVE ID of the vulnerability. This links to CVE’s page on Mend’s official database site.
Severity: Level of severity of the vulnerability (
Critical,High,Medium,Low)CVSS: CVSS Score (CVSS 3).
Dependency: Name of the dependency file.
Type: The type of dependency (
DirectorTransitive).Fixed in: Version of the dependency that fixes the vulnerability.
Remediation Available: If remediation is available (via Mend Remediate), there will be a green checkmark icon. If remediation is not available, there will be a red “X” icon.
Reachability: Once the Reachability scan is enabled, if the vulnerability is reachable, this will be indicated by a “Reachable” status.
Details: List of CVEs found by the SCA scan on the open-source component. Click on each CVE’s dropdown arrow for a deep-dive into the CVE vulnerability and how it impacts the open-source component:

Caching
The caching mechanism aims to improve the performance of Reachability over time, resulting in shorter Reachability scan times.
For each library (e.g. jar file), Mend generates a corresponding dot file graph, which represents its internal file/class level dependencies. The first time a library is encountered, Mend calculates its graph on the fly by language specific file/class graph builders, and then uploads it to the S3 or S3 compatible global cache for re-use in subsequent scans.
Note that the data stay private & secure as they are hosted on your company’s own cache.
To enable it, configure the specified environment variables or scm-scanner properties file parameters:
REACHABILITY_AWS_S3_ENDPOINT (optional, default=https://s3.amazonaws.com)
REACHABILITY_AWS_S3_ACCESS_KEY (required, unless using IAM role-based credentials)
REACHABILITY_AWS_S3_SECRET_KEY (required, unless using IAM role-based credentials)
REACHABILITY_AWS_S3_REGION (optional, default=us-east-1)
REACHABILITY_AWS_S3_BUCKET (optional, default=reachability)
REACHABILITY_AWS_S3_KEY_PREFIX (optional, default=dot-file-cache)Reference
Parameters
Note: For the full set of Mend for GitHub Enterprise configurations across our solutions, visit the main Mend for GitHub Enterprise documentation.
Mend Reachability Settings (scanSettings)
Repository-level Parameters
Parameter | Type | Description |
|---|---|---|
enableReachability | Boolean | Required to enable Mend Reachability scan |
reachabilityScanDelayHours | Float | Optional. Default Value:
Note: The |
Note that setting this parameter to a low number may cause a higher load on your servers, due to higher frequency of Mend Reachability scans. This may result in increased costs when using hosted cloud services.
Controller-level Parameters
Parameter | Type | Description |
|---|---|---|
MEND_REACHABILITY_ZERO_DAY_ENABLED | Boolean | Default: |
MEND_REACHABILITY_ZERO_DAY_MIN_SCORE | Float | Default: |
Check Run Settings (checkRunSettings)
Parameter | Type | Description |
|---|---|---|
strictMode | String | Optional. Default Value:
Note: For strictMode to work, the vulnerableCheckRunConclusionLevel and licenseCheckRunConclusionLevel parameters must be set to |
strictModeInfo | Boolean | Optional. Default Value:
|
Supported Languages
Language | Package Manager | Details |
|---|---|---|
.NET | NuGet | Configuration file(s): .nuspec, packages.config, .csproj, project.assets.json, packages.lock.json |
C, C++ | Conan | Configuration file(s): conanfile.txt, conanfile.py |
Java | Gradle | Configuration file(s): build.gradle, settings.gradle |
Java | Maven | Configuration file(s): pom.xml, settings.xml |
JavaScript | npm | Configuration file(s): package.json, package-lock.json |
JavaScript | Yarn | Configuration file(s): package.json, yarn.lock |
JavaScript | Lerna | Configuration file(s): |
JavaScript | pnpm | Configuration file(s): |
Python | Conda | Configuration file(s): |
Python | pip | Configuration file(s): requirements.txt |
Python | Pipenv | Configuration file(s): Pipfile & Pipfile.lock |
Python | Poetry | Configuration file(s): pyproject.toml, poetry.lock |
Supported versions of each language or package manager are listed here.
