The Code Findings Report
Overview
The Code Findings Report, accessible from your Mend Platform's main navigation, provides detailed information on your Application's or Project's findings.
Download the report to conduct further analysis, allowing you, as a Security Champion or AppSec Manager, to identify and share actionable insights with your developers.
Getting It Done
There are two ways to generate a Code Findings Report in the Mend Platform user interface:
Via the Reports page.

Via a chosen Application/Project.

Note: To investigate code findings, address false positives, and communicate results, please visit our Triage Your Code Security Findings document.
Generate the Code Findings Report via the Reports Page
Click the Reports button located in the top bar of the Mend Platform user interface:

Click the Create button (
 ) at the top-right edge of the Reports page.
) at the top-right edge of the Reports page.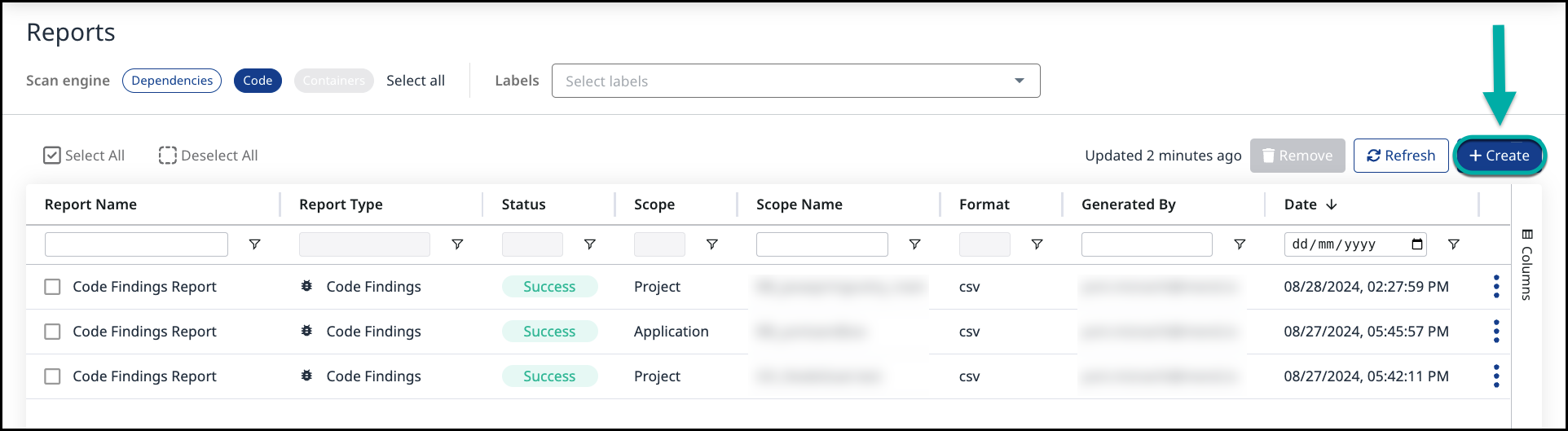
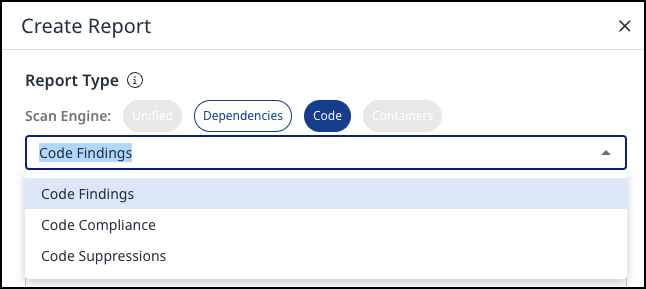
Select Code Findings from the drop-down list of the Create Report wizard:
Scope - Define the report’s scope by specifying the Application name. You can also narrow it down by selecting multiple Projects or a specific Project within that Application.

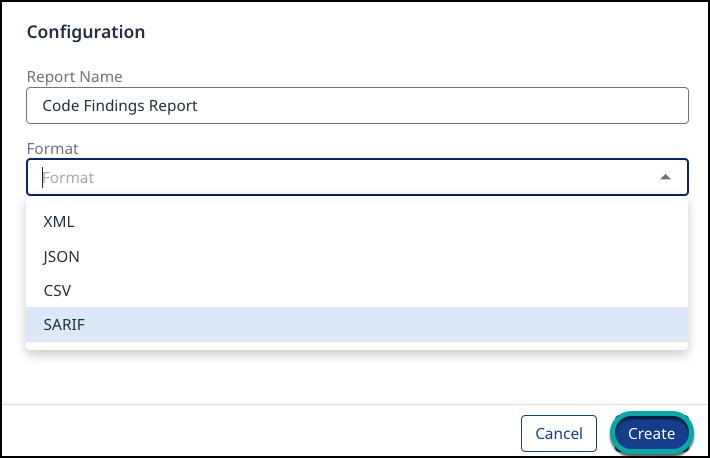
Configuration - specify the Report Name and Format (XML/JSON/CSV/SARIF):
Click Create.
Generate the Code Findings Report via a chosen Application/Project
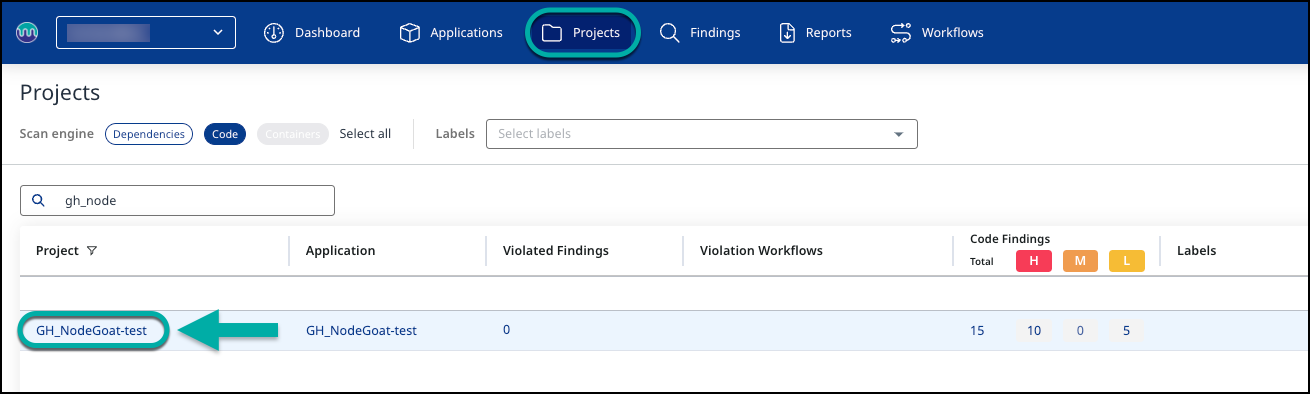
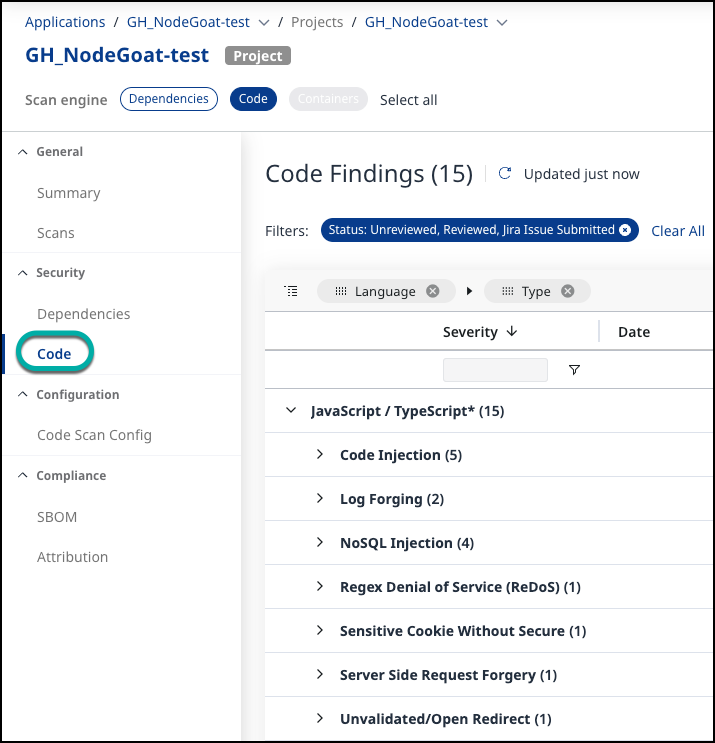
Navigate to the desired Application or Project and click on it.
Click Code on the left pane:
Click the Create Report button (
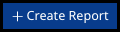 ) at the top-right edge of the Code Findings page.
) at the top-right edge of the Code Findings page.
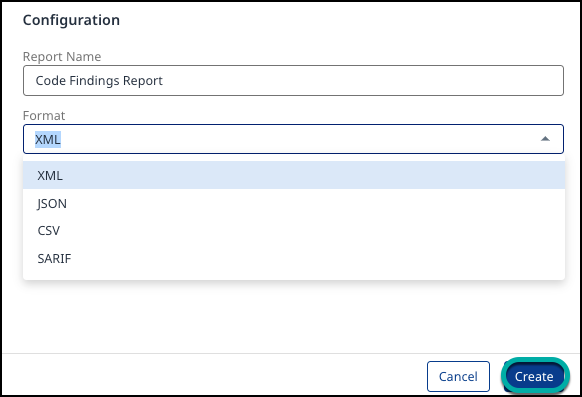
Select Code Findings from the drop-down list of the Create Report wizard:

Scope: The scope option is locked based on the Application or Project selection you made when accessing the Code Findings page.

Configuration - specify the Report Name and Format (XML/JSON/CSV/SARIF):
Click Create.
Understanding the Code Findings Report
The Code Findings Report shows detailed information on your Application's or Project's findings.
Example of the report in a table format:
| Vulnerability Type | Severity | CWE-ID | Input Source | Input Line | Input File | Sink | Sink Line | Sink File | Project | Detection Time |
|----------------------|----------|--------|----------------------------------|------------|-----------------------|-----------------------------|-----------|----------------------|---------|---------------------|
| Path/Directory Travel| High | CWE-22 | ARGV | 202 | utils/lru/test-lru.rb | File.open | 182 | utils/lru/test-lru.rb| redis | 13 Feb 24 16:21 UTC |
| Weak Hash Strength | Low | CWE-916| Weak cryptographic function -sha | 23 | utils/redis-sha1.rb | Weak cryptographic function | 23 | utils/redis-sha1.rb | redis | 13 Feb 24 16:21 UTC |
| Weak Hash Strength | Low | CWE-916| Weak cryptographic function -sha | 13 | utils/redis-sha1.rb | Weak cryptographic function | 13 | utils/redis-sha1.rb | redis | 13 Feb 24 16:21 UTC |Example breakdown:
Vulnerability Type: Identifies the specific type of security vulnerability detected in the code.
Severity: Indicates the level of risk associated with the finding.
CWE-ID: The Common Weakness Enumeration (CWE) identifier that classifies the type of weakness in the software.
Input Source: The code function where potentially unsafe input is introduced.
Input Line: The exact line number in the source file where the unsafe input is located.
Input File: The source file's name that contains the vulnerable input.
Sink: The location in the code where the potentially unsafe input is used could lead to an exploit.
Sink Line: The line number in the sink file where the input is processed or executed.
Sink File: The name of the file where the sink is located, which helps trace the vulnerability.
Project: The name of the project or repository where the finding was detected.
Detection Time: The date and time when the finding was identified.
