Review the Container Image Scan Findings within your Organization
Overview
As Security Champion or AppSec manager, you will be reviewing the top Applications and Projects with critical and high-severity container image security findings. You will want to drill down into them to review their summaries and findings, including their information and suggested remediations.
Getting it done
Review the top Application with highest severity Container Image Security Findings
Beginning on the Mend Application Security Dashboard, ensure only the Containers engine is enabled.
Click the Dependencies and/or Code scan engines to disable them if they aren’t already.
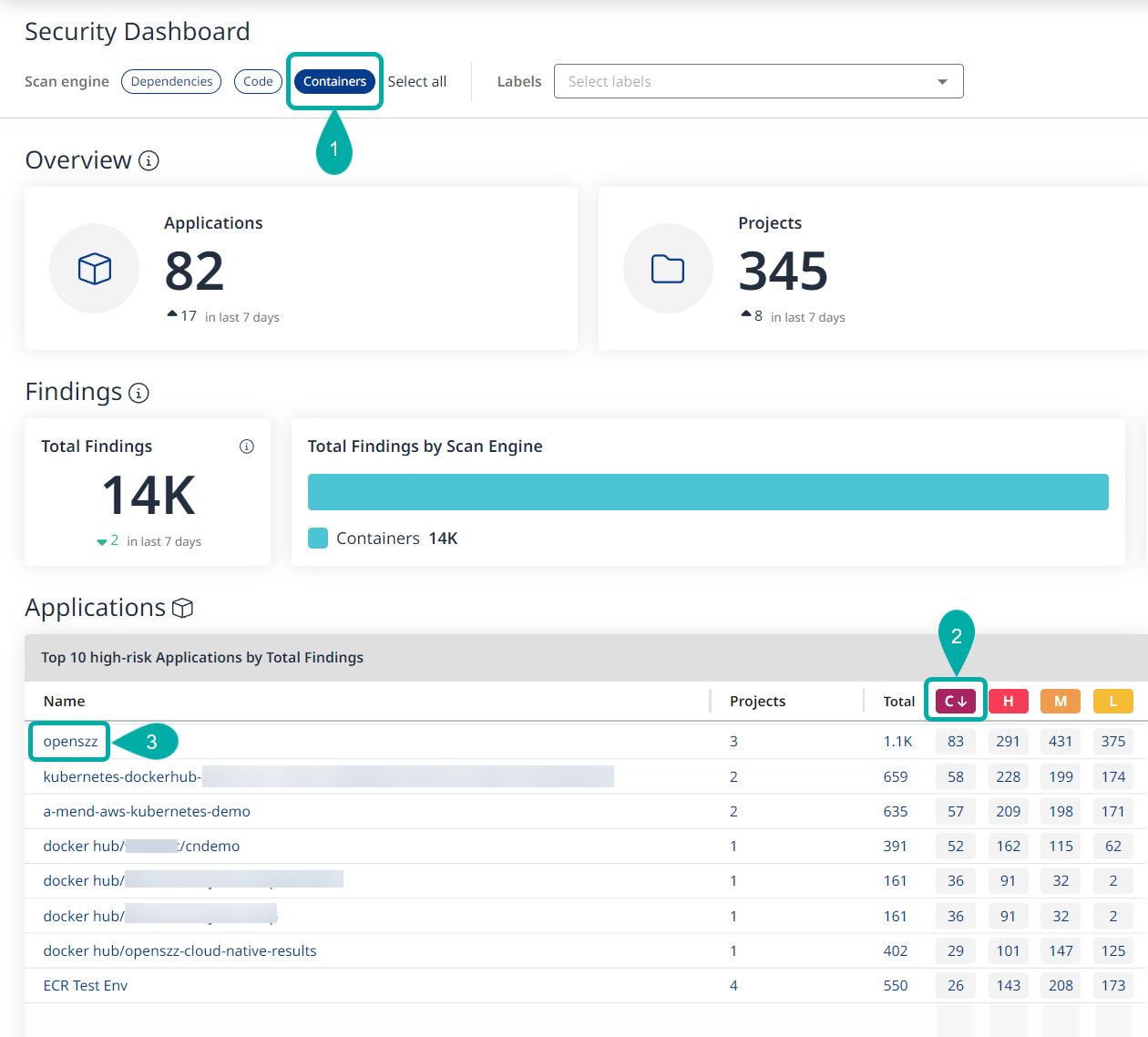
By default, the Applications widget showing the Top 10 high-risk Applications by Total Findings is ranked by the total number of findings.
Click the “C” in the box on the Applications widget to rank by most critical-severity findings.
If multiple applications are tied for the selected ranking order, they will be listed alphabetically.
Click the Application that has been sorted to the top with the most critical-risk findings. You will be redirected to that application's summary page.
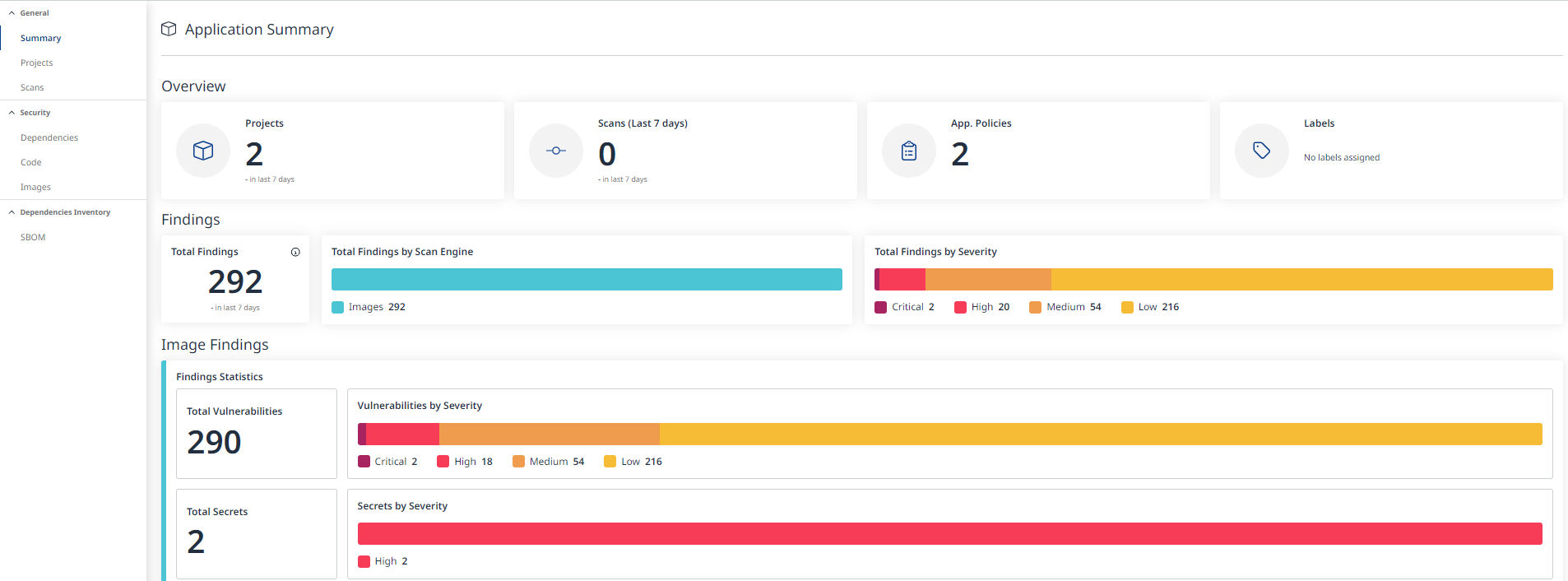
The Application Summary screen contains some vulnerability-related information about your application, including the overall number of vulnerabilities distributed by severity as well as secrets:
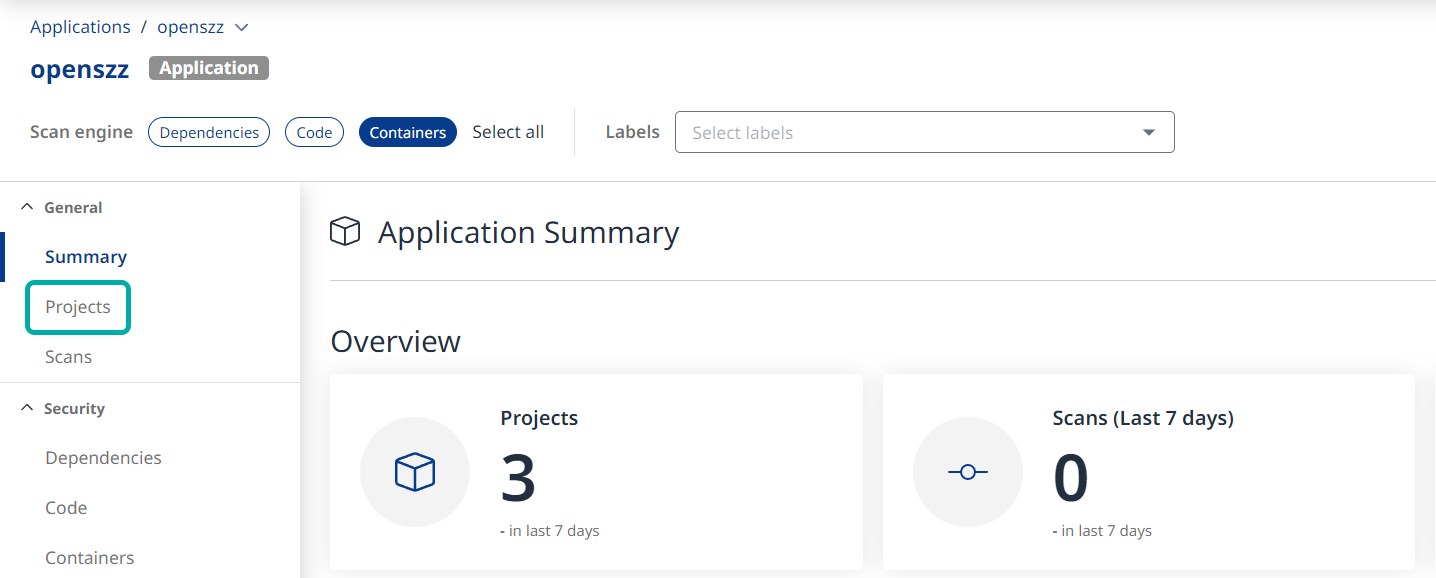
Click Projects in the left pane or click the Projects widget in the Overview section to view the Projects associated with the Application.
Review the top Project within the Application with highest severity Security Findings
Click the “C” in the red box on the Projects table to rank by most critical-severity findings.
Click the Project that has been sorted to the top with the most high-risk findings. You will be redirected to that project's summary page.
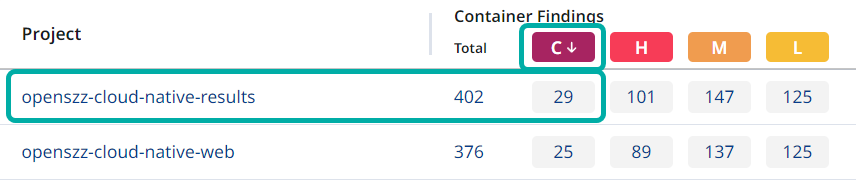
Click Containers in the left pane to view the latest container image findings associated with the Project (1). By default, the findings will be sorted by Severity (2), but we encourage you to add filters (3), to sort the findings in a manner that suits your needs.
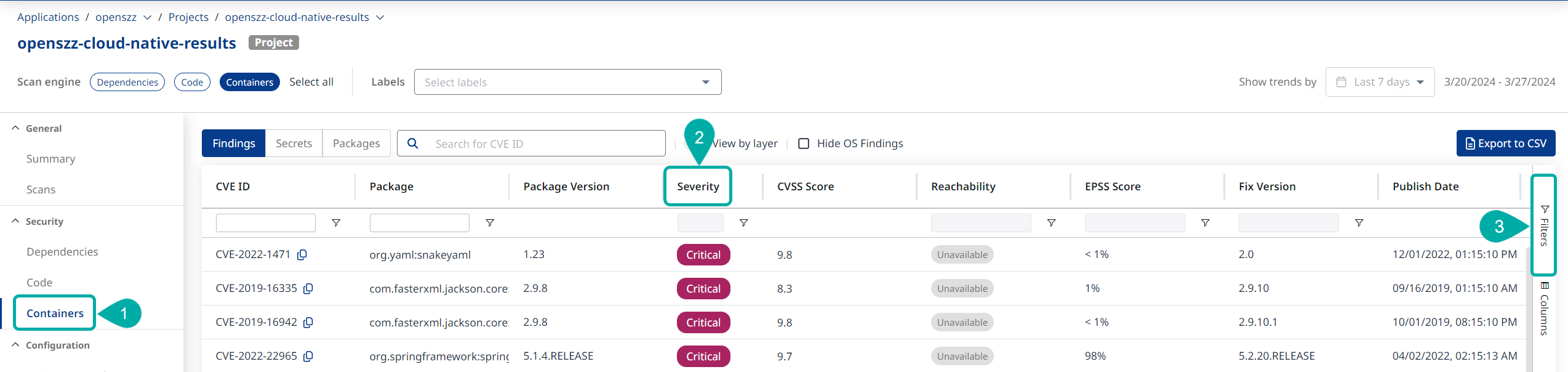
Filtering & Sorting options
While hovering with the mouse cursor over a column name, an options icon (3 lines) will appear:
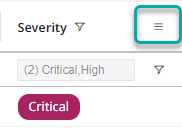
Clicking on it will reveal a menu which will enable you to change the settings of that particular column.
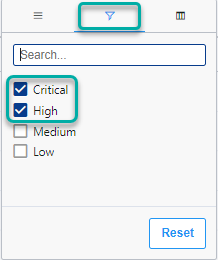
Severity
On the Severity column menu, you can select the severity levels you wish to include in the findings table:
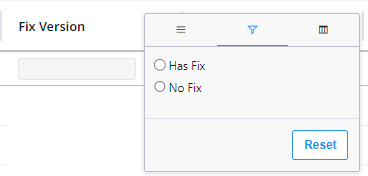
Fix Availability
Click the Fix Version column's options icon to filter by ‘Has Fix’ or ‘No Fix’:
EPSS Score
Click the EPSS Score column's options icon to filter by Exploitability Probability in the next 30 days*:
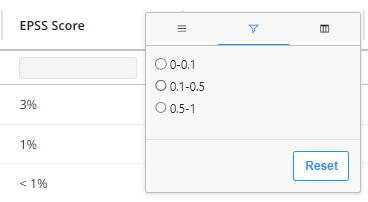
* The probability is displayed in decimal fractions in the filter while in the findings table it is displayed in percentages.
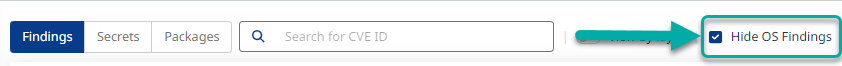
Hide OS Findings
Checking this option will exclude operating-system findings from the findings table. This option is useful if you don’t update base image packages:
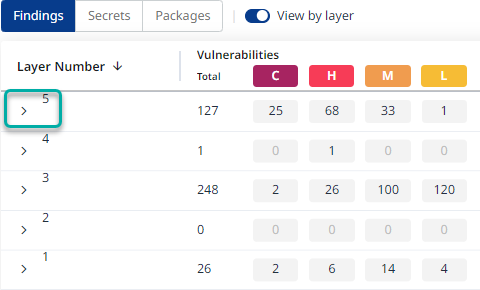
View by layer
Typically when it comes to container images, there are multiple layers that might contain vulnerabilities.
For more accurate navigation within your Image scan results, you can filter and sort the results by layers, by toggling the View by layer option:
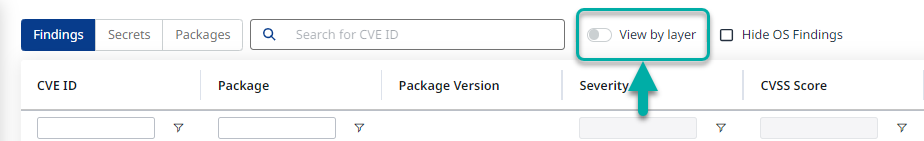
Once toggled, the findings will be rearranged by layer numbers, allowing you to expand each layer, to reveal its vulnerabilities:
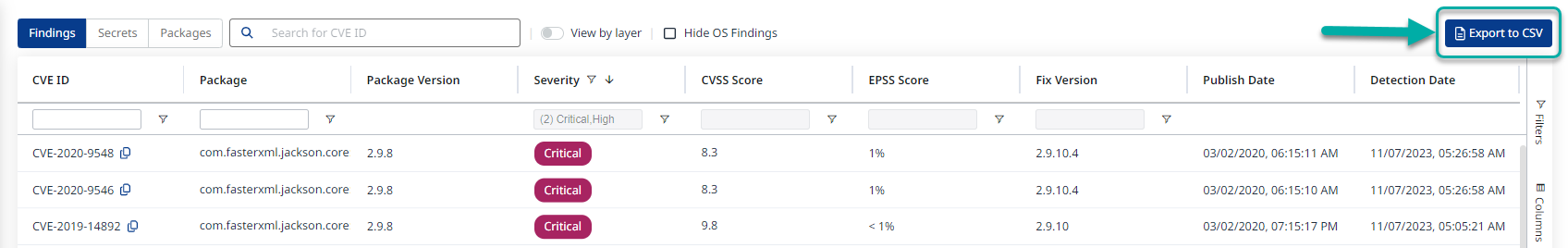
Exporting the data
After you’ve filtered and sorted the findings, you can export them to CSV by clicking the Export to CSV button at the right edge of the screen:
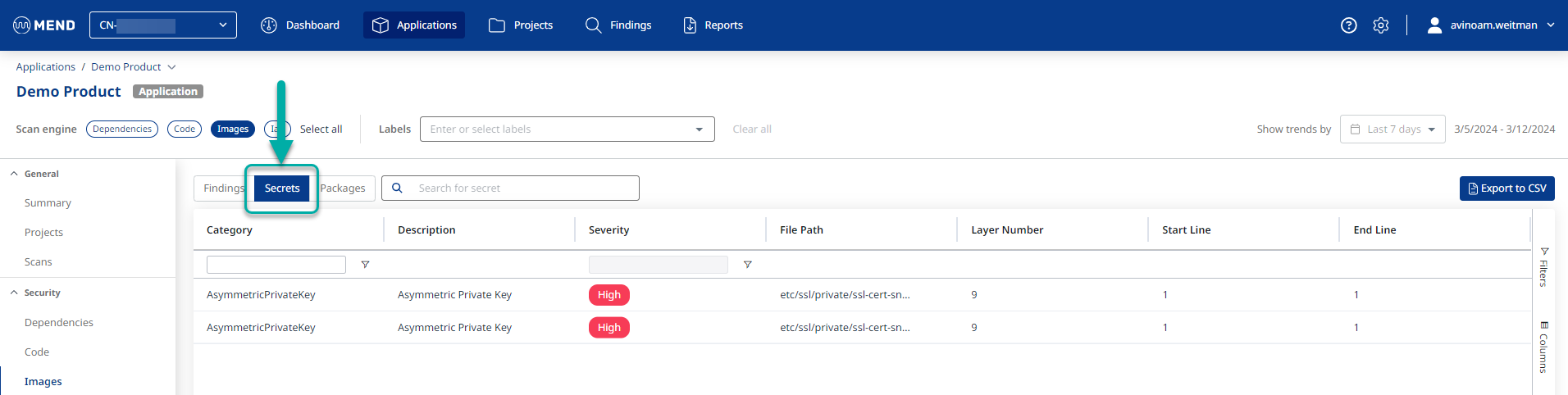
Secrets
Secrets are any kind of sensitive or private data that gives authorized users permission to access your IT infrastructure. These include keys and credentials such as SSH keys and certificates, TLS keys, encryption keys, API keys, database credentials, and more.
Secrets should be kept strictly private as attackers can easily find and use them to access and control the assets they are meant to protect. Developers may leave hard-coded secrets in container images, especially during rapid development and deployment cycles, thereby putting your organization and infrastructure at risk.
Secrets detected during your Container Image scan will be displayed in a separate tab from the rest of the findings:
Packages
The Project scope will always show the latest image scan for the selected project.
Within the Project, click on the Packages tab to see a full package inventory of all detected packages in the image, their type, package version, compliance status, number of vulnerabilities by severity, and layer indication:
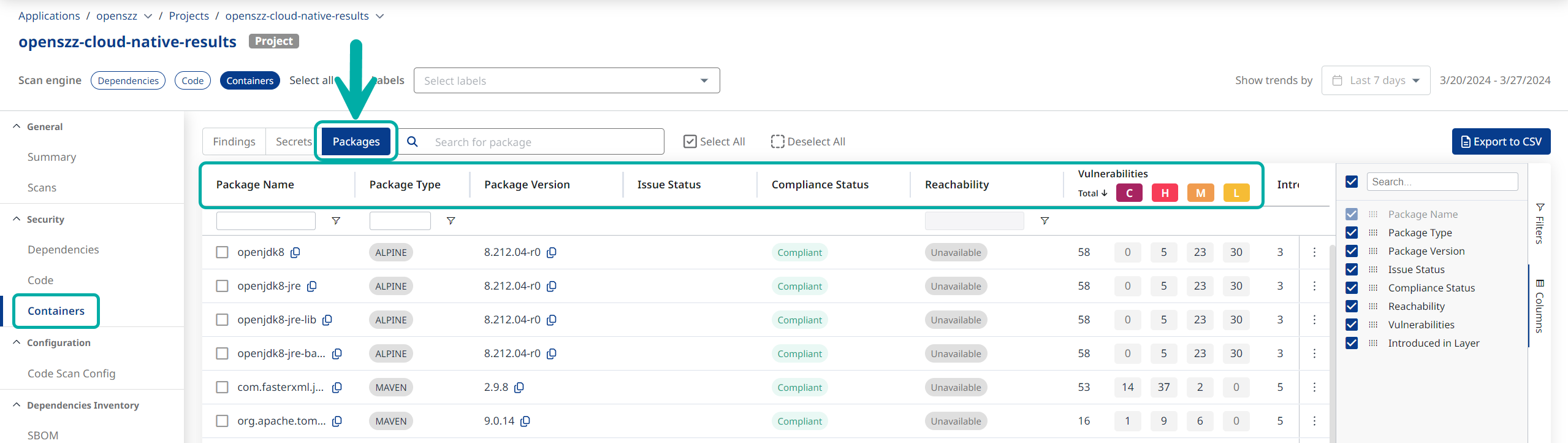
The Packages table groups the vulnerabilities by the packages they were detected in.
Any package in the table is displayed in a separate line, that can be clicked, to display the Package Details pane on the right and, among other things, review the package licenses:
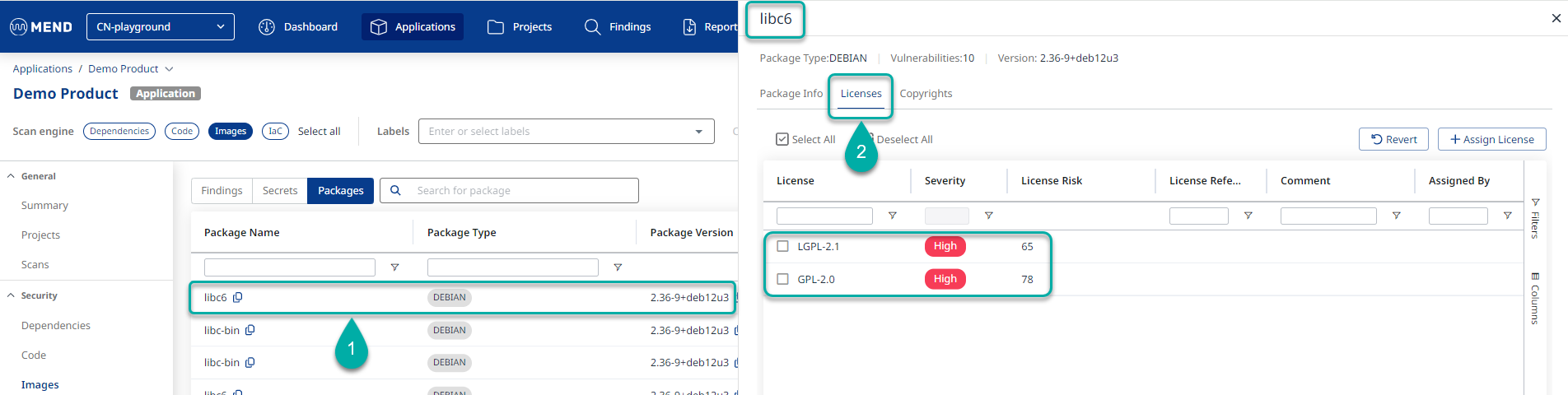
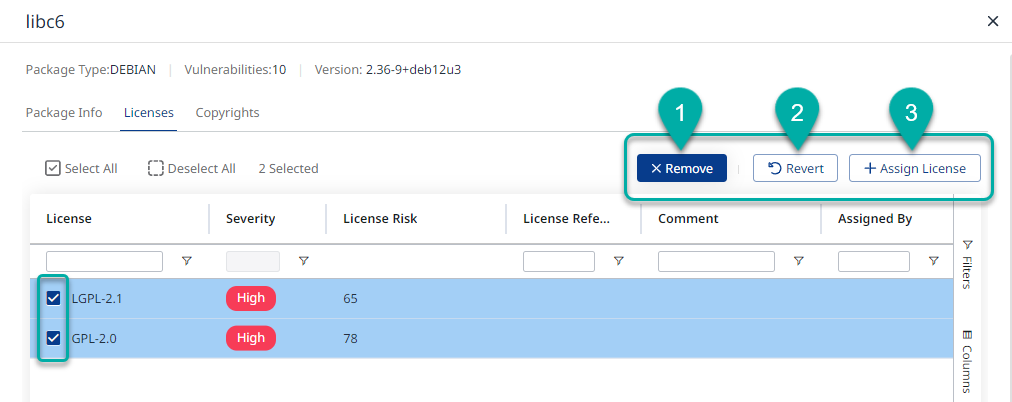
Package Licenses
The Licenses screen allows you to perform 3 main actions:
You can remove licenses (can be performed in bulk).
You can revert manually performed license changes (can be performed in bulk).
You can assign new licenses.