Remediation Strategies in Mend SCA
Overview
Mend.io offers two remediation strategies for your organization’s vulnerable dependencies:
Least Vulnerable Package (default) - recommends the latest minor version of a library that offers the most impactful risk reduction.
First Fix - recommends the earliest version of a package that resolves all the known vulnerabilities that have an available fix.
The Remediation Strategy is an org-level strategy which affects the dependency fix recommendations you will get throughout the organization (regardless of the context, i.e., Application/Project). Mend.io recommends using Least Vulnerable Package (LVP), however you are given the option to utilize the First Fix strategy instead. This article aims to help you understand the difference between the two as well as provide the step-by-step to implement them.
Least Vulnerable Package (LVP) automatically suggests the newest, least vulnerable library version as the optimal upgrade path for a vulnerable library.
Supported Languages and Coverage
Java
Supported: Maven Central packages.
Coverage includes Maven, Gradle.
JavaScript
Supported: npm packages.
Coverage includes npm, Yarn, pnpm, and Lerna.
Exception: Packages from CDN.js are not covered.
Not Supported: Bower package manager.
Python
Supported: PyPI packages.
Coverage includes pip, pipenv, and poetry.
Not Supported: Conda.
C#
Supported: NuGet Gallery packages.
Coverage includes: NuGet and Paket.
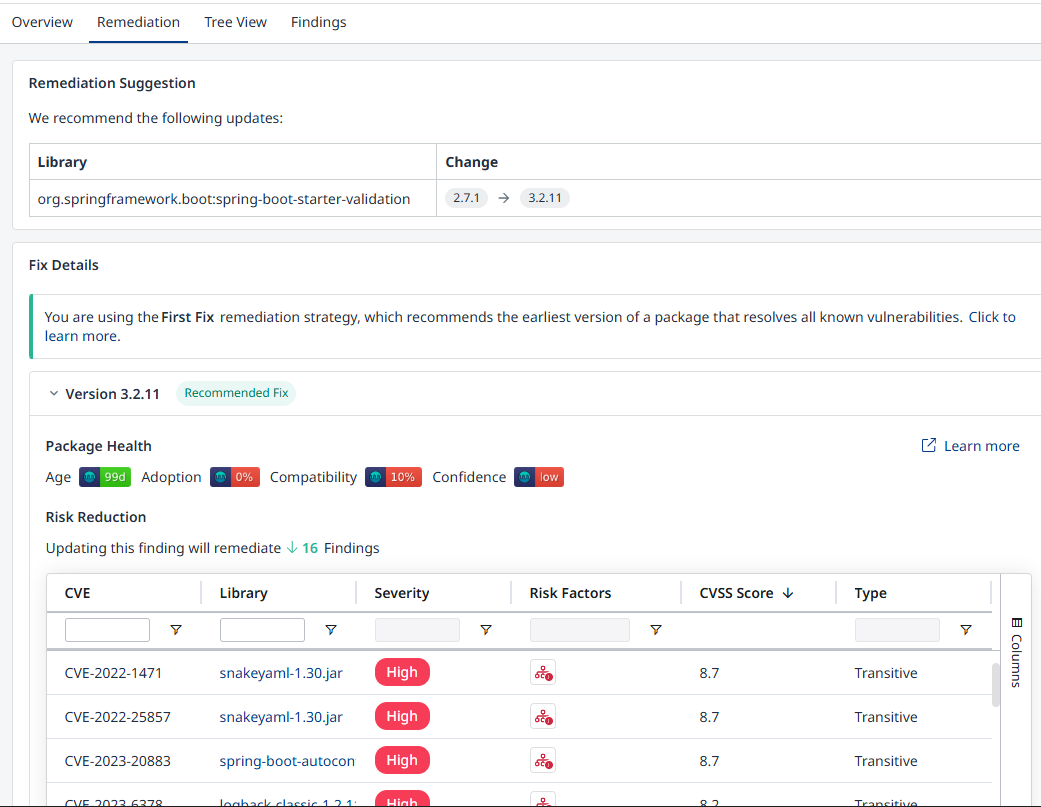
Remediation Suggestions
In the Direct Libraries table of your application or project’s Dependencies section on the Mend AppSec Platform, there are 3 potential remediation suggestion values denoted in the Remediation column:
Update version - The recommended upgrade path, based on the organization’s remediation strategy (Least Vulnerable Package / First Fix).
No minor upgrade required - This status is displayed when the organization’s remediation strategy has confirmed the existing minor library version is the least vulnerable one currently available.
This value is only applicable when using Least Vulnerable Package as the remediation strategy.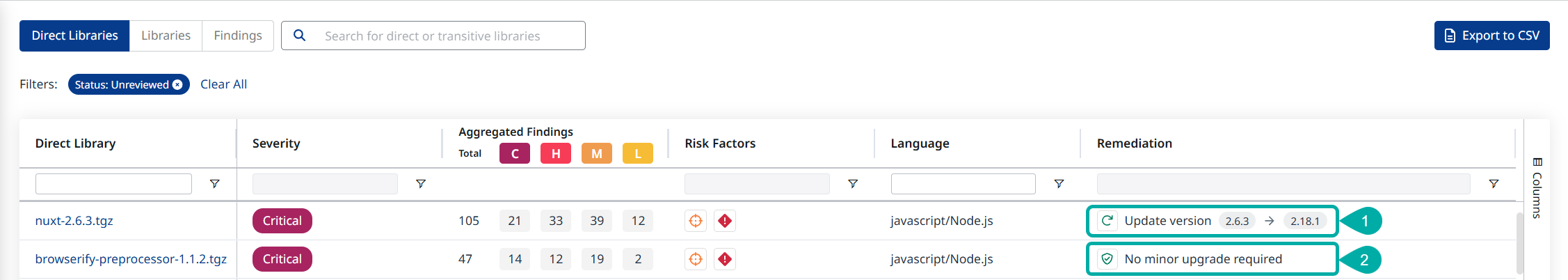
Unavailable - This status is displayed when no remediation can be suggested (e.g., when the library’s language, package manager or registry of origin is not supported).
Least Vulnerable Package (LVP)
How is it calculated?
Mend.io’s approach towards remediation with LVP is to establish a fix from a dependency tree perspective that will provide the most meaningful risk reduction. This risk score is calculated using the vulnerabilities' CVSS 3.X scores from each version’s dependency tree via the sum of the formulas for each severity below:
Icon | Severity & CVSS Score | Formula |
|---|---|---|
 | (C) Critical (9.0-10.0) | 10,000 x CVSS Score |
 | (H) High (7.0-8.9) | 1,000 x CVSS Score |
 | (M) Medium (4.0-6.9) | 10 x CVSS Score |
 | (L) Low (0.1-3.9) | 1 x CVSS Score |
Example
Let’s take a look at an example. For your application, you decide to add the npm library, express v3.0.0, and then run an SCA scan. Express v3.0.0 has a total of 17 transitive dependencies. Let’s review its dependency tree and vulnerabilities:
express-3.0.0.tgz (1 Medium)
→ commander-0.6.1.tgz
→ connect-2.6.0.tgz (5 Medium)
- bytes-0.1.0.tgz
- formidable-1.0.11.tgz
- pause-0.0.1.tgz
- qs-0.5.1.tgz (3 High, 1 Medium)
- send-0.0.4.tgz (1 High, 1 Medium)
→ cookie-0.0.4.tgz
→ crc-0.2.0.tgz
→ debug-4.3.4.tgz
- ms-2.1.2.tgz
→ fresh-0.1.0.tgz (1 High)
→ methods-0.0.1.tgz
→ mkdirp-0.3.3.tgz
→ range-parser-0.0.4.tgz
→ send-0.1.0.tgz (1 High, 1 Medium)
- mime-1.2.6.tgz (1 High)Adding up, express v3.0.0’s dependency tree has a total of 16 vulnerabilities, 7 High and 9 Medium. We then compare all other minor 3.x versions of express against v3.0.0 using our risk-scoring equation to determine the least vulnerable dependency tree. Let’s look at a visual of the scoring and decision-making below:
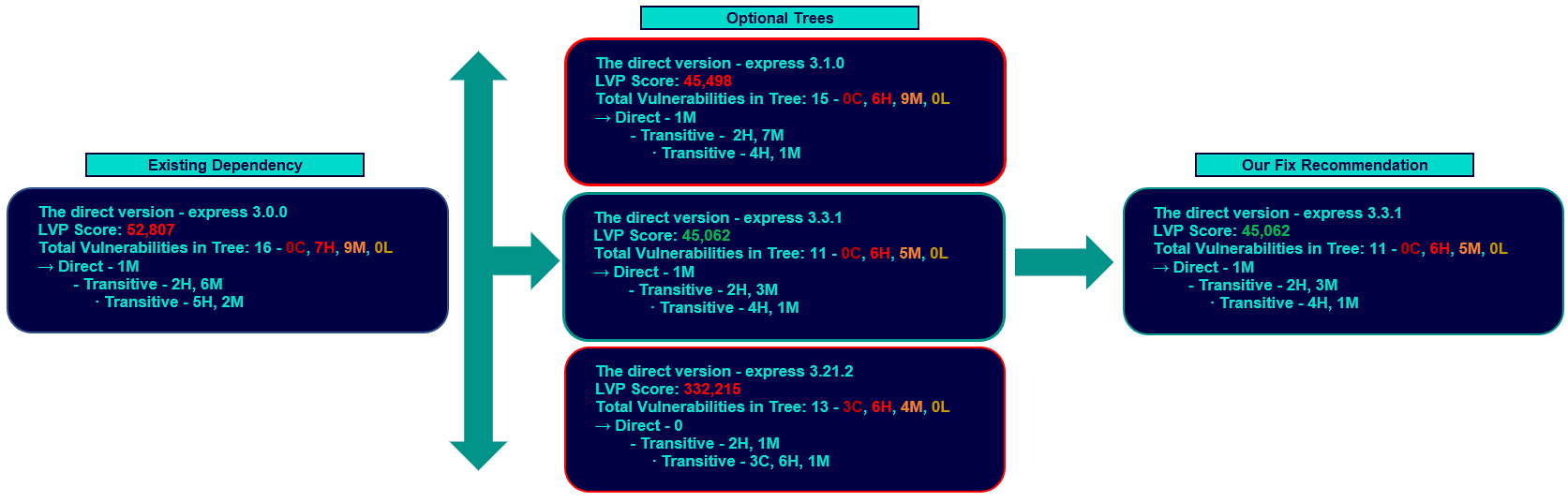
This results in express v3.3.1 being identified as the version embodying the greatest risk reduction and is therefore the suggested remediation, with a total of 11 vulnerabilities. LVP also displays the vulnerability counts of the current version in your application/project inventory (express v3.0.0) and the latest available 3.x minor version (express v3.21.2). In this example, updating to v3.21.2 was not recommended as it has a numerically higher LVP score, with more severe vulnerabilities than both the current version and v3.3.1.
Before You Begin
LVP is available in the Mend AppSec Platform UI as well as the GitHub repo integrations.
LVP currently supports npm, Maven and Python..
LVP evaluates major and minor versions and may provide up to four upgrade paths (labelling the recommended one as “Recommended Fix”):
Least vulnerable minor version
Latest minor version
Least vulnerable major version
Latest major version
LVP in the Mend AppSec Platform UI
The Least Vulnerable Package information is available in the Remediation tab of the library or vulnerability:
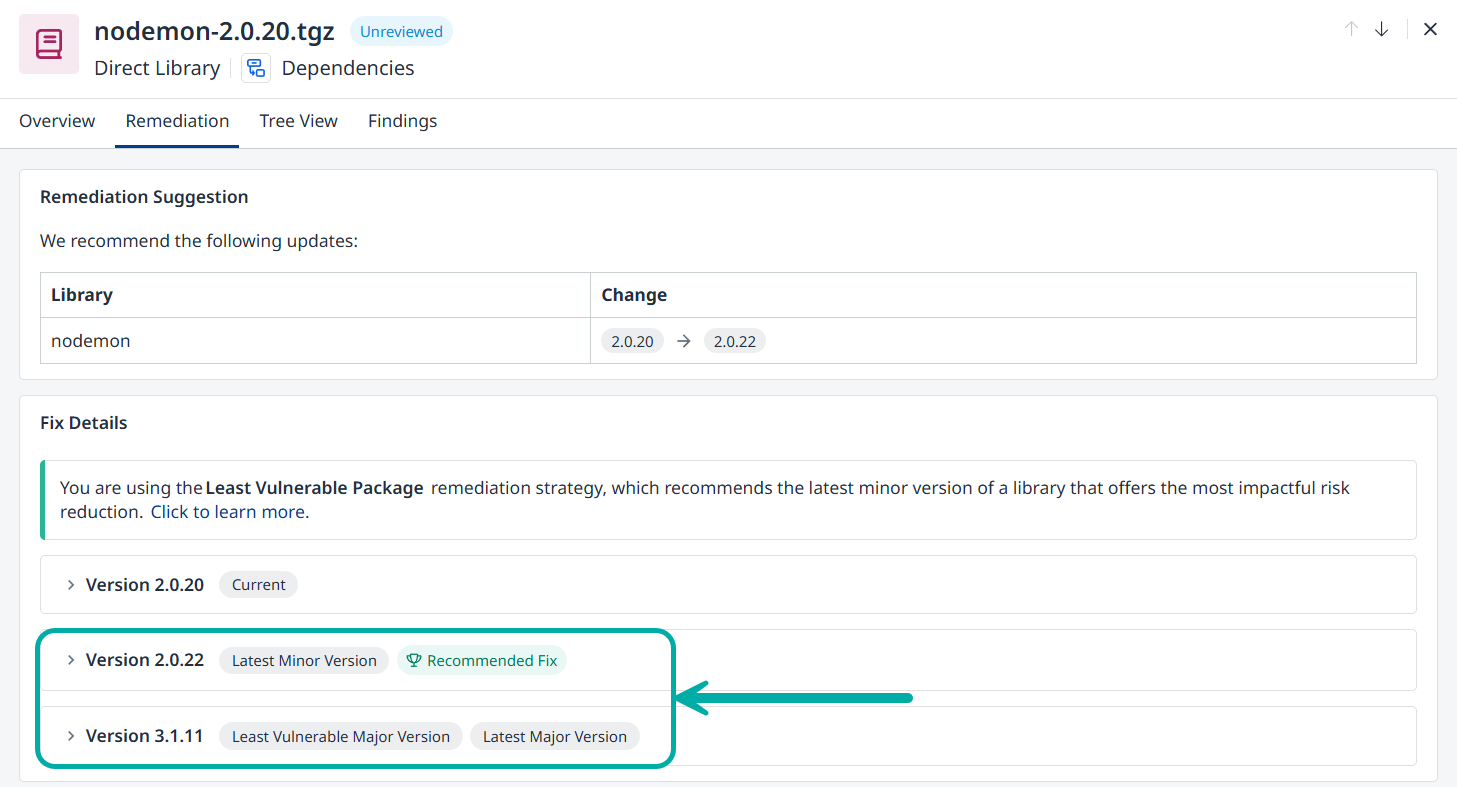
If no minor version upgrade recommendation exists, this will be denoted by an icon in the library’s Remediation column. Hovering on it will spawn a tooltip containing the following text: “No minor update is available. This upgrade may include breaking changes.”
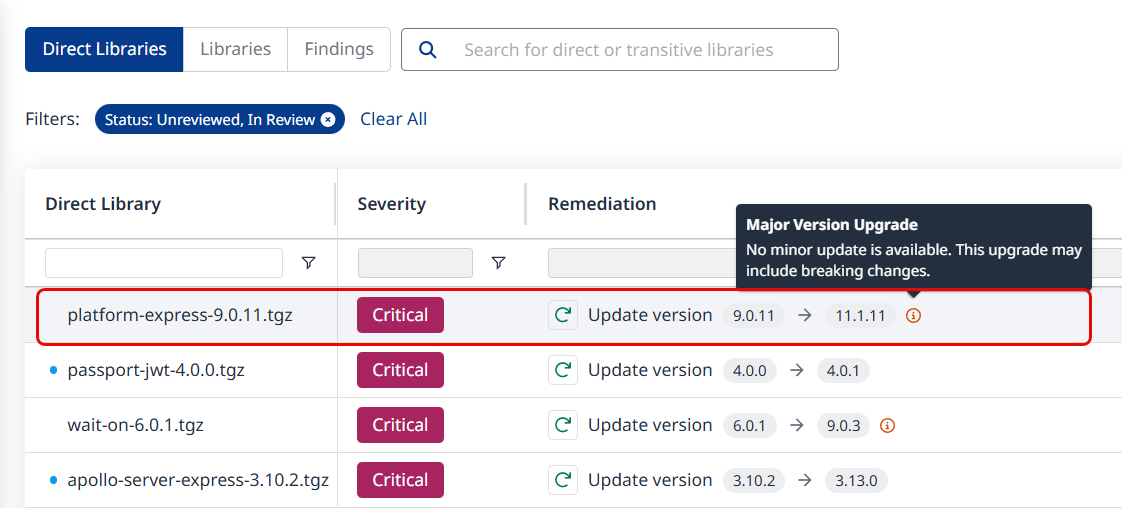
There is a possibility for multiple upgrade paths to result in the same upgrade recommendation. In such cases, they will be merged, as depicted below:
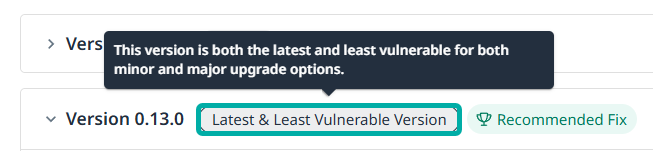
This scenario will be denoted by a tooltip containing the following text:
“This version is both the latest and least vulnerable for both minor and major upgrade options”.
LVP in the Repo
Supported on GitHub.com and GitHub Enterprise
In your repo-config.json or .whitesource file, the “
issueType" setting must be set to "DEPENDENCY"Remediate must be enabled.
Within your Mend repo integration, navigate to your repo-config.json (global) or your .whitesource (local repo) file.
Open your repo-config.json or .whitesource file in edit mode and add the
leastVulerablePackageSettings.trueparameter to enable LVP. This is set at the same level as thescanSettingsparameter:CODE"leastVulnerablePackageSettings": { "enabled": true }Enable Merge Confidence. by inputting the following parameter in your repo-config.json or .whitesource file →
remediateSettingsblock:CODE"extends": ["mergeConfidence:all-badges"]Save and commit your changes.
Kick-off a Mend scan by: GitHub.com - Initiating a Scan
Allow the Mend check run to complete and Remediate PRs to be created.
Navigate to the Pull requests tab to view your Remediate PRs:
Sample repo-config.json/.whitesource file
{
"scanSettings": {
"configMode": "AUTO",
"configExternalURL": "",
"projectToken": "",
"baseBranches": [],
"enableLicenseViolations": "true"
},
"checkRunSettings": {
"vulnerableCheckRunConclusionLevel": "failure",
"displayMode": "diff",
"useMendCheckNames": true
},
"issueSettings": {
"minSeverityLevel": "LOW",
"issueType": "DEPENDENCY"
},
"remediateSettings": {
"workflowRules": {
"enabled": true,
"minVulnerabilitySeverity": "LOW"
},
"extends": ["mergeConfidence:all-badges"]
},
"leastVulnerablePackageSettings": {
"enabled": true
}
}First Fix
Note: Fix recommendations are calculated at scan runtime. Applications/Projects scanned before the introduction of this feature may require a new scan for recommendations to appear in the UI.
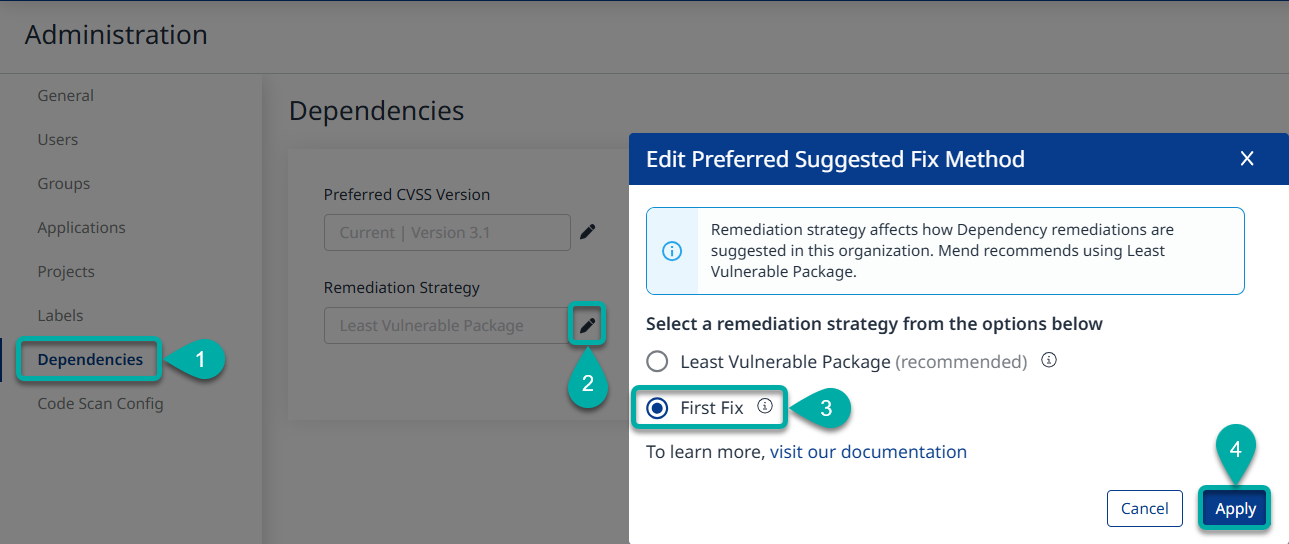
Choose First Fix as your Organization’s Remediation Strategy
Choose Administration from the drop-down menu at the top-right corner.
Step 1 - Click Dependencies on the left-pane menu.
Step 2 - Click the pencil icon to change your organization’s Remediation Strategy.
Step 3 - Select First Fix.
Step 4- Click Apply.
Review the First Fix Recommendations in the Platform UI
The First Fix information is available in the Recommended Fix tab of the vulnerability: