Understanding and Managing Vulnerabilities
Overview
Although open-source projects have many advantages, one main disadvantage is that they might contain vulnerabilities that can directly affect their users.
The National Cybersecurity FFRDC, operated by the MITRE Corporation, maintains the CVE (Common Vulnerabilities and Exposures) system, and publishes on a regular basis new known open-source vulnerabilities which potentially affect thousands of users.
In addition, Mend uses a proprietary patent-pending algorithm that matches the specific component with its vulnerability, resulting in a database that contains more than 175,000 vulnerabilities. These are collected every few minutes, from MITRE and other resources and repositories such as RubyOnRails, RetireJS, NodeSecurity and GitHub issue tracker.
Vulnerability Types
There are two types of vulnerabilities:
CVE (Common Vulnerabilities and Exposures): Provided by the MITRE Corporation, CVEs identify vulnerabilities by year and ID, and provide information about which library has the vulnerability, and which versions are vulnerable. CVE vulnerabilities are verified by MITRE and NVD.
CVE Identifier: ID given to a validated known vulnerability by MITRE in the CVE database.WS: Vulnerabilities that have no CVE identifier are provided by Mend due to scanning other repositories and advisories such as: Bugzilla, GitHub issue tracker, Node Security, etc.
After a WS vulnerability is found, Mend attaches a unique identifier to it, and provides all the relevant information (such as, vulnerable library, vulnerable versions, severity, etc.). WS vulnerabilities are verified by the Mend security research team.
WS Identifier: ID given to a validated known vulnerability by Mend as it has yet to be published to the CVE database/NVD.
The vulnerability identifier (Vulnerability ID) of either the CVE or WS type can be found in the Vulnerabilities Report and Security Alerts: View by Vulnerability screen.
Searching Libraries for CVEs and Vulnerabilities
This procedure describes how to perform a global search for CVEs and Mend vulnerabilities in your libraries, for informative, analysis, or reporting purposes.
Do as follows:
From any screen in the Mend Application, click the search icon at the top. The Global Search dialog box is displayed.
Select Library or Vulnerability.
If you select Library, enter the library, and in Type, select the type from the drop-down list and then click Search.
If you select Vulnerability, enter the vulnerability's individual CVE number, and click Search. An informative popup displays one of the following options:
The vulnerability is found in your library. Click View to view general information about this vulnerability in the Security Vulnerability screen.
The vulnerability is known to Mend but is not found in your library. Click View to view general information about this vulnerability in the Security Vulnerability screen.
The vulnerability is not known to mend, and therefore not found in your library. Click Report to report this vulnerability to Mend for further analysis and for inclusion in its database of vulnerabilities.
Viewing and Utilizing Vulnerabilities Information
Mend provides detailed information regarding any vulnerabilities in your products, as described in the following sections.
Viewing Vulnerability Alerts
In the Organization Alerts pane in the Mend Home page, you can see general information regarding the alerts in your organization and specifically the total number of vulnerability alerts that were found, with their color-coded severity levels. By clicking the summary number, you can open an alert view showing detailed report data about the vulnerabilities. For details, see Security Alerts: View by Vulnerability.
Vulnerability Impact Analysis
From the Vulnerability Analysis pane in the Mend Home Page, you can determine the impact of the vulnerabilities in your organization.
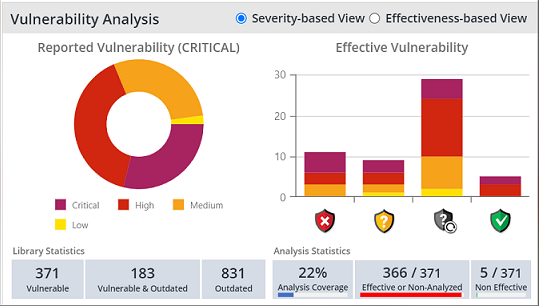
The Reported Vulnerability pie chart shows the library distribution based on the highest vulnerability severity – Critical, High, Medium, or Low. Clicking on the pie chart launches the Security Alerts: View by Library screen, where you can see the libraries and projects that each vulnerability appears in, review vulnerability statistics, such as the number of reported vulnerabilities and ignored alerts for a selected library, and ignore and activate (restore) a selection of vulnerability alerts associated with a library.
The Effective Vulnerability graph shows the vulnerability severity distribution based on an effectiveness indicator (i.e., shield). Clicking on the graph launches the Security Alerts: View by Vulnerability screen, where you can manage the alerts per vulnerability according to specific products/projects. For example, use this screen to ignore alerts of a specific vulnerability across all libraries in the selected scope.
Viewing the Vulnerabilities of your Libraries
The Vulnerabilities Report contains all relevant information about your vulnerabilities and is the best way to view the vulnerabilities of your libraries. For details on how to access and view this report, see the Vulnerabilities Report.
IMPORTANT: If you are working with Security Alerts: View By Vulnerability enabled, this report was removed and its functionality can now be accessed through the Security Alerts: View By Vulnerability alerts. See Security Alerts: View by Vulnerability.
The vulnerability identifier (Vulnerability ID) of either the CVE or WS vulnerability type can be found in the Vulnerabilities Report. Clicking the vulnerability identifier link in the Vulnerability ID column navigates you to the Security Vulnerability screen where more specific information is provided about the vulnerability.
Security Vulnerability Screen
To access the Security Vulnerability screen, do as follows:
Click the relevant Vulnerability ID link in the Vulnerabilities Report.
-Or
Click the relevant Vulnerability ID link in the Security Alerts: View By Vulnerability screen.
The Security Vulnerability screen displays the following information:
Relevant information regarding the specific vulnerability such as its ID, description, and CVSS3 base score metrics (when available).
Libraries that are vulnerable due to this specific vulnerability.
Suggested fixes to this vulnerability, sorted according to their popularity (the first one will be the one with the most votes as useful).
Any other references (if they exist) that may assist you. For example, the CVE links to mend's informative Vulnerability Lab.
For example:
Marking Suggested Fixes as Useful
It is highly recommended to mark a suggested fix to a security vulnerability as useful.
To do this:
In the Security Vulnerability screen, next to the fix that you found useful, click the star:
As a result, this fix will be the first one to appear in your Vulnerabilities Report.
