Scan container images from your Kubernetes clusters with Mend
NOTE: This page is only applicable for users still on the container solution in the Legacy SCA Application (“Cloud Native” UI). Most users will be directed to Mend Container in the new Mend AppSec Platform upon trying to access the Cloud Native UI.

Overview
Empower your teams with our Kubernetes (K8s) integration solution. Our K8s integration allows getting all deployed images from your K8s environment to prioritize them, with the deployment context that we retrieve from the K8s environment, helping you understand not only potential security risks, but prioritizing them based on what is deployed, and where.
Use cases for integrating Kubernetes with Mend
By including the Mend K8s integration into your toolkit, you:
Allow your DevOps team to perform on-demand scans to monitor the images currently running in production environments, helping to identify any vulnerabilities or issues at a specific point in time.
Support risk-based management for your AppSec Manager and Security Champions by identifying and prioritizing the most critical vulnerabilities detected on your deployed images.
Help your AppSec Manager maintain an updated inventory of the running images captured during each scan, aiding in effective and potential updates.
Getting it done
Configure the Mend Kubernetes integration
To learn more about setting up Mend with your K8s environment, read here:
Trigger the Mend Kubernetes integration
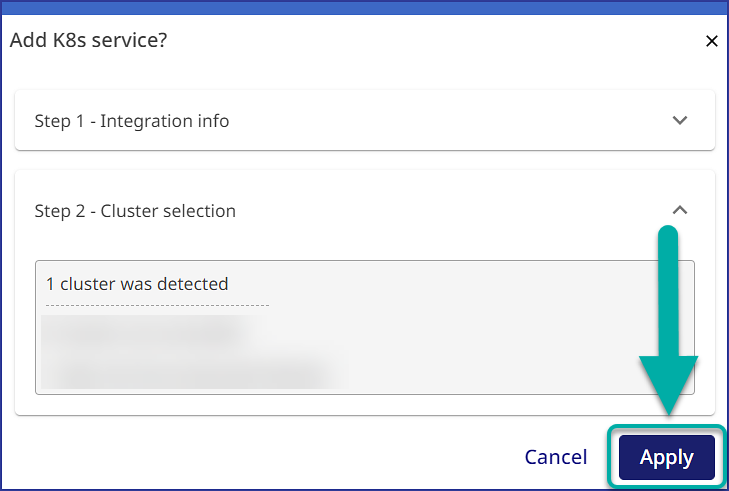
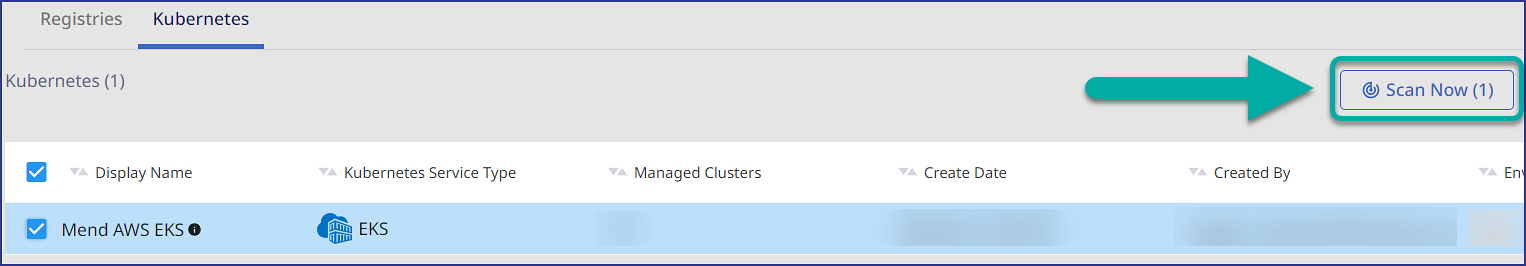
Run the Mend K8s integration scan within the Mend Cloud Native Application UI via one of the following actions:
Clicking on the Apply button during your initial configuration setup:
Selecting your K8s integration and clicking on the Scan Now button within the Kubernetes tab:
View the results of the Mend Kubernetes integration
Visit our Review your Mend Kubernetes integration results document to understand the findings of your Mend K8s integration scan.
Reference
Mend Kubernetes integration-supported environments
We support the following K8s services for the Mend K8s integration:
Amazon Elastic Kubernetes Service (Amazon EKS)
K8s native (i.e. kind)
Boundaries of the Mend Kubernetes integration
The Mend K8s integration scans images from accessible clusters and from running pods.
The Mend K8s integration scans images that are accessible to the Mend Cloud Native Application via a Docker V2-based public registry or via an existing Mend private registry integration.
Editing an existing Mend K8s integration is not currently available. You must create a new integration within the Kubernetes tab of the Cloud Native Application UI to apply any changes.
Rescanning an existing Mend K8s integration is currently only available via the Scan Now button within the Kubernetes tab.
Mend Kubernetes integration service user
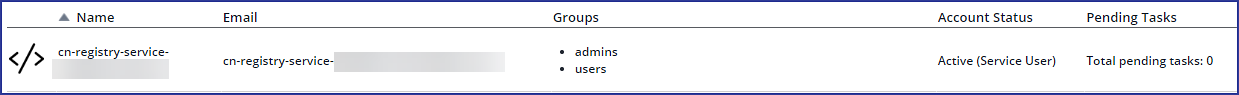
When you configure and activate our Kubernetes integration for the first time, a service user is automatically created within the integrated Mend organization.
The service user will have a name similar to “<cn-registry-service-unique_string>”. This service user is automatically added to the admins Group (with organization administrator permissions) and is required for the integration to function properly.
You can view this service user via the Mend SCA UI → Admin - Users page.