Configure Amazon EKS with Mend’s Kubernetes integration
NOTE: This page is only applicable for users still on the container solution in the Legacy SCA Application (“Cloud Native” UI). Most users will be directed to Mend Container in the new Mend AppSec Platform upon trying to access the Cloud Native UI.

Overview
The Mend Kubernetes (K8s) integration can connect with your Amazon EKS service using your provided access and secret keys.
Getting it done
Prerequisites before you configure Mend’s Kubernetes integration for Amazon EKS
Your Mend user must be an organization administrator in order to access the Cloud Native UI.
Your Amazon EKS role that owns the access and secret keys provided to Mend for authentication must have an IAM policy attached with the necessary actions for all relevant K8s clusters. See the Amazon EKS setup for Mend K8s integration access section of this document for instructions.
Amazon EKS setup for Mend K8s integration access
Create/Edit an AWS user with the following IAM policy that includes these policy permissions:
CODE{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sts:AssumeRole", "eks:ListTagsForResource", "eks:AccessKubernetesApi", "eks:DescribeCluster", "eks:ListClusters" ], "Resource": "<USER_ARN>" } ] }
Mend Tip: If you are scanning images from your private ECR, make sure to include the permissions needed for Mend to integrate with your private registries: Configure your private Amazon Elastic Container Registry (ECR) with Mend. Also, here are additional reading sources from AWS:
Create access and secret keys for this user via the Security Credentials tab → Access keys section within AWS. Keep the access and secret keys on hand for the integration steps later on within the Mend Application. For assistance within AWS, read here: Managing access keys (console).
Apply Mend’s Cluster Role provided below to each of the clusters you wish to integrate. This step allows Mend access to the clusters to obtain the list of running images. In the
mend-readonly-group.yamlYAML file example below, we usereadonly-groupas the value for thegroupname:
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: readonly-clusterrole
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs: ["get", "watch", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: readonly-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: readonly-clusterrole
subjects:
- kind: Group
name: readonly-group
apiGroup: rbac.authorization.k8s.io"*" can be replaced with a specific list of resources, based on your needs.
Mend Tip: You can apply the YAML file above with kubectl via the following command: kubectl apply -f mend-readonly-group.yaml. Also, here are additional reading sources from AWS:
Within the ConfigMap, add your AWS user (from step one) and its ARN under the
mapUserssection:Open the ConfigMap (i.e via the kubectl command:
kubectl edit configmap aws-auth -n kube-system)Using our
readonly-groupexample from step three, add to themapUserssection (or create amapUserssection, if needed) the following:CODEmapUsers: | - userarn: <USER_ARN> username: <USERNAME> groups: - readonly-group
Save your changes and exit out of the files. You are now ready to configure the integration within the Mend Application.
Set up the Mend Kubernetes integration for Amazon EKS in the Mend Application
Within the Mend Application, navigate to the Cloud Native UI:

Navigate to the Integrations dashboard:
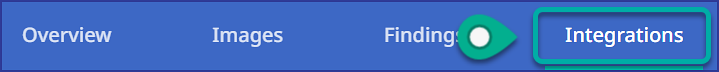
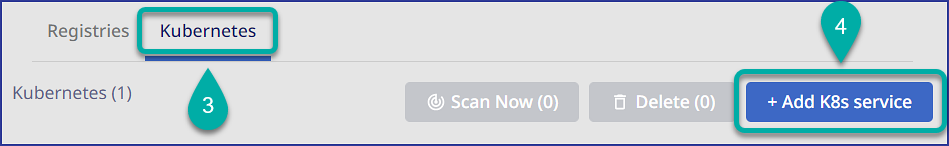
Click on the Kubernetes tab.
Click on + Add K8s service:
The “Add K8s service?” pop-up wizard appears. Select AWS EKS for the Service Type setting to start the configuration setup for Amazon EKS.
Fill out the Step 1 - Integration info section with your Amazon EKS information. For more information on the parameters provided, refer to the Amazon EKS parameters section within this document:
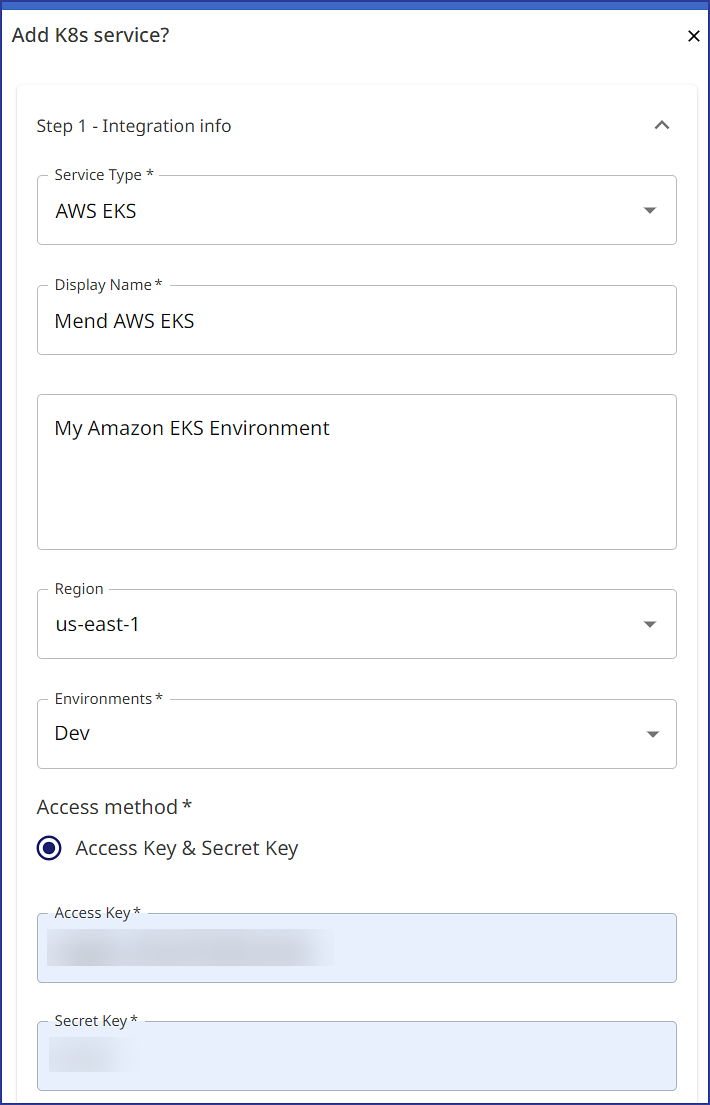
Once you provide your Access Key and Secret Key, click on Submit:
In Step 2 - Cluster selection, confirm the number of clusters identified is correct and which are accessible to Mend for the integration:
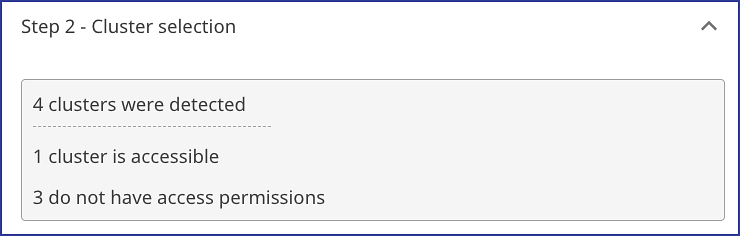
Click on Apply to add your Amazon EKS K8s integration:

Reference
Mend Kubernetes integration - Amazon EKS parameters
Parameter | Description |
|---|---|
Display Name | The name of your K8s integration. This will be displayed in the Integrations dashboard → Kubernetes tab. |
Description | Optional. Provide any text. We recommend providing information that will help you remember the integration. |
Region | Select the AWS region where your Amazon EKS is hosted. The region options are:
|
Environments | Select the type of environment of your Amazon EKS (multiple options can be selected). The environment options are:
|
Access method | The method to authenticate Mend with your Amazon EKS environment. The available options are:
|
Access Key | Provide your user access key for your EKS environment |
Secret Key | Provide your user secret key for your EKS environment. |
