Trigger repository scans manually with Mend for Azure Repos global configuration
Overview
This feature enables users to trigger scans for specific repositories manually.
For each repository in the list, a scan will be triggered (in the latest commit of the specified branch), including the creation of the security check run.
Getting It Done
The scan.json file
In order to trigger the manual SCA scan, a file called scan.json needs to be pushed to the whitesource-config repo. The scan.json file contains a list of repositories and their branches to scan, and can also be configured to save the scan logs to a defined ws-logs repository. More information on these features is included in the setup section below.
Note:
The
repositorieslist is limited to ten. If there are more than ten repositories included in the scan.json file, no repositories will be scanned, and a check run will be created.If a branch name is not specified, the default branch will be scanned.
Setup
Within your Azure DevOps project, create a “whitesource-config” repository and a “ws-logs” repository.
Ensure that your Azure DevOps PAT for the Mend integration has access to these two repositories within your Azure DevOps project.
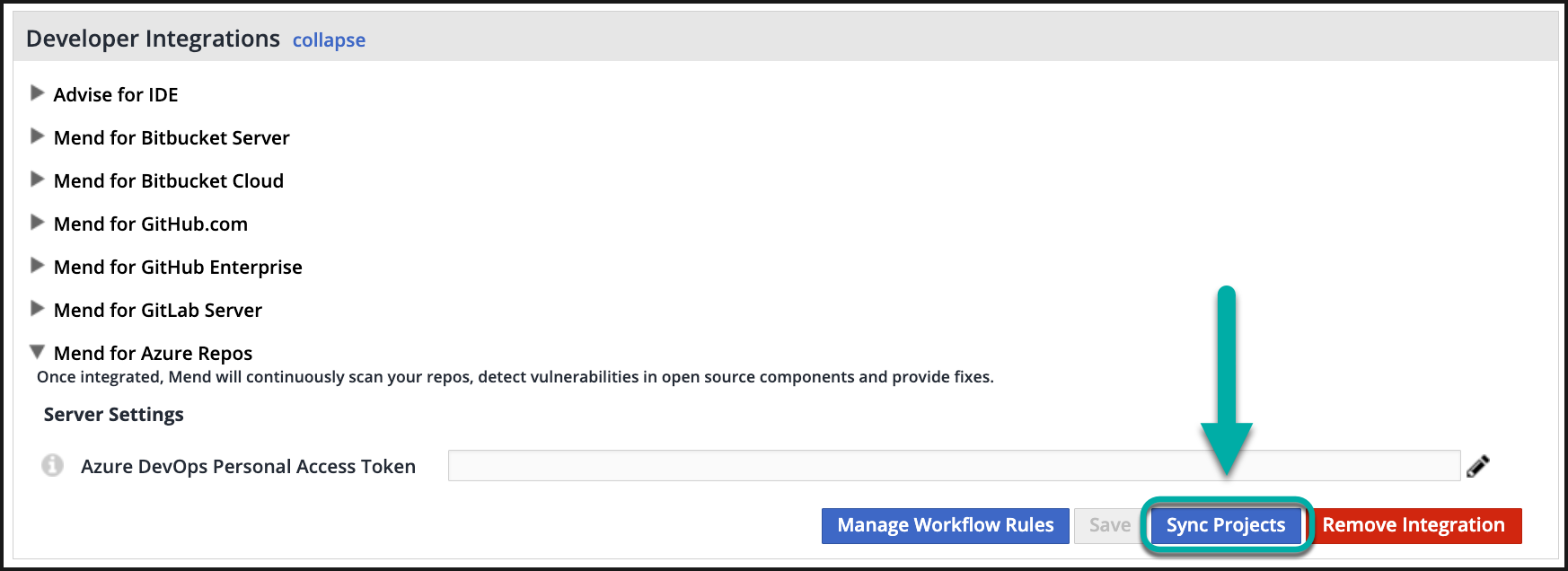
Sync your Azure project by going into your Mend UI → Integrations tab → Azure Repos → Sync Projects.
Note: This will kick off the integration to check if there are any new repos that need to be onboarded (this being the "whitesource-config" and "ws-logs" repos you created in step 1).
Check your "whitesource-config" repo; there should be a global-config.json and a repo-config.json.
Within your "whitesource-config" repo and create, commit, and merge the scan.json file with the following settings:
CODE{ "repositories": [ { "fullName": "Azure_Project_Name1/repoName1", "branchName": "main", "uploadScannerLogs": true } ] }
Note: The parameter uploadScannerLogs should be set to true within the scan.json in order to generate Mend for Azure Repos manual scan logs.
Once you merge this commit with the scan.json, this will trigger the manual scan on both the "master" and "dev" branches.
In the commit, you will see the Status as PENDING. Once the manual scan is completed, you will see a commit message stating "The manual scan(s) process completed successfully", with a status of TRIGGERED.You will also see another commit stating that the scan.json has been deleted, as the manual scan process completed.
Go to the "ws-logs" repo. There you will find:
A commit with the following message: "Added log files for scan token X". You can download the ZIP folder from here. (This scan token is also helpful to us in Support for troubleshooting).
Two ZIP folders within the "Files" of the "ws-logs" repo.
These ZIP folders contain the scan log for each branch (“dev” and “master”), which is titled "unified-agent-log.txt".
Note
The format of the scanZIP file name is
scanner_logs_{SCAN_TOKEN}.zip.If the
ws-logsrepository does not exist, the manual scan will not run and the following check run will be created, explaining the reason: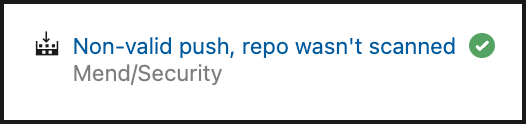
Reference
scan.json Parameters (repositories)
Parameter | Type | Description |
|---|---|---|
fullName | String | Required. Provide a list of specific repositories to trigger the manual scan on. For example:
CODE
|
branchName | String | Optional. Default Value: |
scanType | String | Optional. By default, the scan.json file only triggers manual SCA scans.
CODE
|
uploadScannerLogs | Boolean | Optional. Default Value:
|