Scan your Infrastructure as Code (IaC) with Mend for GitHub Enterprise
Overview
Mend for GitHub Enterprise’s IaC scan provides a review of your Infrastructure as Code (IaC) configuration files.
Use Case
Mend for GitHub Enterprise IaC scans can be utilized in the following ways:
You, a DevOps engineer, before deployment, want to ensure that your cloud infrastructure is following best practices in the commits made to your GitHub repository.
You, a development team leader, are responsible for a repository and want to make sure there are no violations in your team’s IaC configuration files. You want to monitor the overall state of the repository.
Mend’s Answer: With every valid commit, the IaC scan creates a Mend IaC Check that provides an overview of all violation details as well as generates GitHub Issues for each violation and how to confront them using provided best practices. This is all done without you ever needing to leave GitHub Enterprise.
Getting It Done
Once you have installed the Mend for GitHub Enterprise app, you will see a GitHub Pull Request (PR) created by the whitesource/configure branch appear in your integrated repositories. This is also referred to as the Mend for GitHub Enterprise "onboarding PR.":
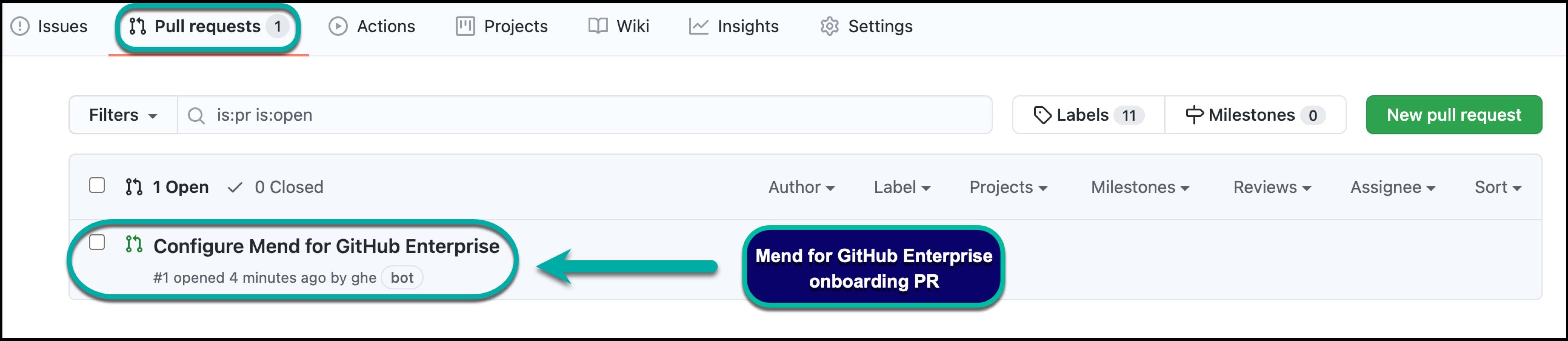
The “onboarding PR” will contain the .whitesource file, which handles the configuration of your Mend for GitHub Enterprise scan. You can edit the .whitesource file before merging the onboarding PR to ensure that your first scan is configured appropriately for your repository:
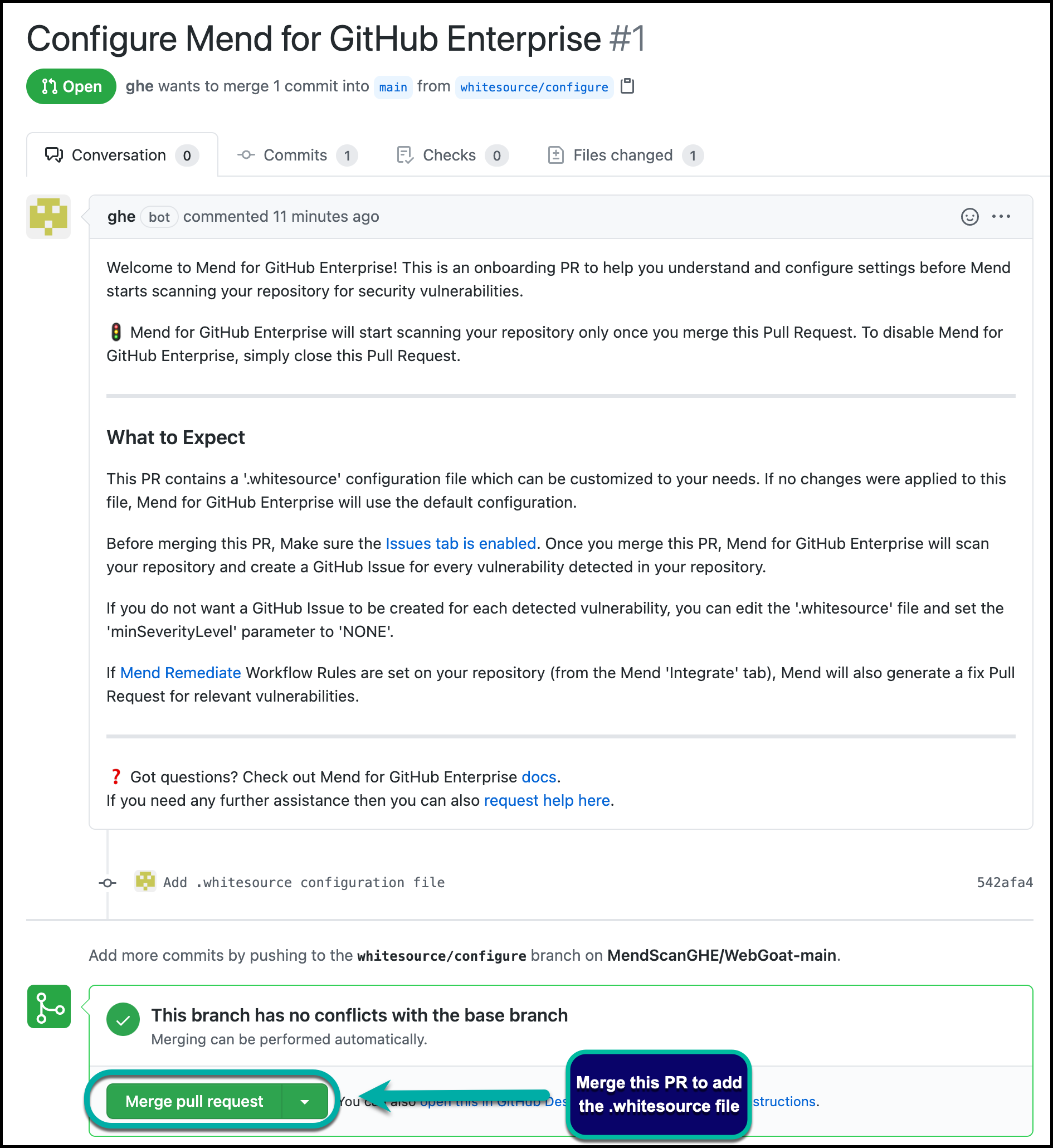
Configure
The .whitesource file is used to configure Mend for GitHub Enterprise IaC scans. To learn more about the IaC-supported environments, configuration, and available parameters, please visit our Configure Mend for GitHub Enterprise for IaC documentation.
Start the Scan
Once you merge the onboarding PR into your default branch, this will start the first IaC scan on your repository.
Any concurrent IaC scans on your repository are initiated via a valid GitHub push command. As the IaC check relies on the SCA check, a valid push command meets at least one of the following requirements:
Note: IaC scans can only be performed on base branches.
One of the commits in the push command added/removed a source file(s) that has an extension supported by Mend. Refer to the Mend Languages page in order to find out whether or not a specific language and its extensions are supported.
One of the commits in the push command includes an addition/deletion/modification of the package manager dependency file(s). Refer to the list of supported dependency files to find out whether your dependency files are supported.
For Go, Python, JavaScript, or Maven projects, when the manifest file (go.mod, Pipfile, package.json, or pom.xml) is changed, the scan will be triggered only if the dependencies section is changed.
Note:
A push command may consist of multiple commits.
You can manually trigger a scan for several repositories at once. For more information, refer to our Global Configuration document.
View the Scan Status
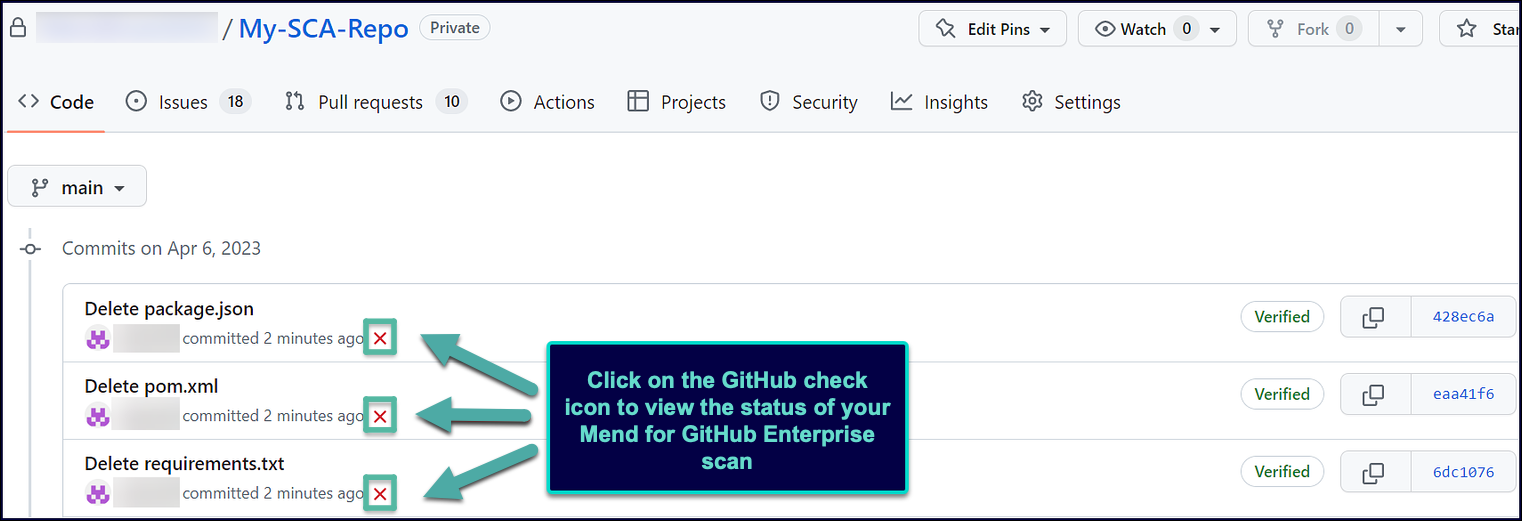
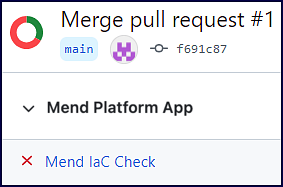
Once the scan is started, there is a GitHub check created called Mend IaC Check.
Within GitHub, In the Code > commits page of your repository, you can view the status and results of each scan. Click a specific check icon in order to view the Mend check:
The following commit status indicators are available as feedback on the head commits:
Success: (Green checkmark icon) No IaC violations were detected.
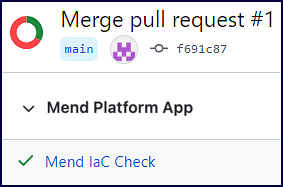
Failure: (Red ”X” icon) One or more IaC violations were detected during the Mend scan.
View the Scan Results
Once your Mend for GitHub Enterprise scan has been completed, there are multiple resources to review your results. For more information to help you in understanding your findings, visit our View the results of your Mend for GitHub Enterprise IaC scan documentation.
