The Dependencies Risk Report
Overview
The Dependencies Risk Report, accessible via Mend AppSec Platform’s main navigation, is a management-level tool that provides a bird's-eye view of all aspects of an account's open-source libraries with regard to security, quality and compliance. It identifies vulnerable and outdated libraries, providing details on severity levels, available fixes, and license risks. The report delivers clear and actionable data to help maintain the security and compliance of your applications.
Getting it done
You can generate the report via the Reports page.
Click the Reports button located in the top bar of the Mend Platform user interface:

Click the Create button (
 ) at the top-right edge of the Reports page.
) at the top-right edge of the Reports page.
Select Dependencies Risk from the drop-down list of the Create Report wizard:
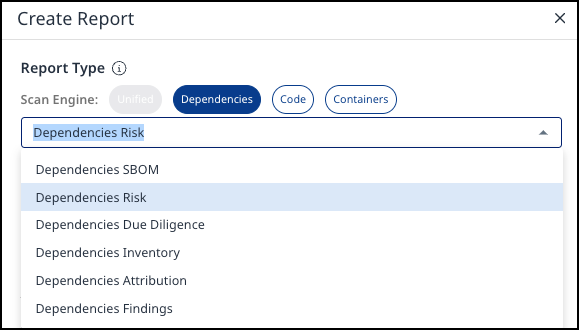
Scope - Define the report's scope by specifying the application. You can refine the scope by selecting one or more projects within that application.
Configuration - Specify the Report Name. The Format is PDF.

Notification – Get notified by email when the report is ready by selecting the Send me an email notification when this report is ready checkbox.
Click Create.
Once the report is ready, you can download its .pdf from the main Reports page:
Understanding the Dependencies Risk Report
The Dependencies Risk Report provides a detailed analysis of the open-source libraries used in your application / project. It highlights key information on security vulnerabilities, outdated libraries, and licensing risks.
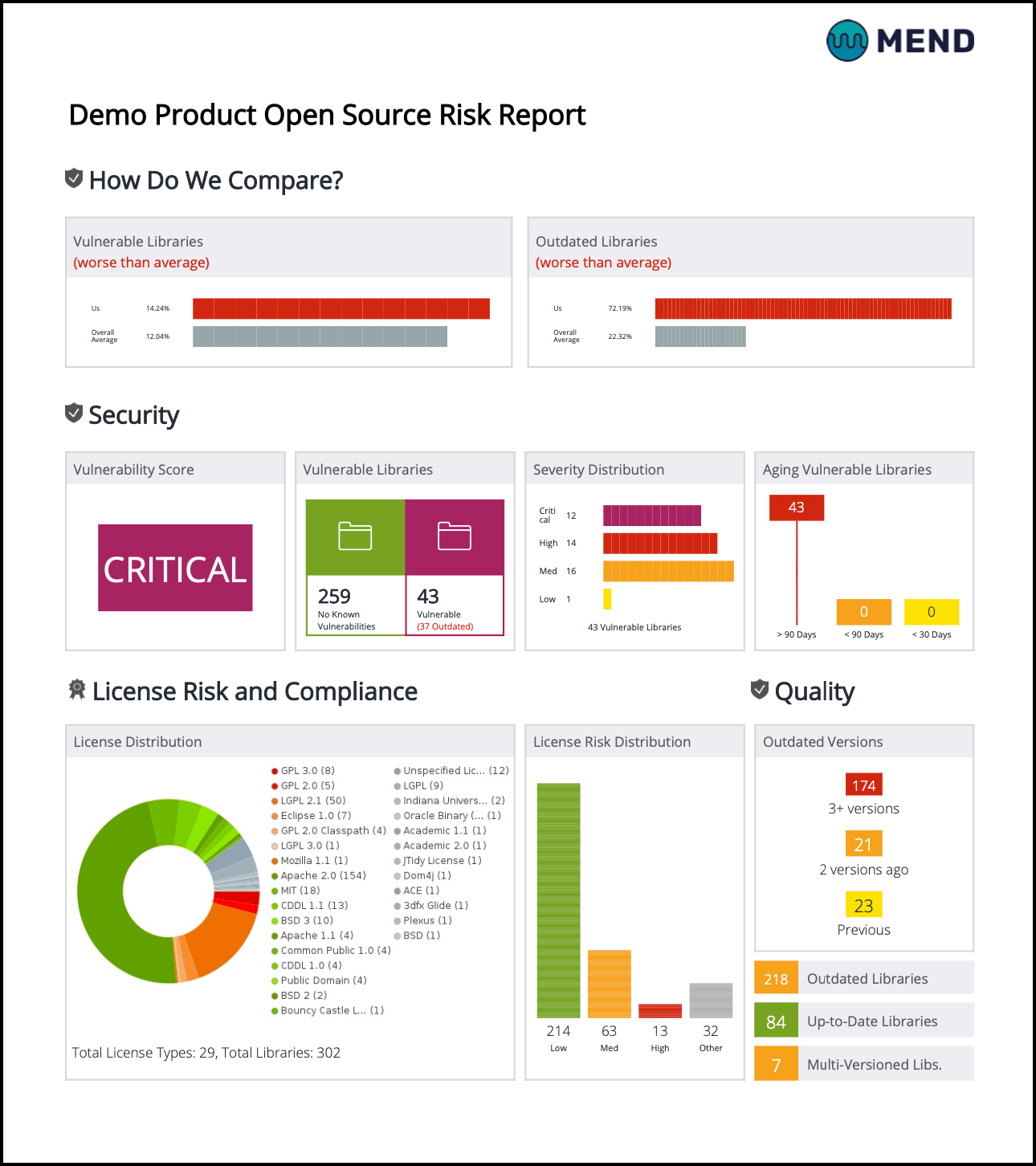
The first page of the report contains information about the selected scope [Application / Projects(s)] and the creation date. Various security and license risk metrics will be displayed in 3 panels:
How Do We Compare? (not available at the project level)
Security
License Risk and Compliance
How Do We Compare?
NOTE: This panel is not available at the project level.
The “How Do We Compare?” panel displays how selected measurements of your organization's risk and compliance levels compare to overall average statistics calculated for Mend customers. It includes the following three charts:
Vulnerable Libraries: The percentage of vulnerable libraries in your application/project compared to the overall average calculated for Mend customers.
Outdated Libraries: The percentage of outdated libraries in your application/project compared to the overall average calculated for Mend customers.
NOTE: An indication is also provided (in brackets) showing if the above measurements are better than average/worse than average.
Security
This panel displays a high-level graphic analysis of the health of your software. This includes the vulnerability score (based on the highest severity vulnerability), number of vulnerable components out of total components, severity distribution, aging security vulnerabilities, license risk distribution, outdated components out of total components and libraries with multiple versions.
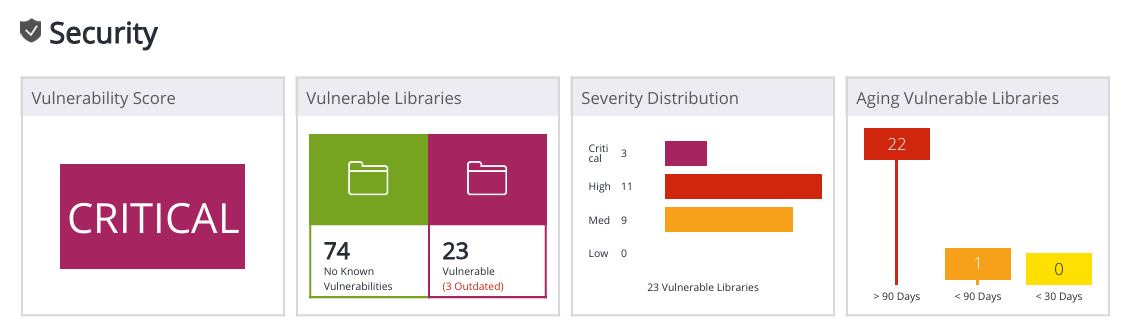
Panel | Description |
|---|---|
Vulnerability Score | Displays the highest severity in the scope (Application / Project). |
Vulnerable Libraries | The following statistics can be displayed about Vulnerable libraries:
|
Severity Distribution | Counts the distribution of the highest severity vulnerability of all libraries. If a library has critical, high, medium and low vulnerabilities, it is counted as 1 Critical. |
Aging Security Vulnerabilities | Vulnerability count by vulnerability age. |
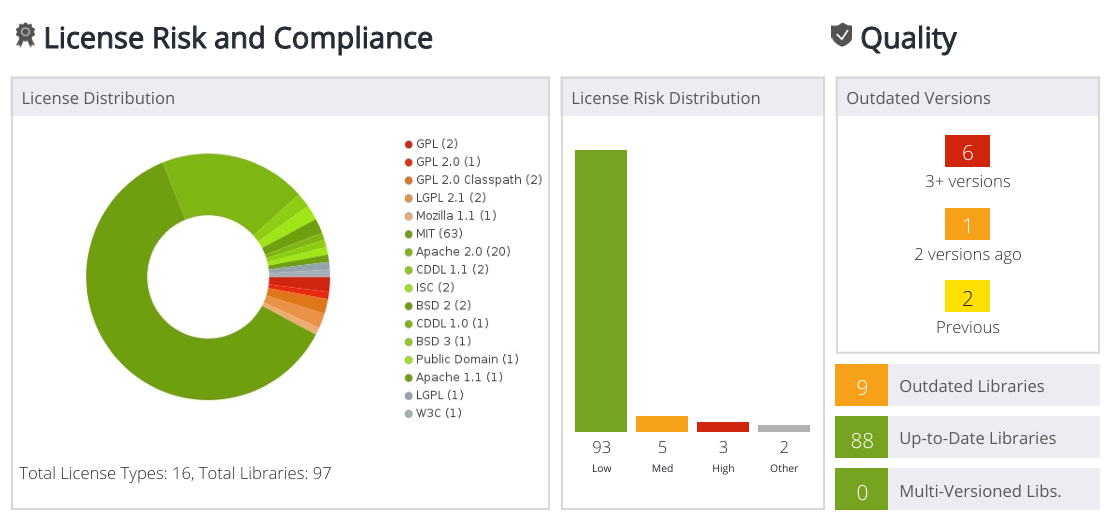
License Risk and Compliance
This panel provides an overview of the License Distribution of the application, showing which licenses are used and how many libraries are associated with each license.
This panel also provides the License Risk Distribution, indicating the number of policy-violating libraries, and how many libraries are associated with each license (see Risk Score Rating). The Other bar refers to libraries with unspecified licenses, or licenses that have yet to be rated.
Quality
This panel on the right provides information about outdated library versions and libraries with multiple versions.
The Report Body - Key Sections
General Overview
The General Overview section of the report provides a summary of all the libraries in your application / project. Columns:Project - The project within the application for which the summary is displayed.
Libraries - Displays the overall number of dependencies in the project, the number of direct dependencies, and the number of indirect dependencies (where applicable).
Licenses - Displays the overall number of licenses in the project alongside the risky licenses.
Security - Displays the overall number of vulnerabilities in the project alongside the outdated libraries.
Last Scan - Applicable for application and project-level reports only, this column displays the date of the most recent scan performed on each project.
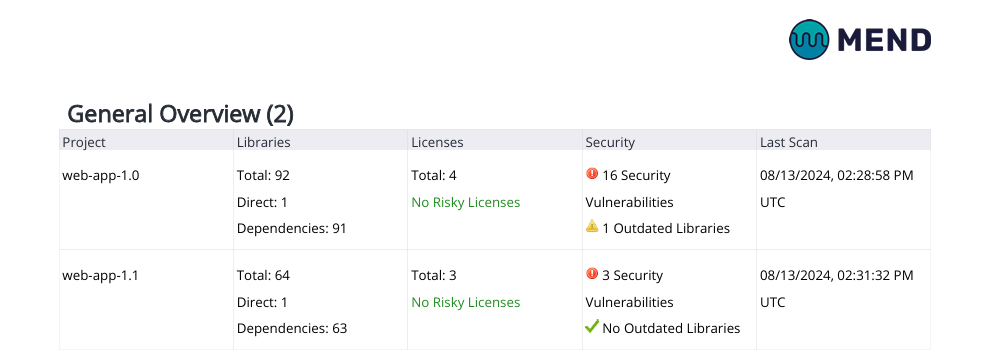
The General Overview Table in an Application-level Dependencies Risk Report
Security Vulnerabilities
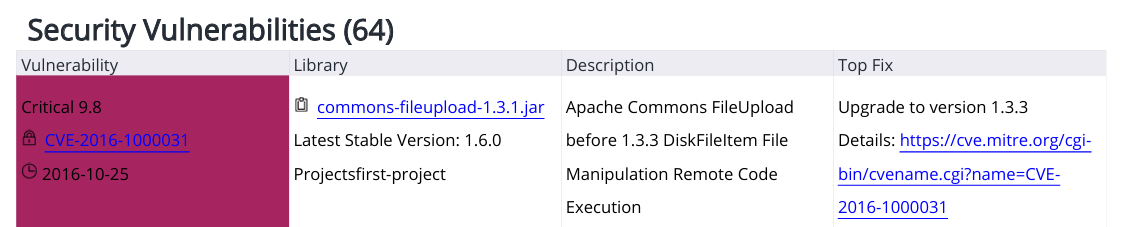
Security vulnerabilities are sorted by severity (Critical / High / Medium / Low) and score, in a descending order from highest to lowest.
The aging of vulnerabilities is also displayed, such as how long they’ve been present in the codebase. Columns:Vulnerability - specifies the severity and score, as well as the CVE ID.
Library - specifies the impacted library, as well as its latest stable version.
Description - describes the vulnerability.
Top Fix - specifies the recommended fix and the relevant reference.
Outdated Libraries
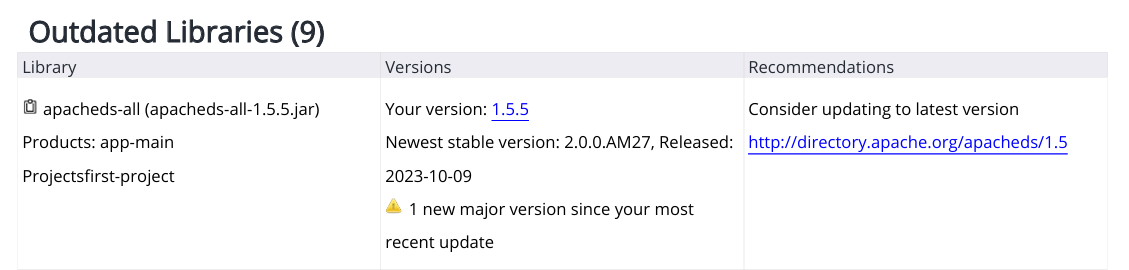
Identifies outdated libraries by one or more versions, detailing how far behind each library is from the latest release. Columns:Library - specifies the outdated library detected in your inventory.
Versions - specifies your version vs. the newest stable version.
Recommendations - provides a mitigation recommendation, e.g., upgrade to the latest version.
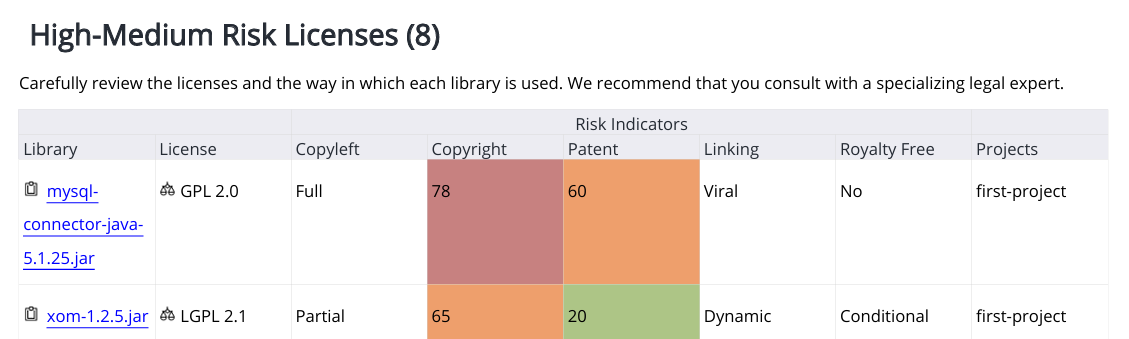
License Risk and Compliance
Assesses the legal risks associated with the licenses governing your libraries and flags those that might pose compliance risks. Licenses are classified by risk level (High / Medium / Low). Columns:Library
License
Risk Indicators
Copyleft
Copyright
Patent
Linking
Royalty Free
Projects