The Dependencies Findings Report
Overview
The Dependencies Findings Report, accessible via your Mend Platform’s main navigation, provides a detailed summary of the vulnerabilities found in the open-source libraries used in your project. It highlights each vulnerability by its severity, CVSS score, and affected library, offering precise data on the security posture of your dependencies. This report includes essential information like CVE IDs, affected versions, and available fixes for each finding.
Getting it done
You can generate the report via the Reports page.
Click the Reports button located in the top bar of the Mend Platform user interface:

Click the Create button (
 ) at the top-right edge of the Reports page.
) at the top-right edge of the Reports page.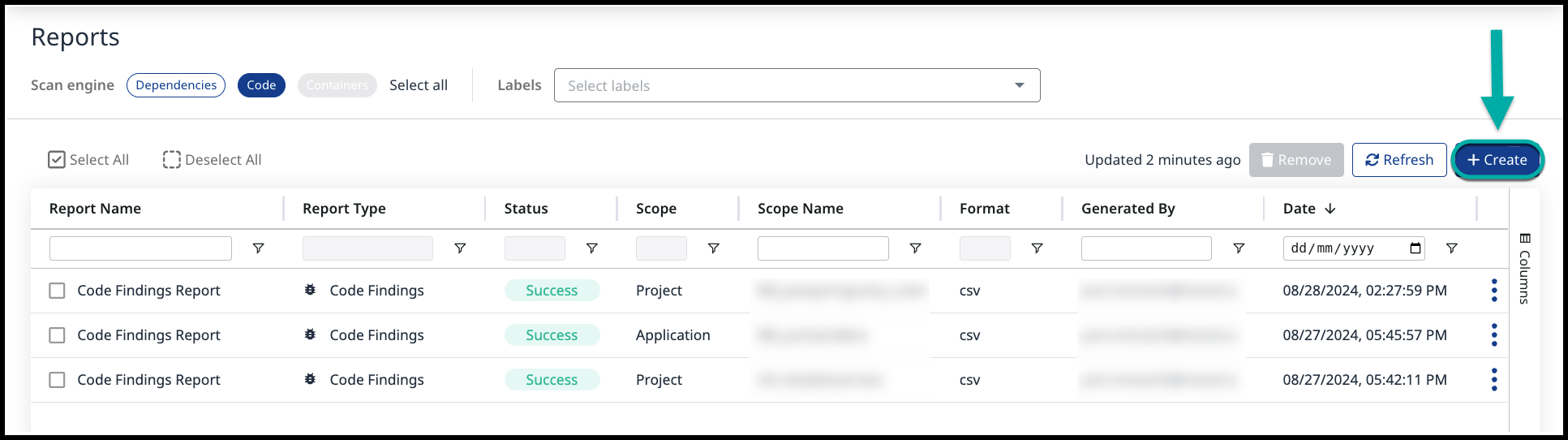
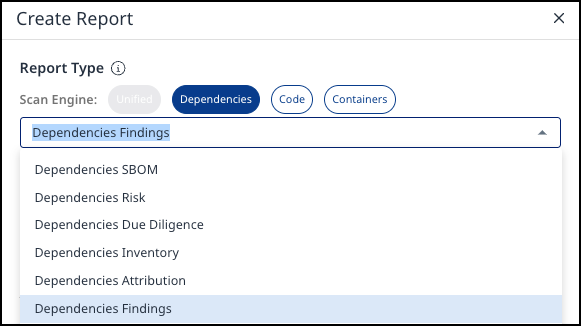
Select Dependencies Findings from the drop-down list of the Create Report wizard:
Scope - Define the report's scope by selecting one of the following:
- Organization: Generate an organization-level report, combining findings from all applications and projects in the organization.
- Application/Project: Refine the scope by selecting one or more projects within a selected application.
- Label: Include all findings from applications/projects that carry a specific label, e.g., “Team A”.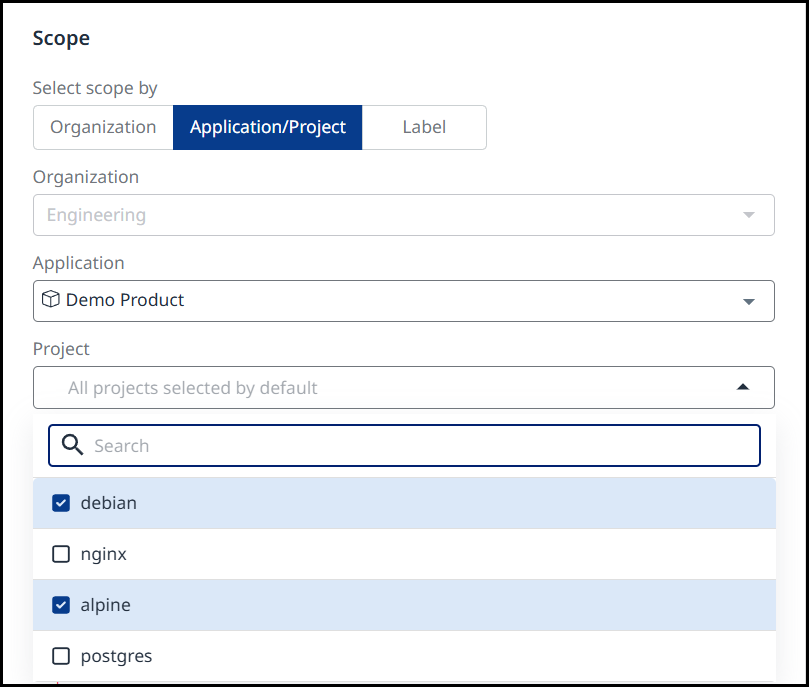
A Selection of Projects within an Application
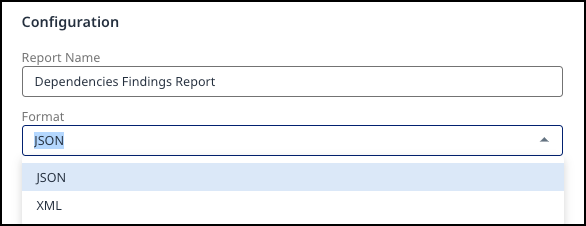
Configuration - Specify the Report Name and Format (JSON/XML).
Findings Type – Choose the findings to include in your report: Malicious Packages, Security Findings, and suppressed vulnerabilities. All findings are selected by default, but you can adjust your selection as needed.

Notification – Get notified by email when the report is ready by selecting the Send me an email notification when this report is ready checkbox.
Click Create.
Understanding The Dependencies Findings Report
The Dependencies Findings Report will show the following details, repeated for each dependency.
Example of the report in table format:
| Name | Type | Severity | Score | CVSS3 Severity | CVSS3 Score | Publish Date | Last Updated Date | Score Metadata Vector | URL | Description | Project | Product | CVSS3 Attributes | Library | Top Fix | Locations |
|---------------|------|----------|-------|----------------|-------------|--------------|------------------|------------------------------------------------|------------------------------------------------------------|--------------------------------------------------------------------------------------------------|------------|------------|------------------------------------------------|------------------------------------------------|-------------------------------------------------------------------------------------------------|-----------------------------------------------------------------------------------------|
| CVE-2023-6378 | CVE | High | 7.1 | HIGH | 7.1 | 2023-11-29 | 2024-08-02 | CVSS:3.1/AV:L/AC:L/PR:N/UI:N/S:C/C:N/I:N/A:H | https://www.mend.io/vulnerability-database/CVE-2023-6378 | A serialization vulnerability in logback receiver component part of logback version 1.4.11 allows| GH_WebGoat | GH_WebGoat | Attack Vector: LOCAL, Attack Complexity: LOW, | logback-classic-1.4.11.jar | Upgrade to version ch.qos.logback:logback-classic:1.3.12,1.4.12 (2023-11-29) | /home/wss-scanner/.m2/repository/ch/qos/logback/logback-classic/1.4.11/logback-classic- |
| CVE-2024-3653 | CVE | Medium | 5.3 | MEDIUM | 5.3 | 2024-07-08 | 2024-09-14 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L | https://www.mend.io/vulnerability-database/CVE-2024-3653 | A vulnerability in Undertow requires enabling the learning-push handler, which, if misconfigured,| GH_WebGoat | GH_WebGoat | Attack Vector: NETWORK, Attack Complexity: LOW,| undertow-servlet-2.3.10.Final.jar | Upgrade to version io.undertow:undertow-core:2.2.34.Final, io.undertow:undertow-servlet:2.2.34.F| /home/wss-scanner/.m2/repository/io/undertow/undertow-servlet/2.3.10.Final/undertow-ser |
| CVE-2023-34053| CVE | Medium | 5.3 | MEDIUM | 5.3 | 2023-11-28 | 2024-08-02 | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L | https://www.mend.io/vulnerability-database/CVE-2023-34053 | Spring Framework versions 6.0.0 - 6.0.13 may be vulnerable to denial-of-service attacks through s| GH_WebGoat | GH_WebGoat | Attack Vector: NETWORK, Attack Complexity: LOW,| spring-web-6.0.13.jar | Upgrade to version org.springframework:spring-web:6.0.14 | /home/wss-scanner/.m2/repository/org/springframework/spring-web/6.0.13/spring-web-6.0.13|Table Columns:
Name: CVE identifier.
Type: Type of issue.
Severity: Severity level of the finding (Critical, High, Medium, Low).
Score: CVSS v2 score.
CVSS3 Severity: CVSS v3 severity level (Critical, High, Medium, Low).
CVSS3 Score: CVSS v3 score.
Publish Date: Date the vulnerability was first disclosed.
Last Updated Date: Most recent update to the vulnerability information.
Score Metadata Vector: Detailed vector string that describes the vulnerability.
URL: URL link for the vulnerability details on Mend.io's vulnerability database.
Description: A short description of the vulnerability.
Project: Name of the project associated with the vulnerability.
Product: The application that contains the vulnerable dependency.
CVSS3 Attributes: Detailed CVSS v3 attributes such as attack vector, complexity, etc.
Library: Name and version of the affected library.
Top Fix: Recommended fix or upgrade for the vulnerability.
Locations: File path where the vulnerable library is located.
Fix Type (only available in Excel format): Indicates the source of the suggested remediation.
Blank - no suggested remediation exists for this finding.
“Mend” - the suggested remediation is provided by Mend.io
“Mend, HeroDevs” - a remediation suggestion by HeroDevs exists, on top of the one provided by Mend.io.
