Search Findings in your Organization
Overview
The Search Findings tool allows you to quickly locate and observe vulnerabilities in your Applications and Projects within your Organization. The search method you choose depends on whether you focus on a particular library or vulnerability.
Notes:
The Search Findings will show results of CVEs or library names of different Applications or Projects available in your organization on the Mend Platform. It will not provide detailed descriptions of all known CVEs or their impacts.
The Search Findings tool is available for Dependencies (SCA) and Containers.
Getting it done
There are two ways you can use the Search Findings tool:
Searching by a specific library name effectively identifies various CVE vulnerabilities associated with that library across different Applications or Projects.
Searching by the CVE identifier allows you to list different libraries affected by the same CVE across your Application or Projects.
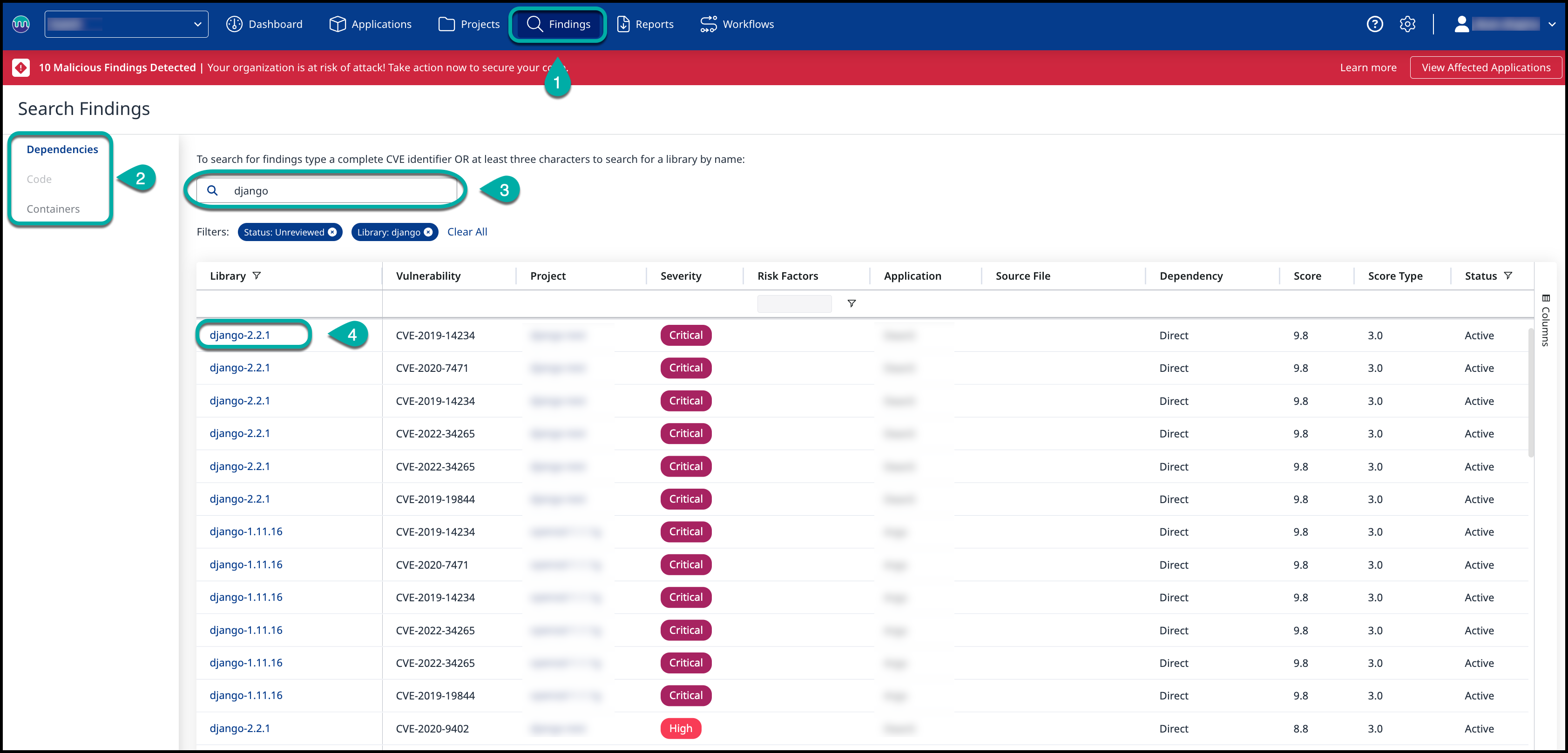
Search by Library Name
Click on the Findings tab within your Organization.
From the left menu pane, select the Scan Engine (Dependencies/Containers) you want to search for.
Enter at least three characters of the library name or full name to search for matching libraries in your inventory. Filters can be used to refine the results.
Click on the library name to open the Library Summary Page.
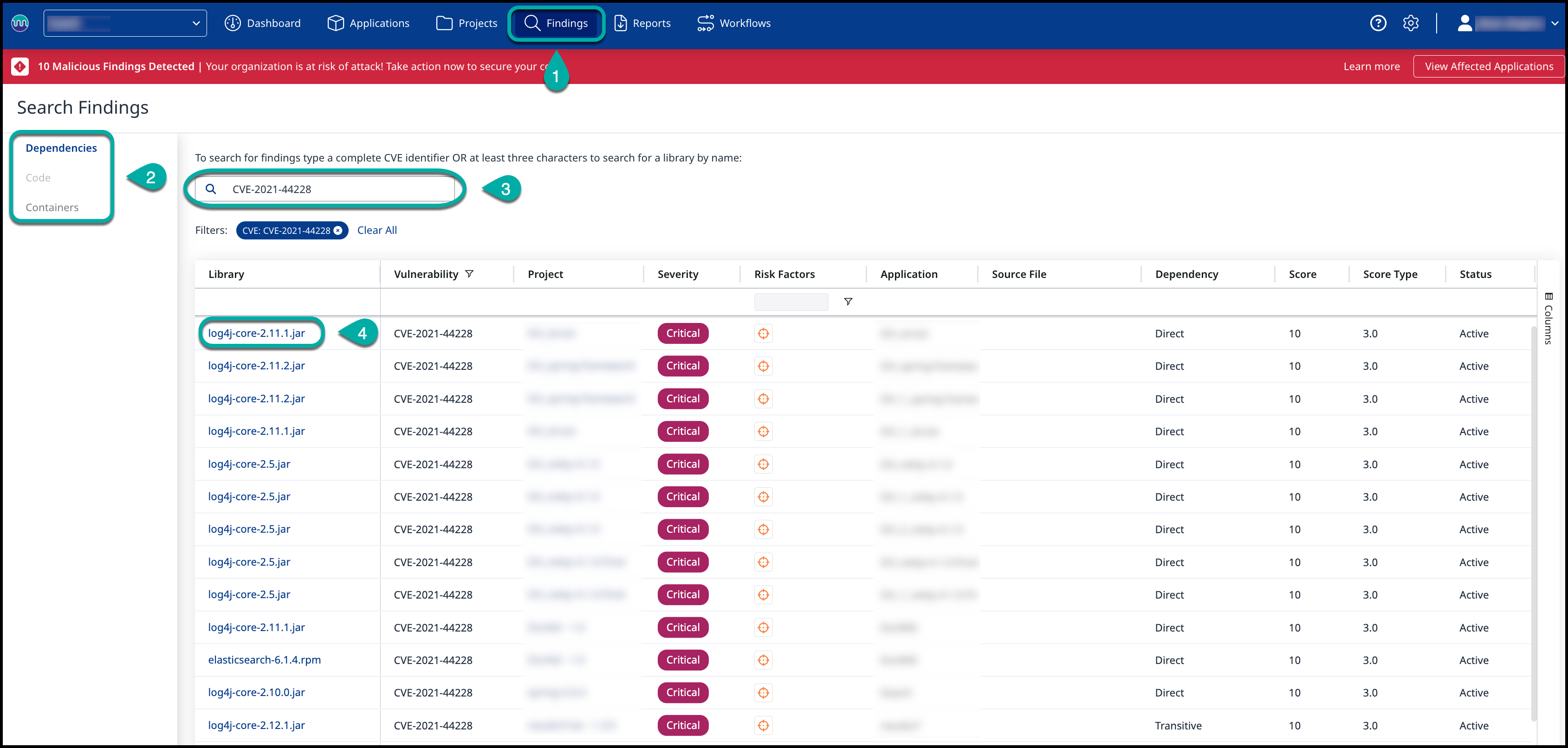
Search by CVE Identifier
Click on the Findings tab within your Organization.
From the left menu pane, select the Scan Engine (Dependencies/Containers) you want to search for.
Enter the CVE identifier to search your project for matching CVEs and the affected libraries in your inventory. Filters can be used to refine the results.
Click on the library name to open the Library Summary page.
The Library Summary Page
The Library Summary Page offers a comprehensive overview of vulnerabilities associated with a specific library, detailing their severity and identification. In this section, we will focus on the Vulnerabilities List, which details all identified vulnerabilities tied to the library.
Each Vulnerability entry includes:
Severity Rating: Vulnerabilities are categorized by severity (e.g.,
High, Medium, Low) to aid in prioritizing response efforts.CVE Identifier: Provides standardized references for each issue, facilitating access to detailed reports and mitigation strategies.
CVSS Scores: Each vulnerability is accompanied by a Common Vulnerability Scoring System (CVSS) score, quantifying its severity based on factors like exploitability and impact.
Publication and Modification Dates: Tags each entry with its publication and last modification dates, helping track the timeliness and relevance of the information.
Vulnerability Details: For selected vulnerabilities, detailed descriptions are offered, including how the vulnerability occurs, its potential impacts, and the resolution steps taken.
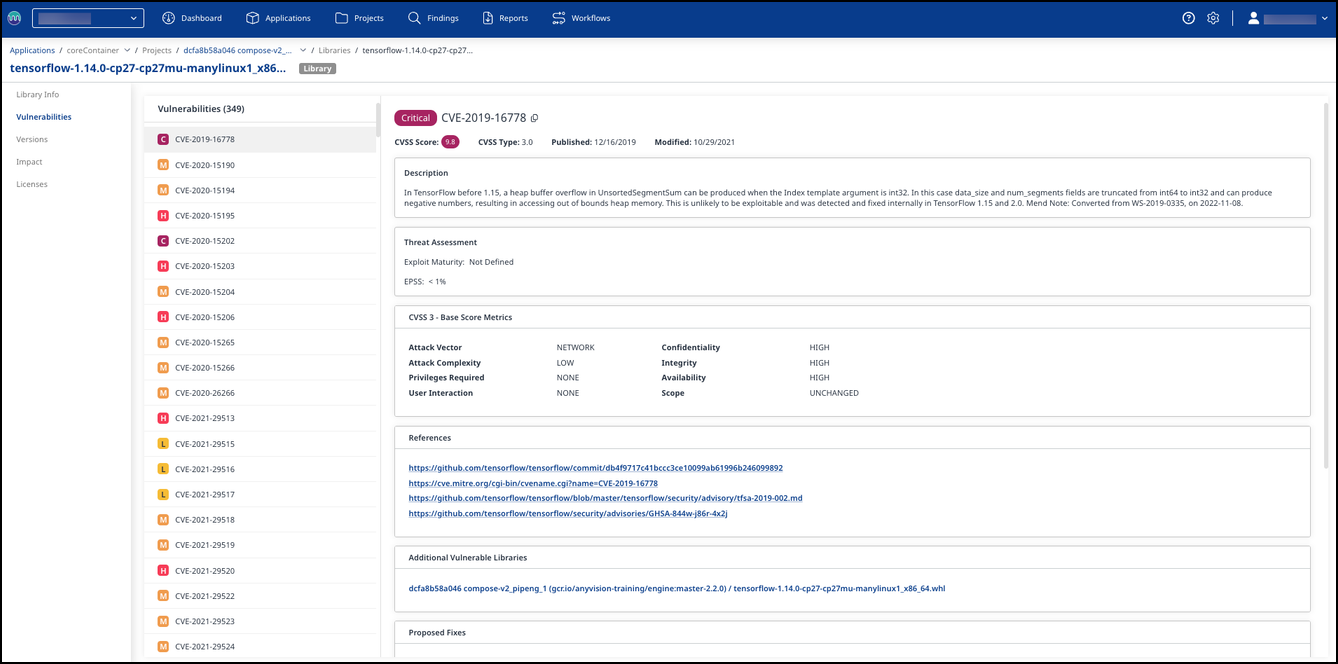
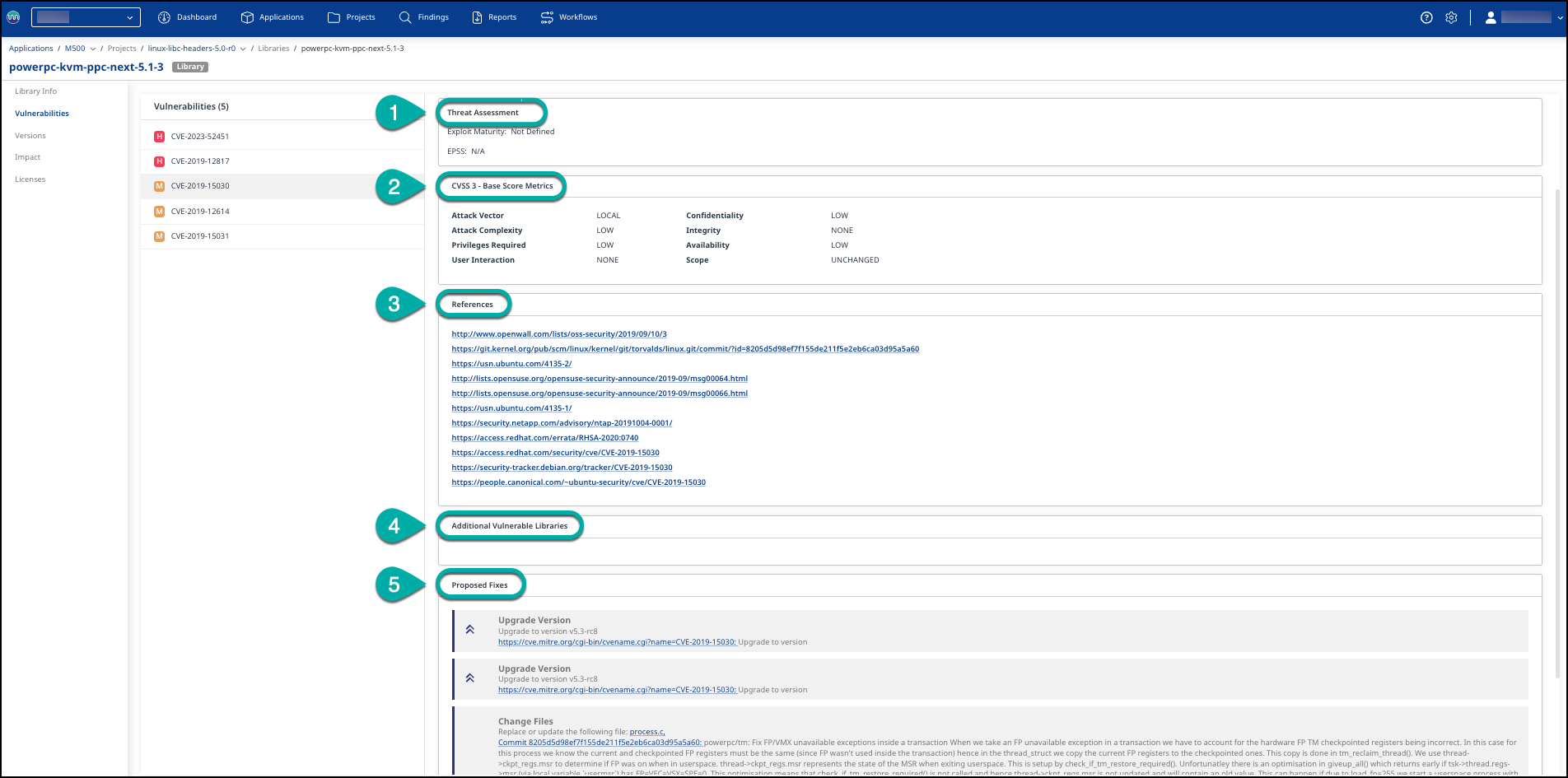
In subsequent sections, five additional areas provide a complete picture of this specific vulnerability.
These sections include:
Threat Assessment: Evaluate software vulnerabilities' risk and potential impact, providing a comprehensive overview of how threats could affect your systems. This section includes Exploit Maturity ranges and an EPSS (Exploit Prediction Scoring System) score.
CVSS 3 - Base Score Metrics: Provides a standardized method to capture the principal characteristics of a vulnerability and produce a numerical score reflecting its severity.
References: Offers links to more information about this vulnerability on git.kernel.org.
Additional Vulnerable Libraries: Lists other libraries in this project that share this vulnerability.
Proposed Fixes: Fixes available for the identified vulnerability.
Search Result Fields
The following table provides descriptions for each field displayed in your search results.
Search Result Fields | Description |
|---|---|
| The name of the library affected by the vulnerability Note: Clicking the name will link you to the Library page. |
| The identifier of the vulnerability in the affected Library |
| The Options here are: |
| The name of the project this vulnerability affects Note: Click the name will link you to the project summary page. |
| The Application containing the Library and vulnerability |
| In case you have a source file it will show up here |
| Indicates whether the library is a direct or a transitive dependency |
| CVSS Score: The CVSS score is a numerical value ranging from 0.0 to 10.0 that represents the severity of a vulnerability |
| CVSS Type: The CVSS type refers to the version of the CVSS standard being used |
| Indicates whether the vulnerability in the library is reachable within the code For more information on Reachability, please check out our SCA Reachability documentation. |
| Indicates the status of a vulnerability, which can be one of the following: Unreviewed, In Review, Issue Created, Remediated, or Suppressed For more information on Mend SCA statuses, please check out our Mend SCA statuses documentation. |
| Comments on CVE / library |
| The Admin/user who submitted the last modification |
| The date of the last modification |
| The date when this vulnerability was first detected |
| What integration is currently active with this library |
| Date when the vulnerability was published |
| The internal tracking security ID for organizational tracking |
Export your Findings
As a security or compliance user, you may want the ability to export the vulnerability/library search results from the “Findings” page, for further analysis, sharing with stakeholders, or storing for auditing purposes.
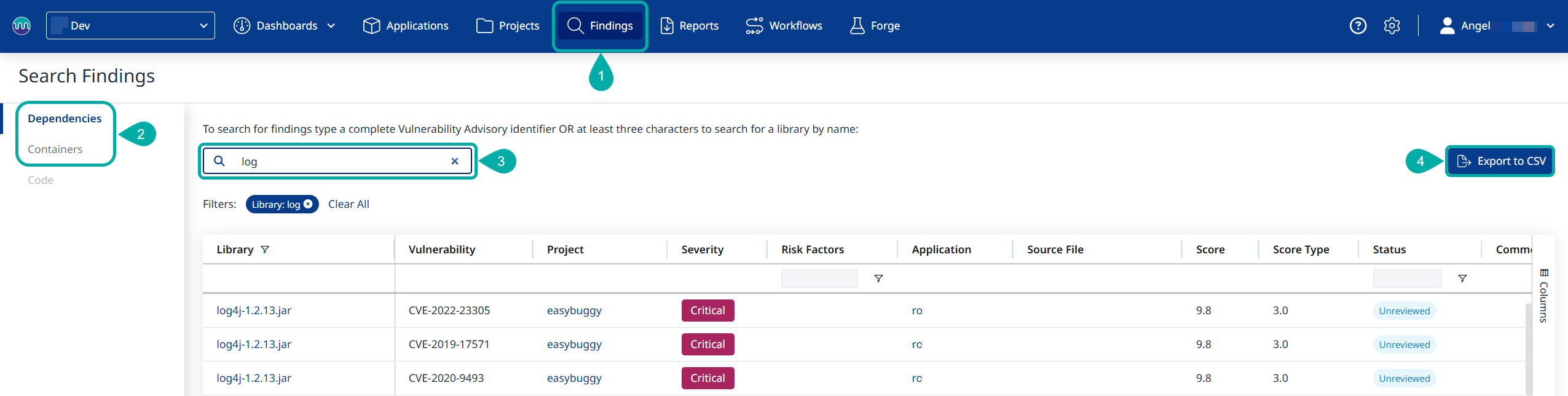
To download the findings, follow these steps:
Navigate to the Findings page.
Select your engine of choice: Dependencies (SCA) or Containers.
Define the search parameters:
For findings - type a complete Vulnerability Advisory identifier (e.g., “CVE-2021-44228”).
For libraries - specify at least 3 characters of the library name (e.g., “log” for log4j libraries).
Export the table by clicking the Export to CSV button on the right.
Note: The export includes all results that match the search parameters, not just those visible on the current page. The number of entries is indicated at the bottom of the table.
Example:

