Code Secret Scanning
Overview
Mend SAST Secret Scanning provides a comprehensive security overview, by introducing the capability to:
1) Scan both source code and configuration files to detect exposed credentials, based on patterns.
2) View the results alongside standard SAST results.
Configuration Files
Below is a list of some of the more prominent configuration files scanned for exposed credentials.
JSON
XML
.properties
.yaml
.config
For the full list, visit the Code Secrets Appendix.
Getting it done
Secret Scanning as part of a Regular SAST Scan
To add secret detection to your regular SAST scan, enable the --secrets-detection command line parameter in addition to the regular mend code command in the Mend CLI.
When unspecified, secret scanning as part of your SAST scan is disabled.
Note: This mode is also supported in the Developer Platform and Mend for GitHub.com.
Here’s what a SAST scan with secrets detection enabled would look like in the terminal:
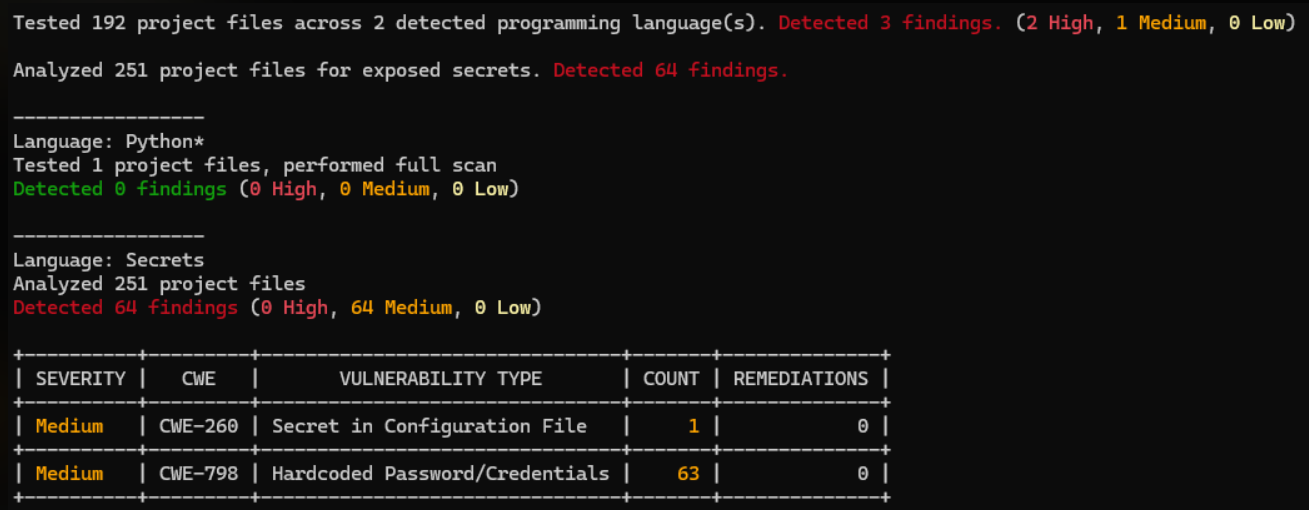
Example of Mend CLI SAST Scan with Secrets Detection
Viewing Results
The results of the secret scanning will appear in the platform UI alongside other Code findings.
They will be differentiated from other code findings by the value “Secrets” in the Language column.
Noteworthy values of secret scanning findings:
CWE Name - 2 possible values:
A. Hardcoded Password/Credentials (CWE-798)
B. Secret in Configuration File (CWE-260)
Severity - Always Medium.
Sink - The type of secret detected, e.g., Postman API Token, AWS Access Key ID, etc.
Language - “Secrets”.
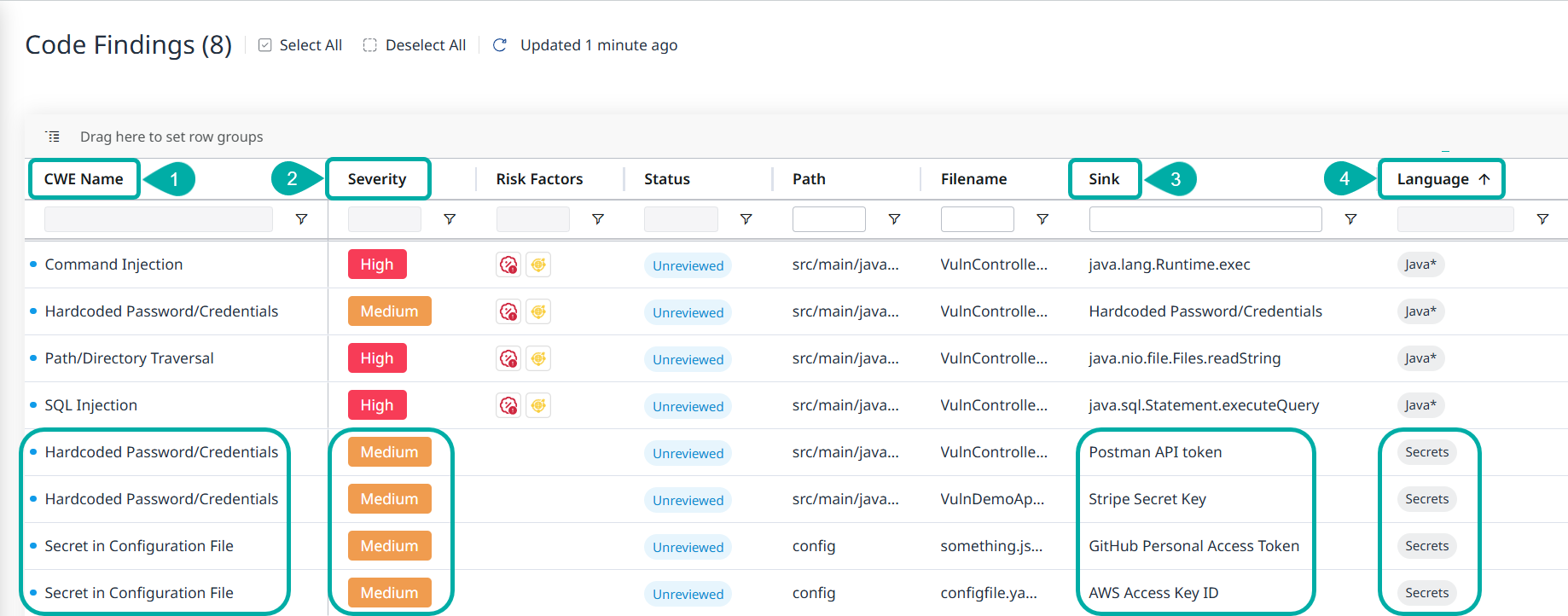
Clicking anywhere on a row of a detected secret will spawn a drawer with more in-depth information about the secret:
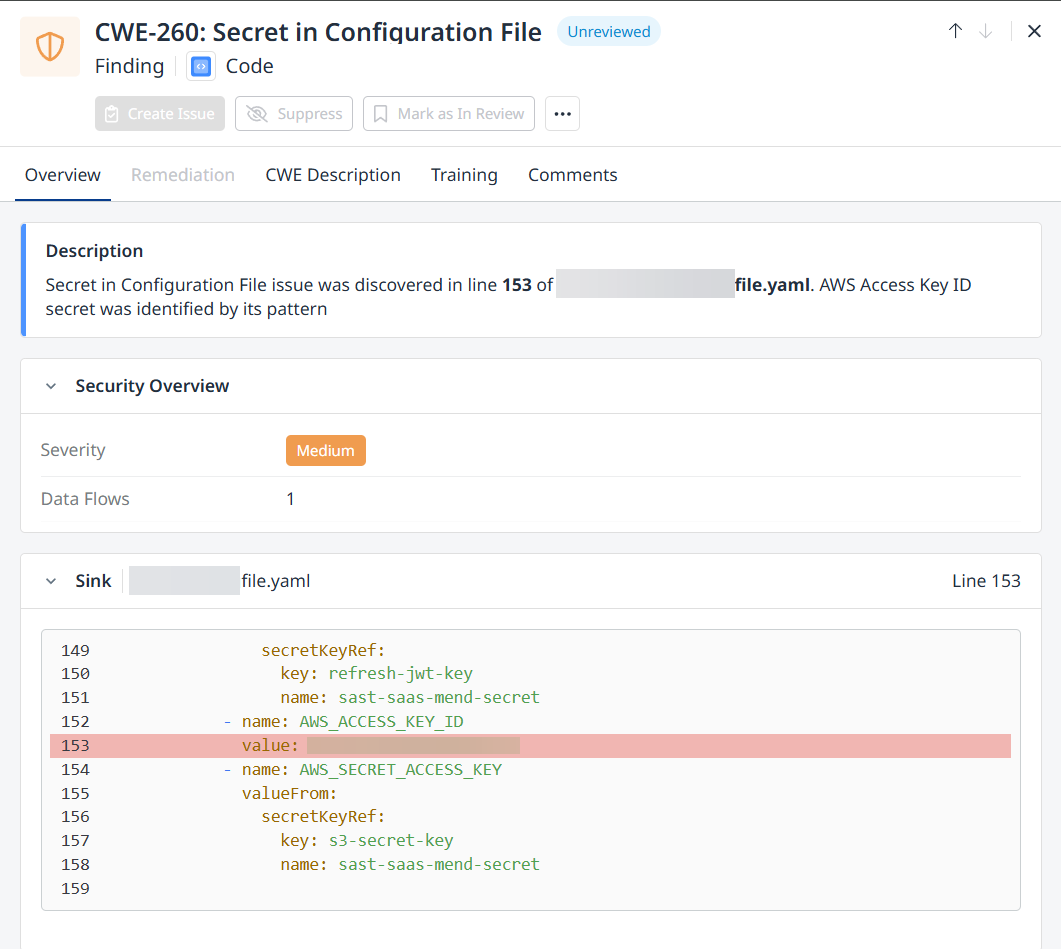
Note:
All secret findings are labelled as ‘Medium’ severity.
Mend.io does not anonymize detected secrets.
Automation Workflows around Secret Detection
You can create Automation Workflows around secret detection to trigger policy violations and fail builds, in a similar fashion to every other Code finding.
Visit the Automation Workflows documentation for more details.
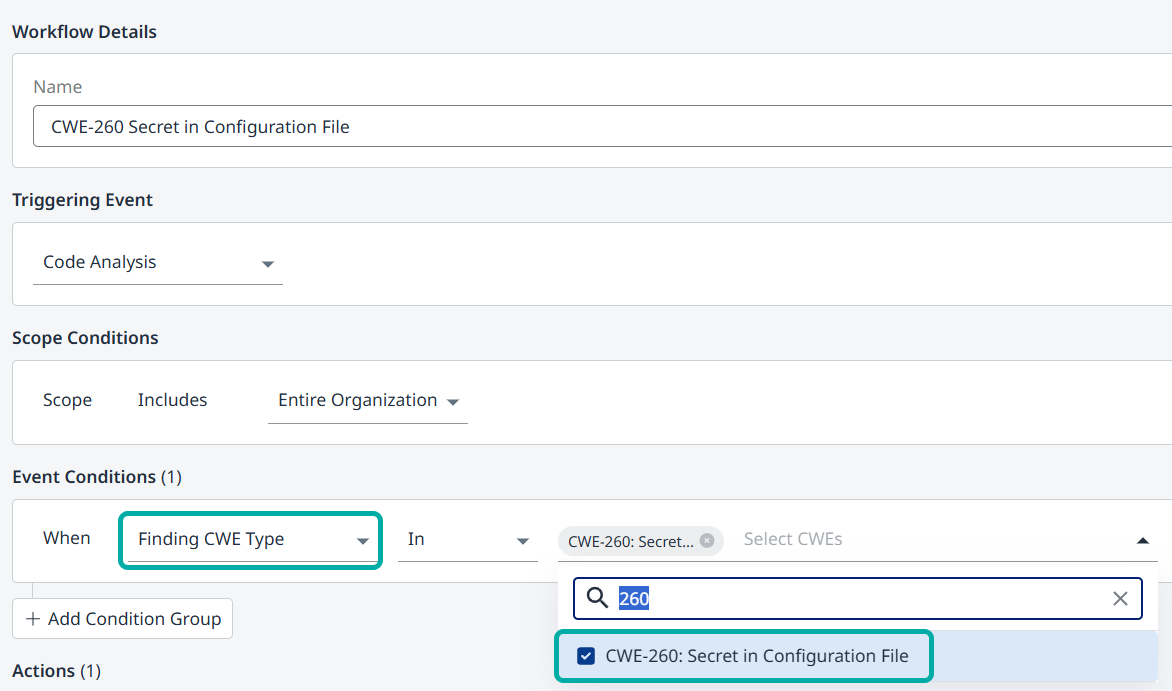
Example - Automation Workflow Triggered by Detection of CWE-260: Secret in Configuration File
