Viewing Mend Prioritize Scan Results via Dashboard
Overview
When Mend Prioritize (Effective Usage Analysis) is enabled, various screens, components, and reports in the Mend application are enhanced with additional information about security vulnerabilities.
This page describes this functionality.
For customers with Security Alerts: View By Vulnerability enabled, note that gray shields will not be displayed, as they indicate libraries, not vulnerabilities.
Home, Product and Project Screens
With Mend Prioritize, the Home, Product and Project main screens display vulnerabilities effectiveness-related information in the Vulnerability Analysis pane.
In addition, Security vulnerability displays (e.g., Home screen, Security Vulnerabilities screen) feature effectiveness indicators ('shields') for components analyzed with Mend Prioritize. For more information regarding the Vulnerability Analysis Pane, click here.
WhiteSource Prioritize Indicators
Prioritize Effectiveness Indicators
Effectiveness Indicator |  Red Shield |  Yellow Shield |  Green Shield |  Gray Shield | No shield |
For a security vulnerability listed in the Security Vulnerabilities screen | The security vulnerability was confirmed by Effective Usage Analysis to have at least one reference from proprietary code (directly or indirectly) |
| The security vulnerability was confirmed by Effective Usage Analysis to have no effective references from proprietary code | [N/A – this view does not feature the gray shield] |
|
For a component listed in the Top Alerts table under Project | At least one of the security vulnerabilities reported for the component was confirmed by Effective Usage Analysis to have at least one reference from proprietary code (directly or indirectly) |
| Each of the security vulnerabilities reported for the component was marked with a green shield | Vulnerability related information changed for the pertinent library after the library was analyzed by Effective Usage Analysis (e.g., a new vulnerability was reported) | The library was not analyzed with Prioritize.
|
For a component listed in the Top Alerts table under Product or Organization | At least one of the underlying Project-level alerts for the library was marked by analysis with a red shield | At least one of the underlying Project-level alerts for the library was marked by analysis with a yellow shield and none with a red shield | All underlying Project level alerts for the library were marked by analysis with a green shield | At least one of the underlying Project-level alerts for the library was marked by analysis with a gray shield, and none with a red or yellow shield | At least one of the underlying Project level alerts for the library is featured by a Project that was not analyzed with Prioritize and analyzed Projects are not marked with a red, yellow or gray shield |
General | A red shield denotes an ‘effective’ finding | A yellow shield denotes a ‘suspected’ finding | A green shield denotes an ‘ineffective’ finding | A gray shield denotes an ‘outdated’ status finding | A ‘blank’ shield (i.e., no shield) denotes an element that was not analyzed |
Prioritize Severity Indicators
Security Vulnerability views feature enhanced severity details for components analyzed with Mend Prioritize. This is displayed in a number provided in parentheses (x) next to the existing severity provided for a given vulnerability severity class (e.g., High, Medium, Low) like in the following screenshot:
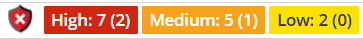
Severity: x (0): Effective Usage Analysis confirmed that the analyzed proprietary code scope (e.g., Project) has 0 references to all (x) vulnerabilities reported for the open-source component (i.e., green shield).
Severity: x (y) [note: 0<y<=x]: Effective Usage Analysis found that the analyzed proprietary code scope has references to some or all (y) of the vulnerabilities (x) reported for the open-source component (i.e., red shield).
Severity: x (x): Effective Usage Analysis found that the analyzed proprietary code scope has references to all vulnerabilities (x) reported for the open-source component (i.e., red shield)
Severity: x (z?): Effective Usage Analysis found that the analyzed proprietary code scope has references to some (z) of the reported vulnerabilities (x), but could not fully establish whether there are references to some of the security vulnerabilities reported for the open-source component (i.e., red shield).
Severity: x (z…?): Effective Usage Analysis found that the analyzed proprietary code scope has references to some (z) of the reported vulnerabilities (x), and while it could not fully establish references to some of the security vulnerabilities reported for the open-source component (i.e., red shield) class-level call traces were found.
Mend Prioritize Details in the Vulnerability Analysis Pane
With Mend Prioritize, the Vulnerability Pane charts depict Mend Prioritize results. The charts visualize the distribution of analysis results and enable users to establish how many of the reported vulnerabilities were confirmed by WhiteSource Prioritize to be effectively referenced from proprietary code.
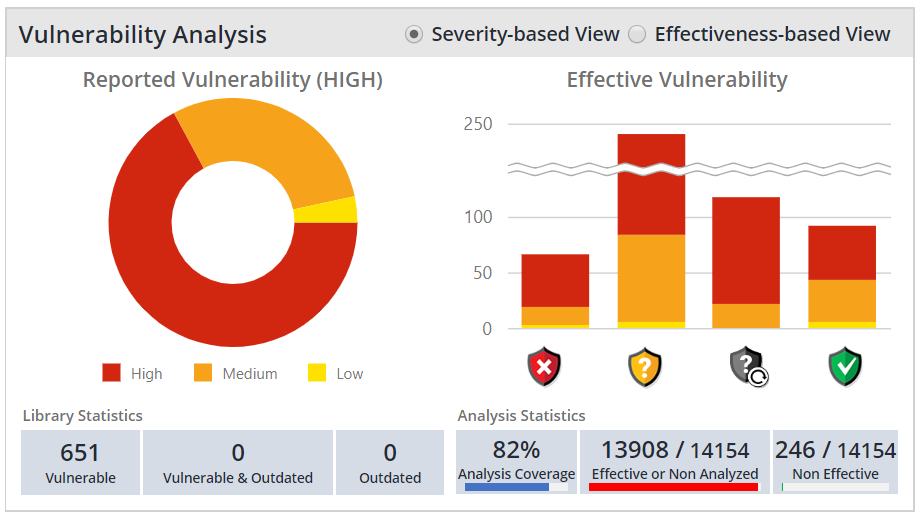
Reported Vulnerability: the distribution of libraries based on their highest vulnerability severity. Consequently, a library that has multiple severities will only be counted once – and for its highest severity
Library Statistics: the number of vulnerable libraries that are outdated, vulnerable, or both
Vulnerable Libraries - the distribution of libraries based on their highest vulnerability severity.
Outdated Libraries – the number of libraries that are outdated.
Severity-based View - Vulnerability Effectiveness: the distribution of security alerts marked with a red, yellow, gray or green shield, accounting for reported vulnerability severity. The vulnerabilities with a reported severity are marked using the same colors denoting the severity on the Reported Library Vulnerability chart.
Effectiveness-based View - Vulnerability Effectiveness: the distribution of security alerts marked with a red, yellow, gray or green shield.
Analysis coverage: the % of analyzed libraries (excluding libraries marked with a gray shield) from the total count of libraries that can be analyzed. The analysis coverage represents the extent Effective Usage Analysis was applied in a given scope (Organization, Product or Project). The coverage is calculated based on the following formula A = B/C where:
A | Calculated Analysis Coverage: the calculated result for analysis coverage in the pertinent scope (Organization, Product or Project) |
B | Number of library-project 'instances' IN SCOPE that were analyzed by Effective Usage Analysis and are current (i.e., not outdated): library-project 'instances' with green, red or yellow shields - but without gray shields |
C | Maximum number of library-project 'instances' in scope that can be analyzed by Effective Usage Analysis: number of all library-project 'instances' in the scope that can be analyzed by Effective Usage Analysis |
A library-project instance denotes a case where a given library is featured in each project. If a given library is featured in 3 different projects, this translates into 3 library-project instances.
Another way to see this is that 3 Effective Usage Analysis processes are required to analyze the projects, regardless of the same library being employed.
Overall Effective Vulnerability Index: reflects the portion of security alerts that are not marked with a green shield (i.e., alerts marked with red, yellow or gray shields, and alerts not marked with a shield). Note that the value reflects a measure of effective vulnerability regarding all projects – i.e., those supported by Prioritize (e.g., Java) and those that are not. The Overall Effective Vulnerability Index allows users to establish the portion of alerts found to be ‘effective’, i.e., alerts that imply direct OR indirect calls from proprietary code to open source software with reported vulnerabilities; such alerts arguably warrant higher priority over alerts that are ‘non-effective’ (marked with a green shield). The index also serves as a measure of the savings potentially realized by attending highly-prioritized alerts.
Mend Prioritize – Detailed Analysis Screen
With Mend Prioritize, the system enhances the regular display of information for security vulnerabilities reported for an open-source component with extended, richer detail.
If an open-source component is analyzed with Mend Prioritize, the detailed view of the component's reported security vulnerabilities (accessed by clicking on the associated Details link in the Alerts report) will feature the following areas:
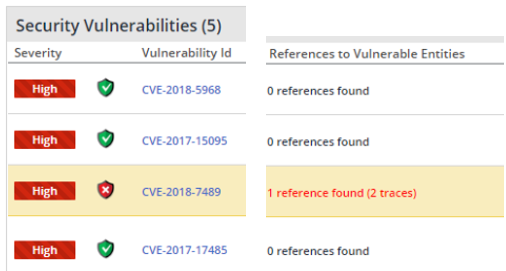
Security Vulnerability Table - In this table, the References to Vulnerable Entities column details (per a selected vulnerability) the number of references and code traces that Mend Prioritize found to exist from proprietary code to component code associated with the pertinent vulnerability. Additionally, a corresponding shield will be placed next to the vulnerability ID and the references details will be displayed in the Found References view beneath this table.
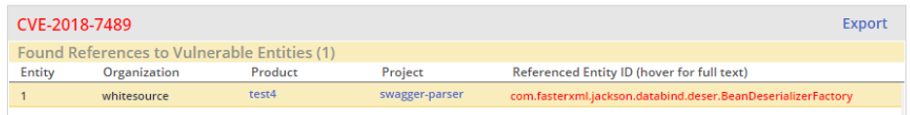
Found Reference View - This view lists references found by Mend Prioritize to exist from proprietary code to open source code for a given security vulnerability selected in the Security Vulnerabilities table. Per each reference the following details will be displayed in independent rows: Organization, Product and Project related to the relevant proprietary code, and the identifier and type of the referenced open-source code featuring the reported vulnerability.
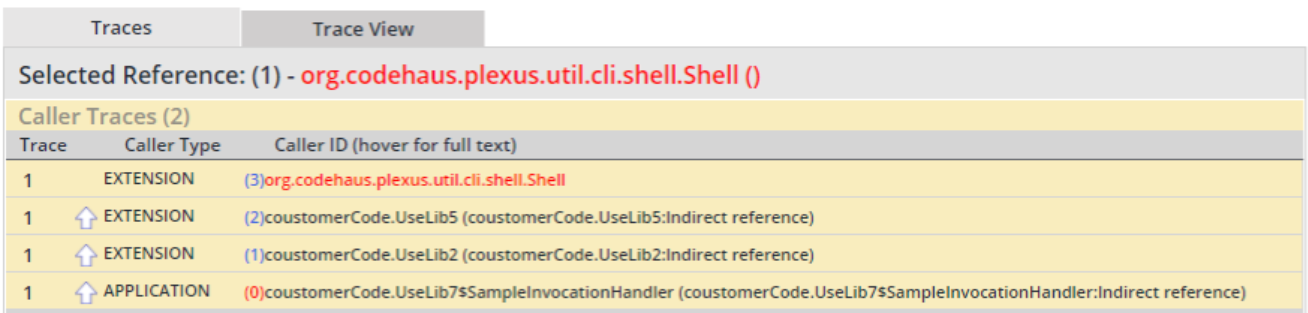
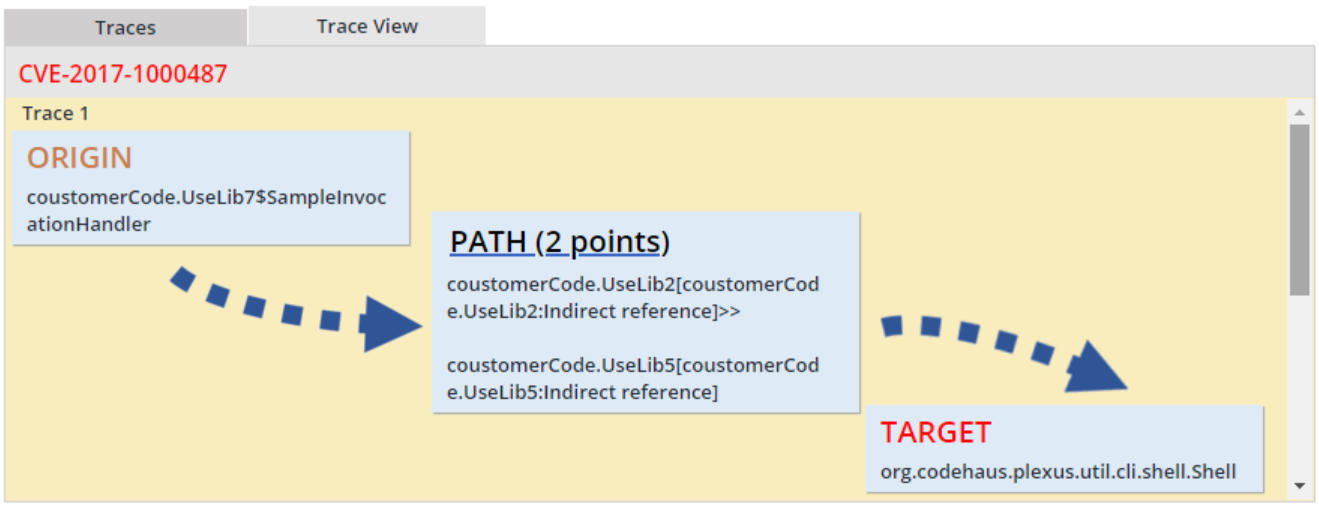
Traces View - This tabbed view lists call traces pertaining to a reference selected in the Found Reference view next to it. The Traces view lists per each reference two elements at minimum – an Origin (proprietary code whence the call trace originated) and a Target (open source code associated with the reported vulnerability). If the Target is not called directly by the Origin, then additional calls will be featured in the Traces view, as warranted. If multiple traces were found, all traces will be featured in the Traces table and can be reviewed by scrolling the view. The table featured in the Traces view provides for each found trace call the following details: trace number; an arrow denoting the code called by the code in a given trace row; the caller type (APPLICATION - the proprietary code) or EXTENSION (the non-proprietary code)); and the caller identifier along with the file name and code line number. The user can elect to display a graphical view of the call trace by selecting the Trace View tab. The display presents the call trace from the Origin to the Target through a path consisting of any interim steps. The user may expand or collapse the displayed path by clicking on it.
Security Vulnerabilities Table
Security vulnerabilities view with Mend Prioritize – security vulnerabilities table
Found References View
The Found References view serves as the 'parent' of the Traces view (see below), with the entries listed by the latter corresponding with a selected entry in the Found References table.
Security vulnerabilities view with Mend Prioritize – Found references table (references found)
Traces view
Security vulnerabilities view with Mend Prioritize – Traces table (traces found)
Automated Policies
It is possible to use Prioritize shields as match options in automated policies. See also Automated Policies documentation.
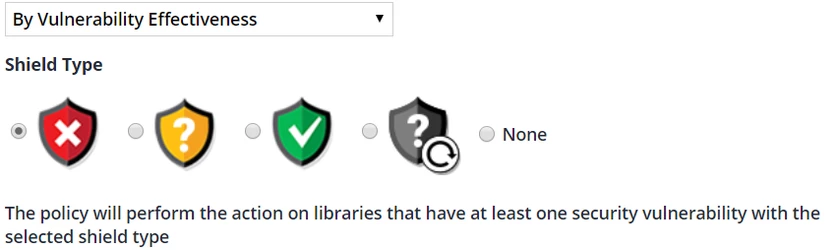
Adding a policy by Shield type.

Adding a Policy by Security Vulnerability Severity AND Vulnerability Effectiveness.
