Mend Prioritize Reports
Overview
IMPORTANT
For customers with Security Alerts: View By Vulnerability enabled, note that gray shields will not be displayed, as they indicate libraries, not vulnerabilities.
Reports detailing Effective Usage Analysis findings can be produced by selecting an option from the Found References view featured in the Security Vulnerabilities screen (figure 34), or by selecting a related report option (e.g., Alerts) from the Reports menu (figure 32).
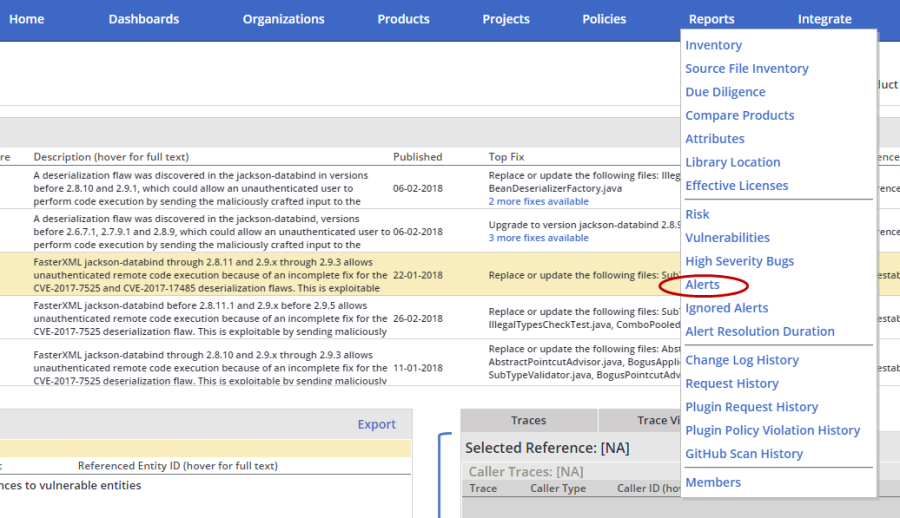
Figure 32: The Reports menu features options to publish Effective Usage Analysis detailed analysis results
The Alerts Report for Effective Usage Analysis
The Alerts report features the following detail:
Creation Time: the time the alert was created
Level: The level code of the alert
Type: the type of alert
Library: the name of the library for which an alert was created
Description: the description of the reported alert
Details: the vulnerabilities reported for the library in the alert
Product: the name of the Product
Project: the name of the Project
Impact Analysis Status (see figure 33 [4]): the status reported for a library processed by Effective Usage Analysis. Valid options include:
1. Done (i.e., green or red shields; condition: Effective Usage Analysis completed successfully on all library reported vulnerabilities (i.e., returned for each vulnerability confirmed 0 or more traces))
2. Partial or Unavailable Data (i.e., yellow shield; condition: Effective Usage Analysis did not complete successfully on one or more library reported vulnerabilities (e.g., was unable to run analysis due to missing vulnerability data))
3. Potentially Outdated (i.e., gray shield; condition: a new vulnerability was found for a library for which Effective Usage Analysis results are available)
4. [Empty] (i.e., no shields; condition: Effective Usage Analysis was not applied to analyze the library)
Impact Analysis Results (see figure 33 [4]): the summary results reported for a library processed by Effective Usage Analysis. Valid options include:
1. [Empty] (condition: 'Impact Analysis Status = [Empty]' or 'Impact Analysis Status = Partial or Unavailable Data')
2. 'High(x?)' (condition: Effective Usage Analysis found effective references to x vulnerabilities reported as High; if analysis results are unclear or incomplete – a '?' should be noted)
3. 'Medium(y?)' (condition: Effective Usage Analysis found effective references to y vulnerabilities reported as Medium; if analysis results are unclear or incomplete – a '?' should be noted)
4. 'Low(z?)' (condition: Effective Usage Analysis found effective references to z vulnerabilities reported as Low; if analysis results are unclear or incomplete – a '?' should be noted)
NOTE: If Effective Usage Analysis is applied on a library reported to have multiple vulnerabilities, then the valid value will be a comma-delimited list of multiple values
Examples for the reported Impact Analysis Status and Impact Analysis Result detail in the exported XLS format:
Example use case Let's assume a library has 2 reported Medium vulnerabilities - CVE-2016-5007 and CVE-2016-9879
Example 1 (red shield):
If Effective Usage Analysis found effective references to both reported vulnerabilities, then the Impact Analysis Status will be: 'Done' and the Impact Analysis Results will be: Medium(2)
Example 1a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: 'Potentially Outdated' and the Impact Analysis Results will be: Medium(2)
Example 2 (red shield):
If Effective Usage Analysis found effective references to one of the reported vulnerabilities and none to the other, then the Impact Analysis Status will be: 'Done' and the Impact Analysis Results will be: Medium(1)
Example 2a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: 'Potentially Outdated' and the Impact Analysis Results will be: Medium(1)
Example 3 (green shield):
If Effective Usage Analysis found effective references to none of them, then the Impact Analysis Status will be: 'Done' and the Impact Analysis Results will be: Medium(0)
Example 3a (gray shield with a symbol):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: 'Potentially Outdated' and the Impact Analysis Results will be: Medium(0)
Example 4 (red shield):
If Effective Usage Analysis was unable to complete analysis on one of the reported vulnerabilities (e.g., due to missing vulnerability data), yet was able to run on the other and found an effective reference, then the Impact Analysis Status will be: 'Partial or Unavailable Data', and the Impact Analysis Results will be: Medium(1?)
Example 4a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: 'Potentially Outdated' and the Impact Analysis Results will be: Medium(1?)
Example 5 (yellow shield):
If Effective Usage Analysis was unable to complete the analysis of both 2 vulnerabilities, then Impact Analysis Status will be: 'Partial or Unavailable Data', and Impact Analysis Results will be: [Empty]
Example 5a (gray shield with '?' symbol):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: 'Potentially Outdated' and the Impact Analysis Results will be: [Partial or Unavailable Data]
Example 6:
If Effective Usage Analysis was not run on any of the 2 vulnerabilities, then Impact Analysis Status will be: [Empty], and Impact Analysis Results will be: [Empty]
Example 6a ([Empty]):
If a new library vulnerability was found after the result above, then the Impact Analysis Status will be: [Empty] and the Impact Analysis Results will be: [Empty]

Figure 33: The Alerts report enables the user to export a high-level summary of Effective Usage Analysis results for each examined project (columns Impact Analysis Status and Impact Analysis Results)
Export Options for Effective Usage Analysis
The system enables the user to obtain printout variations of Effective Usage Analysis detail on a given alert through (1) the export option on the Alerts Report (including analyzed vulnerability severity, figure 33 [1]), (2) the Library Security Vulnerabilities screen (including general vulnerability info and detail on detected traces, figure 36 [1]), and (3) the Trace pane on the Library Security Vulnerabilities screen (detail on detected traces, figure 39 [1])
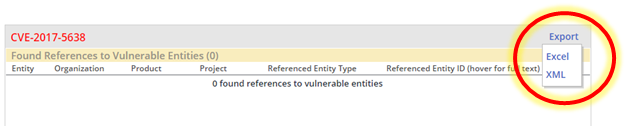
Figure 34: The Found References View features an option to export Effective Usage Analysis detailed analysis results as an Excel based or XML-based report
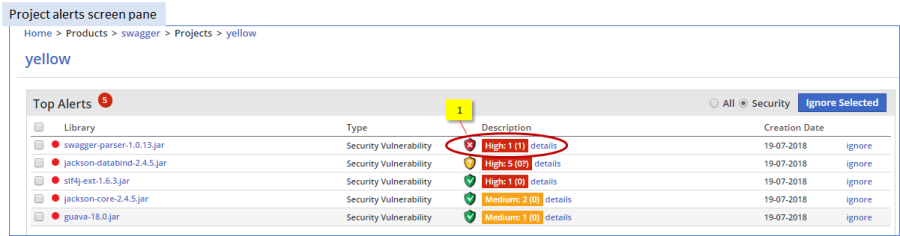
Figure 35: The system enables the user to obtain printout variations of Effective Usage Analysis detail on a given alert (see above [1]) through (1) the export option on the Alerts Report (including analyzed vulnerability severity, figure 33 [1]), (2) the Library Security Vulnerabilities screen (including general vulnerability info and detail on detected traces, figure 36 [1]), and (3) the Trace pane on the Library Security Vulnerabilities screen (detail on detected traces, figure 39 [1]) 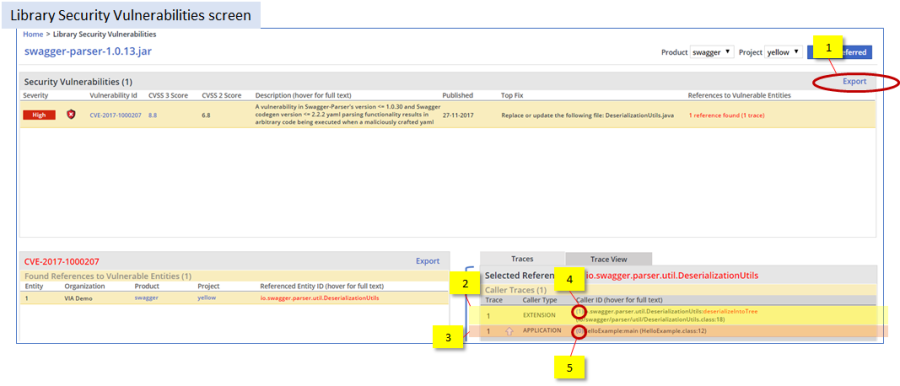
Figure 36: The Library Security Vulnerabilities screen enables the user to export [1] analysis findings on listed vulnerabilities in XML or XLS format. The figure highlights two trace elements: [3][5] the APPLICATION element starting the trace and [2][4] the EXTENSION
The exported report features general detail on each vulnerability listed, including specific detail on Effective Usage Analysis trace findings:
Entity #: an ID assigned to an entity with a reported vulnerability that is referenced (directly or indirectly) from proprietary code
The Entity # field features detail corresponding with analysis results, as follows:
Red-shielded vulnerability: a non-zero value (reflecting a found referenced ID, which is only relevant to red shields)
Green-shielded vulnerability: 'None'
Yellow-shielded vulnerability: 'Partial or Unavailable Data'
None-shielded vulnerability (a newly detected vulnerability (for the analyzed library) that was not processed by Effective Usage Analysis: [ Empty ]
Organization: name of the Organization featuring the analyzed Project
Product: name of the Product featuring the analyzed Project
Project: name of the analyzed Project featuring the library instance
Referenced Entity ID: the name of an entity with a reported vulnerability that is referenced (directly or indirectly) from proprietary code
Trace #: an ID assigned to the trace (there can be multiple traces for a found Referenced Entity)
Call Order: the ordinal sequence number of the trace element (0 is the originating call)
Caller Type: type of caller (APPLICATION (name of the jar file with proprietary code) or EXTENSION (name of jar file with the non-proprietary code))
Caller ID: the file, class and line number where a call originated
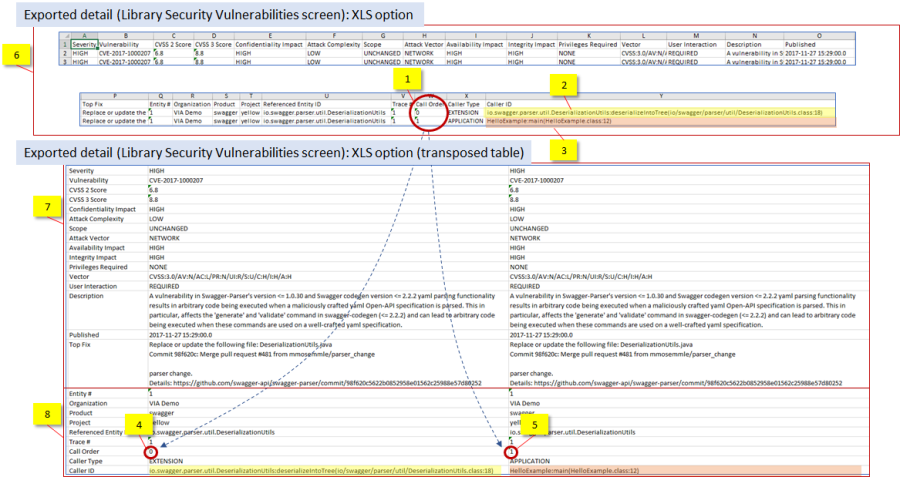
Figure 37: An example of the analysis detail exported (as XLS) from the Library Security Vulnerabilities screen: the top area [6] displays the details featured in the exported file (including the trace elements featured in the UI screen (figure 34, [2][3]), whereas the bottom part [7][8] displays (and highlights) the same detail after being transposed
Examples for the reported Impact Analysis Status and Impact Analysis Result detail in the exported XML format:
Example 1 (red shield):
If Effective Usage Analysis found effective references to both of them, then the output would be: <Impact Analysis Status>Done</Impact Analysis Status><Impact Analysis Results>Medium(2)</Impact Analysis Results>
Example 1a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status>Potentially Outdated</Impact Analysis Status><Impact Analysis Results>Medium(2)</Impact Analysis Results>
Example 2 (red shield):
If Effective Usage Analysis found effective references to one of them and none to the other, then the output would be: <Impact Analysis Status>Done</Impact Analysis Status><Impact Analysis Results>Medium(1)</Impact Analysis Results>
Example 2a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status> Potentially Outdated</Impact Analysis Status><Impact Analysis Results>Medium(1)</Impact Analysis Results>
Example 3 (green shield):
If Effective Usage Analysis found effective references to none of them, then then the output would be: <Impact Analysis Status>Done</Impact Analysis Status><Impact Analysis Results>Medium(0)</Impact Analysis Results>
Example 3a (gray shield with 'v' symbol):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status>Potentially Outdated</Impact Analysis Status><Impact Analysis Results>Medium(0)</IImpact Analysis Results>
Example 4 (red shield):
If Effective Usage Analysis was unable to run analysis on one of the reported vulnerabilities (yet was able to run on the other and found an effective reference), then the output would be: <Impact Analysis Status>Partial or Unavailable Data</Impact Analysis Status><Impact Analysis Results>Medium(1?)</Impact Analysis Results>
Example 4a (gray shield with 'x' symbol):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status>Potentially Outdated</Impact Analysis Status><Impact Analysis Results>Medium(1?)</Impact Analysis Results>
Example 5 (yellow shield):
If Effective Usage Analysis was unable to run analysis on both 2 vulnerabilities, then the output would be: <Impact Analysis Status>Partial or Unavailable Data</Impact Analysis Status><Impact Analysis Results></Impact Analysis Results>
Example 5a (gray shield with '?' symbol):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status>Potentially Outdated</Impact Analysis Status><Impact Analysis Results>Partial or Unavailable Data</IA Results>
Example 6:
If Effective Usage Analysis was not run on any of the 2 vulnerabilities, then Impact Analysis Status will be: <Impact Analysis Status></Impact Analysis Status><Impact Analysis Results></Impact Analysis Results>
Example 6a ([Empty]):
If a new library vulnerability was found after the result above, then the output will be: <Impact Analysis Status> </Impact Analysis Status><Impact Analysis Results></Impact Analysis Results>
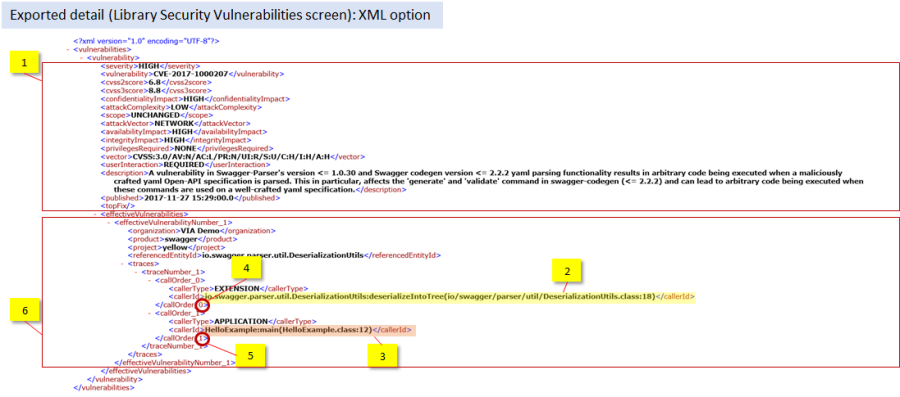
Figure 38: An example of the analysis detail exported (as XML) from the Library Security Vulnerabilities screen: the top area [1] displays general vulnerability details, whereas the bottom part [6] displays (and highlights) the trace elements highlighted in figure 34 [2][3]

Figure 39: An excerpt of an exported XLS file featuring detail on traces using the Export option on the lower Trace pane in the Library Security Vulnerabilities screen. This option enables the user to restrict the exported detail to found traces ([2][3]). The bottom part of the figure displays an excerpt of the detail featured in the exported XLS format.
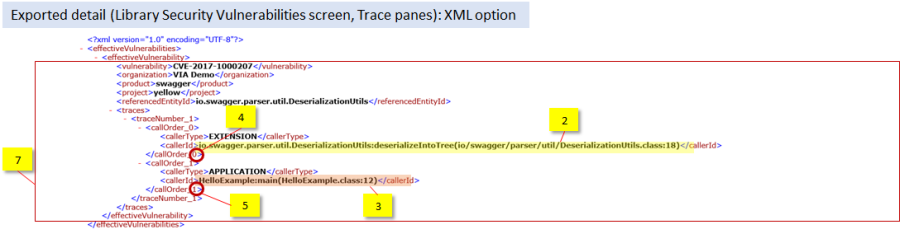
Figure 40: An excerpt of an exported XML file featuring detail on traces found by Effective Usage Analysis, including highlighted aspects of such traces ([2][3][4][5])

Figure 39: Comparison of the XML detail featured in the file exported using the 2 Export options in the Library Security Vulnerabilities screen: the vulnerability-level (top) and the trace-level. The figure shows that the trace-level Export option produces essentially a subset of the detail provided via the Vulnerability-level Export option
The Vulnerabilities Report for Effective Usage Analysis
The Vulnerabilities report features the following detail:
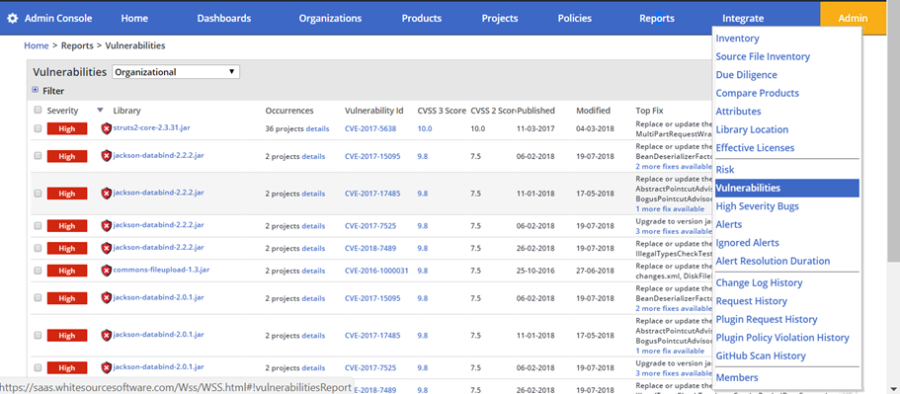
Figure 40: The Vulnerabilities report enables the user to export a summary of security vulnerability attributes for library alerts along Effective Usage Analysis results (columns Impact Analysis Status and Impact Analysis Results)
Effective Usage Analysis Summary and Detailed Report
Refer here for details.
