Scan Details
Note: The legacy Mend SAST application was deprecated on April 1st, 2025. For assistance with migrating to the Mend AppSec Platform, please contact your customer success manager or the success team at success@mend.io.
Overview
The scan Details tab displays an in-depth table of findings from a scan:
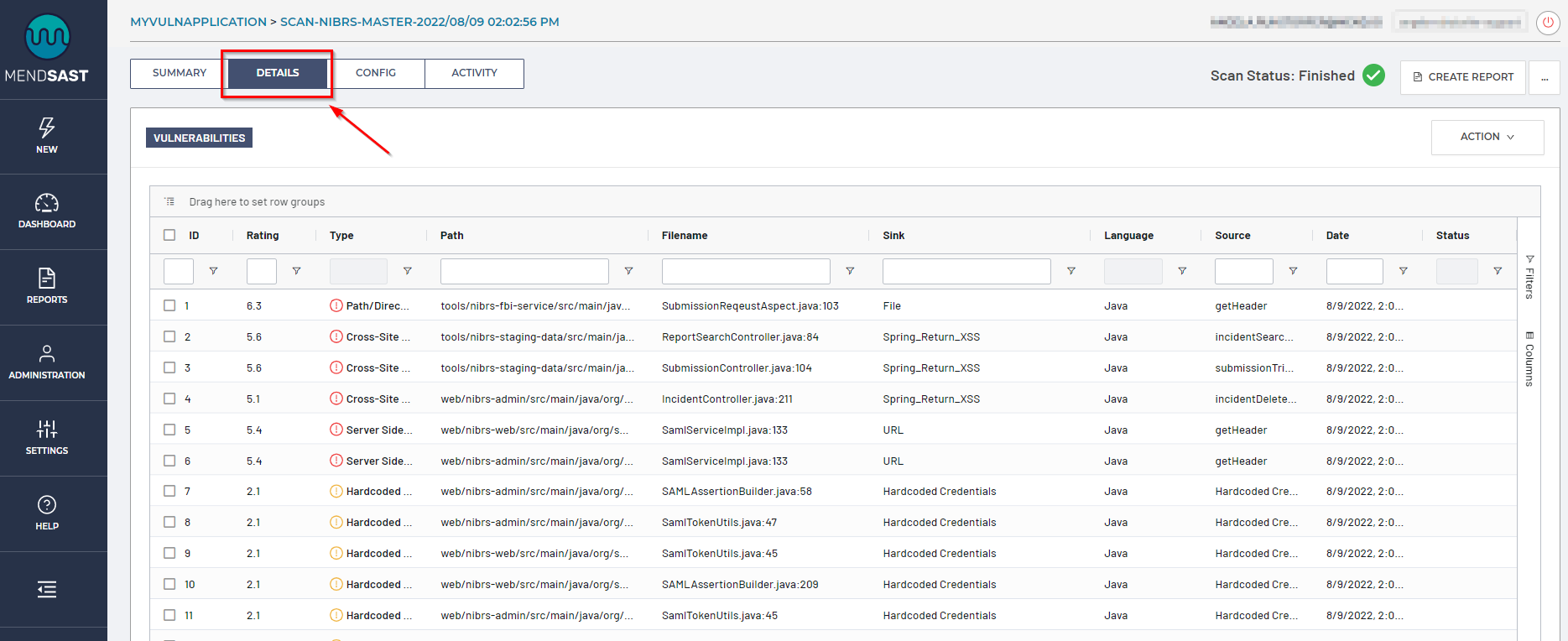
Adjusting the table
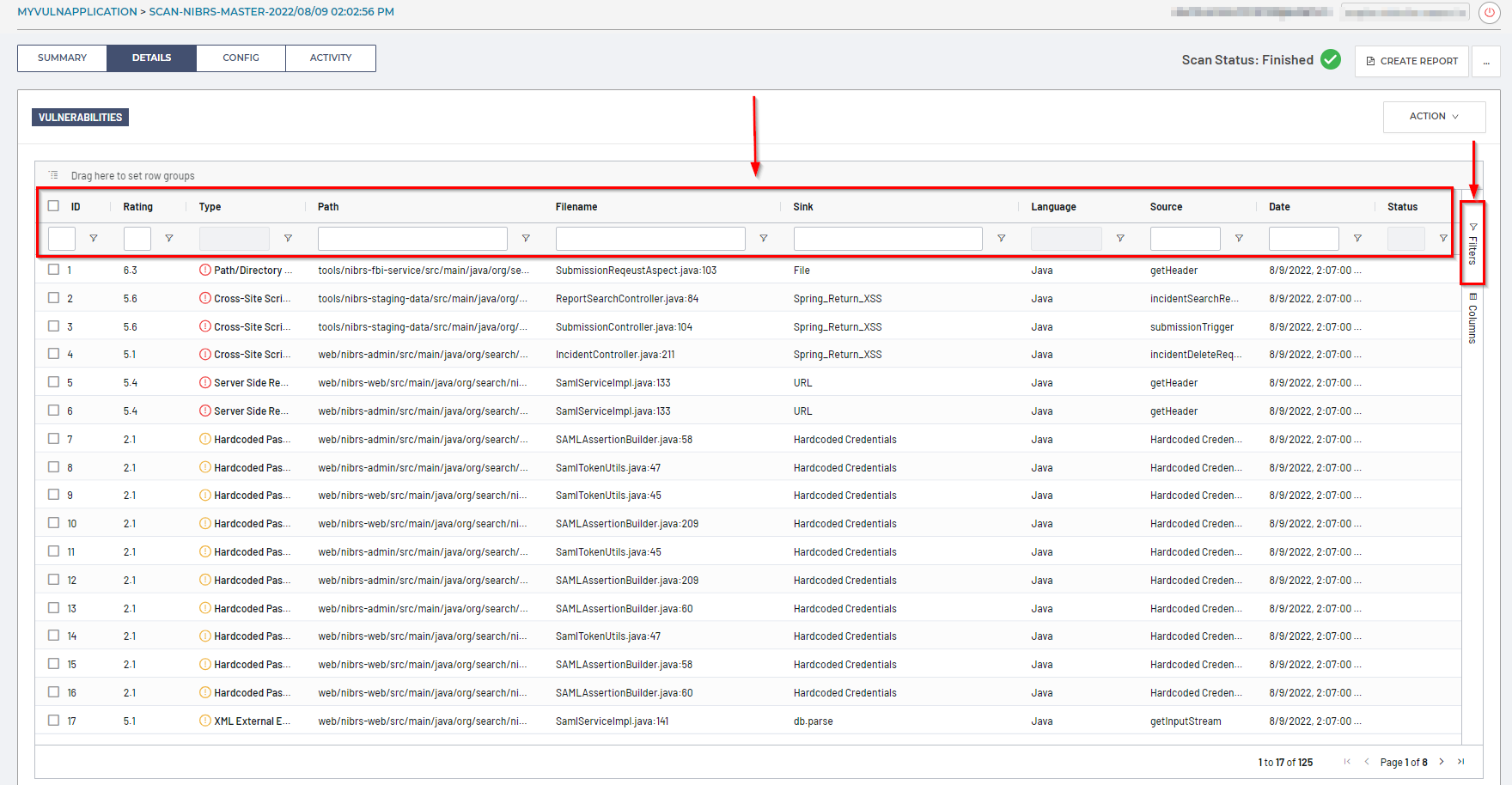
Filtering
To filter the findings within the scan’s Details table, you can click on the Filters icon underneath each column header, or, click on the Filters option on the right side of the table:
Columns
To show or hide columns within the scan’s Details table, click on the Columns option on the right side of the table:
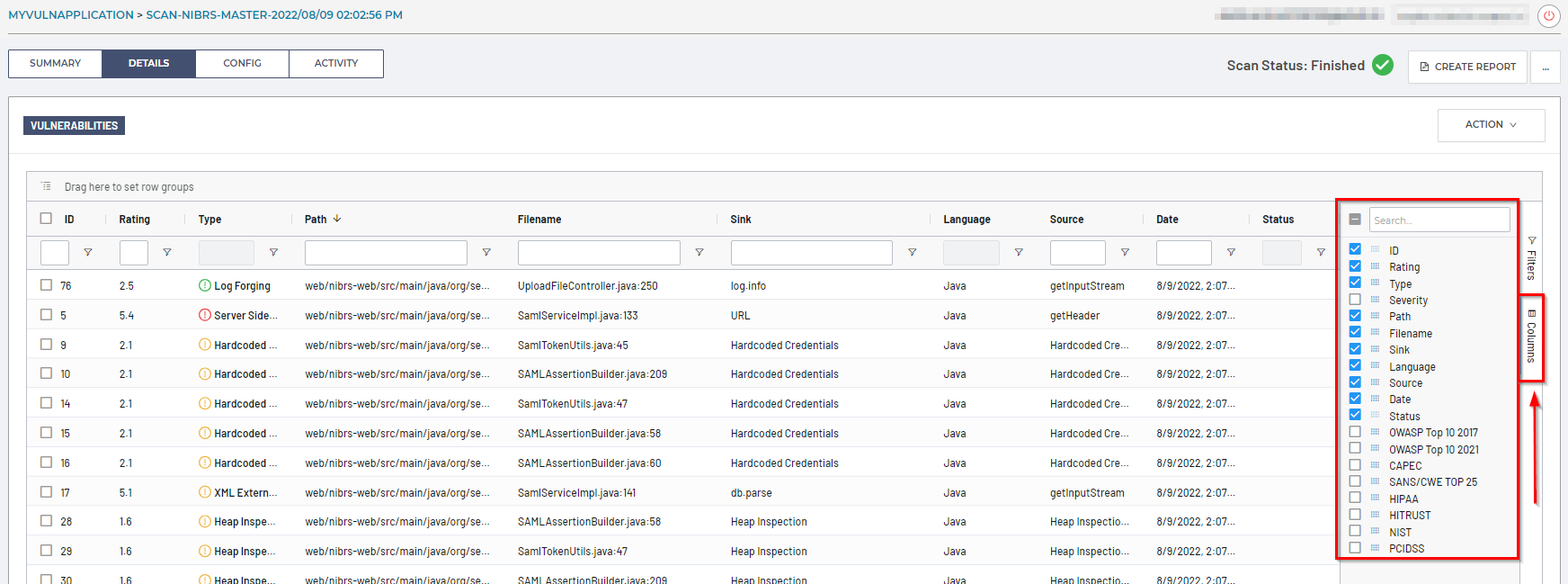
Rearrange the columns by grabbing the ‘hamburger’ icon next to each column title and dragging it left or right.
Row groups
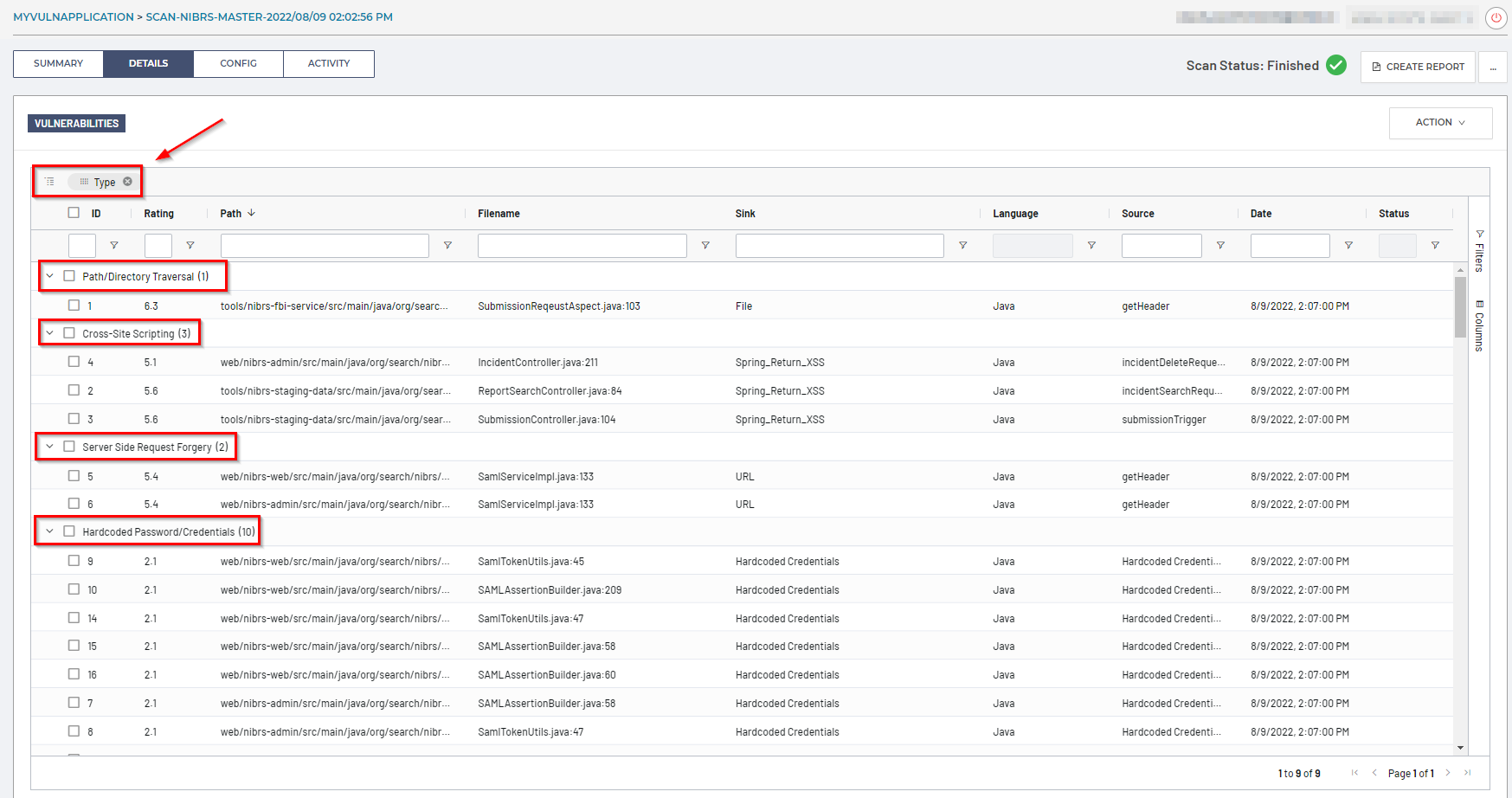
You can group vulnerabilities by dragging a column to the top bar above the table, or via the Columns > Row Groups section to create a flexible hierarchy of your scan data.
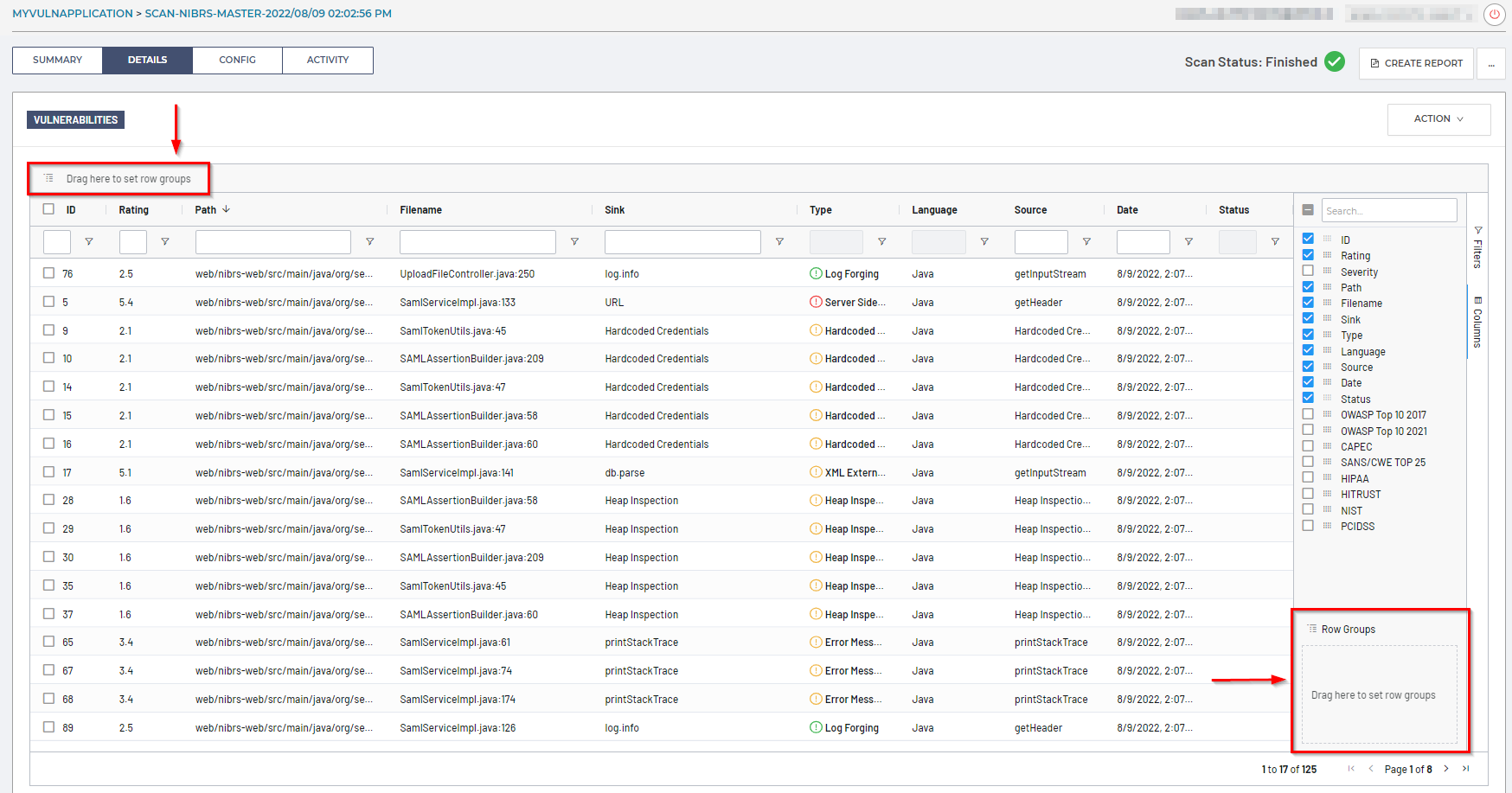
For example, dragging the Type column to Row Groups will reorganize the Details table by Vulnerability Type, as seen here:
Actions
Within the scan’s Details tab, you can complete actions on selected vulnerabilities from the table by clicking on Action:
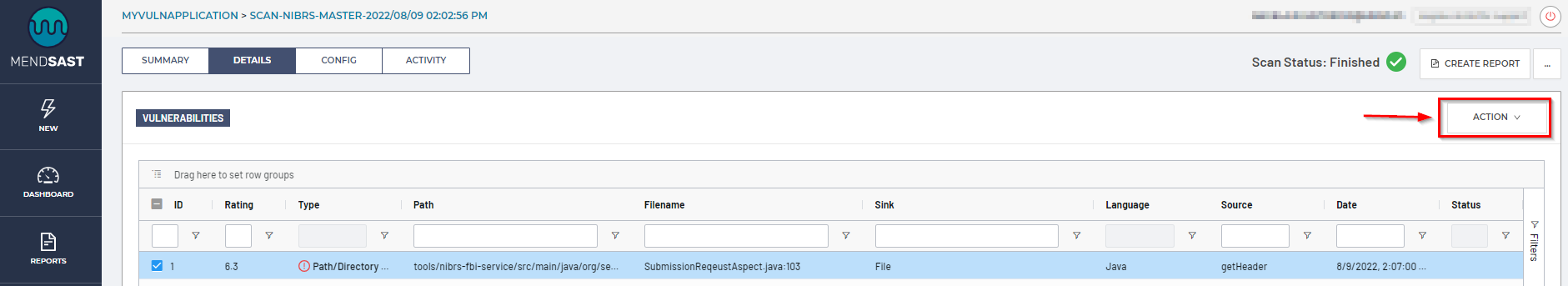
These actions include:
Mark as Reviewed - Mark the selected vulnerability(ies) as Status “Reviewed”
Mark as Unreviewed - Mark the selected vulnerability(ies) as Status “Unreviewed”
Suppress - Suppress the selected vulnerability(ies)
Unsuppress - Unsuppress the selected vulnerability(ies)
Change Severity - Edit the Severity of the selected vulnerability(ies) (Low, Medium High)
Submit Issues - Create an Issue on this vulnerability from your Settings > Issue Tracking configuration
Add Comment - Add a comment to the selected vulnerability(ies)
Vulnerability Information
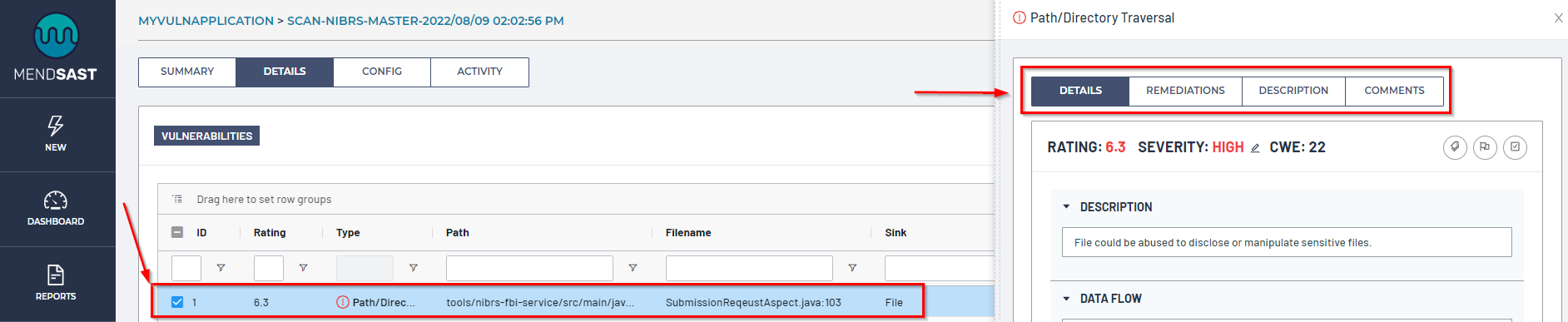
To view a detailed explanation of a vulnerability, simply click on the desired vulnerability within the table to open the information window of that vulnerability, which will open a sidebar that includes the vulnerability’s Details, Remediations, Description, and Comments tabs:
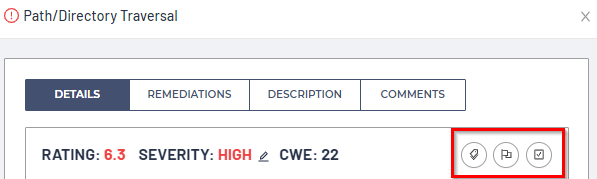
Vulnerability Details
The vulnerability Details tab provides the Rating, Severity, CWE ID, a brief Description, and an advanced Data Flow explanation on how the exploit works.
Hover over the Rating and Severity scores to display tool-tips that show the exact severity score and how the two were calculated:
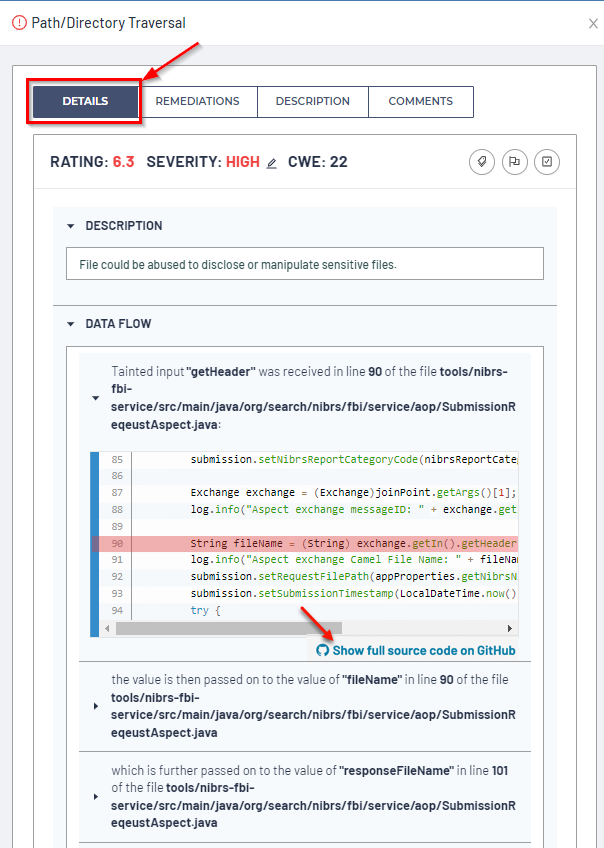
Within the vulnerability Details page, you can also:
Submit ALM Issue (Tag icon): Create an Issue on this vulnerability from your Settings > Issue Tracking configuration.
Suppress / unsuppress a vulnerability (Flag icon): Suppress / unsuppress this vulnerability. Reasons to Suppress an individual vulnerability or entire vulnerability type/group can be for scenarios such as false positives or accepted risks.
Review / unfull review a vulnerability (Checkbox icon): Mark / unmark this vulnerability for review.
Access the file from your repository.
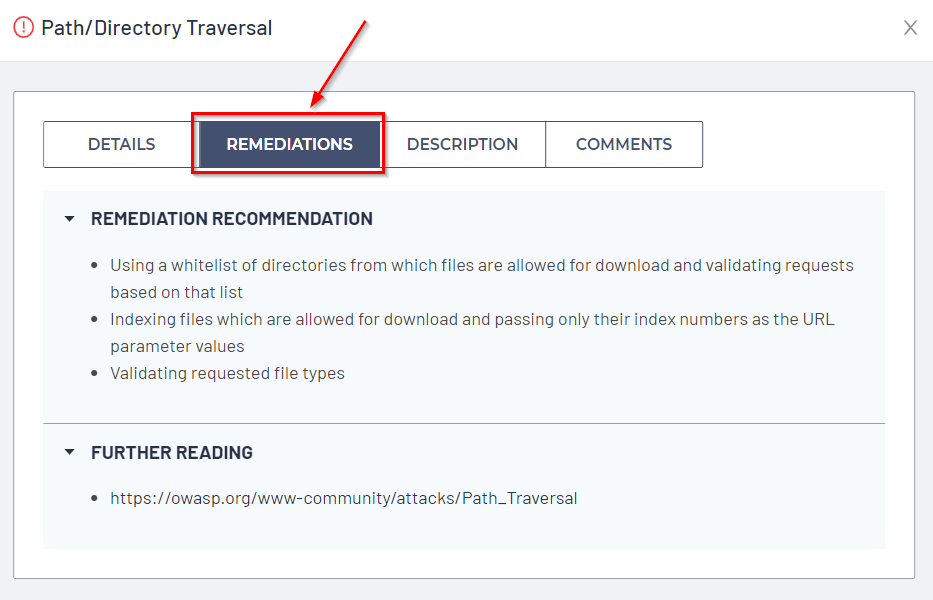
Vulnerability Remediations
The vulnerability Remediations tab provides details on the Remediation Recommendations to correct the vulnerability:
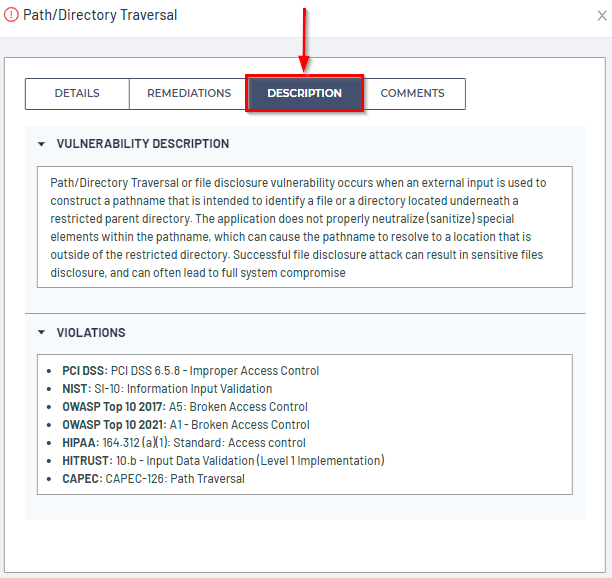
Vulnerability Description
The vulnerability Description tab provides a detailed Vulnerability Description, as well as the compliance Violations the vulnerability causes:
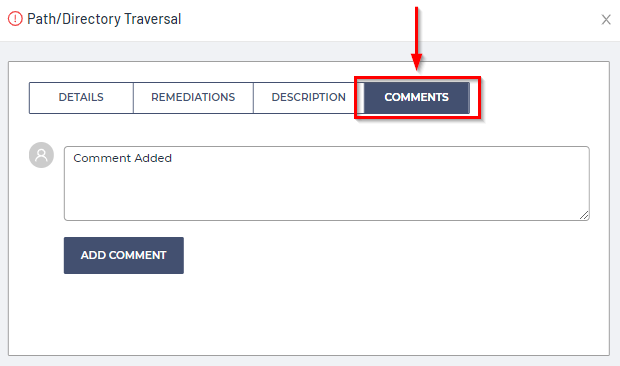
Vulnerability Comments
In the vulnerability Comments tab, you can add comments to the vulnerability:
Additional Actions
To view information on how to create a scan report and other additional scan options, please navigate to our Scan Actions article.
