Python with JFrog Artifactory - Host Rule Implementation
This article details the instructions to successfully configure our repo integrations with your Python (Pypi) private registries that are hosted in JFrog Artifactory. Python private registries can be accessed by authentication via a password or token. This will allow our repo integrations to scan your private Python packages for vulnerabilities and compliance.
Option 1: Generating a JFrog token
Within the JFrog platform Artifactory, navigate to your Administration > User Management > Access Tokens setting:
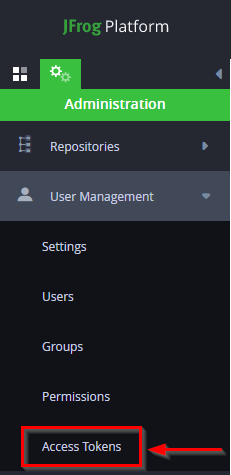
Click + Generate Token:
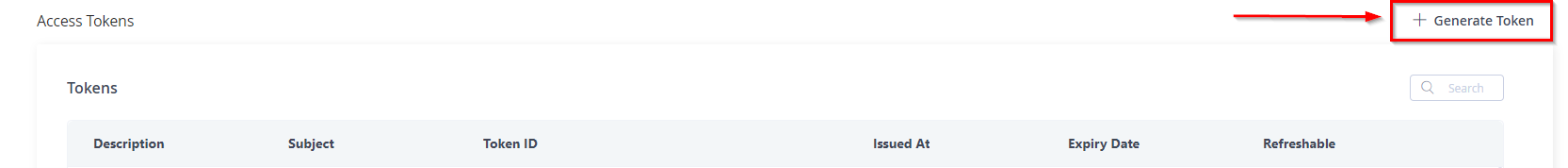
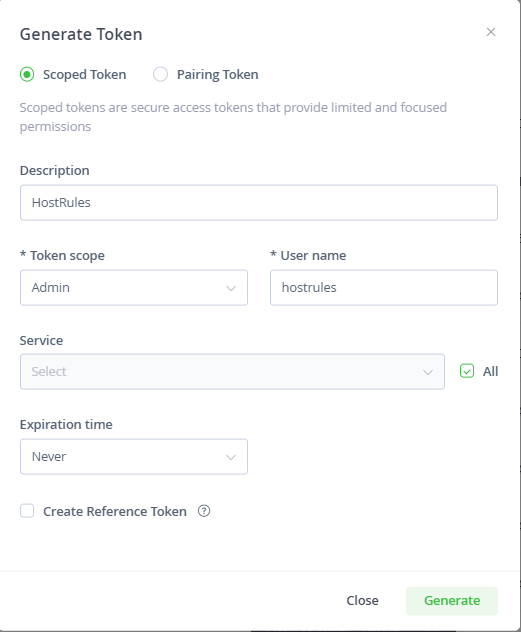
In the Generate Token window, select the Scoped Token option and fill in the settings as seen here:
Description: can be any value
Token scope: Admin
User name: can be any value
Service: All
Expiration time: Never
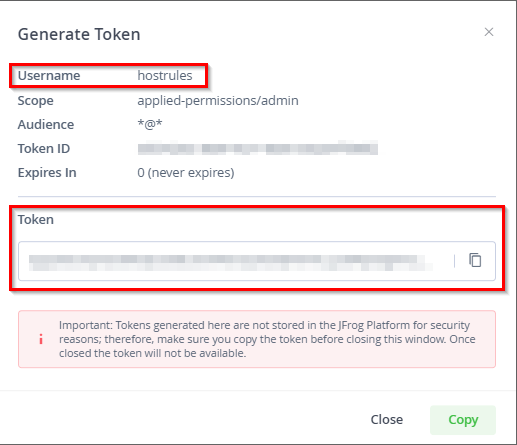
Click on Generate. Copy the Username you defined and the token that is generated:
Option 2: Using your JFrog password
Within the JFrog platform Artifactory, navigate to the repository where your Python packages are located
Click on Set Me Up in the top-right corner of the page:
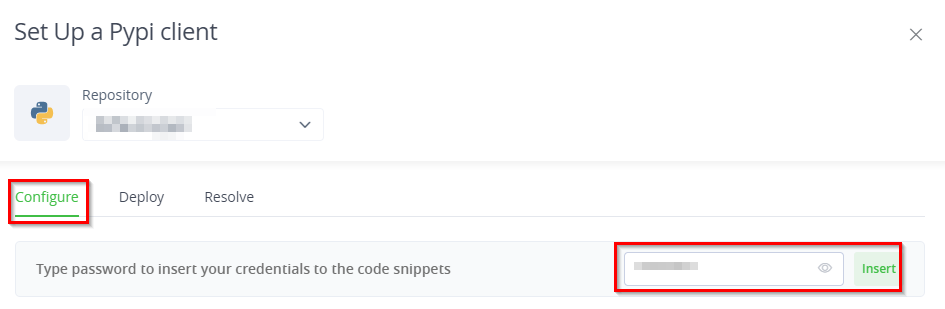
Make sure the correct repository is selected within the Set Up a Pypi Client window
In the Configure tab, enter your password and click on Insert:
Navigate to the Deploy tab and copy the
passwordvalue under the "To deploy packages using setuptools..." option: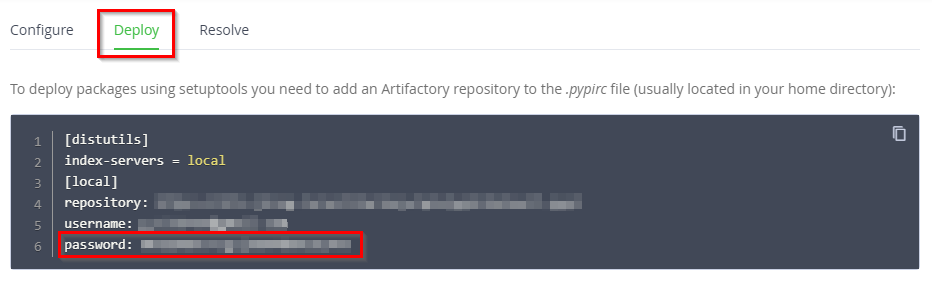
Encrypting the JFrog token or password
For Mend-Hosted repo integrations (GitHub.com, Bitbucket Cloud, and Azure Repos)
Navigate to our Mend's Repository Integration Secrets Encryption page
Each secret you encrypt must be scoped to a GitHub org, Bitbucket Cloud Workspace, or Azure project, and its use will be restricted to those within the app. There are the following fields on the encryption page:
Organization\Group - required; your GitHub org, Bitbucket Cloud Workspace, or your Azure project to which secrets are to be scoped
Repository - optional; your GitHub or Azure repository to which secrets are to be scoped
Raw value - required; your JFrog token that was created earlier in Option 1, or your JFrog password from Option 2
Click on Encrypt. This will create an encrypted value, which is the result of the encryption to be used in the integration
Copy this encrypted value
For Self-Hosted repo integrations (GitHub Enterprise, Bitbucket Server and Data Center, and GitLab)
Follow the steps outlined below to generate encryption for each of the Self-Hosted repo integrations:
Mend for GitHub Enterprise | Handling Private Registries and Authenticated Repositories
Installing Mend for GitLab | Handling Private Registries and Authenticated Repositories
When generating a secret, there are the following fields on the encryption page:
Organization\Group - required; your GitHub org, GitLab group, or Bitbucket group to which secrets are to be scoped
Repository - optional; your repository to which secrets are to be scoped
Raw value - required; your JFrog token that was created earlier in Option 1, or your JFrog password from Option 2
Click on Encrypt. This will create an encrypted value, which is the result of the encryption to be used in the integration
Copy this encrypted value
Where can I find the matchHost URL for Python?
The URL that is to be used for the matchHost setting in the hostRules can be found by following these steps:
Within the JFrog platform Artifactory, navigate to the repository where your Python packages are located
Click on Set Me Up in the top-right corner of the page:

Make sure the correct repository is selected within the Set Up a Pypi Client window
In the Configure tab, enter your password and click on Insert:

Navigate to the Deploy tab and the
repositoryvalue under the "To deploy packages using setuptools..." option will be the matchHost parameter you will host when applying the hostRules: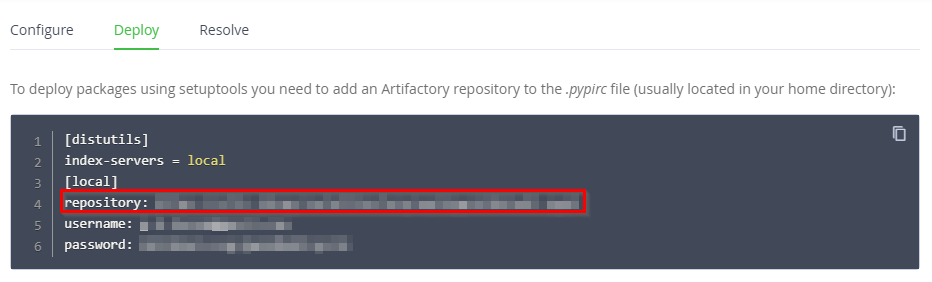
NOTE: When looking into the Artifactory repo’s General tab, the URL to file will look something like this:https://<JFrog_Instance>/artifactory/<JFrog_Repo_Name>/
This is not the correct URL for the matchHost setting. We need the specific repository URL under the Deploy tab (from the steps mentioned above), as Artifactory adds the needed api/pypi values to the URL, like so:https://<JFrog_Instance>/artifactory/api/pypi/<JFrog_Repo_Name>/
More information on Python repos + Artifactory logic can be found in Artifactory’s documentation here.
Applying the hostRules
Within your repo-config.json (if you have a global setup) or, in your .whitesource file (if you are configuring at the repo level), include the following required hostRules settings:
matchHost - The URL of the JFrog repository where your Python packages are located. NOTE: You should have one rule for each JFrog repository where your Python packages are located - meaning there can be multiple hostRules
hostType -
pypiuserName -
When using a token (Option 1), this will be the Username value that was set when you created the JFrog token
When using a password (Option 2), this will be the email address of your JFrog account
token or password - The encrypted value that was generated
hostRules Examples
token Example:
{
"hostRules": [
{
"matchHost": "https://<JFrog_Instance>/artifactory/api/pypi/<JFrog_Repo_Name>/",
"hostType": "pypi",
"userName": "hostrules",
"encrypted": {
"token": "3f832f2983yf89hsd98ahadsjfasdfjaslf............"
}
}
]
}password Example:
{
"hostRules": [
{
"matchHost": "https://<JFrog_Instance>/artifactory/api/pypi/<JFrog_Repo_Name>/",
"hostType": "pypi",
"userName": "engineers@mend.io",
"encrypted": {
"password": "p278djfdsi9832jnfdshufwji2r389fdskj........."
}
}
]
}