Is My Project Vulnerable to CVE-2019-0820?
This article provides details on the use-cases when your project is vulnerable to CVE-2019-0820 as well as ways to remediate this vulnerability.
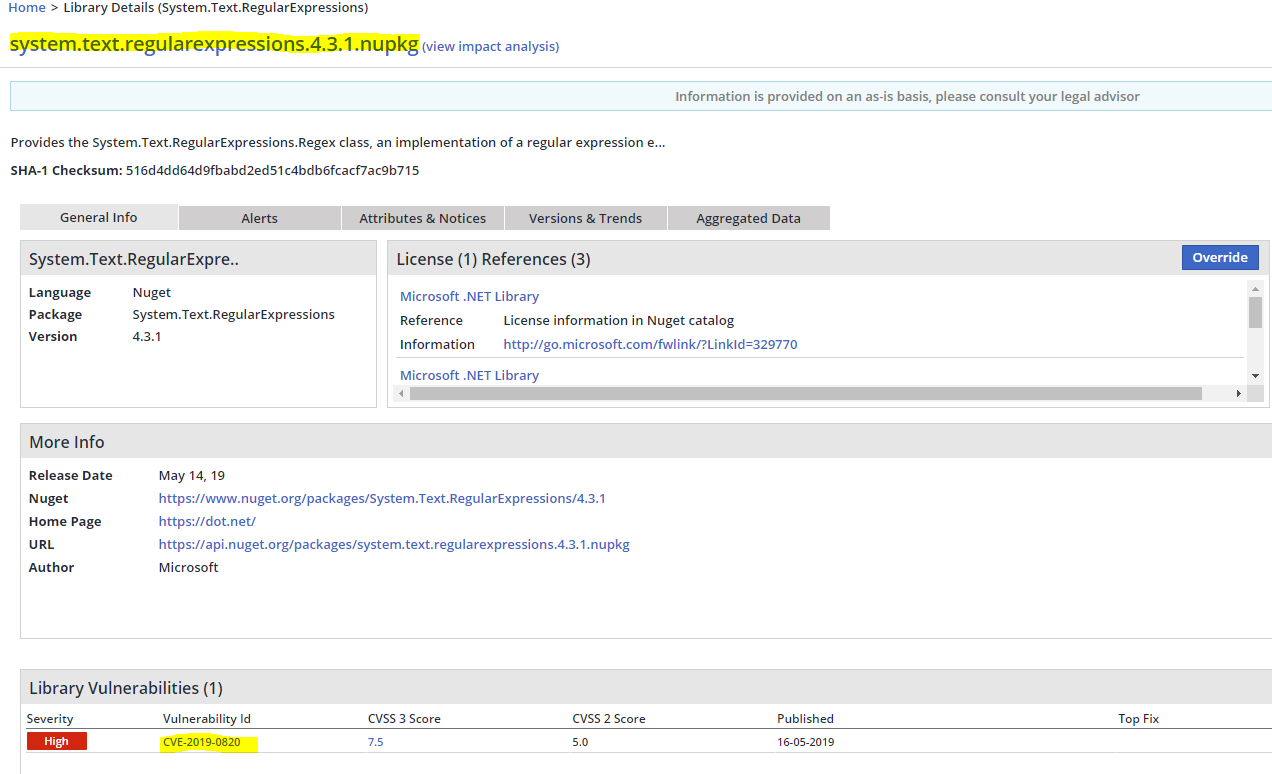
Upon encountering one of the following libraries:
system.text.regularexpressions.4.3.0.nupkg
system.text.regularexpressions.4.3.1.nupkg
The user can see that they are reported by Mend as vulnerable to CVE-2019-0820
When is CVE-2019-0820 a true positive?
In case the project has the CVE-2019-0820 reported then if it is actually vulnerable or not depends on the used .NET Core Runtime version.
The vulnerable .NET Core Runtime versions for this CVE are:
v1.0 branch: 1.0 - 1.0.16 (exclusive)
v1.1 branch: 1.1 - 1.1.13 (exclusive)
v2.1 branch: 2.1 - 2.1.11 (exclusive)
v2.2 branch: 2.2 - 2.2.5 (exclusive)
How to remediate the vulnerability?
To address this vulnerability the user should update the Runtime version and the related package.
If the user is running a higher .NET core version than listed above while using the package version 4.3.1 then they are secured from the vulnerability and they can safely ignore the alert.
Some additional explanations can be found on our documentation page here:
.NET-Core-and-ASP.NET-Core-DLL-Files
Microsoft Security Advisory also presents the relevant exposures for each .NET Framework version here:
Microsoft Security Response Center - Security Update Guide
