The Risk Report
Overview
The Risk Report is a management-level tool that provides a bird's-eye view of all aspects of an account's open-source libraries with regard to security, quality and compliance.
Accessing the Report
From the main menu, select Reports > Risk. The Open Source Risk Report is displayed.
Define the scope for which the report should be created. The default scope is Organizational; however you can select any individual product and/or project for your data scope from the dropdown menus next to the report name, as follows:
Open the All Products dropdown menu and select the product on which you want to base the report.
If you want to base the report on specific projects, open the All Projects dropdown menu and select one or multiple projects in the selected product.
Click Apply and wait for the data to load into the report.
Understanding the Report Data
Note: The first page of the report will include information about the selected scope (Organization / Product / Project), the creation date and various security and license risk related metrics.
The Open Source Risk Report comprises a number of panels and tables displaying risk-related information, as described in the following sections.
How Do We Compare?
NOTE: This section appears only at organizational level.
This section displays how selected measurements of your organization's risk and compliance levels compare to overall average statistics calculated for Mend customers. It includes the following three charts:
Vulnerable Libraries: The percentage of vulnerable libraries in your organization compared to the overall average calculated for Mend customers.
Policy Violating Libraries: The percentage of policy-violating libraries in your organization compared to the overall average calculated for Mend customers.
Outdated Libraries: The percentage of outdated libraries in your organization compared to the overall average calculated for Mend customers.
NOTE: An indication is also provided (in brackets) showing if the above measurements are better than average/worse than average.
Security
NOTE: For customers with Vulnerability-based Alerting enabled, some of the headings in the Security panel were changed. See Security Alerts: View by Vulnerability .
This panel displays a high-level graphic analysis of the health of your software, at organizational level or product level views. This includes the vulnerability score (base on the highest severity vulnerability), number of vulnerable components out of total components, severity distribution, aging security vulnerabilities, license risk distribution, outdated components out of total components and libraries with multiple versions.
Panel | Description |
|---|---|
Vulnerability Score | Displays the highest severity in the scope (Organization, Product or Project). |
Vulnerable Libraries | The following statistics can be displayed about Vulnerable libraries:
|
Severity Distribution | Counts the distribution of the highest severity vulnerability of all libraries. If a library has high, medium and low vulnerabilities, it is counted as 1 High. |
Aging Security Vulnerabilities | Counts the vulnerabilities according to the Vulnerability-based Alerts data model. See also Security Alerts: View by Vulnerability . |
License Risks and Compliance
This panel provides an overview of the License Distribution of the organization (or product), showing which licenses are used and how many libraries are associated with each license.
This panel also provides the License Risk Distribution, indicating the number of policy-violating libraries, and how many libraries are associated with each license (see Risk Score Rating). The Other bar refers to libraries with unspecified licenses, or licenses that have yet to be rated.
Quality
This panel to the right of License Risks and Compliance provides information about any outdated library versions.
Additional Risk Information
The remainder of the Risk report contains detailed tables with various component-level breakdowns.
NOTE: In the detailed tables, by clicking on any of the field names you can sort the table in ascending order. Clicking the field name again will sort in descending order.
General Overview Table
This table provides an overview of Libraries, Licenses, Security & Quality per product.
General Overview Columns
1. Project - The project within the product for which the summary is displayed.
2. Libraries - Displays the overall number of dependencies in the project, the number of direct dependencies, and the number of indirect dependencies (where applicable).
3. Licenses - Displays the overall number of licenses in the project alongside the risky licenses.
4. Security - Displays the overall number of vulnerabilities in the project alongside the outdated libraries.
5. Last Scan - Applicable for product and project-level reports only, this column displays the date of the most recent scan performed on each project.
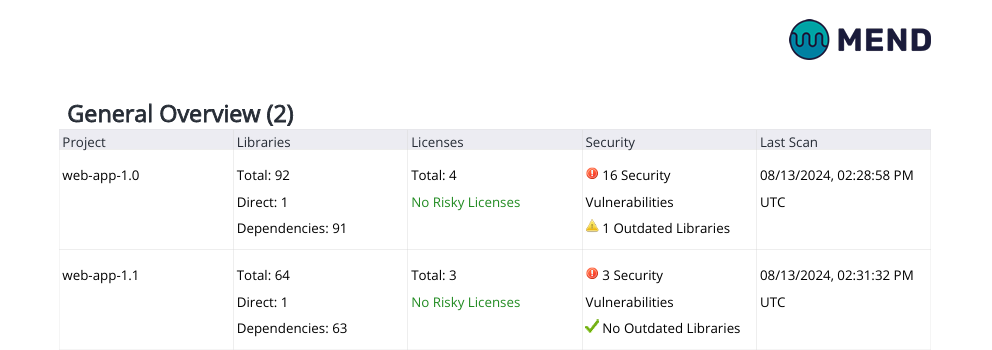
Example of the General Overview Table in a Product-level Risk Report
Security Vulnerabilities Table (Security)
This table provides a detailed list of Security Vulnerabilities per component. For each Vulnerability, the associated Library, Description and Top Fix are displayed.
Outdated Libraries Table (Security)
This table provides details of Outdated Libraries per product or project, their current Versions, and the recommended action to be taken for each outdated library (usually to update to the latest version). When selecting per product, the table only lists each library one time and not once per project as shown on the Product Dashboard.
Use of Different Versions of the Same Library (Security)
This table provides details of libraries for which different versions are included in the code base. It displays only multi-version usage within the same product, not multi-version libraries throughout the organization (i.e., using different versions of a library in two separate deliverable products does not count as multi-version usage).
Policy Violations (Compliance)
This table provides details of libraries that violate organizational or product policies per project, along with the date of violation and recommended actions.
High-Risk Licenses (Compliance)
This table provides details of libraries that are associated with high-risk licenses, along with indications on the risk nature and score, as well as recommended actions.
Exporting the Report
You can export the Risk report as a PDF file, to be shared within the organization. To do this:
Click Export to PDF at the top right of the report.
The exported report will reflect the selected report scope (organizational, product or project) and specified filters.
