Identify your container image secrets with the Mend CLI scan
Overview
Secrets are any kind of sensitive or private data that gives authorized users permission to access your IT infrastructure. These include keys and credentials such as SSH keys and certificates, TLS keys, encryption keys, API keys, database credentials, and more.
Secrets should be kept strictly private as attackers can easily find and use them to access and control the assets they are meant to protect. Developers may leave hard-coded secrets in container images, especially during rapid development and deployment cycles, thereby putting your organization and infrastructure at risk.
The Mend CLI scans your images to find any secrets that have been left behind.
Note: This article specifically covers the usage and support of the Mend CLI’s OS license detection feature. For general information on the Container Image engine of the Mend CLI, check out these articles:
Use cases for identifying container image secrets with the Mend CLI
As an AppSec Manager, your organization must comply with various security policies and regulations that require sensitive data to be protected at all times. If secrets are exposed in container images, the organization could face penalties and reputational damage.
As a DevOps Engineer, you are responsible for managing the company's internal tools and services. You create a container image that includes credentials for an internal system. If this image is leaked or compromised, an attacker could gain unauthorized access to the system.
Mend’s Answer: By implementing Mend CLI’s secret detection for your container images, you can ensure that any exposed secrets are identified and resolved before deployment.
Getting it done
Prerequisites before identifying container image secrets with the Mend CLI
The following prerequisites are required before running a Mend CLI Container Image scan:
Run the Mend CLI to identify your container image secrets
Secret detection is enabled by default. To initiate the Mend CLI Container Image scan, run the following command:
mend image <image_name[:image_tag]>View the secrets detected by the Mend CLI Container Image scan
Console results
The Mend CLI Container Image scan outputs a summary of the detected secrets ordered by their severity risk:
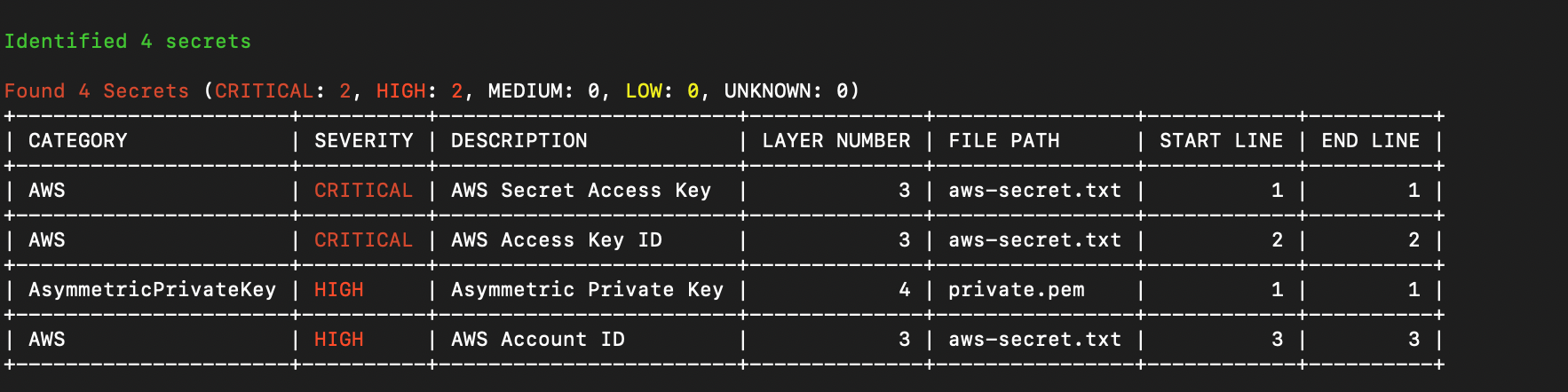
Field | Description |
Category | The Secret Category, for example: Cloud Provider, SaaS Provider, etc. |
Severity | The Secret Severity Level. The supported values are:
|
Description | A description and the type of secret |
Layer Number | The layer in which this secret was found |
File Path | The full path and name of the file in which the secret was found. |
Start Line | The line in the file in which the secret is located |
End Line | The line in the file in which the secret ends |
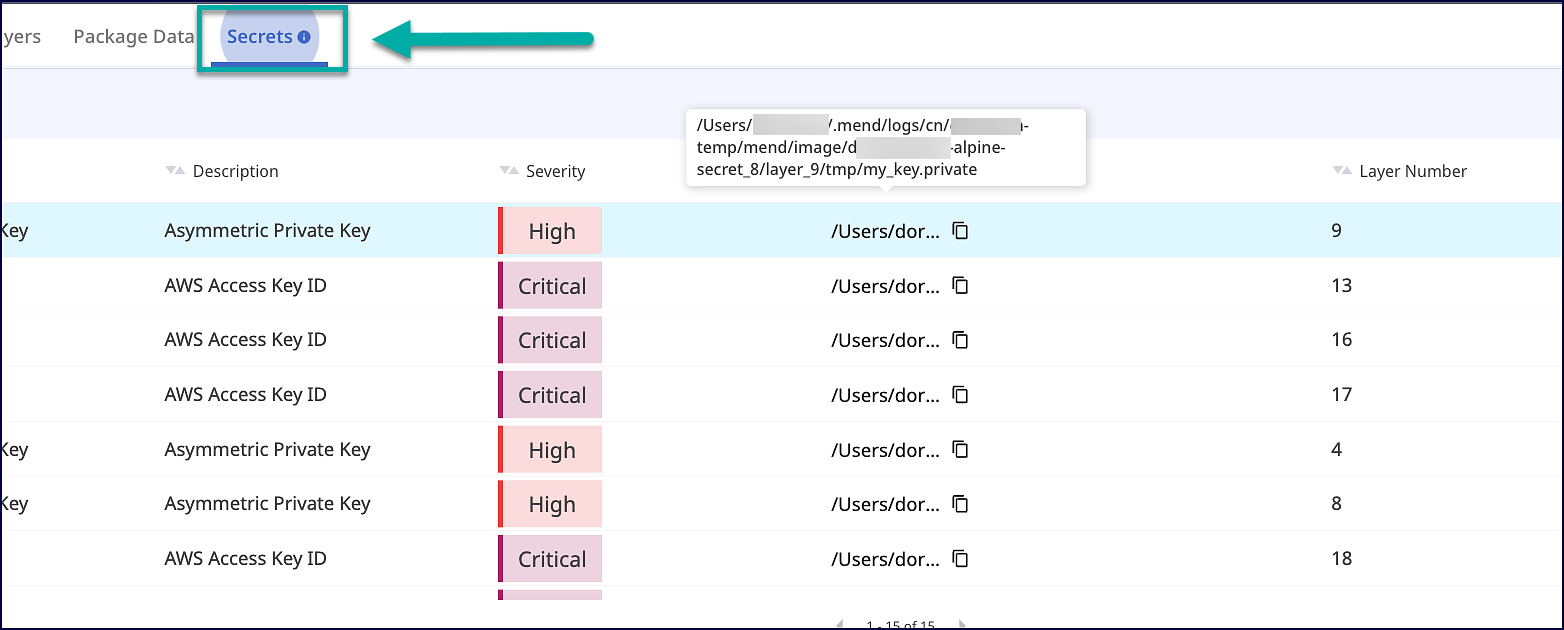
Mend Cloud Native Application
Note: Only organization administrators can access the Mend Cloud Native Application UI.
Within the Mend Cloud Native Application, you can review each Mend CLI scan’s summary, details, and more. For more information on how to navigate the Mend Cloud Native Application, visit our Mend Cloud Native Application documentation:
Reference
Mend CLI-supported file types for secret detection
Text-based files
All text-based files based on the file encoding.
For example:
File Type |
|---|
.json |
.pem |
.private |
.txt (Including Linux text files without suffix) |
.yaml |
Native code files: .go, .py, .js, and others. |
Mend CLI-supported formats for secret detection
Format | Details |
|---|---|
Alibaba |
|
AWS |
|
Bitbucket |
|
GitHub |
|
GitLab | GitLab Personal Access Token |
Package manager tokens |
|
Private Keys |
|
SaaS Keys & tokens | lack, Shopify, Stripe, Twilio, Facebook, Twitter, Adobe, Asana, Atlassian, Databricks, Discord, Dropbox, Doppler, Dynatrace, Grafana, HashiCorp, HubSpot, and Intercom |
SSH Key |
|
