Mend Container Runtime Sysdig Integration
Overview
Using Mend.io and Sysdig together will have the benefit of an end-to-end application security solution that combines left-side and right-side insights with richer context to both ends of their security coverage.
Teams who are focused on left-side AppSec will have better visibility on what’s happening in runtime, with the ability to provide runtime context to the security issues they create.
Cloud Security teams focused on the runtime side will have visibility into who owns what and will be able to close the loop with the developers faster.
With this offering, we help AppSec teams bridge gaps between code and the cloud.
Getting it done
Note: The integration only supports images with the Open Container Initiative (OCI) label org.opencontainers.image.source=<repo path>
Set Up the Sysdig Integration
Navigate to the integrations catalog (Cogwheel
 --> Integrations), and scroll down to the Runtime section.
--> Integrations), and scroll down to the Runtime section. 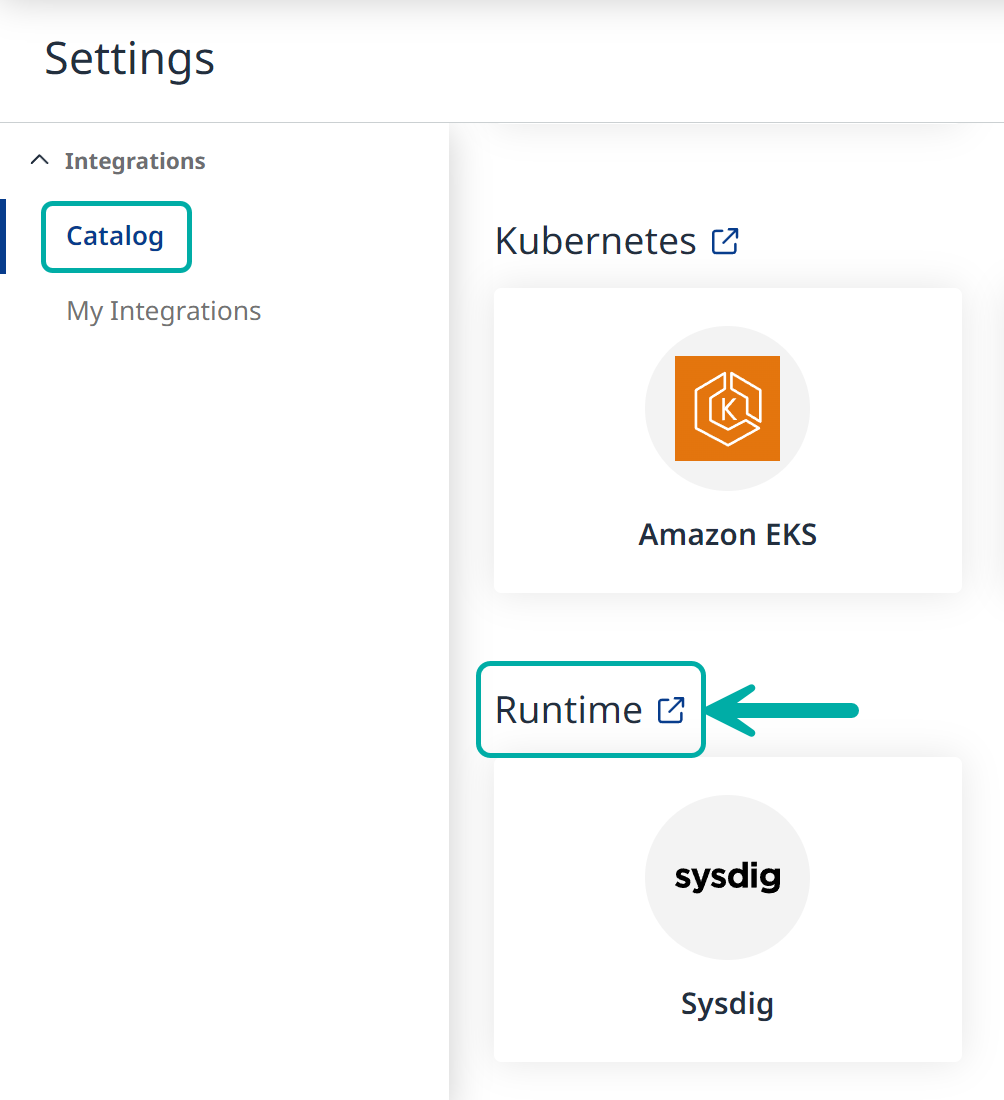
Click on the ‘sysdig’ icon to start the wizard.
The Setup Wizard
Step 1 - Authentication
a. Display Name = A free text to display in the Mend UI
b. Sysdig URL = The Sysdig URL of your environment
c. User Email = The user email that is associated with the Sysdig account
d. API Key = The Sysdig API Key (the API key to use is the “Risk spotlight” key from the Sysdig App)
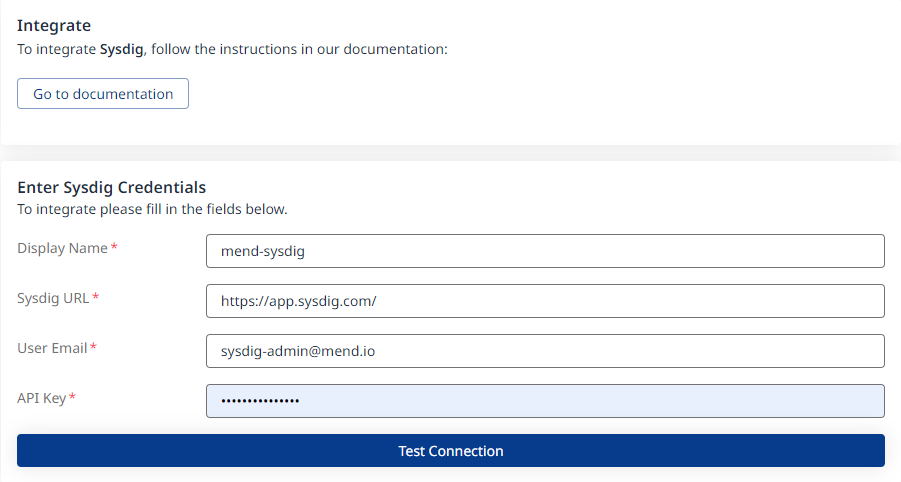
Click ‘Test Connection’. Once successful, click Next to move on to Step 2 - Clusters.
Step 2 - Clusters
In this step, the list of monitored clusters will be displayed.
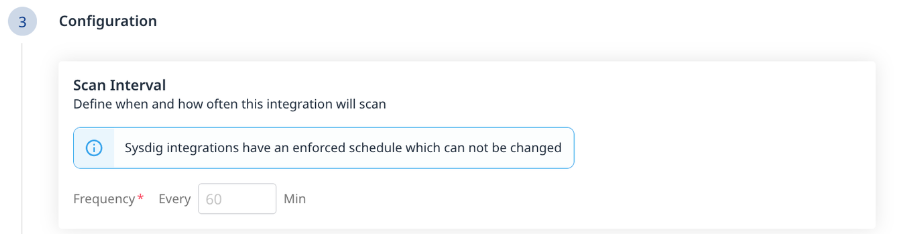
Step 3 - Configuration
Define the Frequency of your scans.
Step 4 - Summary
In this step, the summary of your input from steps 1-3 will be displayed. You can go back to the previous screens of the wizard to make changes, by clicking the ‘Back’ button at the bottom right corner of the screen. If you wish to confirm your configuration and add your registry, click the ‘Done’ button:

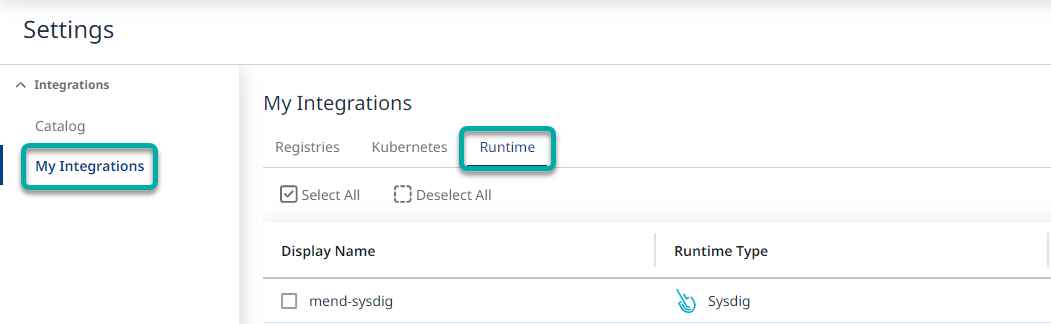
See the active integration in the ‘My Integrations’ section. Make sure to select the ‘Runtime’ tab:
View the Results of your Sysdig Integration
Package and CVE Runtime Statuses
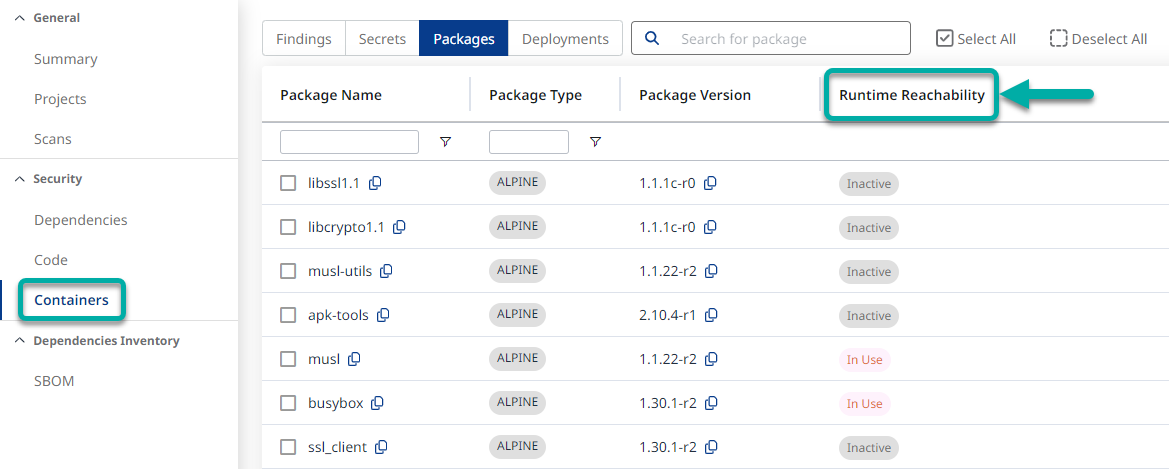
A. Navigate to your application or project’s ‘Packages’ tab.
B. Check the status in the Runtime Reachability column for a specific package. This column describes the package status during runtime.
Stauses:In Use describes a package that Sysdig identified as used during runtimeInactive describes a package that, at the time of the scan, was not identified by Sysdig as used during runtime.
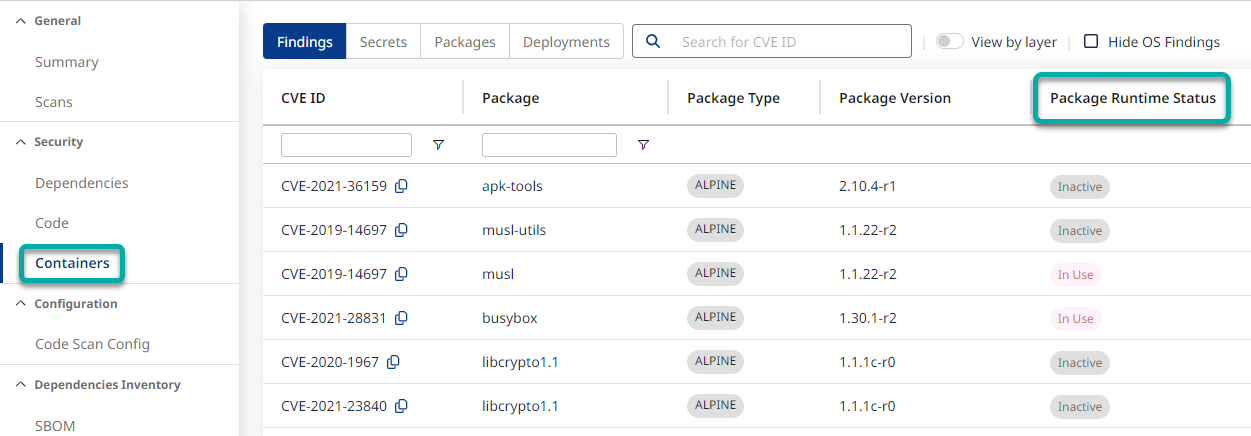
Note: Similar information is available per CVE under the ‘Findings’ tab
Deep Dive into the Runtime Context
By clicking on a CVE / Package that is classified as In Use and navigating to its Reachability tab,
you can see a static image level reachability status, as well as the Runtime/Container level reachability context.
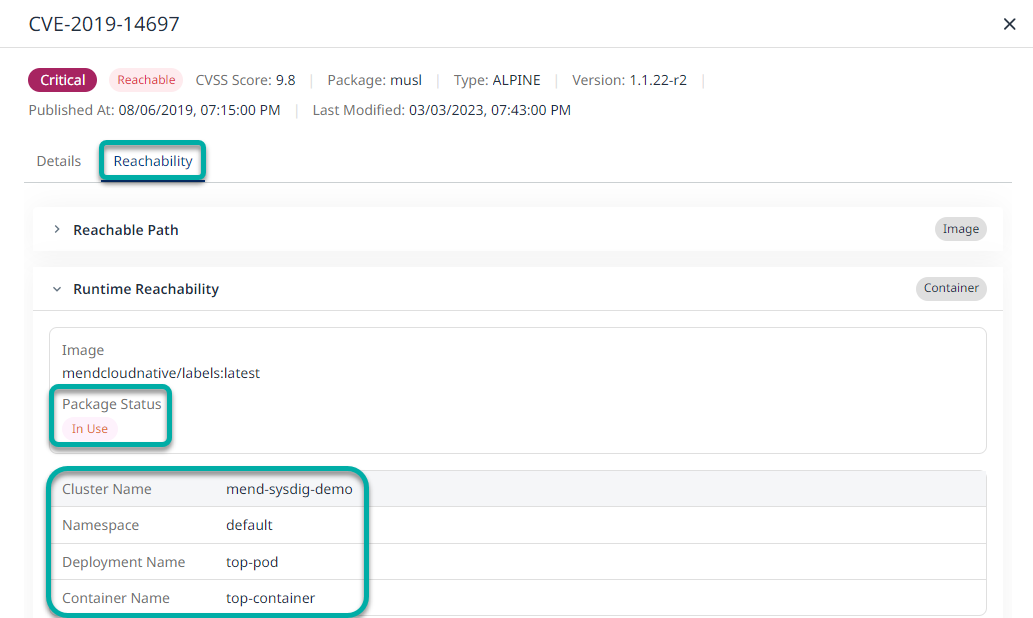
Note: All of the instances where the image is in use during runtime are displayed, alongside the cluster name, namespace, deployment name and container/pod name.
Prioritizing Findings with the Runtime Reachability
Mend.io recommends using all of the following to demonstrate the prioritization value:
Filtering by CVE severity values.
Applying the static container reachability (By Mend.io) filter to
ReachableApplying the Runtime Reachability indication (By Sysdig) filter to
In UseSort the findings by the EPSS score to understand the exploitability risk.
[Optional] filtering out the Operating System packages from the findings
Limitations
The integration only supports images with the Open Container Initiative (OCI) label org.opencontainers.image.source=<repo path>
