Integrate Mend Reachability Insights into Microsoft Defender for Cloud
Overview
Mend.io integrates with Microsoft Defender for Cloud to share open-source security findings from Mend SCA and Container directly into the Defender portal. This allows security teams to view Mend-detected vulnerabilities in the context of their broader cloud security posture.
To set up the integration, you need to generate a token in the Mend AppSec Platform and use it to connect Mend to Microsoft Defender for Cloud. Once connected, relevant SCA and Container findings from Mend will be automatically pushed and displayed in Defender for Cloud. The Mend.io integration with Microsoft Defender for Cloud surfaces both SCA Reachability and Container Reachability, enabling runtime teams to focus on exploitable risks only.
Getting it done
Prerequisites
A Mend account with read access to your organization's Mend projects and findings.
You need a Microsoft Azure subscription.
You must enable Microsoft Defender for Cloud on your Azure subscription.
You must enable Defender Cloud Security Posture Management (CSPM) on your Azure subscription.
To view all prerequisites, please refer to the Connect Mend.io to Defender for Cloud documentation.
Retrieve your Activation Key from the Mend Platform
Log into your organization via the Mend Platform.
Note: Make sure you are an organization administrator.Navigate to the settings (cog icon) → Integrations:
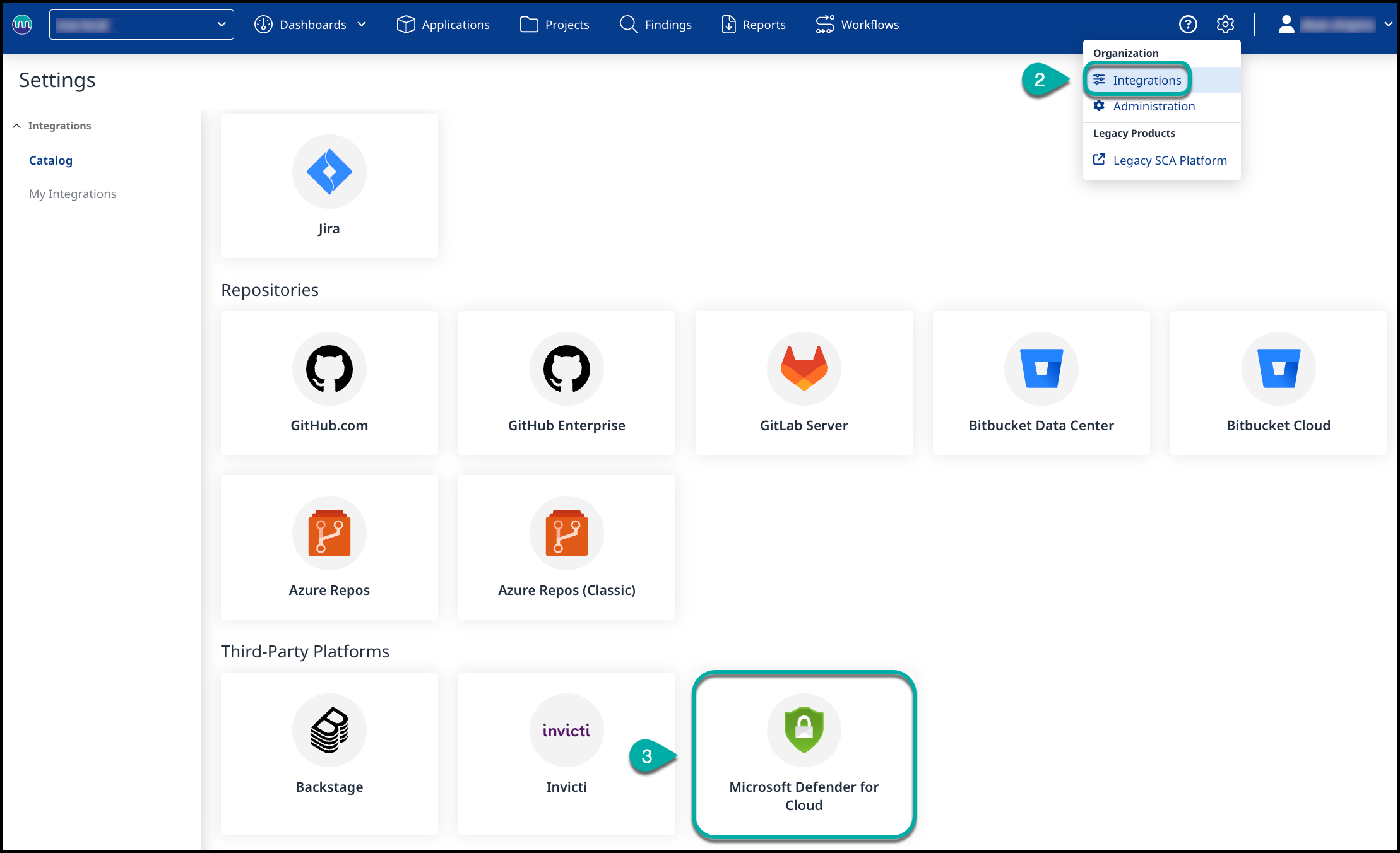
Click on the Microsoft Defender for Cloud card. Then, click on the Get Activation Key button that appears to get your activation key for the Invicti Integration.

Copy and save this value for the next step.
Configure the Mend Integration in Microsoft Defender for Cloud
Details about connecting Mend.io to Defender for Cloud can be found here.
After the integration is successfully created, Defender for Cloud scans repositories connected to Mend.io and populates results after six hours.
