Configure Single Sign-On (SSO) for the Mend Platform
Overview
Integrate your enterprise-level Single Sign-On (SSO) solutions seamlessly with the Mend Platform UI to streamline user management and enhance your organization's access security.
Note: This feature enables SAST-only customers or new SAST + SCA customers without an existing SSO setup in the Legacy SCA Platform to configure the SSO login. If assistance is needed with the migration plan, reach out to your Mend contact for support.
How does SSO with the Mend Platform work?
Mend supports SP-Initiated (Service Provider Initiated) Single-Sign-On using SAML version 2.0.
The identity provider (IdP) connects between the service provider and the user. Examples of IdPs include Okta and Microsoft ADFS.
Use Case
The following illustration describes the functionality of Mend as a service provider in exchanging authentication and authorization data:
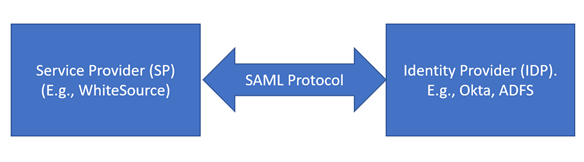
In Mend, the system parses the SAML permissions sent from the IDP. A SAML-enabled login does not include caching.
Getting it done
Note: Before getting started with the steps to configure and enable SSO for the Mend Platform, we strongly recommend reading through the Prerequisites and Boundaries sections of this article.
Prerequisites before configuring SSO for the Mend Platform
To set up an account SSO within the Mend Platform, you must be a user with account-level Admin role permissions.
To set up an organization SSO within the Mend Platform, you must be a user with organization-level Admin role permissions.
Configure SSO in your IdP
To configure your IdP for SSO with the Mend Platform, you will need to create a SAML 2.0 application within your IdP’s platform. Make sure to include the information below in the relevant application fields during your IdP-side configuration steps:
SSO URL:
https://login-<your_mend_instance_environment>/login/callback?connection=wss-con-<orgUUID>Example:
https://login-saas.mend.io/login/callback?connection=wss-con-<orgUUID>In Okta, as an example, the same string will also be used for ‘Recipient URL’ and ‘Destination URL’.
Audience URI:
urn:auth0:<your_mend_environment's_subdomain>-<2nd_level_domain>:wss-con-<orgUUID>Example:
urn:auth0:saas-mend:wss-con-<orgUUID>
Configure SSO in the Mend Platform UI
Configuring SSO within the Mend Platform UI is done via:
For account SSO:
Click on Settings (:mp_cogicon:) → Account → Account Management:
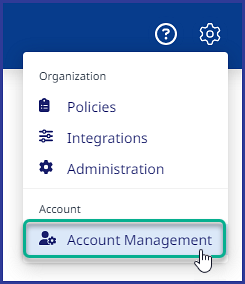
Click on SAML Integration:

Within the SAML Integration page, click on Edit:

For organization SSO:
Click on Settings (:mp_cogicon:) → Organization → Administration:
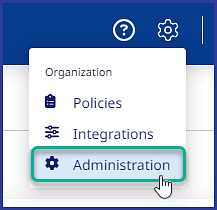
Under General, select SAML Integration:
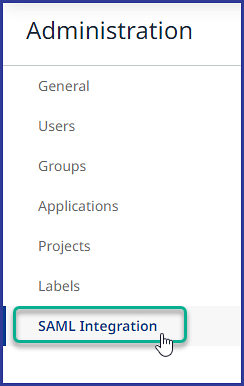
Within the SAML Integration page, click on Edit:

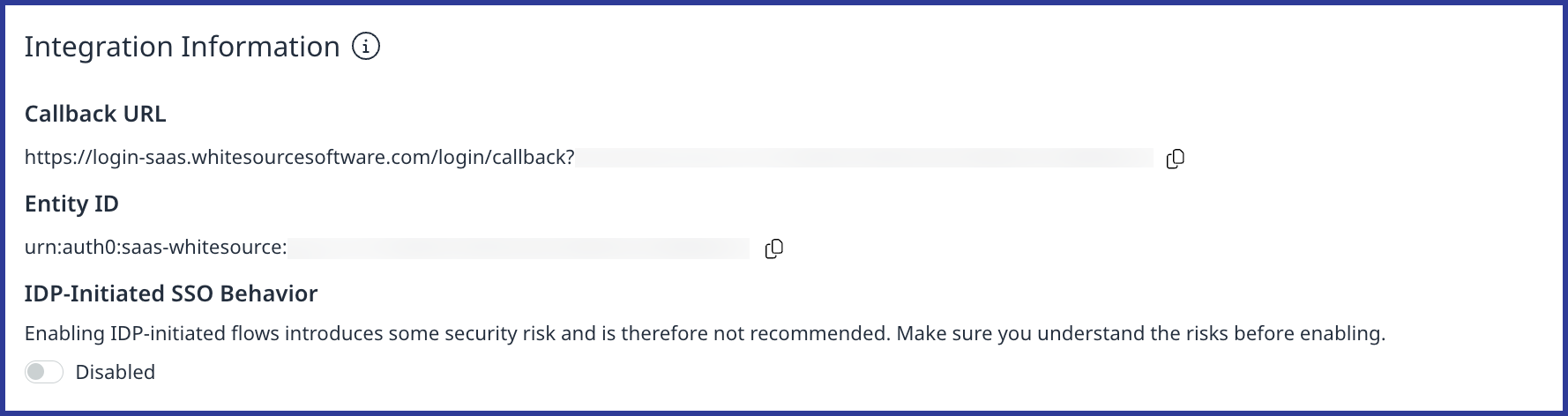
Integration Information
In the Integration Information section, you can find the Callback URL and Entity ID parameters for integrating your Idp’s platform with the Mend Platform. Also, you have the option to enable IDP-Initiated SSO Behavior.
Note: IdP-Initiated flows carry a security risk and are therefore not recommended. The recommendation is to use SP-Initiated flows whenever possible.
Metadata
In the Metadata section, add your IdP SAML application’s Metadata URL (the syntax of this URL varies across IdP platforms):

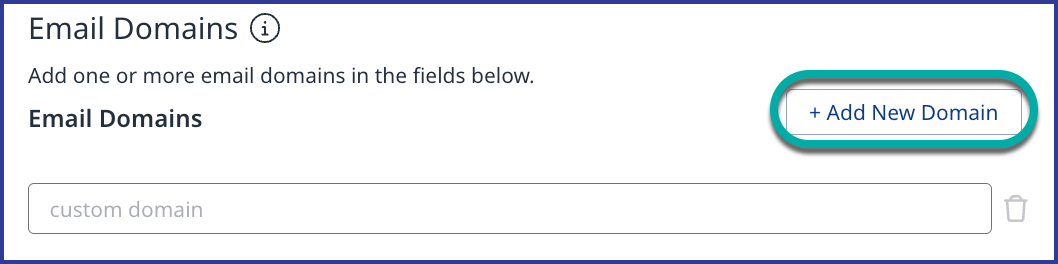
Email Domains
In the Email Domains section, click on + Add New Domain to add the email domain(s) used by your organization:
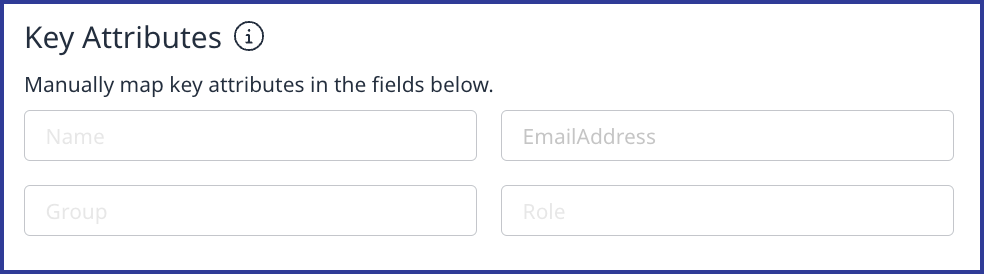
Key Attributes
In the Key Attributes section, add the attributes from your IdP that match the Mend Platform key attributes provided (Name, Email, Group, and Role). You can typically find these attributes by viewing your IdP’s SAML assertion. Below is a simple example:
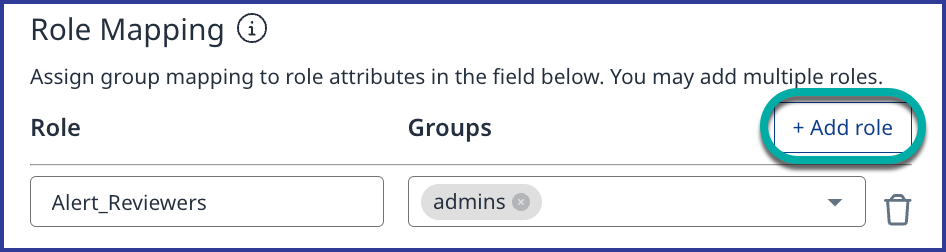
Role Mapping
In the Role Mapping section, click on + Add role to assign SSO users to defined roles in the Mend Platform.