Code Scan Customization Candidates
Overview
Scan Rule Customization is a project-specific mechanism that allows you to increase the accuracy of your Code scans. Scan Customization Candidates serve as a complementary feature, whereby potential candidates for enhancing the rules are picked up during the scan and presented to the Mend.io Professional Services engineer via the Rule Customization UI, where they can be accepted or rejected.
Use-case
An organization uses a framework that Mend.io does not support out of the box. During the regular SAST scan, the code will be analyzed for any potential entry points/sources/sinks/sanitizers. These candidates will be presented to the Mend.io Professional Services engineer in the customization view and can be accepted to proactively increase the accuracy of the Code findings.
Limitations
Scan Customization Candidates cannot be edited, they can only be approved or rejected.
Getting it done
AI Usage Toggle
Note: The Code Scan Customization toggle must be enabled for the Customization Candidates feature to be available.
Enable or disable AI-based Rule Customization for your Code scans using the Code Scan Customization toggle under the AI Usage section of your organization’s General Configuration.
If enabled, data about invocations of external libraries and method declarations in your source code is collected during the scan and will be shared with Mend.io’s AI model to improve the accuracy of your Code scans by suggesting candidates for further customization of the Code scan rules. Disable this option to prevent any information about your code from being shared with the model and turn off the candidate suggestions entirely.
Navigate to the Administration page using the cogwheel drop-down menu:
Under General Configuration, use the Code Scan Customization toggle to enable or disable the feature.
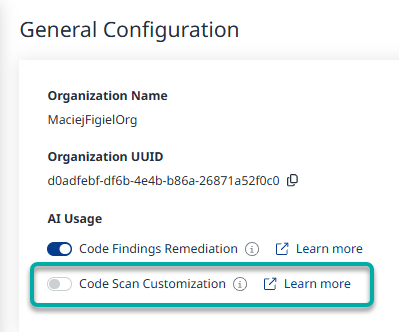
Note: Toggling these on means you consent to the use of AI for Code Findings Remediation and Code Scan Customization, respectively.
Supported Languages
Mend AI-based Code remediation supports the following languages and CWEs (Common Weakness Enumeration):
Language | CWE |
|---|---|
C/C++ |
|
C# |
|
Java | |
JavaScript | |
Python | |
TypeScript |
