Use the Mend CLI Container Image policy check for build control
Overview
You can set a build to fail if a Container Image component violates a policy defined by your organization within the Mend Application by configuring your pipeline to check for Exit Code 9 from the Mend CLI.
Note: This article specifically covers the usage and support of the Mend CLI’s policy check violation feature. For general information on the Container Image engine of the Mend CLI, check out these articles:
Getting it done
By default, your defined policies are checked during every Mend CLI Container Image scan. New policy violations on a previously scanned image will only be identified by rescanning the image with the Mend CLI.
While the results of the policy check are always updated in the Mend Cloud Native Application, the --show policy flag must be included in the Mend CLI command for the policy check results to appear in the terminal output.
Mend Tip: We recommend avoiding breaking builds unless you have carefully defined your policies and change management processes as this can cause significant disruptions to existing workflows.
Prerequisites before using the policy check with the Mend CLI Container Image scan
The following prerequisites are required before running a Mend CLI Container Image scan to fail on policy violations:
Define a policy within the Mend SCA Application or via the SCA API 2.0.
Run the Mend CLI Container Image scan fail policy check
To configure the Mend CLI Container Image scan to fail when a defined policy is violated, returning an Exit Code 9, run the following command:
mend image <IMAGE_NAME>[:<TAG>] --fail-policyMend Tip: To check the exit code of the Mend CLI after running scan, you can run the following example commands in your terminal:
For macOS/Linux:
echo $?For Windows:
echo %ERRORLEVEL%
View the policy violations detected by the Mend CLI Container Image scan
Once the Mend CLI scan is completed, there are multiple resources to review your results.
Policy Violations - Mend CLI
To explicitly print the Container Image policy violations to the Mend CLI output, include the --show policy flag in your command, for example:
mend image <IMAGE_NAME>[:<TAG>] --show policyPolicy violation findings are available in all Mend CLI-supported export formats for reporting: JSON, SARIF, TXT, and XML.
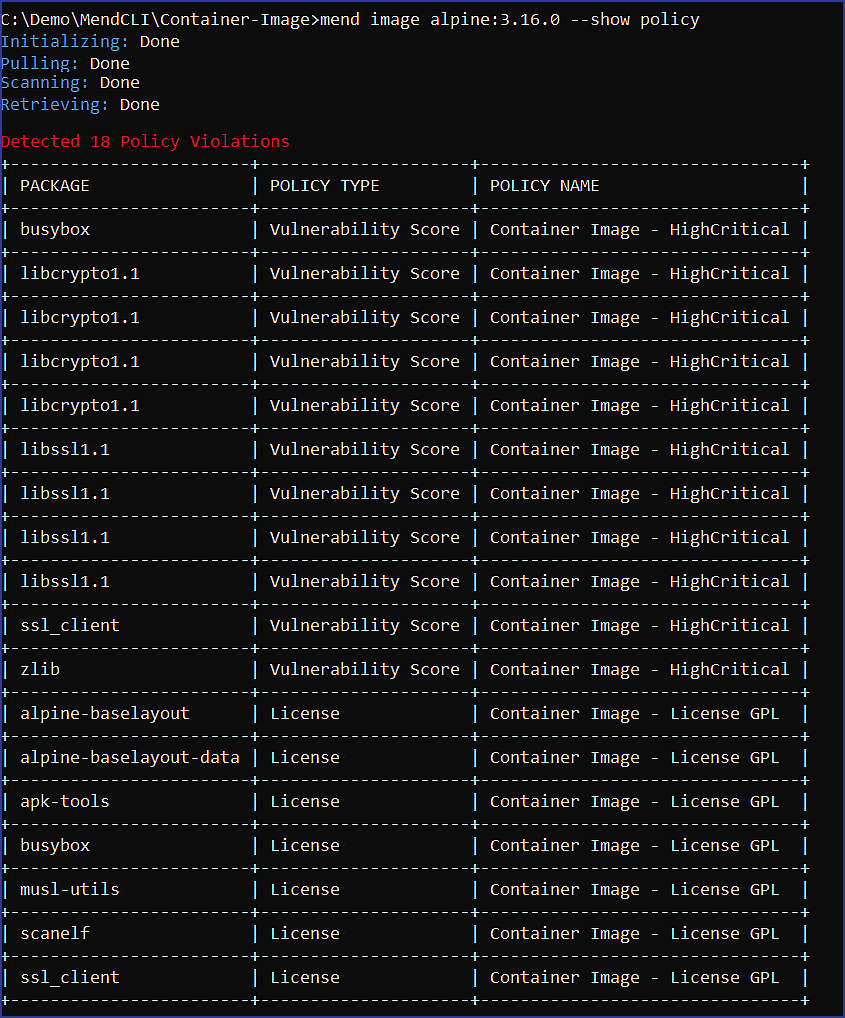
Field | Description |
|---|---|
| The name of the detected package that violated the policy. |
| The Match Type of the violated policy. The available values are:
|
| The name of the violated policy. |
Policy Violations - Mend Cloud Native Application
Policy violations will always appear in the Mend Cloud Native Application.
Within the Images tab overview, you can see and filter the data table on policy violations:
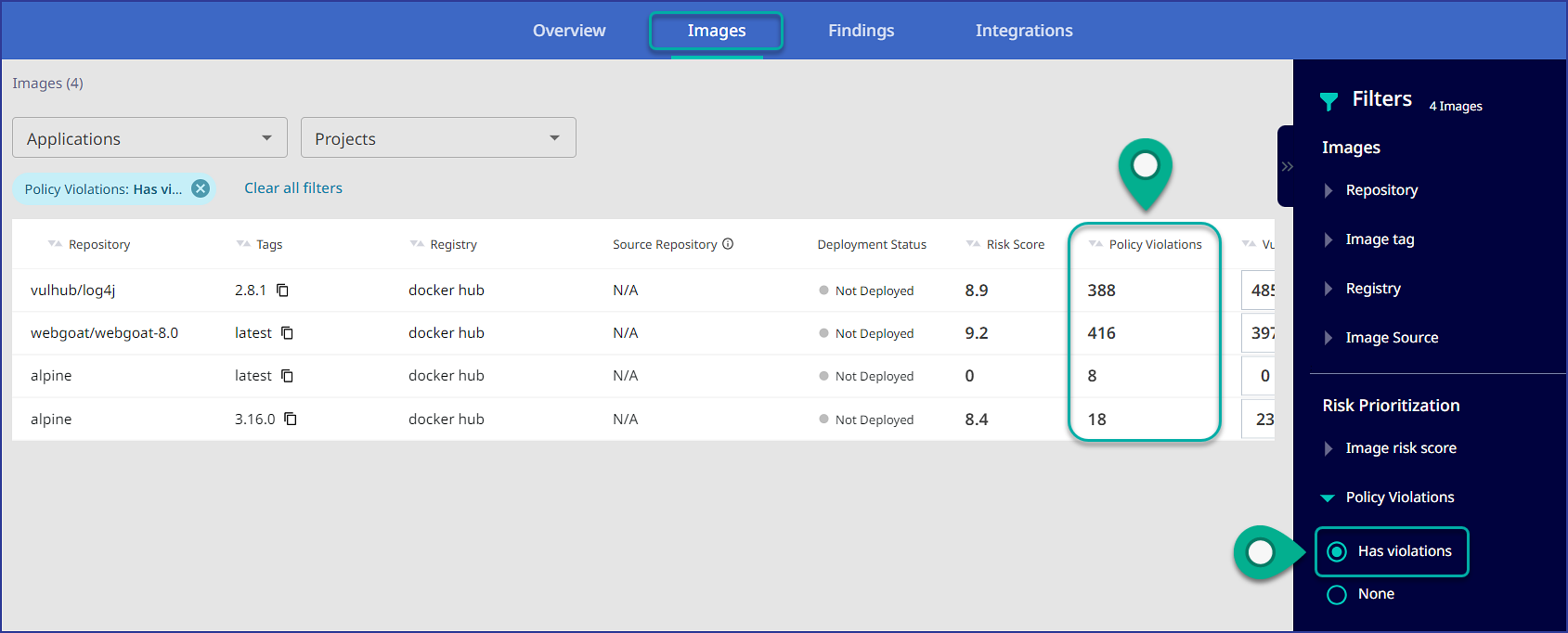
Clicking on an image within the Images tab will bring you to a detailed view of a specific image, where you can:
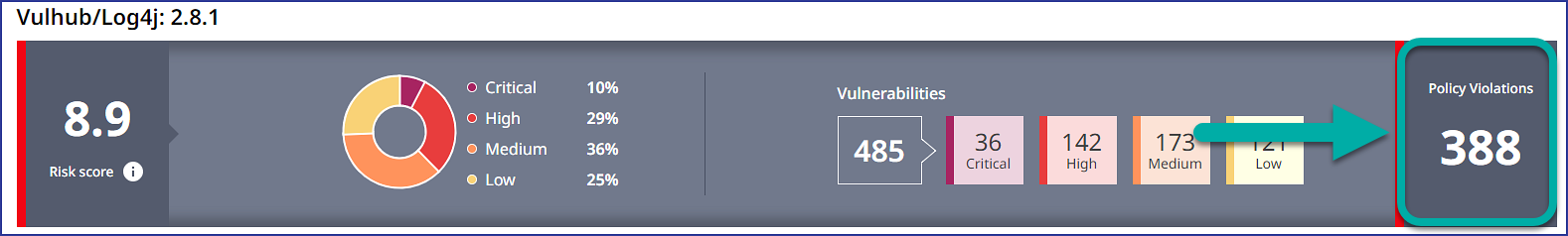
View the total count of Policy Violations for the image:
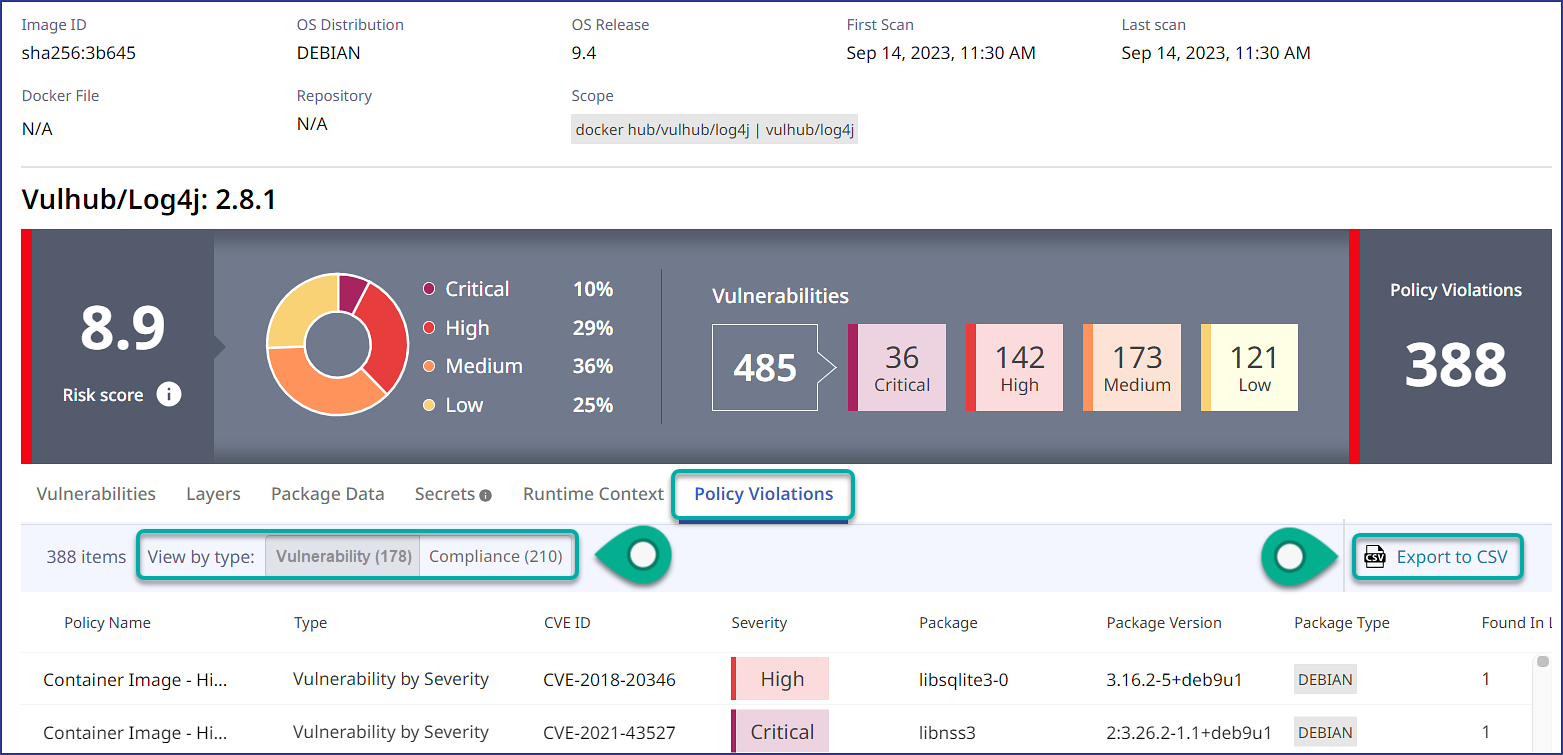
View the Policy Violations tab. Here, you can see the policy violations by Match Type for the image, as well as export this data to a CSV file:
Reference
Mend CLI Container Image limitations for policy checks
The policy check for container images supports the following:
Report Formats:
Mend Cloud Native UI: CSV
Mend CLI: JSON, SARIF, TXT, XML
The policy check for container images does not currently support:
In-House or Whitelisting rules.
Using the “Apply to existing inventory” button within the Mend SCA Application for policies.
