Least Vulnerable Packages Feature
Least vulnerable packages (LVP) automatically suggests the newest, least vulnerable library version and then auto-generates a PR for that version.
How does Mend calculate the risk reduction for LVP?
Our new approach to remediation with LVP is to establish a fix from a dependency tree perspective that will provide the greatest risk reduction. We calculate this risk score using the vulnerability(ies) CVSS 3.0 scores from each version’s dependency tree via the sum of the formulas for each severity below:
Icon | Severity & CVSS Score | Formula |
|---|---|---|
 | (C) Critical (9.0-10.0) | 10,000 x CVSS Score |
 | (H) High (7.0-8.9) | 1,000 x CVSS Score |
 | (M) Medium (4.0-6.9) | 10 x CVSS Score |
 | (L) Low (0.1-3.9) | 1 x CVSS Score |
Example
Let’s take a look at an example. For your application, you decide to add the npm library, express v3.0.0, and commit this change to your repository’s main branch, kicking off a Mend scan. Express v3.0.0 has a total of 17 transitive dependencies. Let’s review its dependency tree and vulnerabilities:
express-3.0.0.tgz (1 Medium)
→ commander-0.6.1.tgz
→ connect-2.6.0.tgz (5 Medium)
- bytes-0.1.0.tgz
- formidable-1.0.11.tgz
- pause-0.0.1.tgz
- qs-0.5.1.tgz (3 High, 1 Medium)
- send-0.0.4.tgz (1 High, 1 Medium)
→ cookie-0.0.4.tgz
→ crc-0.2.0.tgz
→ debug-4.3.4.tgz
- ms-2.1.2.tgz
→ fresh-0.1.0.tgz (1 High)
→ methods-0.0.1.tgz
→ mkdirp-0.3.3.tgz
→ range-parser-0.0.4.tgz
→ send-0.1.0.tgz (1 High, 1 Medium)
- mime-1.2.6.tgz (1 High)Adding up, express v3.0.0’s dependency tree has 16 total vulnerabilities, 7 High and 9 Medium. We then compare all other minor 3.x versions of express against v3.0.0 using our risk-scoring equation to determine the least vulnerable dependency tree. Let’s look at a visual of the scoring and decision-making below:
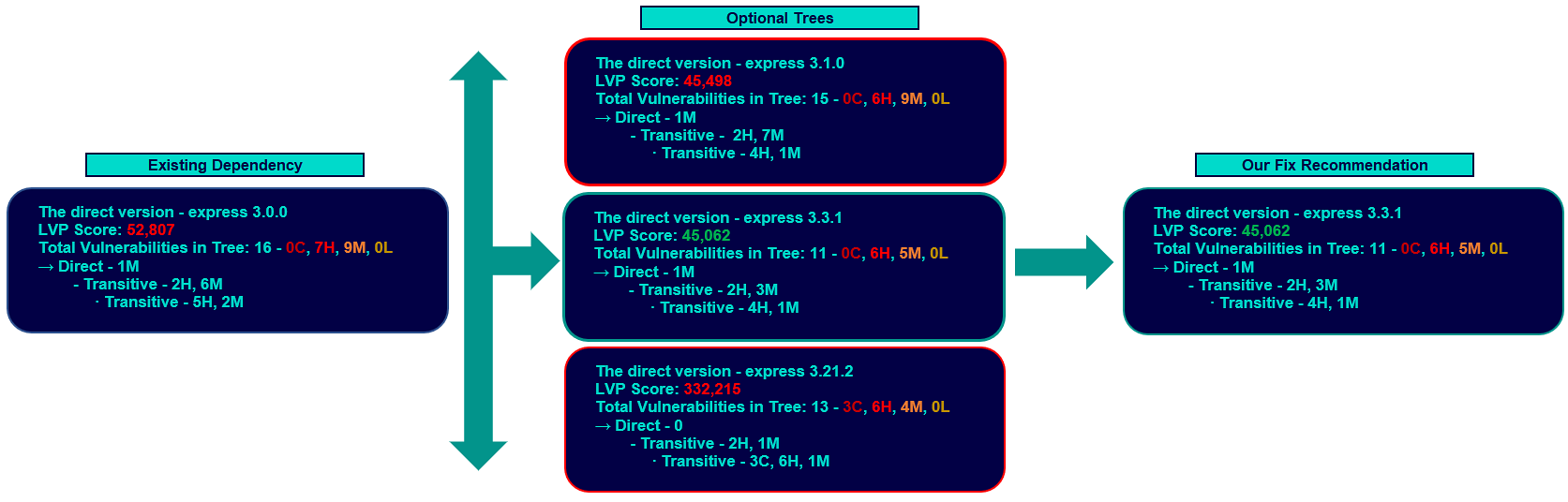
This results in the PR being generated with express v3.3.1 as the greatest risk reduction remediation fix, with a total of 11 vulnerabilities. We also display the vulnerability counts of the current version in your repository (express v3.0.0) and the latest available 3.x minor version (express v3.21.2). We did not recommend updating to v3.21.2 here as it has a numerically higher LVP score, with more, severe vulnerabilities than the current version and v3.3.1:
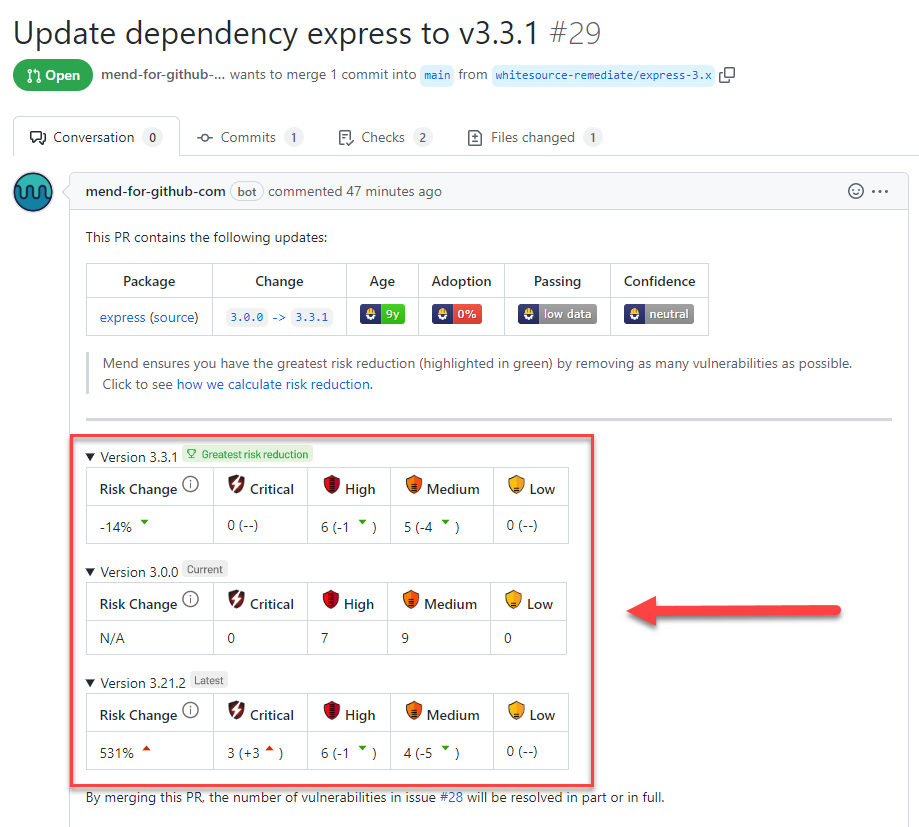
Procedure
Before You Begin
Supported on GitHub.com and GitHub Enterprise
Supported languages are listed here.
In your repo-config.json or .whitesource file, the “
issueType" setting must be set to "DEPENDENCY"Remediate must be enabled
Steps
Within your Mend repo integration, navigate to your repo-config.json (global) or your .whitesource (local repo) file.
Open your repo-config.json or .whitesource file in edit mode and add the
leastVulerablePackageSettings.trueparameter to enable LVP. This is set at the same level as thescanSettingsparameter:CODE"leastVulnerablePackageSettings": { "enabled": true }Enable Merge Confidence. by inputting the following parameter in your repo-config.json or .whitesource file →
remediateSettingsblock:CODE"extends": ["mergeConfidence:all-badges"]Save and commit your changes.
Kick-off a Mend scan by: GitHub.com - Initiating a Scan
Allow the Mend check run to complete and Remediate PRs to be created.
Navigate to the Pull requests tab to view your Remediate PRs:
Sample repo-config.json/.whitesource file
{
"scanSettings": {
"configMode": "AUTO",
"configExternalURL": "",
"projectToken": "",
"baseBranches": [],
"enableLicenseViolations": "true"
},
"checkRunSettings": {
"vulnerableCheckRunConclusionLevel": "failure",
"displayMode": "diff",
"useMendCheckNames": true
},
"issueSettings": {
"minSeverityLevel": "LOW",
"issueType": "DEPENDENCY"
},
"remediateSettings": {
"workflowRules": {
"enabled": true,
"minVulnerabilitySeverity": "LOW"
},
"extends": ["mergeConfidence:all-badges"]
},
"leastVulnerablePackageSettings": {
"enabled": true
}
}